How adversaries are using your DNS data
Find out how much can you learn about a company and their employees simply through DNS data?

“Use DNS data for your network security.”
At BlueCat, we’ve said that countless times. In fact, we talk about the security applications a lot. Whether it’s configuring DNSSEC, leveraging DNS response data, or hardening your security posture, there are endless ways to use DNS data for good.
What we don’t talk about enough is how the bad guys use DNS data. The same way security teams learn revealing details about network traffic, adversaries are using DNS for reconnaissance on enterprises and their employees. The intelligence they gather feeds into their cyber attack strategies.
So how much can you learn about a company and their employees simply through DNS data?
We took one business day’s worth of DNS logs from a corporate laptop, analyzed the data, and were surprised by how much we can learn about one person by just looking at their logs.
Here are the five things we discovered, along with how adversaries may use the intelligence we uncovered.
(Personally) Identifiable Information
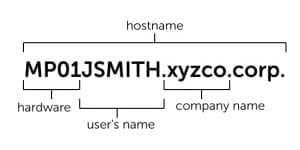
Finding: There was a recurring character set in all internal DNS queries which contain the device hostname.
What would an adversary do? Many organizations use a common naming convention for devices connected to the network. The hostname often includes details like a user’s name, the company name, and the type of hardware. We found all three of these in the queries we looked at. Having this intelligence gives an adversary two advantages. By knowing the naming convention, they can easily direct their attacks to a specific user’s device on the network. All it takes is a quick Google or LinkedIn search to identify a target. Also knowing the type of hardware, such as PC or Mac, means they can choose malware designed for a specific operating system.
Corporate Power User
Finding: There were 7346 DNS queries from this laptop over eight hours. Only 7%, or 517 queries, were user-generated, making the remaining 93%, or 6829 queries, machine-generated. (Keep in mind that the average corporate laptop generates between 4000 to 5000 queries during a workday.)
What would an adversary do? The high quantity of queries from one device indicates a power user or a technical worker. A user like this typically has access to more backend systems than others. The sheer volume of queries makes this user an ideal target, because more queries can mean more valuable data. Especially when the data comes from one source, it’s less work for an adversary. Another advantage is the opportunity for DNS tunneling. Again, the volume of queries creates an ideal environment for the unwanted traffic to get lost in.
The Suite of Business Applications
Finding: A large percentage of external domains queried included common business applications: Dropbox, Slack, Office365, Outlook, and Adobe.
What would an adversary do? A company’s suite of business applications can be very telling. A view into the software used gives bad actors a sense of what vulnerabilities they can exploit. Keep in mind that those vulnerabilities are unique for each application. When compounded by the volume of applications across an enterprise, the attack surface becomes larger and creates a more complex environment to secure. In a more tactical fashion, an adversary can use this information to design more effective phishing emails. Business applications become trusted names among an organization’s employees. Sending emails that leverage another company’s familiar brand is a social engineering tactic that often works. It’s a reason why phishing emails are still one of the most common delivery methods for malware.
Unofficial Job Description
Finding: A substantial amount of device- and user-generated queries were directed to VMWare ESXi, GitHub, and AWS domains.
What would an adversary do? The combination of these three domains indicates the scope of the user’s work-related responsibilities. We know that ESXi is a tool for managing virtual machines, GitHub is for software development, and AWS is for cloud services. It is likely this user works with infrastructure and development. Chances are they’re a network engineer or in a similar role. Adversaries can glean the type of access this user has, which helps map their infiltration strategy. This insight is particularly valuable as bad actors plan network lateral movement, a common technique for cyber attacks.
Soccer Family in Toronto
Finding: This user browsed many soccer club websites.
What would an adversary do? This is where things get creepy. Since this observation is very personal in nature, it is particularly useful for more vicious bad actors. By analyzing the soccer club sites, we found several soccer club sites were specific to a Toronto neighbourhood, a good indicator of where this user may reside. Most soccer club sites they visited were exclusively for youth soccer, so it’s highly likely they have kids of their own. The most revealing website was one for an Assyrian athletic club for adults, likely indicating the user’s cultural background. Knowing where this user lives, the fact they have a family, and their ethnicity dramatically ups the creepy factor. An adversary can use personal details like this in extortion tactics or threats.
Independently, each of these findings provides a piece of the puzzle. Together they give us, and adversaries, a full picture of who this user is in the corporate setting and at home. As enterprises learn how to better defend against cyber attacks, adversaries are becoming more sophisticated. DNS data, like the logs we analyzed, provide points of personalization that allow for more targeted attacks.
What You Can Do
Network security has become more challenging as environments have become increasingly complex. Here are a few strategies that can protect against bad actors on your network:
- Look at your DNS traffic and understand what is exposed in your queries
- Consider configuring internal systems to expose less unless absolutely necessary
- Safeguard your DNS data, ensure where it’s being stored is properly protected with adequate security measures
Learn more about how BlueCat secures DNS as part of our intelligent security offering.