Forensic investigation using DNS for faster incident response
In this video, learn how BlueCat DNS Edge provides investigative insight and faster responses for security breaches and helps reduce attack surfaces.
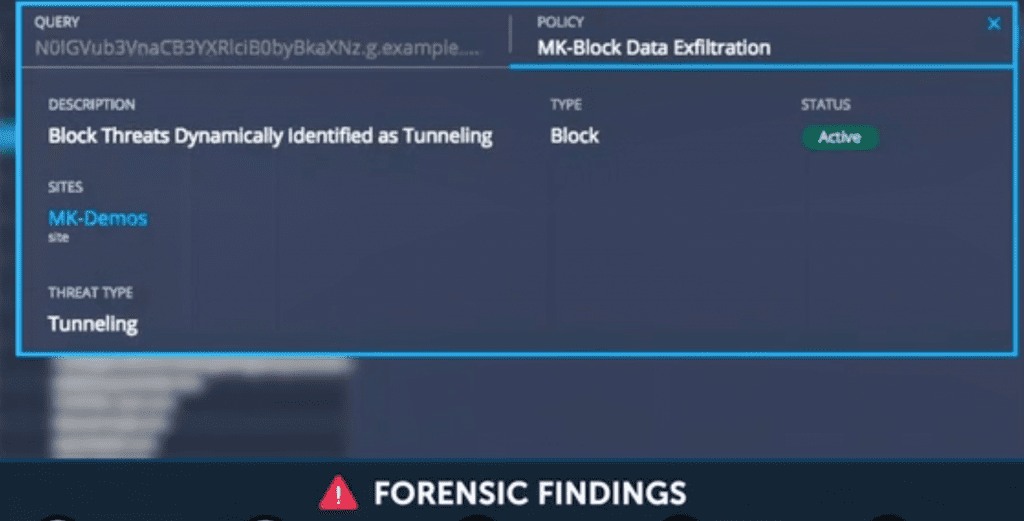
When a security incident occurs, incident response teams have to quickly get to the root of the issue – identifying infected clients, potentially-breached services, or data sources.
This video demonstrates the forensic value of DNS Edge to provide investigative insight, faster and more focused responses, and the ability to reduce attack surfaces. Watch as we demonstrate a comprehensive investigation of a breach, identifying the origination point and taking action to further protect the network.