Patch is available for the Critical Vulnerability (CVE-2020-2021) Impacting Palo Alto Firewalls
Another vulnerability bug with a CVSS 10 severity score was disclosed last week. Palo Alto Networks has published the security advisory PAN-148988 for a critical issue (CVE-2020-2021) affecting multiple versions of PAN-OS.
The US Cyber Command has issued a warning to the private and government sector last week to immediately patch the bug as they expected that nation-state-backed attackers would attempt to exploit the vulnerability.
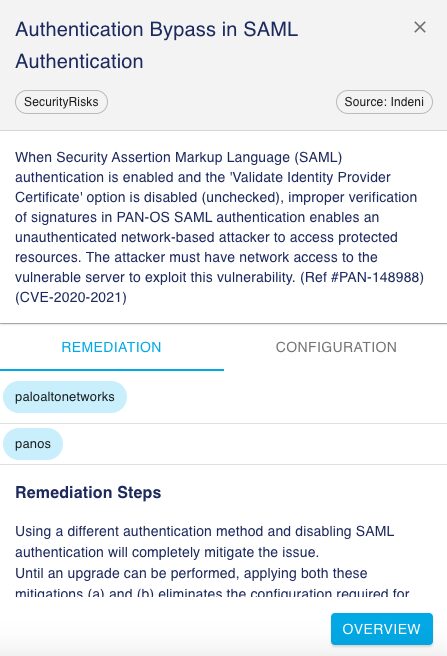
CVE-2020-2021 is an authentication bypass vulnerability that could allow unauthenticated attackers to access protected resources and gain control of the vulnerable devices. The vulnerability is exploitable only if the device is configured to use Security Assertion Markup Language (SAML) authentication and the “Validate Identity Provider Certificate” option is disabled (unchecked) in the SAML Identity Provider Server Profile.
Given this bug is 10 out of 10 on the vulnerability severity scale, we have accelerated the development of an Auto-Detect Element to detect this vulnerability advisory alert. 
The ADE will be released in 7.3.1 with general availability targeted for mid-July, 2020. We encourage you to take advantage of this new ADE. After the upgrade, obtain a list of potentially impacted devices. Run a custom report by following these steps:
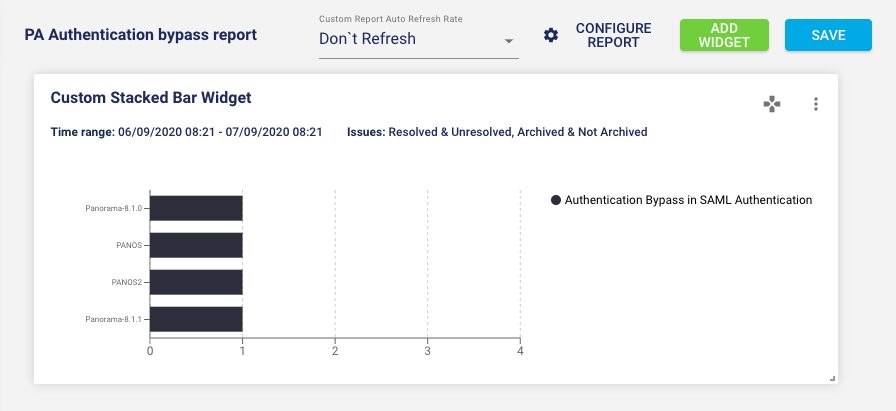
Go to Custom Report, create a new report by selecting the “Authentication Bypass in SAML authentication” issue for all the Palo Alto Networks devices.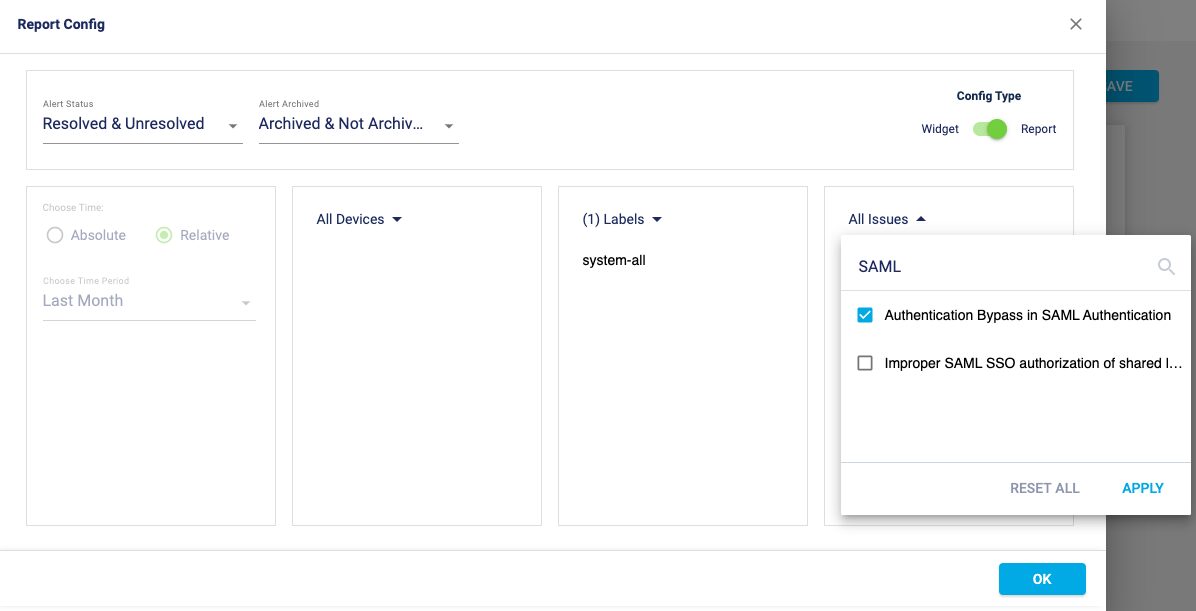
When I ran a report for our lab environment, I uncovered that some of our Palo Alto devices have been impacted by this vulnerability. Now it is time to patch these devices.