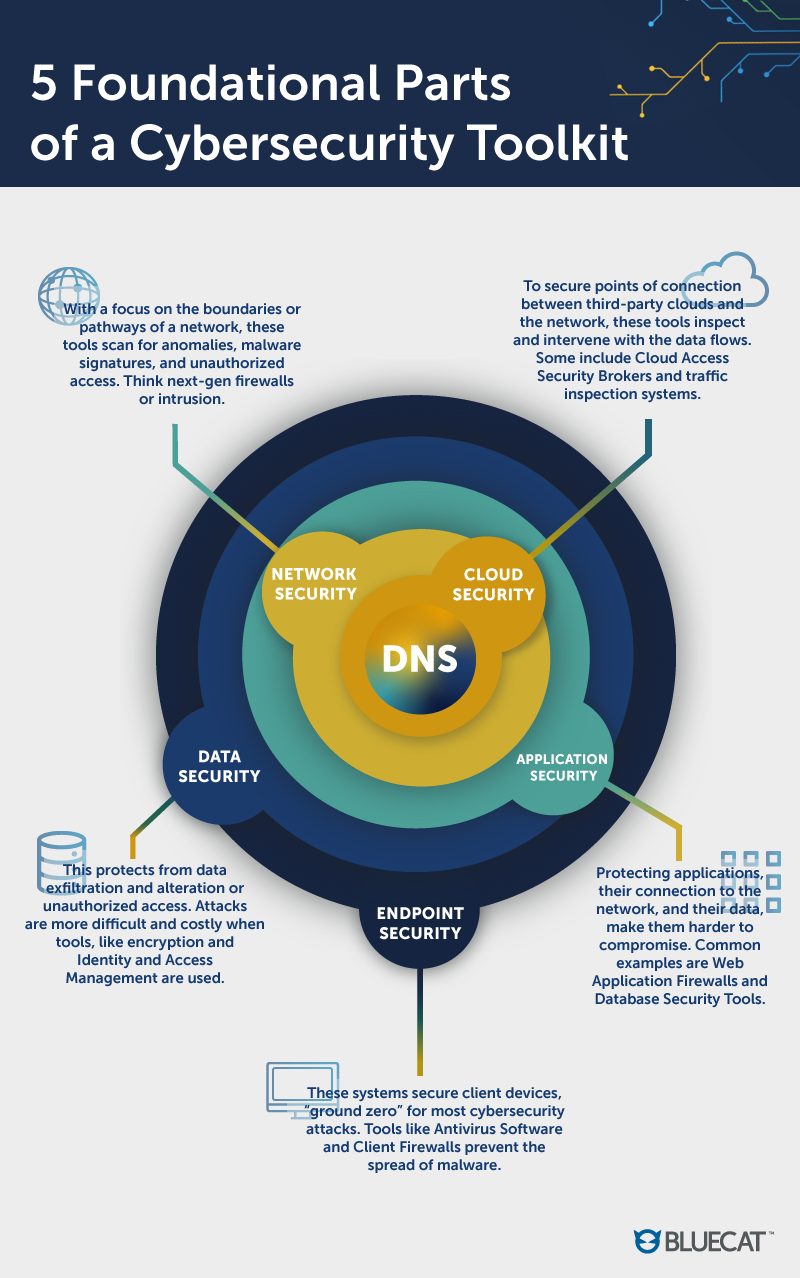
DNS in the Cybersecurity Stack
Malicious actors exploit DNS every day to establish command and control, navigate through networks, and exfiltrate data. Most security tools on the market today aren’t designed to capture and use DNS data for security purposes.
The good news is you can do something about it. This eBook will show you how DNS can enhance your existing security strategy.
You’ll discover:
- The role DNS can play in securing your enterprise
- How DNS can enhance your defense-in-depth strategy
- How DNS-level protections complement the other tools in your security stack
- How to leverage DNS to reduce your attack surface, prevent data exfiltration, and enhance your network visibility