Comparing indeni and Check Point’s SmartWorkflow and Compliance blades
Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
The summary:
SmartWorkflow helps you track your rulebase, the Compliance blade helps you identify specific configurations that are not in compliance with known security regulations. Both exist in order to ensure your firewall configuration is secure and so, your network is secure. indeni’s role is to make sure your firewall works – performance, log flow, routing, kernel parameters, SIC connectivity, licensing, contracts, etc.
Therefore, indeni is an amazing fit with your SmartWorkflow and Compliance blades.
The longer version:

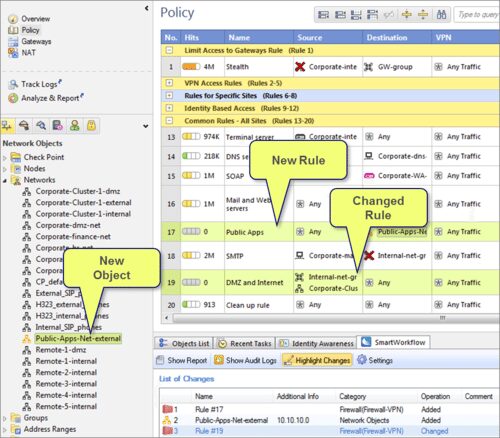
SmartWorkflow:
From checkpoint.com: “The Check Point SmartWorkflow Software Blade provides a seamless and automated process for policy change management that helps administrators reduce errors and enhance compliance. Enforce a formal process for editing, reviewing, approving and auditing policy changes from a single console, for one-stop, total policy lifecycle management.”
What that means is that you have a way of tracking changes made to the firewall rulebase (policy) to ensure that these changes are being done in the correct way. The reason for doing this is simple: the firewall is the gatekeeper to your network and you want to make sure that the traffic it lets in is the one you want it to.
indeni has no ability to track the firewall policy or identify changes to the rules. We have specifically refrained from doing that as we know the market has very capable solutions for dealing with this challenge – some provided by the firewall manufacturer (like SmartWorkflow) and some by third parties.
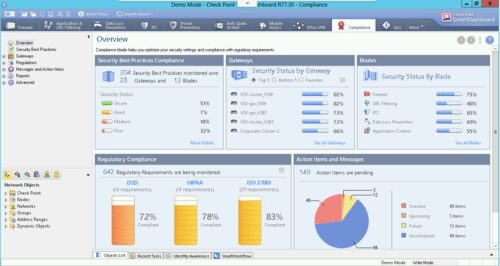
Compliance Blade:
From checkpoint.com: “The Check Point Compliance Software Blade monitors your management, Software Blades and security gateways to constantly validate that your Check Point environment is configured in the best way possible. The Check Point Compliance Software Blade provides 24/7 security monitoring, security alerts on policy violations, and out-of-the-box audit reports.”
So the compliance blade is there to make sure you are in compliance with the variety of regulations that you must adhere to – DSD, HIPAA, PCI DSS, etc. Each of those regulations lists a set of requirements that must be followed on your firewalls – from ensuring stateful inspection is used to how connections are timed out. Each regulation has a different set and there’s some overlap between them.
indeni focuses on the operational health of the firewall, as well as OS-level configurations that need to be done for compliance purposes (like what users are defined). Therefore, it augments the compliance blade by ensuring that the firewall isn’t only secure and following security best practices, but also alive and kicking.
The bottom line:
indeni is a great fit with the SmartWorkflow and Compliance blades. It ensures that your security meets standards and regulations and your network is up and running without issues. With indeni, you can find all of the issues listed below, which you cannot find with the SmartWorkflow and Compliance blades:
- Gateway cannot access certificate authority
- Policy installation resulted in high CPU load cluster may failover
- Firewall log file increase rate critical – possible connectivity loss to log server
- Firewall kernel table limit approaching or reached
- ClusterXL member is in a critical state
- Cluster member down due to NIC error
- Some received packets have been dropped by NIC (SA#24915)
- High memory usage
- DNS servers configured but responding too slowly
- Use of NTP servers configured but not operational
- Firewall Connection Table Limit Approaching or Reached
- A NIC has failed recently (SA#24915)
- RX traffic drastically reduced post fail over possible ARP issue
- Two cluster members differ in their routing tables (SA#66322)
- DNS server resolution test failed
- NAT connections (fwx_alloc) table limit approaching or reached
- Errors have been found in packets transmitted by NIC (SA#24915)
- ARP table is approaching its limits (SA#25890)
- VPN gateway is dropping unexpected packets (SA#22255)
- NIC duplex set to half with speed of 10mbps or 100mbps (SA#24967)



