Ensuring Availability of Check Point devices during COVID-19
Virtual Private Network (VPN) usage is surging as the number of employees forced to work from home increases due to the COVID-19 pandemic. Security practitioners around the world are struggling to cope with the challenges posed by the drastic increase of remote workers stressing the IT infrastructure in an unprecedented way. Many organizations are not prepared to support the majority of their workforce working from home. Indeni can help you maintain business continuity during times of crisis. To ensure maximum reliability, Indeni continuously assesses Check Point device health by comparing expectations of device capacity against the current load. The ability to proactively alert administrators of capacity limits is key to keeping these devices up and running.
Indeni has automated best practices for Check Point firewalls to deliver predictive and actionable insights that help you prevent costly disruptions during this challenging time. We have provided a quick snapshot of some of them, below.
1) Track the number of VPN connections
Indeni continuously assesses the number of concurrent VPN connections against automatically-learned limits for the Check Point device. It is important that we track the number of users at all times to maintain stability. As connections are approaching the device limit, we proactively notify users before the VPN service is impacted.
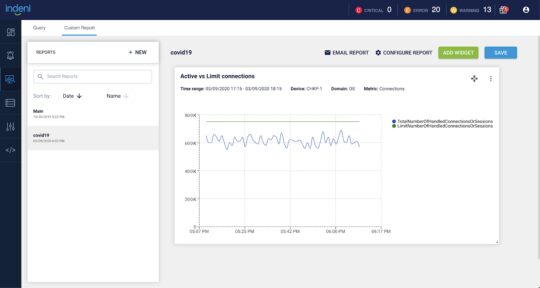
We recently announced a new feature to show the actual number of VPN connections against the maximum number of connections limit in response to the COVID-19 crisis. 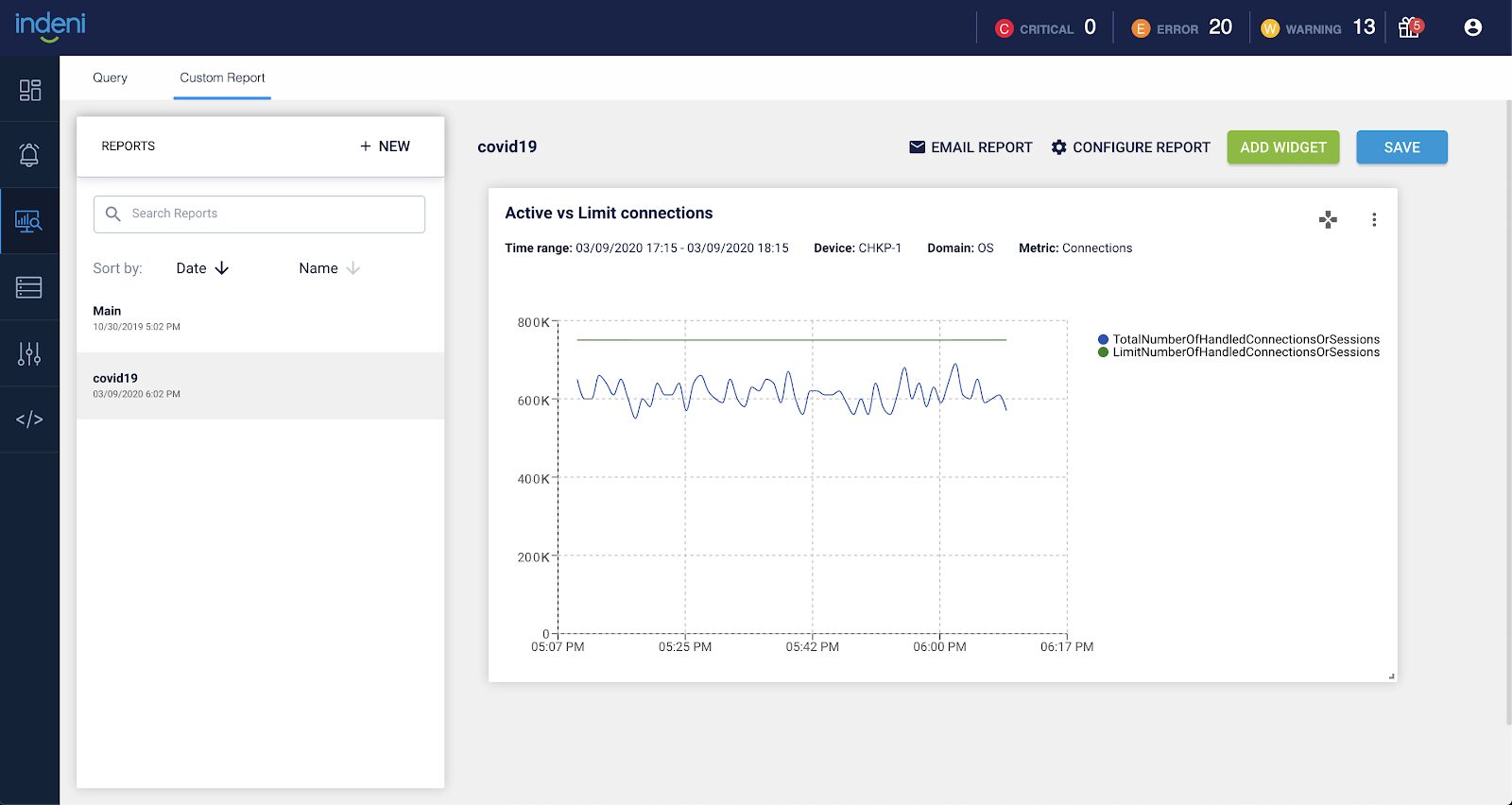
2) Performance and Availability of VPN services
It is now more important than ever that IT teams capture metrics about the performance and availability of VPN services. Indeni continuously assesses device (or Virtual System) health by comparing expectations of device configuration against the reality of current status. You will be proactively notified of performance issues that could become bigger problems. Below is a sample list of health checks:
- Check for VPN tunnels status & errors found in $FWDIR/conf/ipassignment.conf which is used for remote access VPN configuration
- Check for network connectivity – BGP peer(s) down, OSPF neighbor(s) down, failure with one or more ISP links, is the next hop accessible?
- CPU soft lockup
- Pnote(s) down
- Debugging file is rotating too fast
- High ARP cache
- Firewall kernel table limit approaching
- NAT connection limit nearing
- Connectivity to key services such as Management Servers, logging servers, LDAP servers, Certificate Authority, AAA servers, etc.
Our alerts come with recommended remediations. They are built from the real-world experience of certified IT professionals. They help you remediate potential disruptions regardless of individual skillsets.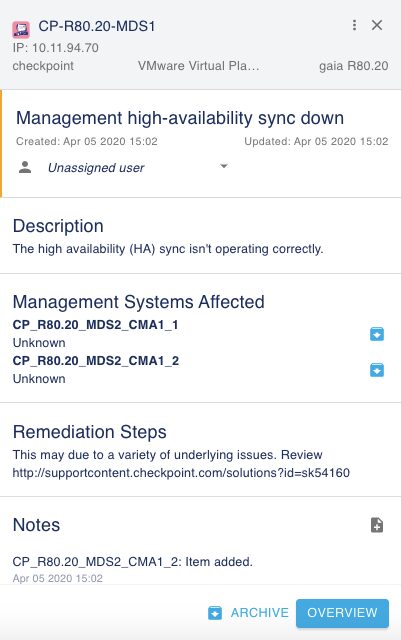
3) Auto-Triage issues immediately to reduce the IT burden
At times like this, you are going to need all the help you can get. You can leverage Auto-Triage to help reduce the burden on IT. For example, a device is logging locally which can eventually become a P1 event. When Indeni detects device logging locally, Indeni will automatically investigate the problem, without human intervention, and present details of the triage step by step leading to faster resolution and preventing a detrimental event.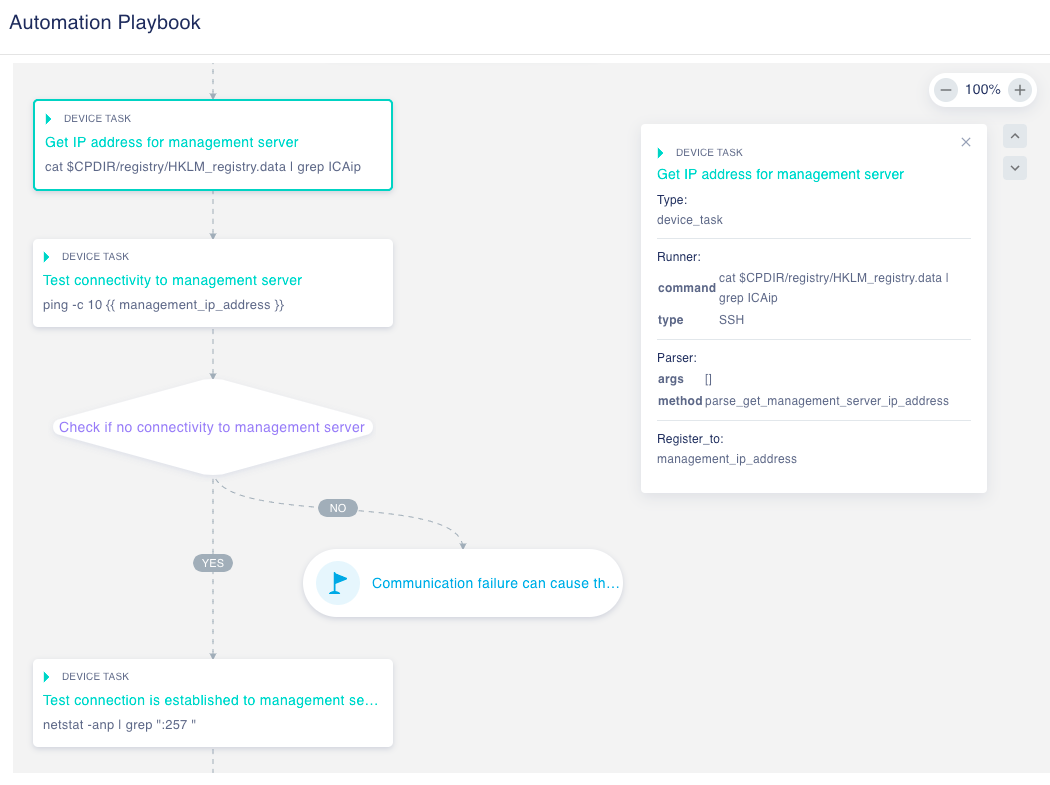
4) VPN Security
Many cybersecurity industry alerts and security bulletins have been published recently on the topic of VPN security. For example, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (DHS CISA) and the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC) are encouraging organizations to adopt a heightened state of cybersecurity for VPN services. Check Point researchers reported that coronavirus-themed domains are 50% more likely to be malicious than other domains. Therefore, it is important that the VPN service is patched and up-to-date, as attackers are targeting these VPN devices. Indeni continuously assesses Check Point devices for hotfixes applied to meet your security requirements. Indeni also identifies security risks, just to name a few:
- LDAP fingerprint not trusted
- Abnormal unsuccessful login attempts identified
- SNMP configured with default community string
- SNMPv2c/v1 used
- Telnet is enabled on the device
- Repeated failed login attempts by a user – In this example, Indeni detected a rather suspicious activity where a user has made 390 failed logins in the last hour.
5) Validate Best Practices
Indeni continuously assesses devices for alignment with configuration recommendations from vendors and seasoned practitioners. Implementing best practices means outages happen less often. This is a sample list of the best practices for Check Point devices:
- Aggressive aging enabled
- Routes defined in clish/webUI are missing
- SecureXL disabled
- Firewall more than one sync interface defined
- Host missing from hosts file
- RADIUS server uid is not 0
- UID for running user is not 0
- SmartEvent log handling too slow
- Cluster has preemption enabled
- ClusterXL Virtual MAC (VMAC) mode value does not match requirement
6) Valid Licensing and Contracts
Indeni identifies and proactively notifies you about upcoming licenses or contract expirations. If you are taking advantage of the vendor’s offer by obtaining special licenses during the COVID-19 pandemic, rest assured that Indeni can help you manage these ongoing maintenance tasks.
7) SSL Certificate Expiration
An expired SSL certificate would cause a variety of problems such as a:
- Failure of HTTPS requests
- Failure of SSL/TLS web traffic inspection
- Failure of X.509 certificate-based VPN tunnels
Yet, this is one of those often forgotten maintenance tasks and this would be the worst time to encounter this problem. Indeni alerts you in advance if the certificate is about to expire.
Next Steps
Existing customers can upgrade to version 7.1.5 or later. Those who are not currently using Indeni, but would benefit from these capabilities, can download Indeni from our website or reach out directly to us at [email protected]. We promise to find a way to give access to these capabilities even to those organizations that cannot currently purchase our software. We are committed to helping however we can during this time.
