Results are in! F5 Agility 2018 Attendee Survey

As a crowdsourced network automation platform, Indeni is constantly learning and improving from the IT community. It comes as no surprise that research was the main focus of Indeni’s lively booth at F5 Agility 2018 conference. Indeni’s booth visitors were invited to answer a brief survey, earning them a complimentary reward within the Indeni Crowd Learning Path. Just shy of 100 attendees answered the survey, providing the Indeni community with even more data regarding Network & Security Automation Trends in 2018.
Let’s dive in, shall we? In regards to years of experience with F5 devices, it is amazing to see that 80% of attendees had over three years of experience under their belt. That is a lot of expertise compiled into one survey. It makes sense we would see many seasoned F5 experts representing their companies at Agility.
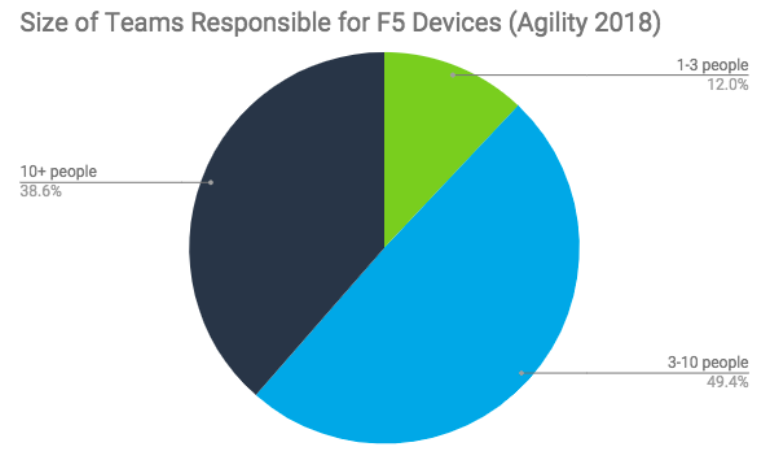
The second survey question was simple: “how many people are on the networking team?”. Most attendees reported having a team of three to ten people. When asked more questions about their team, like how many people are responsible for the F5 devices, the vast majority said “me, myself, and I!”. It became very apparent that the ratio of complex devices in an environment to the number of people managing them is becoming an inhibiting factor to productivity. This is in-line with findings from our Network & Security Automation Trends Report where over half of survey participants said they lacked the talent to support existing network management responsibilities.
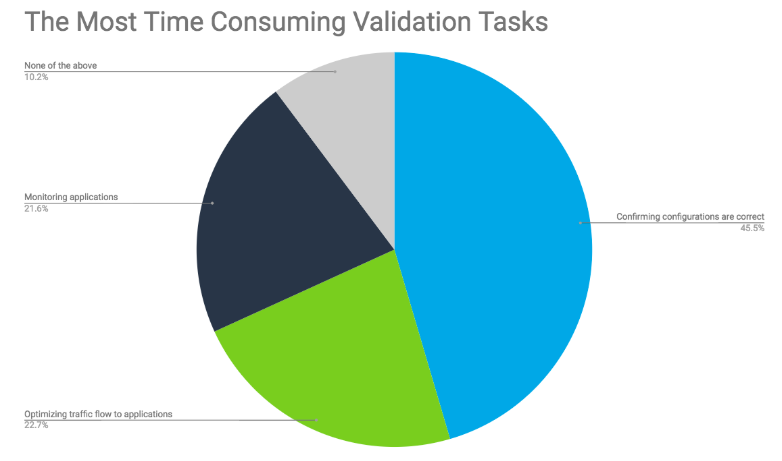
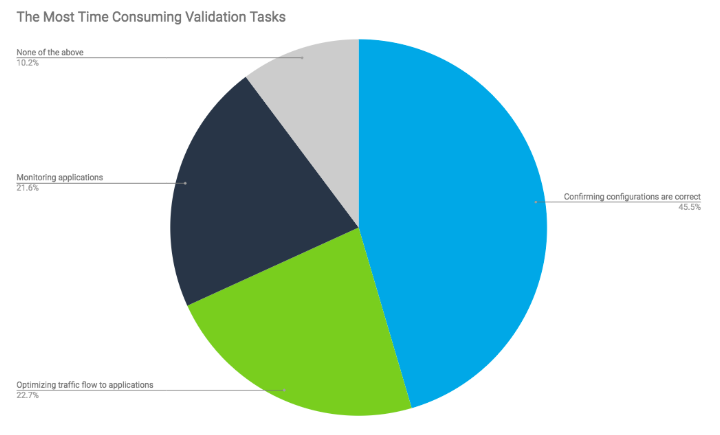
Last but not least, the onsite survey asked which validation tasks take up the most time. Of the four options, 46% of respondents reported spending too much time confirming configurations are correct. Cluster configurations and other high availability configurations are always at the top of the head-ache list. After that, it was pretty evenly split with almost a quarter of participants claiming to have issues with either monitoring applications and optimizing traffic flow to applications. Indeni recommends checking out the following resources to alleviate traffic flow and application issues:
- How to Avoid F5 LTM SNAT Pool Exhaustion
- 7 Ways to Manage F5 LTM Traffic With Profiles
- F5 Networks Best Practices for Application Monitoring
- How to monitor F5 devices – SNMP vs API vs SSH
Calling All F5 Enthusiasts – Ask The Expert
Take the opportunity to ask a seasoned expert, @Patrik_Jonsson, anything regarding F5 LTM! Patrik is an Indeni Knowledge Expert (IKE) and has been awarded Indeni Crowd Member of the Month in addition to earning the F5 DevCentral MVP award four years in a row.
Ask the Expert Details:
- Date: August 27, 2018 – September 2, 2018
- Location: Indeni Crowd Forum
Benefit from Patrik’s knowledge in these ways:
- Get tips, tricks and resolution steps for F5 LTM related issues
- Clarify Indeni’s abilities to automate daily repetitive tasks for F5 devices
- Ask about Indeni plans to improve F5 coverage for customers and end users
- Propose new metrics and scripts for F5 on Indeni
