The top four DNS response codes and what they mean
Every DNS query gets a response. Stay on top of your network activity with BlueCat by understanding the four most common DNS response codes.
How well do you know your DNS response codes?
DNS queries and responses are fundamental to how the internet works. You want to visit a website, so you enter the URL in your browser. To get there, your device sends out a DNS query. And with the help of resolvers and DNS servers, that query gets a response.

DNS translates human-readable domain names that we remember (like bluecatnetworks.com) to the computer-friendly language of Internet Protocol (IP) addresses (like 104.239.197.100).
Whether you successfully make it to the website or not, every response you get includes a code. The four most common ones, returned with virtually all DNS queries, are NOERROR, NXDOMAIN, SERVFAIL, and REFUSED.
But do you really know what these common codes mean?
Response data, particularly when there’s a problem, can you help you troubleshoot or identify a security breach faster.
In this post, we’ll touch briefly on the full compilation of response codes, also known as DNS return codes. Then, we’ll examine each of the four most common codes in depth. Furthermore, we’ll touch on how BlueCat’s platform can help you better monitor and track your response codes and network activity.
The DNS response code compendium
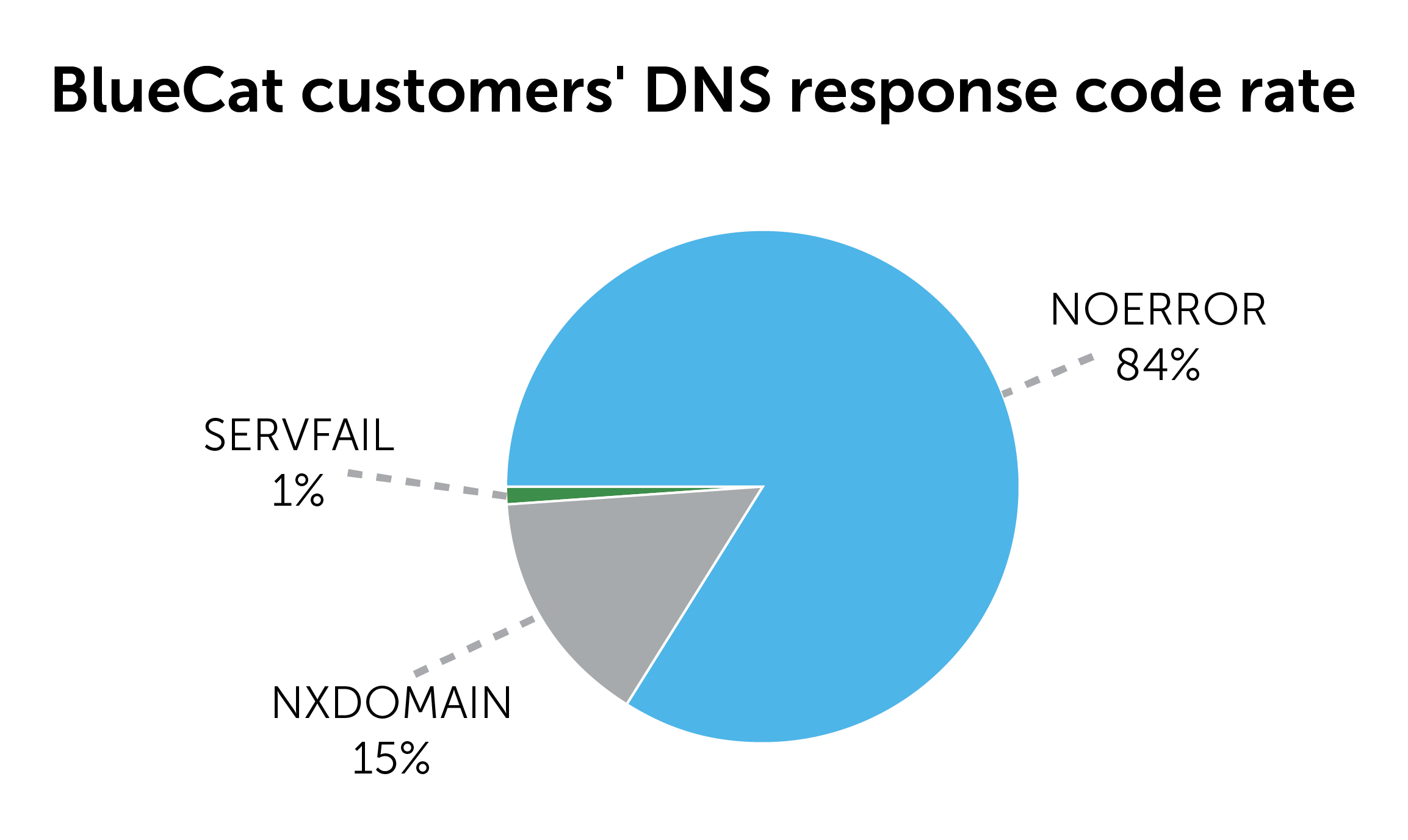
Officially, the full list of response codes numbers more than two dozen. Many are rare and only appear in very unique circumstances.
In surveys of our own customers, DNS queries successfully resolve about 84 percent of the time on their enterprise networks, generating the NOERROR code. Consequently, about 16 percent of DNS queries on their networks fail, resulting in one of the other three common codes.
More than half of IT managers say that their network teams are overwhelmed with DNS tickets and service requests. Download our Network Rising e-book to learn how you can automate the DNS routine and focus on strategic initiatives instead.
DNS response code NOERROR
The most common response
Around 80 to 90 percent of the time, NOERROR will be the response code you’ll see in your network logs.
Essentially, it means the DNS query got a valid response. It’s a way of saying everything was OK, there were no issues with the query. A user asked to go bluecatnetworks.com, and the resolver and DNS servers took it there.
Great! But…
It doesn’t always mean everything is perfect
Just because a NOERROR response was returned doesn’t mean a user on your network was taken to the website they specifically asked for.
For example, take a user who enters bluecat.ca. We’ve purchased that domain and want to be sure they’re redirected to bluecatnetworks.com instead. The user would get a successful NOERROR response code for going to bluecat.ca.
However, it would tell the user’s device, “Hey, actually, this is the domain you really want—bluecatnetworks.com—and here’s the IP address for that domain.”
Furthermore, if a user visits a website and the webserver fails or tells you you don’t have access, there would still be a NOERROR response in the DNS logs. Being able to access web servers, even for them to tell you that you don’t have access, still means that you resolved that domain to the IP address.
| DNS Response Code | Description |
|---|---|
| NOERROR | DNS query successfully completed |
| NXDOMAIN | DNS query failed because the domain name queried does not exist |
| SERVFAIL | DNS query failed because an answer cannot be given |
| REFUSED | DNS query failed because the server refused to answer due to policy |
DNS response code NXDOMAIN
Most of the remaining 10 to 15 percent of response codes received will be NXDOMAIN. The response that the server is sending back is, “Hey, you queried for this domain but that domain doesn’t exist or I don’t know that it exists.”
It’s essentially a way of saying that the query failed. We’ve got an entire blog post devoted to what an NXDOMAIN response code means for your network, but we’ll touch on a few basics here.
Possible meanings for NXDOMAIN
NXDOMAIN could mean:
- User error mistyping a domain name in a browser. Oops!
- A security control blocked the site a user was trying to reach.
- Some outdated code is trying to reach a website that no longer exists.
- A misconfigured application is querying for a misspelled domain.
- An indicator that the domain may be compromised or that malware exists.
A sign of a malware infection
Typically, malware will have instructions in its code to reach out to one or more domains. However, security experts will quickly find the domains that the malware is communicating with and blacklist them, rendering the malware useless. When infected devices can’t resolve to those now-blocked domains, NXDOMAIN responses will result.
To keep one step ahead, attackers often insert domain generation algorithms into their malware. These algorithms will generate a list of domains to query at any given time. Simply put, its code says, “if the malware is opened at this time, query this list of domains. And if it is opened at this other time, query this other list.”
Attackers will start to register those domains at the time that they need them. Out of 20 domains, maybe the malware hits one. So, for example, your network logs might show NXDOMAIN, NXDOMAIN, NXDOMAIN, and then NOERROR.
A burst of NXDOMAIN response codes is a flashing red light for your security team to investigate the possible presence of malware on the network.
DNS response code SERVFAIL
A SERVFAIL response comes back about one percent of the time. While NXDOMAIN is the DNS server telling you that the domain doesn’t exist, a SERVFAIL is the DNS server telling you, “Hey, I can’t give you the answer for that query.”
It could be that there’s a technical problem with the DNS servers. It can also mean that a security control on your network, such as a firewall or intrusion prevention system, is blocking a user from going to that domain.
It’s essentially saying, nope, I’m not giving you a response for that.
Much like NXDOMAIN, excessive SERVFAIL responses warrant further examination. An automatic application with stale configurations could be to blame. Domains that receive SERVFAIL responses could also be investigated for malicious activity.
DNS response code REFUSED
REFUSED results when the DNS name server refuses to perform operations for policy reasons. For example, a particular device may be blocked if it is abusing the nameserver. Or, a particular operation, such as a zone transfer, might be forbidden.
For example, a zone transfer is a way of replicating DNS configuration information across multiple DNS servers for load balancing or backup. Usually, only an authorized person can complete a zone transfer. If a user tries to initiate one but they’re not authorized, then this would be the response code they would get.
BlueCat can help you manage DNS response codes
The BlueCat platform provides a user-friendly interface to see, sort, filter, and track every DNS query and response on your enterprise network. You, too, can make pie charts to see the breakdown of DNS response codes in your environment.
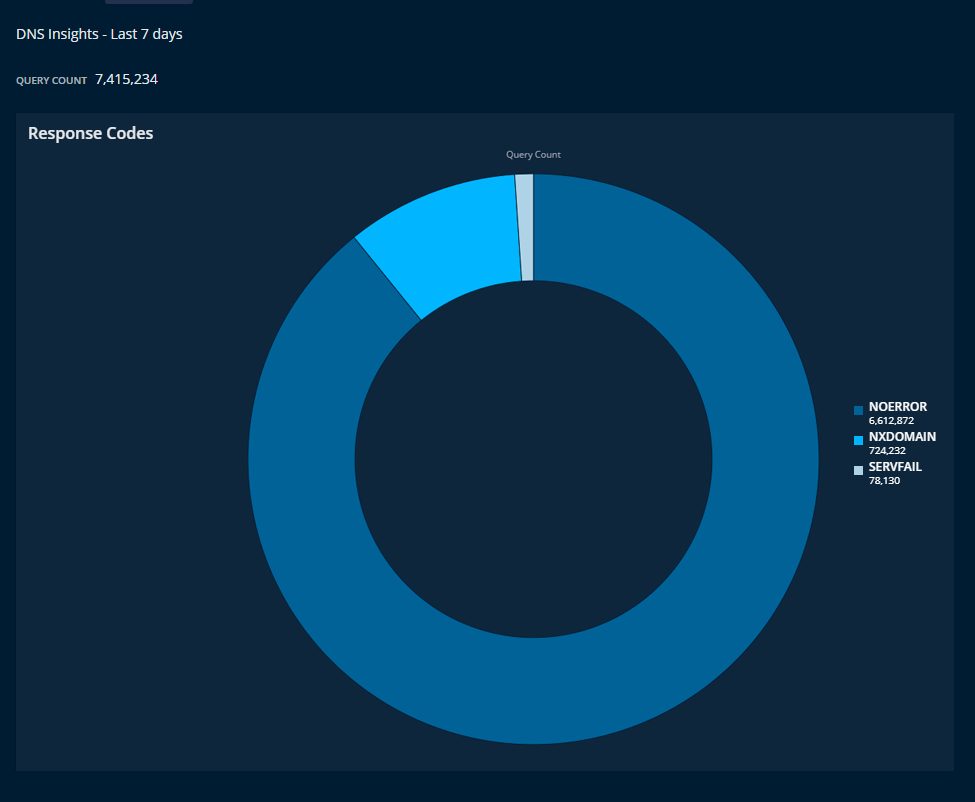
BlueCat’s comprehensive approach to DNS management provides a straightforward and all-encompassing way to see when questionable patterns are emerging on your network. Furthermore, BlueCat makes it easy to set policies that monitor and identify suspicious activity and prevent access to malicious domains.





