Top Check Point Support Features For 2022

After another year of remote working and virtual events, we have learned new ways to drive innovation and manage remote workforces. This year, CPX 360 is once again a virtual event. With CPX 360 just a couple of weeks away, we would like to provide an update and highlight a few of the most popular automation elements.
#1 Comprehensive Maestro support
While customers are taking advantage of Check Point Maestro Hyperscale Network Security to scale out their security infrastructure, they demand infrastructure automation for this new architecture.
We began rolling out support for Maestro in late 2019. Since then, we have been actively developing new features to support Maestro. In 7.8, we added support for multiple security groups. Today, we have hundreds of Auto-Detect Elements for Maestro orchestrators and Maestro secure gateways. The automation spans a wide variety of use cases, all with problem avoidance a primary goal.
- In-depth visibility with proactive alerting
- High availability readiness
- Security risks identification
- Best practices validation
- Organization standards enforcement
- Ongoing maintenance
#2 CloudGuard Network Security Support for Hybrid Clouds
The COVID-19 pandemic has turned the world upside down and forced a rapid acceleration to cloud adoption. For many organizations, hybrid cloud is the new normal. In 2021, we saw an uptake of CloudGuard Network Security managed by Indeni.
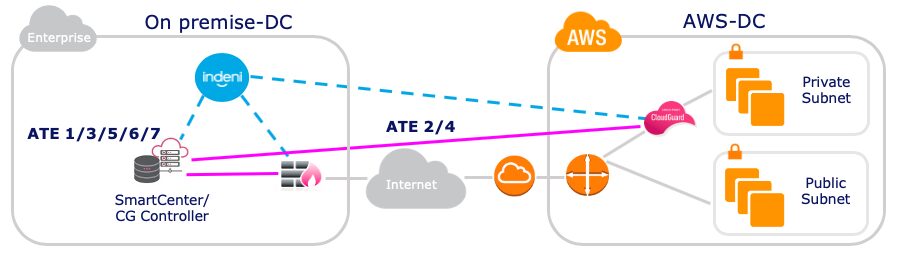
Indeni is typically deployed on premises. In this example, we are showing Check Point CloudGuard Network Security deployed in AWS and Check Point secure gateways deployed on premise. Indeni interacts with CloudGuard Network security in public clouds. It also interacts with Check Point management servers, CloudGuard controllers, and secure gateways in traditional private data centers.
CloudGuard Network Security enjoys the same level of support as other on-premise secure gateways. In addition, we have developed specific Auto-Detect elements to detect connectivity failure, policy installation failure and update failure between CloudGuard controller and CloudGuard instances.
- ATE 1: Ensure CloudGuard Controller is running as a process on the management server.
- ATE 2: Check connectivity between CloudGuard Controller and AWS-DC.
- ATE 3: Check errors on Data Center scanner.
- ATE 4: Check the connection between CloudGuard Controller and CloudGuard instances.
- ATE 5: Check if Identity Awareness web API is running.
- ATE 6: Check if CloudGuard Controller is updating CloudGuard instances.
- ATE 7: Check for imported objects from the Data Center.
CloudGuard Network Security key capabilities:
- Ensure CloudGuard Network Security conforms to the organization’s golden configuration.
- Ensure CloudGuard Network Security can connect to its controller on-premises to get up-to-date policies, through early detection of problems that might degrade the VPN tunnel.
- Analyze secure gateway metrics continuously to track their health and suggest mitigations for risk of failures.
- Ensure CloudGuard Network Security is following Check Point recommended best practices similar to the on-premise secure gateways.
- Help IT teams enforce compliance to a defined set of internal and external policies.
#3 Check Point Device Hardening
With cyber attacks on the rise, enterprises need to be hyper-vigilant about how they secure their firewalls. Device hardening is necessary to reduce the attack surface. In 7.6 & 7.7, we added several security controls based on the Center for Internet Security (CIS) benchmark for Check Point devices. Organizations are adopting these best practices to improve their security, compliance programs and posture.
#4 Check Point SecureXL Enhancements
SecureXL is an acceleration solution that maximizes the performance of the Check Point firewall. When SecureXL is disabled, service can be severely impacted.
Prior to 7.6, we only collected the global status of SecureXL and sent notifications based on enable/disable status. In 7.6, we added several new alerts if SecureXL is disabled by the firewall as a result of certain conditions. The support includes the new templates that were available in GAiA R80.10 or later.
- SecureXL Accept template disabled.
- SecureXL Drop template disabled.
- SecureXL NAT template disabled.
- SecureXL No Match Ranges (NMR) template disabled.
- SecureXL No Match Time (NMT) template disabled.
#5 Unique Routing Protocols Coverage
Our support for routing protocols has always been popular among our customers. My favourite is the check for synchronized static routes among the secure gateways in a cluster. This is something people often forget to add to the standby or backup secure gateway when a new static route is needed. Sadly, no one notices the missing static route until a switchover occurs when you actually need it!
We also support dynamic routing protocols like BGP and OSPF. They are very popular because conventional monitoring tools do not typically support routing protocols. Besides, detecting BGP issues is more than just monitoring the peer state. Recently, we ran into a tricky issue where the peer state is established but the number of active routes is zero resulting in outages. In 7.8, we added a new Auto-Detect element to look for the zero active route condition on active members in a cluster. Another abnormal situation is hidden routes. Sometimes, routes are marked as hidden. This means the routing process learns the routes from the BGP peer, but it is not passing this information to the routing table of the secure gateway. In 7.8, we added a new Auto-Detect Element to detect the BGP hidden route condition. Learn more about our BGP support in this blog.
There, you have our top picks of Check Point support for 2022. If you are planning to attend CPX 360, drop by to talk to us about your Check Point secure gateway needs.