How to automate security operations
Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
Since you are interested in automating security operations, listen to this Intel Chip Chat with Indeni’s CEO, Yoni Leitersdorf. He discusses trends in network operations and automation.
+++
Follow up to 451 Research Webinar with Tufin
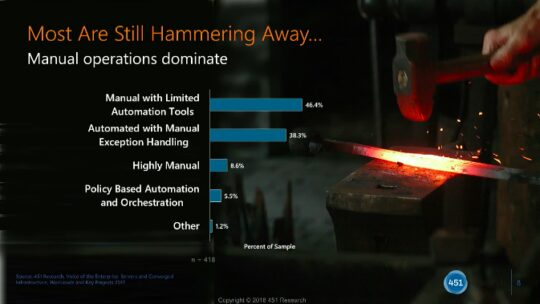
In a recent webinar by 451 Research and Tufin, they shared a graph that resonated with us quite a bit. Despite the advancements in security devices and overlay technologies, manual tasks still dominate day to day for security operations and engineering.
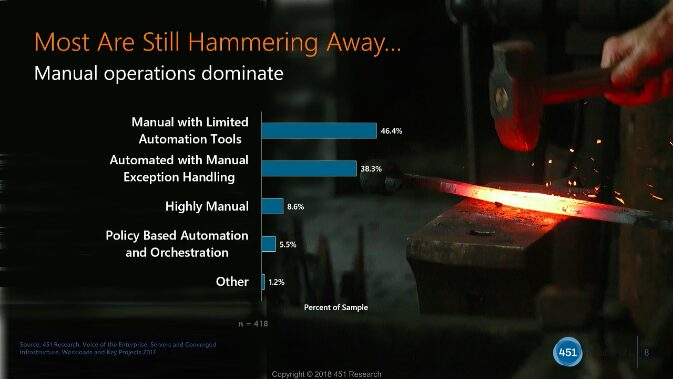
View Webinar presentation here
“The challenge for InfoSec environments is that we need to get our teams to do more with the capabilities they have. One of the biggest things to do.. is validating what you already have in place” – Eric Hanselman, Chief Analyst at 451 Research
How to Automate Task Validation
One of the reasons it is so difficult to implement automation across security devices, such as firewalls, is due to the architecture of the devices themselves. We discussed in more detail the lack of APIs and consistency in operating systems in a previous post here. In short, if you are working with a device that does not have programmable components, you will be recreating the scripting wheel every time you write a command.
Custom scripting leads to security breaches and network downtime
Scripts will break in many scenarios sometimes including:
- When you upgrade to a new operating system
- When you enable new features
- When you change administrators (Fun fact for non-techies: Similar to human-to-human communication, there are many languages to use when communicating with a device)
- Countless others ?
Before achieving task automation, you must first create quality, repeatable scripts. Only then can you automate the execution of pulling or pushing commands to these devices.
How to make repeatable scripts:
- Have a person (or team) who can code to your security devices
- Implement a peer review process by subject matter experts before code is used
- Perform manual and automated testing of code before approving for production
- Create a repository of rules and scripts to allow for reuse where possible (For example Juniper provides a number of security, switching and routing products that use the same operating system JUNOS)
Crowd-sourcing + Network Security Policy Orchestration = Productivity
If you are considering policy orchestration, you should also consider a platform that includes task validation to assist building a strong foundation. By implementing an agile but consistent development process at the scripting level, you can tap into the largest community of IT certified professionals, and ensure industry best practices for security and compliance are in place at the start of your automation journey.
Learn more about Indeni network automation solutions here.
If you found this useful please share with your community by clicking the social icons at the top of the page. Thanks!



