Detect anomalies and CVE risks with LiveAssurance 8.4
The LiveAssurance 8.4 release features an anomaly detection engine for outliers and a CVE analysis engine to uncover device vulnerabilities.

For IT operations teams needing deeper and more automated insight into anomalies and vulnerabilities in their security and network infrastructure, BlueCat LiveAssurance 8.4 is now available.
LiveAssurance avoids network disruption with automation. It is a proactive observability, troubleshooting, and remediation solution for network and security infrastructure like DDI, firewalls, and load balancers. It continuously scans infrastructure for issues and serves up recommended remediation steps that IT operations teams can use to address issues before they cause harm and avoid costly outages.
In this post, we’ll highlight new features in the LiveAssurance 8.4 release, including an anomaly detection engine that uses machine learning models to identify outliers for several metrics in your Palo Alto Networks and BlueCat Integrity devices. Further, we’ll delve into the new CVE analysis engine that uncovers device vulnerabilities for certain CVEs. And finally, we’ll briefly highlight other reporting, alerting, and knowledge enhancements.
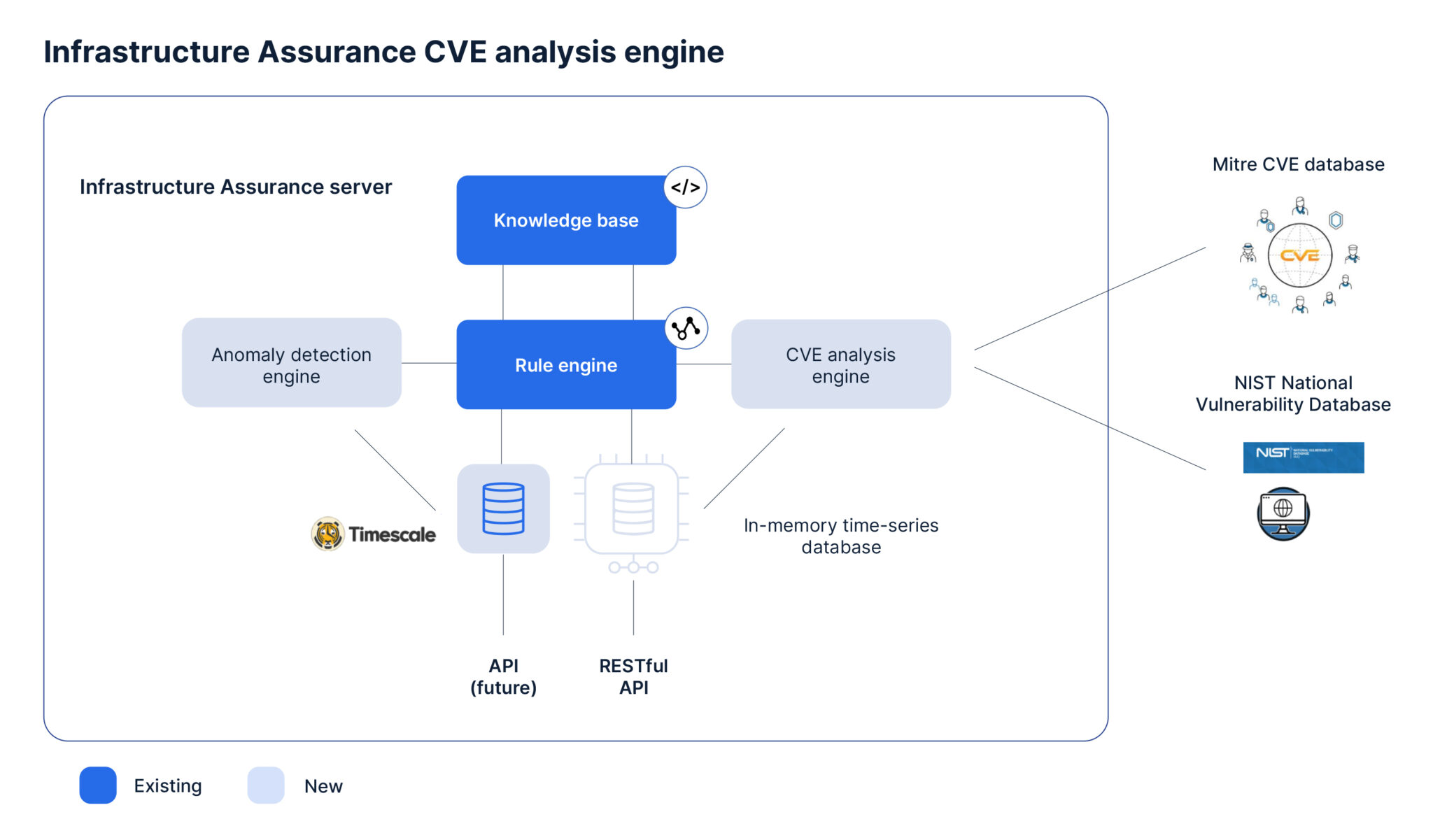
Anomaly detection engine
The anomaly detection engine uses machine learning models to identify outliers and unusual behaviors for several metrics in your Palo Alto Networks Next-Generation Firewalls and BlueCat Integrity DNS and DHCP Server (BDDS) devices. An anomaly detection generates a warning alert.
With awareness of such anomalies, LiveAssurance can identify early symptoms and emerging issues, allowing you to address them before they become bigger problems. Our implementation uses the standard score or z-score method to detect anomalies. A z-score measures exactly how many standard deviations above or below the mean a data point is.
The system evaluates several metrics based on a week’s worth of data points. The newly embedded time-series database stores these data points. When a new data point is collected, a z-score is calculated. An alert is generated if the z-score of that data point is greater than 3 (or less than -3). The alert will remain active for 10 minutes. During that time, if no other anomalies are detected, the alert will resolve itself and go into the cooldown state. If another data point has a z-score greater than 3 (or less than -3), the alert will remain active for another 10 minutes.
Next, we’ll look at what metrics we’re applying to the method to detect outliers and why they’re important.
Anomalies for Palo Alto Networks Next-Generation Firewalls
Palo Alto Networks Next-Generation Firewalls keep a count of all drops and what causes them. Analyzing these drop counters provides insights into the processes, packet flows, and sessions on the firewall. LiveAssurance 8.4 now analyzes four global drop counters for anomaly detection.
- flow_tcp_non_sync_drop: If this counter increases suddenly and significantly, it is indicative of asymmetric routing in your environment. Applications will encounter issues. For example, websites are only loading partially, or applications are simply not working.
- flow_policy_deny: This counter records increments when a security policy denies a session setup for network traffic. An abnormal increase in this counter could mean an issue such as a misconfigured rule, a scanner on the network, or increased attempted connections from a rogue device.
- flow_action_close: The firewall sends a TCP reset (RST) when it detects a threat in the traffic flow. This counter tracks the number of closed TCP sessions by injecting RST. A sudden increase in this counter can potentially pose a security risk, so you’ll want to investigate immediately.
- nat_xlat_address_resolved_fail: This counter provides information about the number of times that FQDN resolve failed. If nat_xlat_address_resolved_fail suddenly spikes, this could mean there is a problem with resolving DNS on the firewall.
Anomalies for BlueCat Integrity BDDSes
For Integrity enterprise customers, LiveAssurance provides proactive observability and automated troubleshooting to root out hidden issues in your DDI environment, along with recommended steps to address them.
A new anomaly alert in LiveAssurance 8.4 for Integrity BDDSes is “A sudden increase in SERVFAIL”. A temporary server overload or a temporary connectivity disruption can cause SERVFAIL errors. A small number of SERVFAIL errors may not be of concern, but a spike in SERVFAIL errors could mean a combination of many issues that can lead to bigger problems.
For example, it could be a technical problem with your DNS servers, firewalls blocking users from going to a domain, or DNSSEC verification failures. These issues can cause downtime for many domains, users, or both. Any of these cases warrant an investigation.
In the screenshot below, LiveAssurance displays anomalies it has identified in Integrity BDDSes, including issue descriptions and recommended remediation steps.
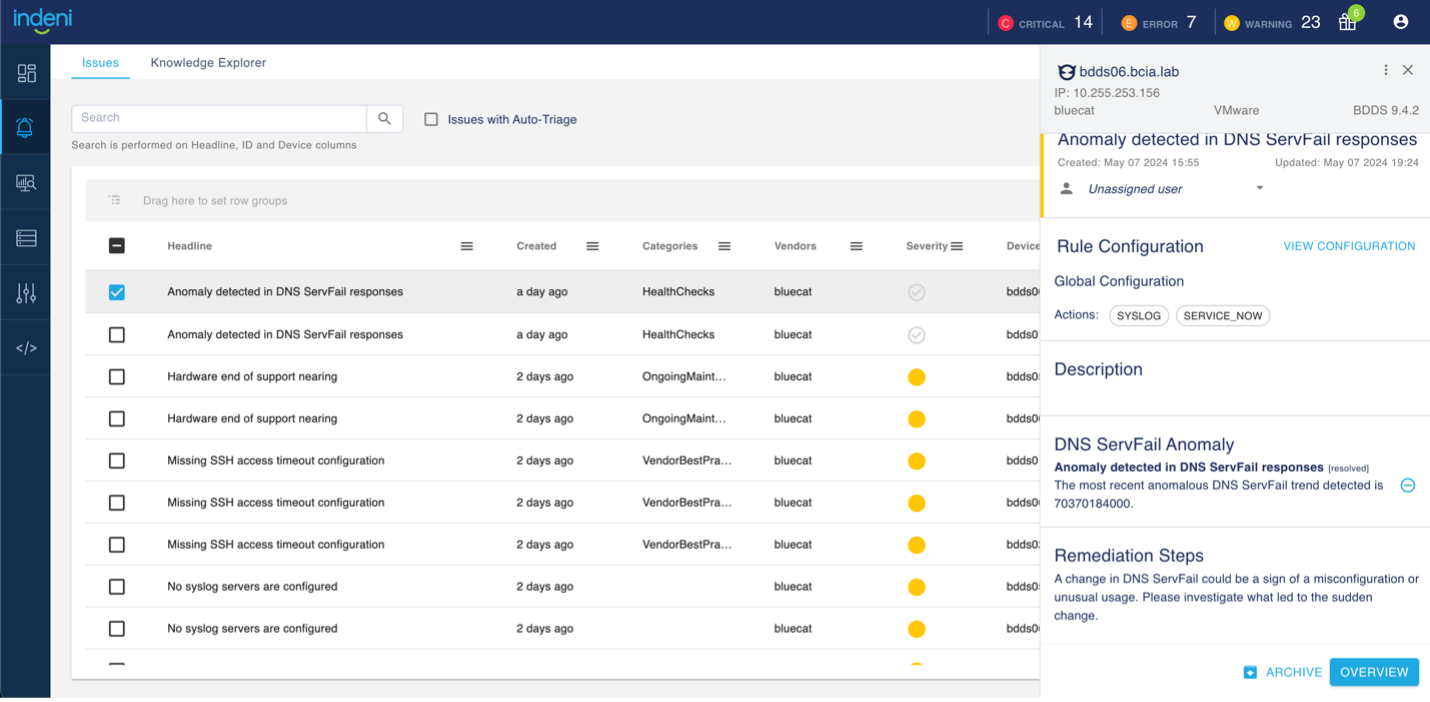
And a final note: This anomaly detection feature is not enabled by default. LiveAssurance customers should contact Customer Success for assistance with enabling it.
CVE analysis engine
Coalition’s 2024 Cyber Threat Index anticipates that the total count of published common vulnerabilities and exposures (CVEs) for 2024 will rise by 25%. This expected sharp increase in CVEs further heightens security concerns. CVE disclosures put tremendous pressure on an already overloaded security team, making automation essential.
LiveAssurance’s CVE analysis engine analyzes a network device’s vulnerability. The engine automatically compares CVE information from MITRE’s CVE database and NIST’s National Vulnerability Database with OS versions running on the devices in your network. Using this comparison, LiveAssurance will automatically generate alerts for devices exposed to certain CVEs.
Imagine the possibility of receiving near real-time alerts about new CVEs that impact your environment. Coupled with LiveAssurance’s new system-defined CVE report, you can get a list of devices with vulnerabilities categorized by severity with just a click. You can run this report after every upgrade to detect new CVEs impacting your environment.
In the screenshots below, LiveAssurance’s system-defined CVE report displays devices with CVE vulnerabilities, categorized by severity.
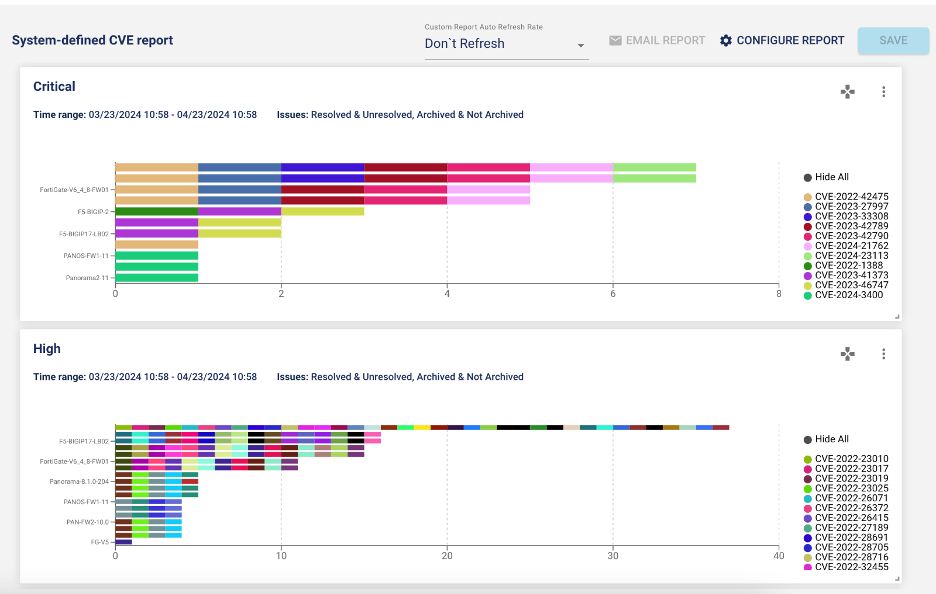
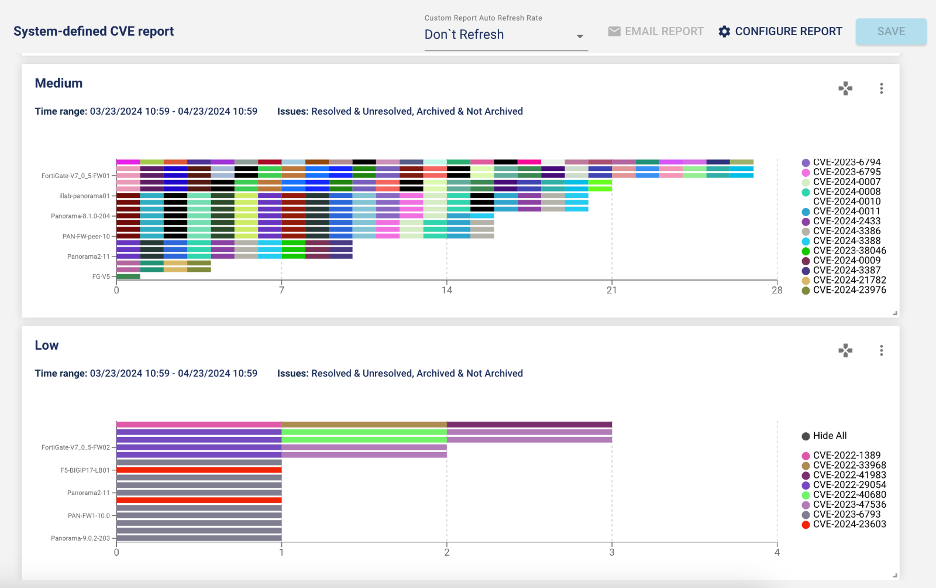
LiveAssurance 8.4’s new CVE analysis engine brings more than 200 alerts, dated from 2022 and onward, to the release. Supported devices for the CVE analysis engine include Broadcom Symantec (formerly Blue Coat) Content Analysis series and ProxySG, Check Point secure gateways, Cisco ASA, F5 BIG-IP Local Traffic Manager (LTM), Fortinet FortiGate firewalls and Palo Alto Networks Next-Generation Firewalls.
Further, so as not to overwhelm the Issues page with more than 200 new alerts, LiveAssurance 8.4 includes a new rule category called CVE. By design, the Issues page and the Knowledge Explorer page exclude rules from the CVE category.
To see rules in the CVE category, reset the default filters by selecting CVE in the Categories column. The new rule headline shows the CVE ID (CVE-2024-xxx). The description consists of details about the vulnerability.
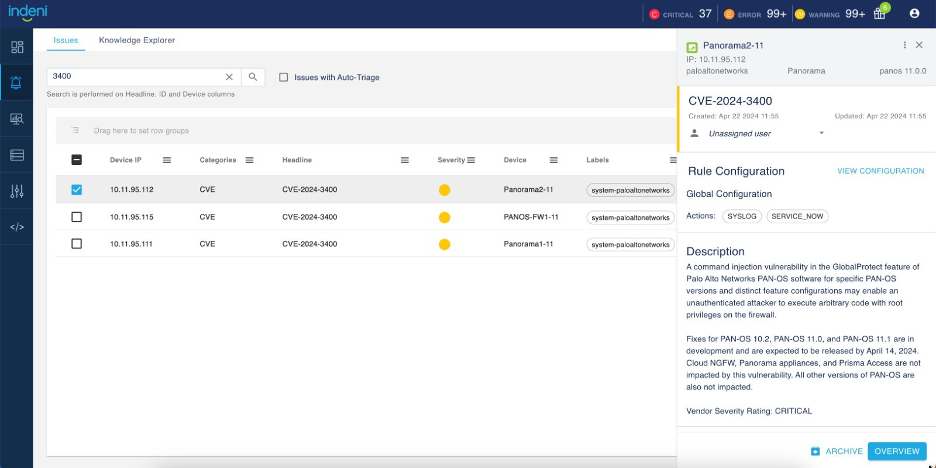
You can also navigate to your CVE alerts from the Issues-At-A-Glance widget from the analytics dashboard.

Reporting, alerting, and knowledge enhancements
LiveAssurance 8.4 also includes enhancements to reporting features, more control over how many alerts you receive, and more than 200 auto-detection knowledge enhancements.
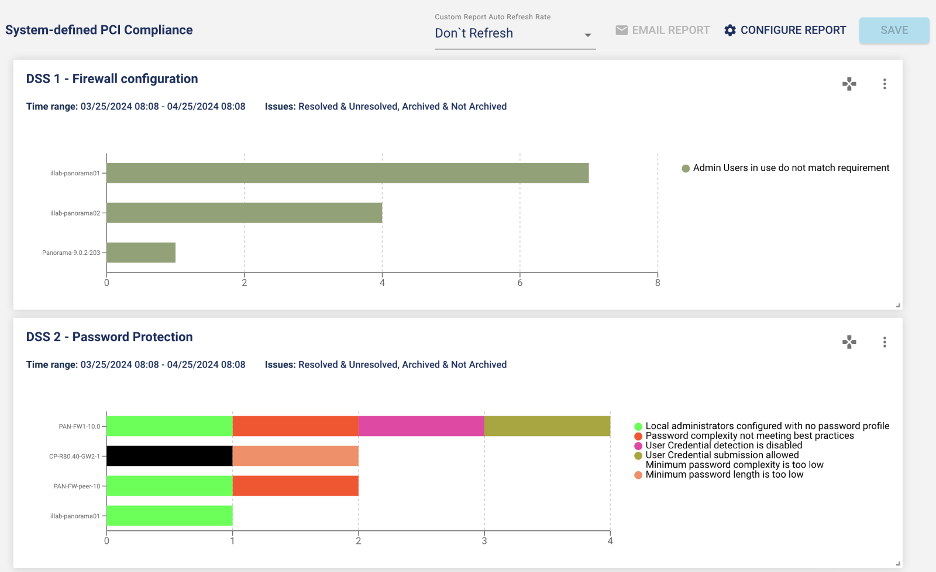
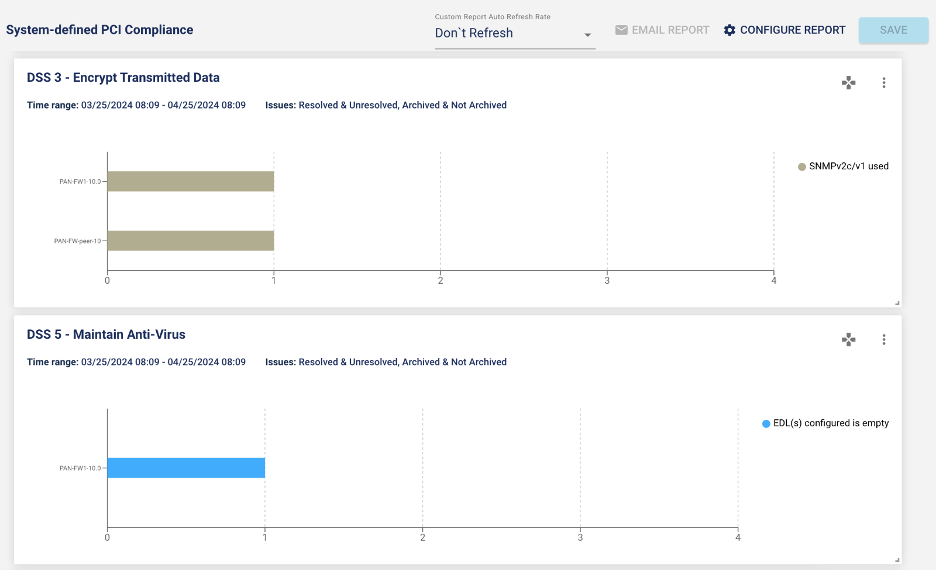
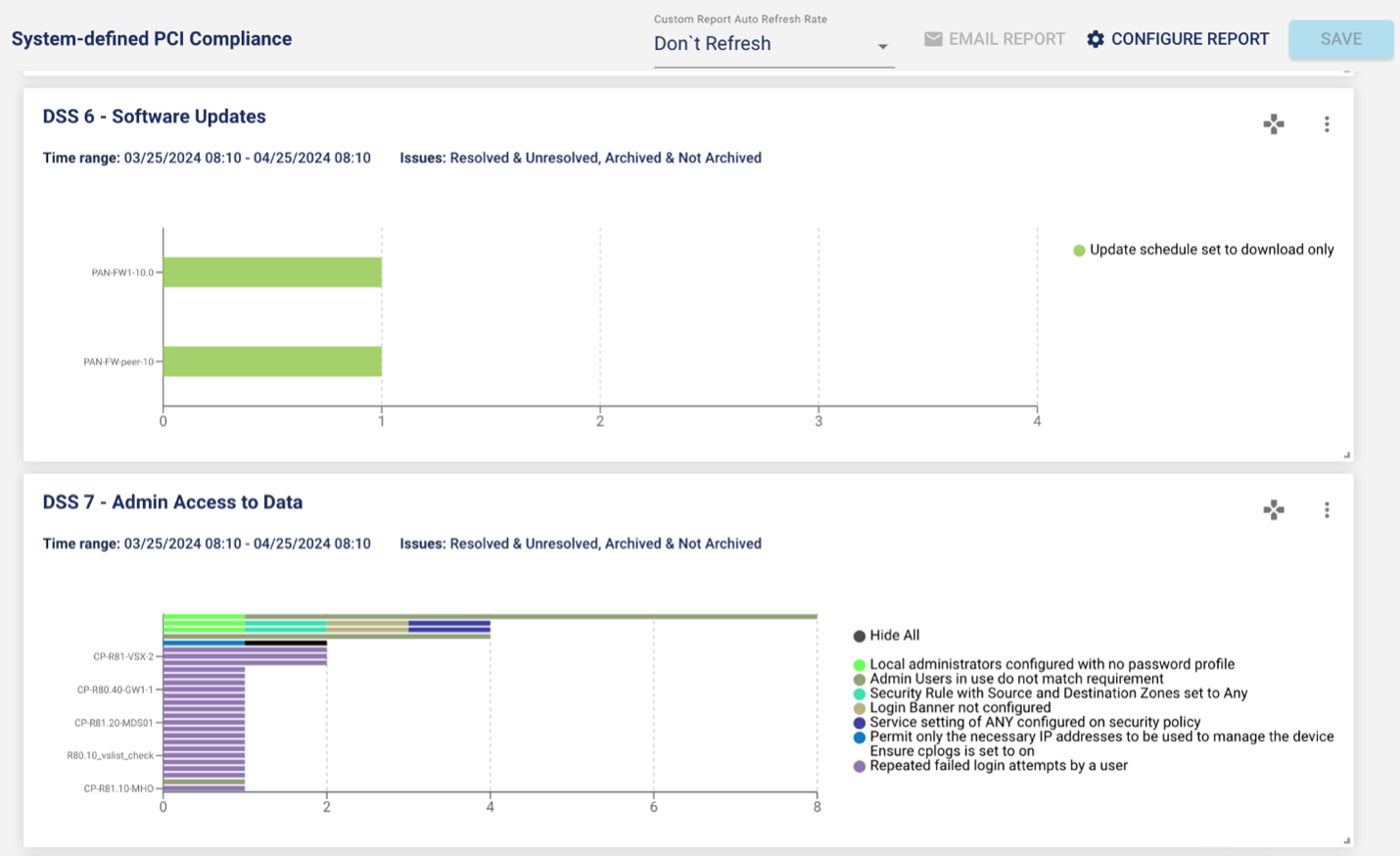
A new system-defined PCI DSS compliance report
The release introduces a new out-of-the-box Payment Card Industry Data Security Standard (PCI DSS) report. More than 100 rules are mapped to the PCI compliance standard.
The screenshots below provide examples of PCI DSS report results.
Legend improvements for reports
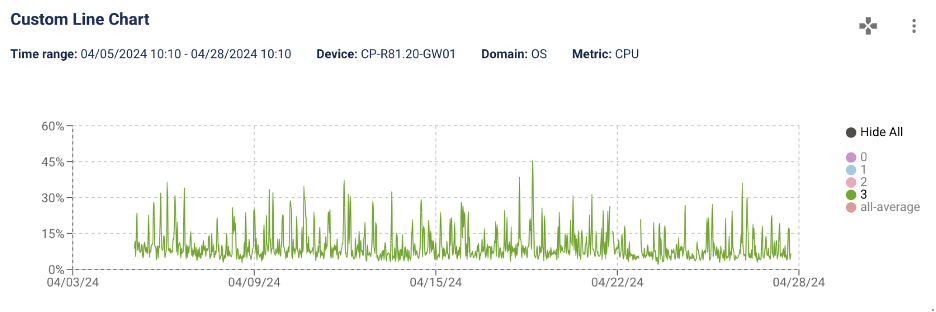
With LiveAssurance 8.4, you can now change the legend and save it in your report. The new Hide All option in the legend makes it easy for you to hide some of the attributes in your graph.
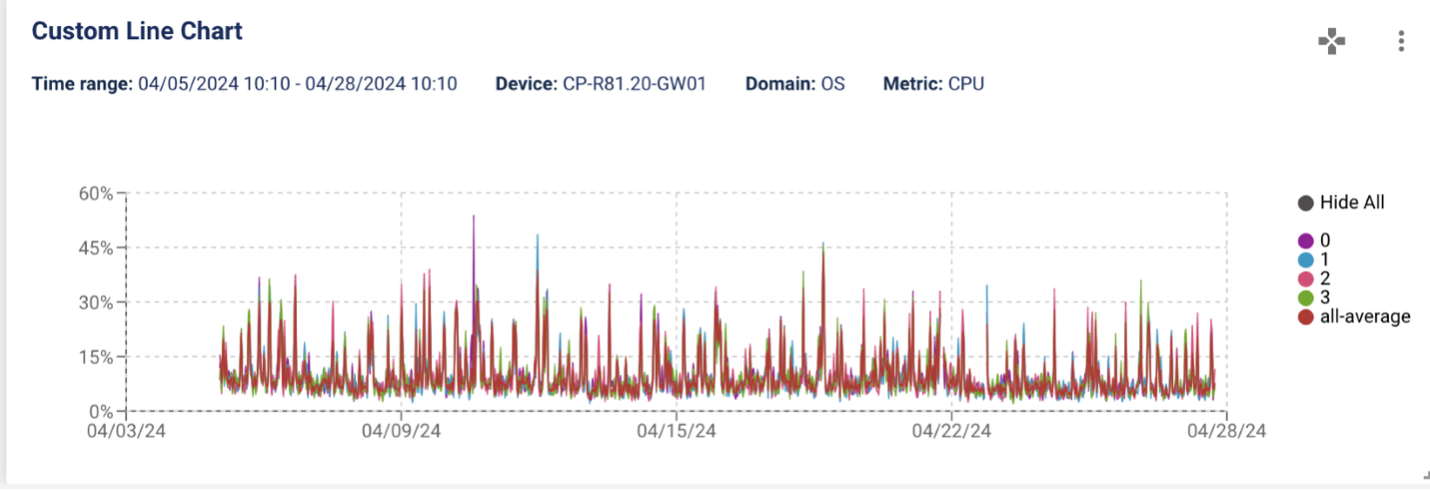
You can now change the legend and save it in your report.
Alerts for every issue item
Alert fatigue is real. LiveAssurance keeps noise levels down without letting problems escape you. The issue item feature is one technique to reduce noise.
A great example is VPN tunnels. A firewall typically has many VPN tunnels connecting remote sites and users. Instead of alerting you to every event in which a VPN tunnel is down, LiveAssurance associates a tunnel as an issue item. When the first VPN tunnel goes down, it creates a new alert. When the second VPN tunnel goes down, it adds the second VPN tunnel down event as an issue item to the existing alert.
With LiveAssurance 8.4, you can disable issue item collection by changing the configuration file. Instead of concatenating issue items to an existing alert, the system generates a new alert for every issue item. But enabling this feature can greatly increase the number of alerts in your environment.
Knowledge enhancements
The LiveAssurance 8.4 release includes more than 200 auto-detection knowledge elements and enhancements. Devices supported by these enhancements include BlueCat Integrity, Broadcom Symantec (formerly Blue Coat) Content Analysis series, Check Point Maestro, and Palo Alto Networks Next-Generation Firewalls. For a complete list of enhancements, see details in the release notes.
Ready to see the anomaly detection engine and CVE analysis engine in LiveAssurance 8.4 for yourself? Request a live demo today.




