DNS Edge November Release: Insights, Fleet Management, Native Threat Protection

DNS data can be difficult to wrangle. Gleaning meaningful insights from the constant stream of data is a daunting task. But there’s a lot of insight for both cybersecurity and networking teams in that data. That’s why the November Release of BlueCat DNS Edge™ provides a new beta capability aptly called, “DNS Insights”.
DNS Insights: Identify Anomalies, Uncover Configuration Issues
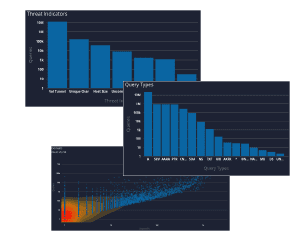 A single DNS log can provide a lot of answers. Charted in aggregate, those logs begin to uncover misconfigurations, understand traffic load, detect malicious activity and anomalies that warrant a closer look.
A single DNS log can provide a lot of answers. Charted in aggregate, those logs begin to uncover misconfigurations, understand traffic load, detect malicious activity and anomalies that warrant a closer look.
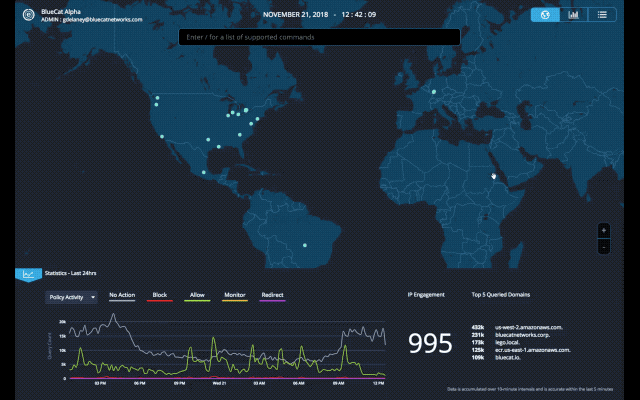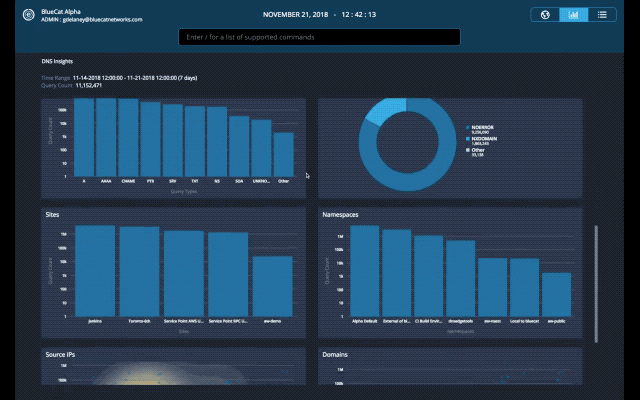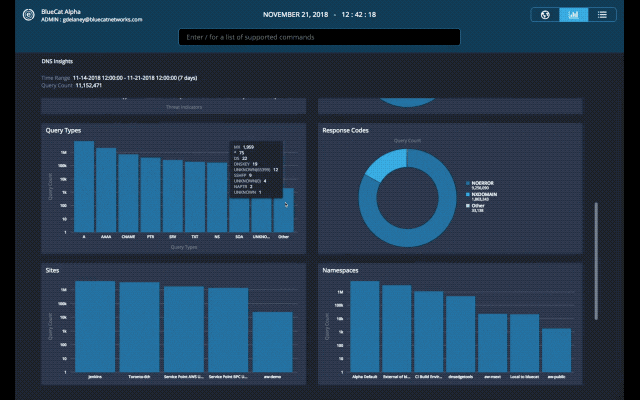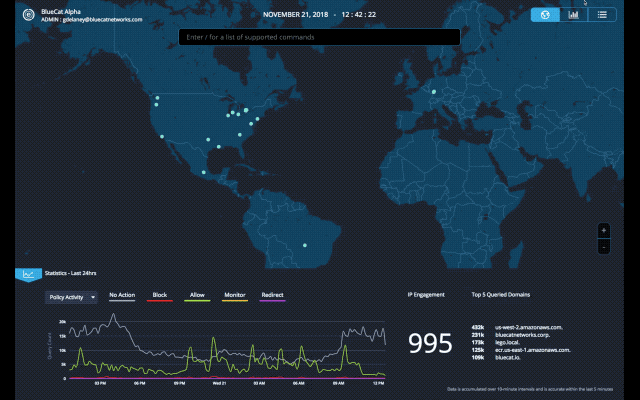
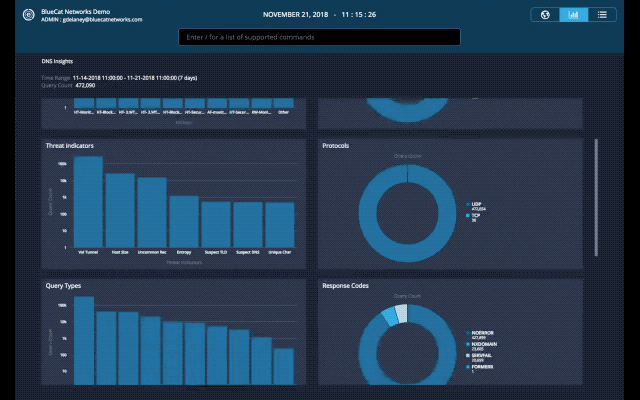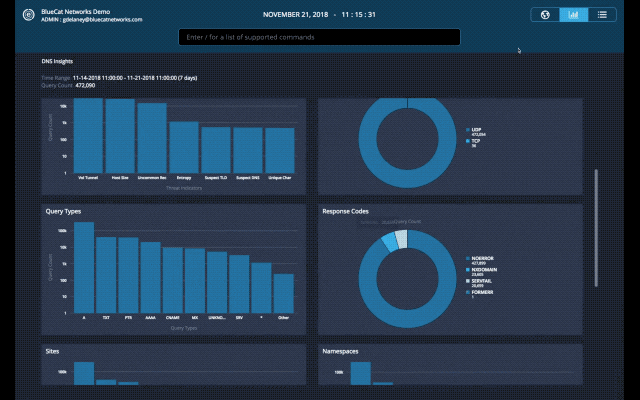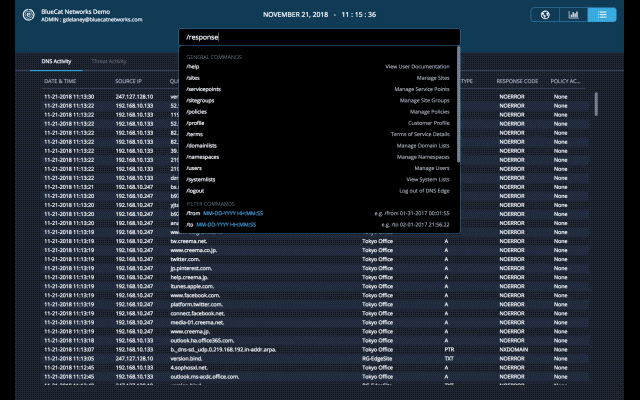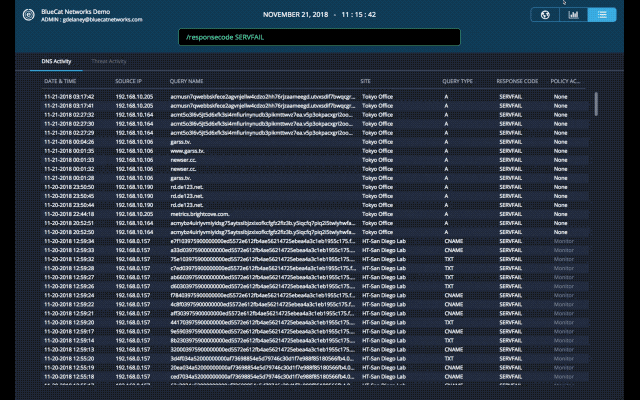
With this latest update of BlueCat DNS Edge, we begin to provide a graphical view of important data with the beta release of DNS Insights. This includes policies, policy actions, threat indicators, protocols, query types, response codes, sites, namespaces, query volume by source IPs and query volume by domain count.
What DNS queries will tell you
Query Types: Unusually high TXT or NULL query types can indicate activity that warrants additional investigation. This investigation involves reviewing those query types to understand the context and source IP they’re originating from. TXT queries are often used to exfiltrate data since the query type itself has a larger character limit than others. NULL query types at unusually high volumes can indicate a DDoS attack from a compromised endpoint.
Response Codes: Query responses such as SERVFAIL or NXDOMAIN can indicate a misconfiguration – for example, an application on a client device looking up an incorrect domain name. NXDOMAINs can also be generated from domain-generating algorithms (DGA) on an infected client device. Spikes in these response codes are often the first signs of bigger problems.
Sites: Unusually high volume of traffic to a particular site can indicate load balancing problems. Addressing these issue may require adjusting anycast configurations, deploying additional DNS Edge service points, or other changes. If the site has a low volume of client devices, it may indicate a compromised endpoint that is worth investigating.
Today, looking deeper into these findings is easily achieved by adjusting the command line within DNS Edge. The additional visibility provided by the DNS Insights tab is just the starting point of what’s to come in future releases.
Service Point Fleet Management
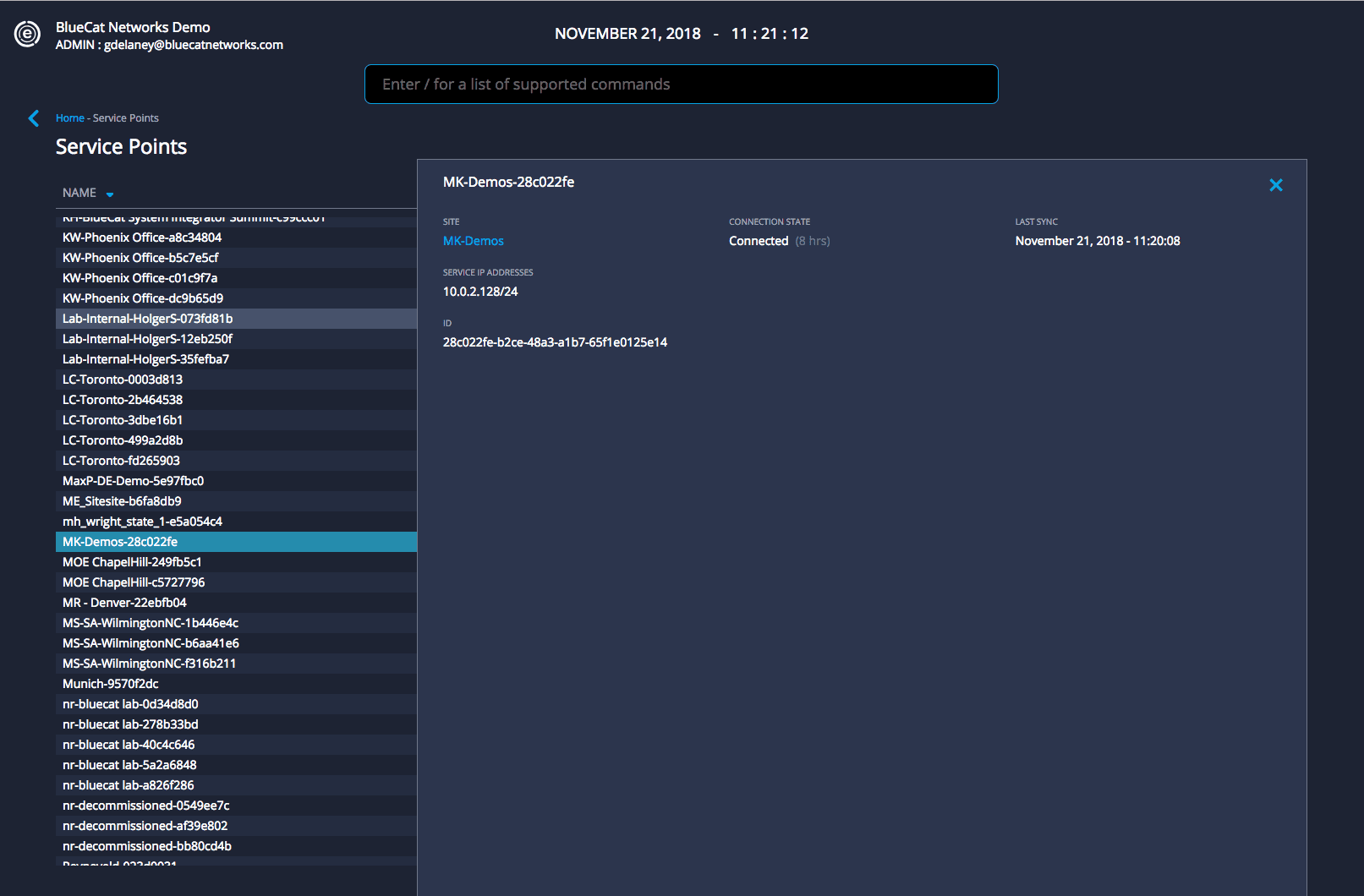
DNS Edge provides critical visibility and control of DNS on your network writ large. With this release, we are delivering additional visibility into Service Points from within your cloud console. “Service Point Fleet Management”, allows users to navigate to /servicepoints from the command line or click on the hyperlinked Service Point within the site window.
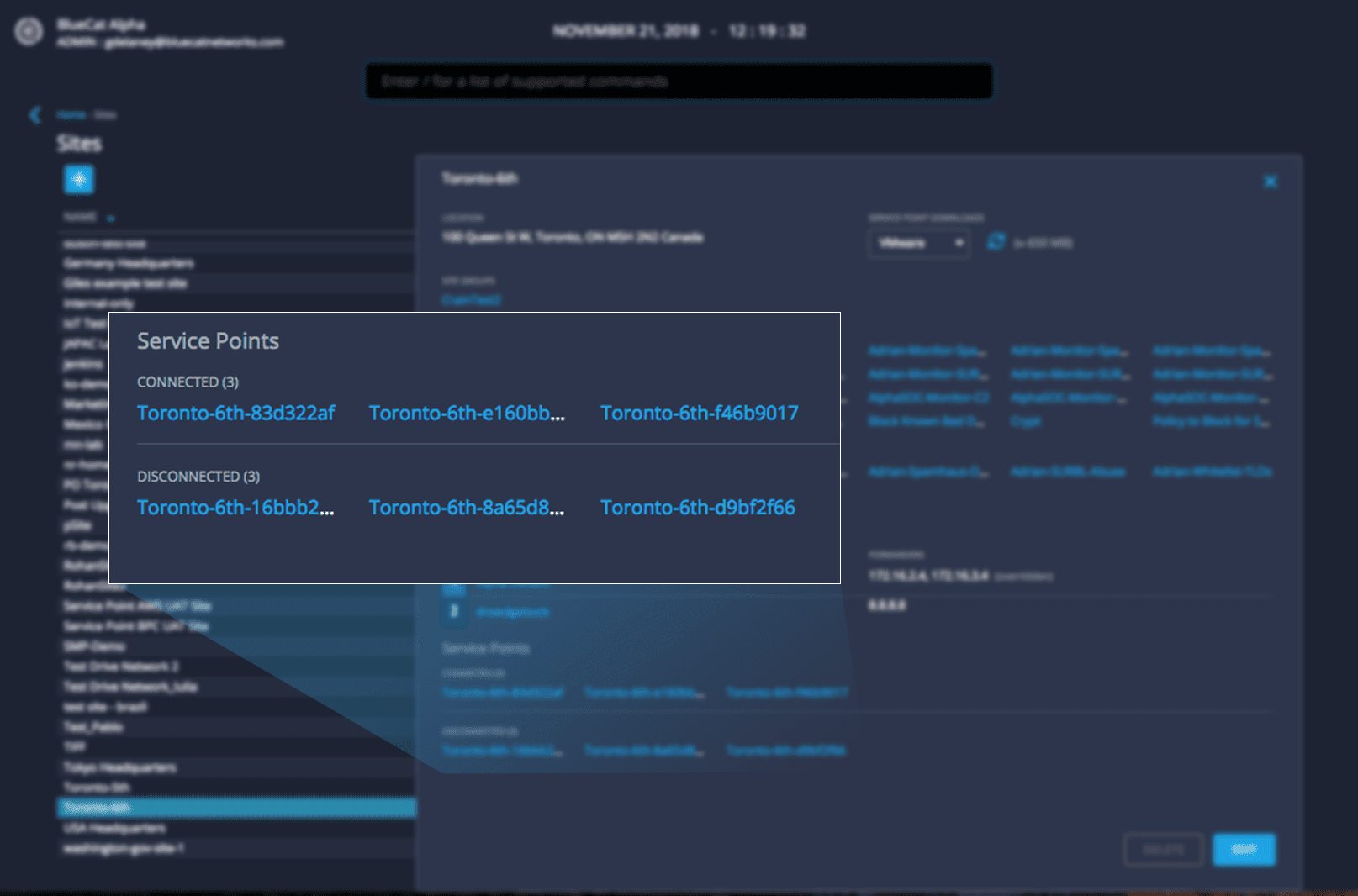
Within a site, users can easily view all Service Points and their connection status.
Native Threat Intelligence Integration
BlueCat Threat Protection™ is a curated source of threat intelligence feeds updated regularly with findings and sources from BlueCat threat analysts. This threat intelligence includes command and control (C2) domains, ransomware, botnets and other malware types. With this release, BlueCat customers with a subscription to Threat Protection can apply feeds to a policy natively available from within their Edge Instance. Users select the appropriate threat feed domain list and create block, redirect or monitor policies to take action.






