Multicloud IP address management with Microsoft Azure
Make the most of Azure with Micetro, the only Microsoft-preferred solution for DNS, DHCP, and IPAM on the Azure Marketplace.
Who needs multicloud IP address management?
Both humans and machines use names and labels to find and access resources. When crossing from the physical to the digital realm, each element or entity requires a label or address for it to be accessed or used. Internal and external networks have boundaries. They are architected using a range of topologies and then grouped depending upon their characteristics, function, and risk level. Profiles and policies are then applied to these network zones and enclaves to facilitate sharing or enforce segregation.
Once an organization consumes services from any external cloud outside of its own fully managed network, it could effectively be thought of as engaging in a form of multicloud architecture. As Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) extend our organizational footprints into new territories, there is no escaping basic asset management for foundational services such as DDI (DNS, DHCP, and IPAM). As footprints inevitably grow and change, multicloud IP address management (IPAM) and DNS administration become even more crucial for the digital assets you name and control. Each new edge, network, or cloud-based resource increases the burden of operational responsibility. Unified DDI management and orchestration become table stakes to keep the packets flowing.
DDI automation, orchestration, and management
Digital borders are defined by IP addresses, prefixes, and virtual policy enforcement points. IP flows initiate and terminate on interfaces using addresses resolved from records in namespaces. Tracking, allocating, and assuring ourselves that our fundamental building blocks are sound is an arduous undertaking though it should be painless and easy.
In a world of increasingly automated service provisioning and consumption, DDI operations must be timely, concise, and correct. The challenge accelerates when embracing IaC (Infrastructure as Code) and programmatic access to dynamic digital resources. We now begin to more deeply realize that DNS is one of the most, if not the most important, active assets and directories. It facilitates resource location, defines service endpoints, and uncovers paths to dependencies across public and private clouds.
Using a single authoritative UI (User Interface) and API, an OTT(Over The Top) DDI solution enables simple integration while streamlining interactions across silos without displacing them. This DDI solution then becomes the one trusted System of Record (SoR). When your perspective shifts to view DNS as the beating heart of a digital footprint, it’s not just operations and security teams that demand effective and efficient Change Management and record management; it also heavily impacts project and product team delivery.
Supported platforms and endpoints
It’s imperative that a DDI solution can meet your current needs, but it also must be able to evolve with your organization’s changing needs. By selecting a DDI platform that doesn’t involve a rip-and-replace methodology, you free yourself to embrace the best-in-breed DNS and DHCP solutions. Avoiding redesign, migrations, and friction is easy with an OTT (Over The Top) management and orchestration solution. This is how smart teams preserve their existing investments in infrastructure, workflows, and expertise. A new unified and trusted authoritative layer can then meet and exceed the demands of the present and even the future.
By providing support for commonly used services such as Windows DNS, BIND, Unbound, PowerDNS, Akamai Fast DNS, Azure DNS, Amazon Route 53, NS1, and Dyn, to name a few, means accelerated time-to-value without any rework. And once your footprint extends outwards from your home cloud to other cloud providers, multicloud data management becomes ever more crucial for development, staging, and production environments.
How to Add Microsoft Azure as a Cloud Service in The Console
In the Men&Mice Console, go to “Cloud Services”, and with a right-click, select “New Cloud Service” (or once “Cloud Services” is highlighted use the green plus symbol).
Here we can then select the type of cloud service required:

Once Azure is selected, we then want to Name our connection, enter a specific Tenant ID, its specific Subscription ID, and then both the Client ID and Client Secret (Value). The configured tenant ID (from the “App registration”) must have the correct role assignment and requisite permissions for the Subscription ID (as previously mentioned).

Note: The “Client Secret” entered above in Figure 3.0 is the Secret “Value” and not the Secret ID.
Micetro will retrieve the data from the cloud provider, save the account information, and then you must select the services required.
Micetro will then synchronize with Microsoft Azure (every 900 seconds) and perform actions on demand. We are now ready for a range of common tasks and workflows including the use of Micetro’s single-layer API to drive automation across our whole DNS namespace and IP footprint.
Note: All sensitive data required for communication with Azure such as IDs and secret values are encrypted both at rest and in transit.
How To Create a Virtual Networks (VNet) in Azure
Creating VNets (Virtual Networks)
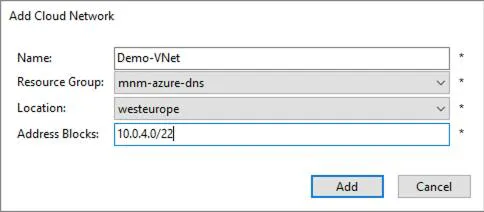
Micetro makes creating VNets easy and will also automatically track our IP allocations via the IPAM. Let’s create a VNet in the “europewest” Azure region using the CIDR block of “10.0.4.0/22,” from which we will allocate two separate subnets of “10.0.4.0/24” and “10.0.5.0/24” from the lower /23.
Note: Currently, we use the Men&Mice Console to create VNets in Azure, but shortly this will become available in the web application, including being applicable for the Workflow module.
From the Console, select the appropriate cloud service and then use the green plus (or Ctrl+n) to add a new Cloud Network:

Enter the Name, Resource Group, Location, and Address Blocks required and click Add:

And we can now see our new Demo-VNet listed in Micetro:

We will now create two subnets inside our newly formed Demo-VNet. We use the green plus button (or Ctrl+n) again to add the details we want for each of the new subnets using the details below:
Details (subnet 1): -Subnet: 10.0.4.0/24 -Title: Untrusted-DMZ-Tier -Description: This is our example initial DMZ tier within the VNet. -Cloud Network: Demo-VNet
Address Range: Reserve Network and Broadcast Address
Details (subnet 2): -Subnet: 10.0.5.0/24 -Title: Trusted-DB-Tier -Description: This is our example trusted DB tier within the VNet. -Cloud Network: Demo-VNet -Address Range: Reserve Network and Broadcast Address
This results in our subnets also going live in Azure:
Meanwhile, we can see that our subnets are also being tracked in our unified Micetro IPAM:
Example API Call(s)
You can test the Micetro REST API using cURL with the appropriate user credentials to administer and access objects.
Tip: When using methods other than the default HTTP GET, remember to supply the header Content-Type of “application/json”. We will use cURL to demo some API calls. cURL is available by default in macOS and most Linux distributions, but it is also available as a binary for Windows if you’re using Windows and don’t want to use Powershell.
Let’s use the Micetro API to look up the earlier IPAM record (17.17.17.17) we created (when we added an A record to the “aws.menandmice.cloud.” zone):
Using macOS/Linux:
curl -silent --user <user>:<password> -X GET \ "https://<your_host>/mmws/api/IPAMrecords/17.17.17.17"Using Windows Powershell:
$cred = Get-Credential Invoke-RestMethod -Method GET -Cred $cred -Uri "https://<your_host>/mmws/api/IPAMrecords/17.17.17.17" | ConvertTo-Json -Depth 5Which results in the following JSON blob response containing all the associated data for the IP record (including its DNS records and DHCP information if applicable):
{
"result": {
"ipamRecord": {
"addrRef": "IPAMRecords/36",
"address": "17.17.17.17",
"claimed": false,
"dnsHosts": [
{
"dnsRecord": {
"ref": "DNSRecords/64",
"name": "aeuw1-w0017.azure.menandmice.cloud. [mnm-azure-dns]",
"type": "A",
"ttl": "600",
"data": "17.17.17.17",
"comment": "",
"enabled": true,
"dnsZoneRef": "DNSZones/12",
"customProperties": {}
},
"ptrStatus": "Unknown",
"relatedRecords": []
}
],
"dhcpReservations": [],
"dhcpLeases": [],
"discoveryType": "None",
"lastSeenDate": "",
"lastDiscoveryDate": "",
"lastKnownClientIdentifier": "",
"device": "",
"interface": "",
"ptrStatus": "Unknown",
"extraneousPTR": false,
"customProperties": {},
"state": "Assigned",
"usage": 4
}
}
}Now, let’s look for the related A record in DNS by specifying the zone and only using a partial search term:
Using MacOS/Linux:
curl -silent --user <user>:<password> -X GET \ "https://<your_host>/mmws/api/DNSZones/azure.menandmice.cloud./DNSRecords?filter=type=A AND name=@aeu"Or Windows Powershell:
$cred = Get-Credential Invoke-RestMethod -Method GET -Cred $cred -Uri "https://<your_host>/mmws/api/DNSZones/azure.menandmice.cloud./DNSRecords?filter=type=A AND name=@aeu" | ConvertTo-Json -Depth 5Which finds (1) record returned:
{
"result": {
"dnsRecords": [
{
"ref": "DNSRecords/64",
"name": "aeuw1-w0017",
"type": "A",
"ttl": "600",
"data": "17.17.17.17",
"comment": "",
"enabled": true,
"dnsZoneRef": "DNSZones/12",
"customProperties": {}
}
],
"totalResults": 1
}
}Learn more about Micetro
IPAM
Gain a complete overview of your network and prevent downtime caused by IP conflicts.
IPAM solutions for enterprises
Look for a solution that gives you a complete overview of all your IPAM.
IPAM for Microsoft
IP address management – (IPAM) for Microsoft with Micetro. Using Microsoft infrastructure products has numerous important advantages.