Latest F5 Vulnerability Receives a CVSS 10 Severity Score
Have you been impacted by the latest F5 vulnerability that received a CVSS 10 severity score?
F5 Networks has published a security advisory on July 1, 2020 warning customers to patch a dangerous security flaw that is very likely to be exploited. CVE-2020-5902 was disclosed as a CVSS 10.0 rating vulnerability, in K52145254. This is classified as a critical rating that you should prioritize and fix as soon as possible.
According to F5 Networks, the “remote code execution” vulnerability allows for unauthenticated attackers, or authenticated users, with network access to the TMUI, through the BIG-IP management port and/or Self IPs, to execute arbitrary system commands, create or delete files, disable services, and/or execute arbitrary Java Code. This vulnerability may result in a complete system compromise.
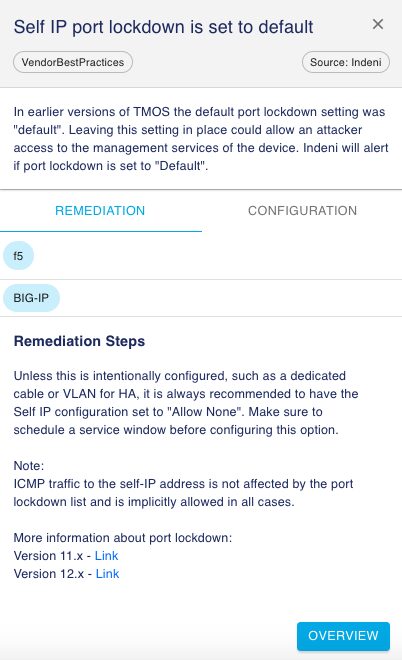
The Indeni “Self IP Port lockdown is set to default” Auto Detect Element will detect this issue.

Based on Indeni Insight, we have observed a total of 22 devices in our install base that have detected this vulnerability. 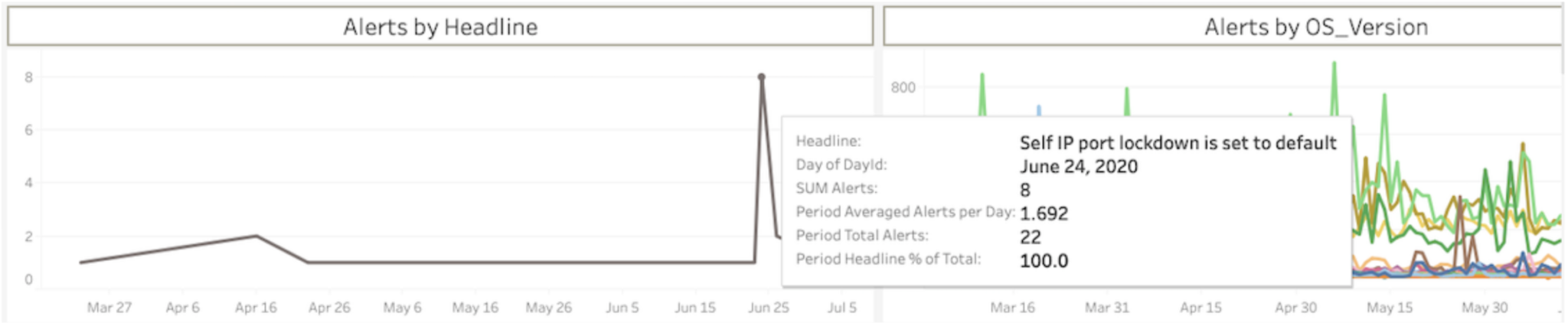
Given the rarity of 10 out of 10 score on the vulnerability severity scale, we encourage you to immediately obtain a list of potentially impacted devices and apply patches. Run a custom report by following these steps: 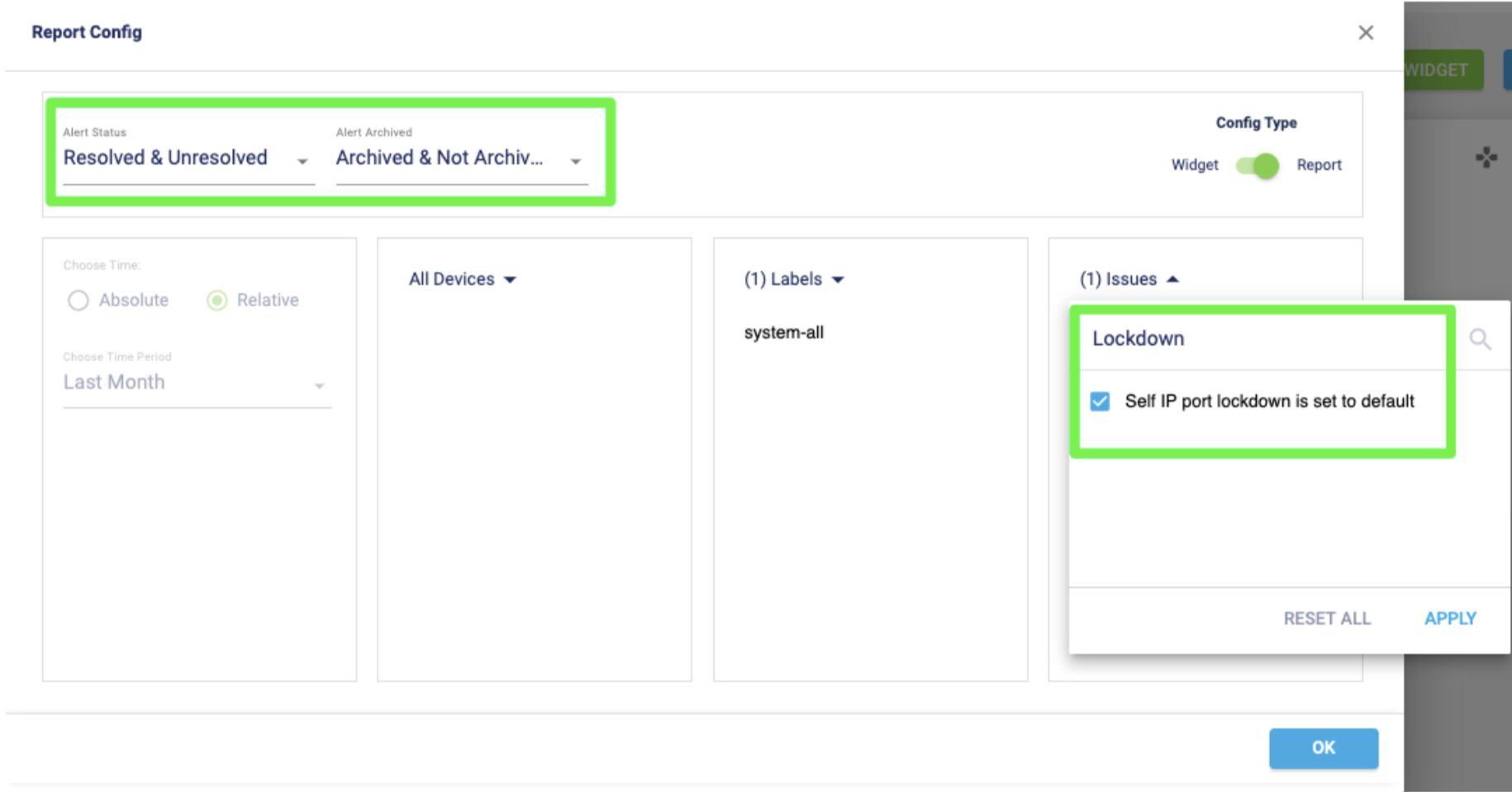
Go to Custom Report, create a new report by selecting the “Self IP port lockdown is set to default” issue for all the F5 devices. Be sure to include issues that have either been resolved or unresolved, archived or not archived.