Top 5 Automation for FortiGate Firewalls
Authors: Vasilis Bouloukos & Ulrica de Fort-Menares
Keep your FortiGate firewalls running smoothly and free from zero day attacks, here’s our list of the most popular automation elements among our customers. Indeni can take a few things off your plate with our Auto-Detect elements (ADE). We have approximately 70 automation elements to help you proactively manage your firewalls, automate mundane tasks and keep you out of trouble. When issues occur, you can count on the recommended step-by-step remediations built by certified Network Security Experts to help you address issues quickly.
#1 High Availability Readiness
Our support for high availability (HA) readiness has always been popular among our customers. HA provides resilience not only in the event of a cluster member failing, but also allows for firmware updates without any downtime. FortiGate Clustering Protocol is the most commonly used HA solution. It allows two or more FortiGates of the same type and model to be put into a cluster in Active-Passive (A-P) or Active-Active (A-A) mode. A-P mode provides redundancy by having one or more FortiGates in hot standby in case the primary device experiences a detectable failure. A-A mode allows traffic to be balanced across the units in the cluster for scanning purposes, and also performs failover.
High Availability Capabilities:
- Alert if one or more firewalls in a firewall cluster experiences problems
- Cluster configuration out of synchronization issues. This is the most common issue with HA. Indeni can identify proactively these issues including checks for sync status, debug zone and configuration file checksum
- Identify cluster heartbeat interface problems by tracking link status and bandwidth utilization
- Identify the status of critical HA monitor links
- Alert if the number of operational heartbeat links are less than the recommended two HA links (no redundancy)
- Identify HA heartbeat interfaces do not have different priorities
- Monitor the uptime of the HA cluster. Any unexpected low uptime should be troubleshot and investigated
- Analyze if HA features configuration settings are activated as per below:
- Session-pickup: The new primary unit uses its synchronized session table to resume all TCP sessions that were being processed by the former primary unit with only minimal interruption.
- Session-override: Always renegotiate when an event occurs that affects primary unit selection
#2 Critical Services
Firewalls depend on many external security services to get dynamic content updates for the latest threat intelligence. Services include AV engine, Virus definition,malware prevention, security rating, intrusion prevention attack engine, URL filtering, etc.
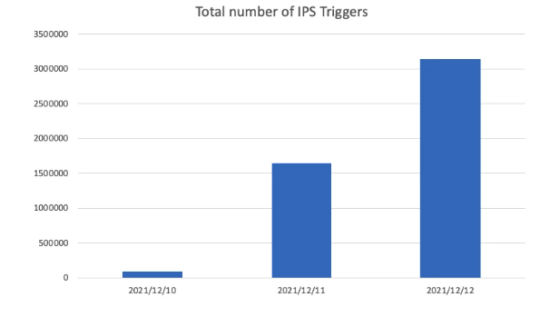
To get the most protection from your firewall, you need to verify the FortiGuard services last update status and versions. A timely update of IPS signatures is the best protection mechanism from zero day attacks. The recent Log4j vulnerability (Log4Shell) is a great example where we saw the exponential growth of IPS triggered attacks shortly after the announcement of the vulnerability. Indeni continuously monitors the last update status of all the UTM features to ensure timely updates.
Source: https://www.fortinet.com/blog/psirt-blogs/apache-log4j-vulnerability
#3 Tackling Conserve mode
A FortiGate goes into the “conserve mode” as a self protection measure when a memory shortage appears on the system. When entering conserve mode the FortiGate activates protection measures in order to recover memory space. Memory shortages are the most commonly found problems with FortiGate. The FortiGate enters conserve mode when memory usage reaches the red threshold (default 88% memory used). If memory usage reaches the extreme threshold (95% memory used), additional new sessions will be dropped. When used memory goes below the green threshold, the kernel releases the conserve mode state.
Several FortiOS releases have encountered issues with memory leaks. After a certain period of time, the memory utilization increases at a level where it has severe service impact. Fortinet TAC many times proposed to proceed with a reload. Indeni can proactively inform the administrator if the Fortigate enters a conserve mode state and the threshold level, thereby preventing a reload. Indeni monitors and analyzes key metrics which could be the root cause of a memory leak and high memory utilization. This includes the top 5 processes:
- consuming the highest memory
- with the most socket memory
- with the most active file descriptors
Detailed Remediation steps are provided for each alert to isolate and resolve this critical issue.
#4 Session Status & Statistics
Getting in-depth session statistics information provides an important picture of what is happening on your system. This is particularly useful if you are experiencing memory issues or if you are close to the hardware session limits of the FortiGate. For instance, if the number of ephemeral sessions is high, not only do you have a very busy device, you may also run into memory issues. A high number of ephemeral sessions may indicate a DoS attack is underway.
Indeni alerts if following conditions are detected:
- Sessions clash causing service degradation
Session clash appears when a new session is created but a conflicting similar session (same tuple) already exists. When that happens, the old session will be deleted and replaced by the new one. The consequence is that it may cause re-transmissions.
- Kernel sessions are deleted due to lack of memory or resources
- Sessions have been dropped due to interface down status or maximum limit reached
- High number of ephemeral sessions resulting in memory shortages
In addition to these alerts, we collect in-depth session information about the system’s state. This includes useful information such as total number of current sessions and the current number of created sessions per second.
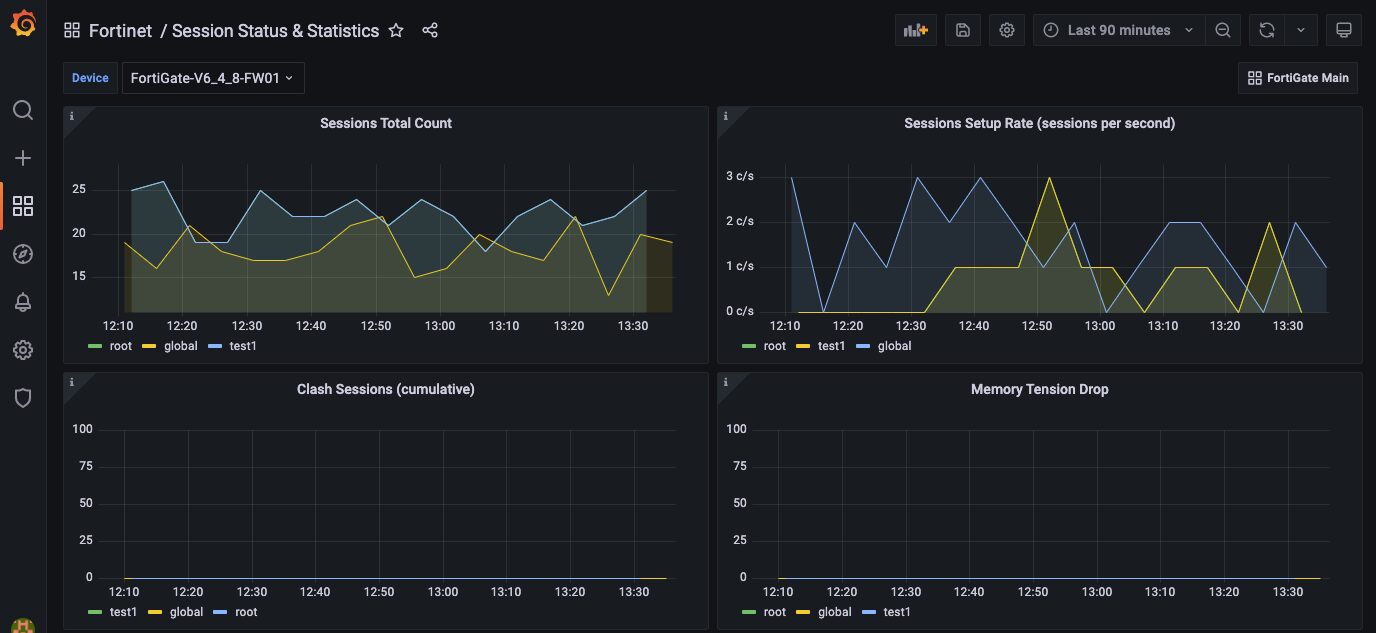
We also collect the current number of sessions in removable state. A session is in removable state when the total number of sessions reaches a certain limit. You can also see the number of times a request was made to flush firewall sessions matching a specific criteria. It is useful to know how many times the more expensive flush was done.
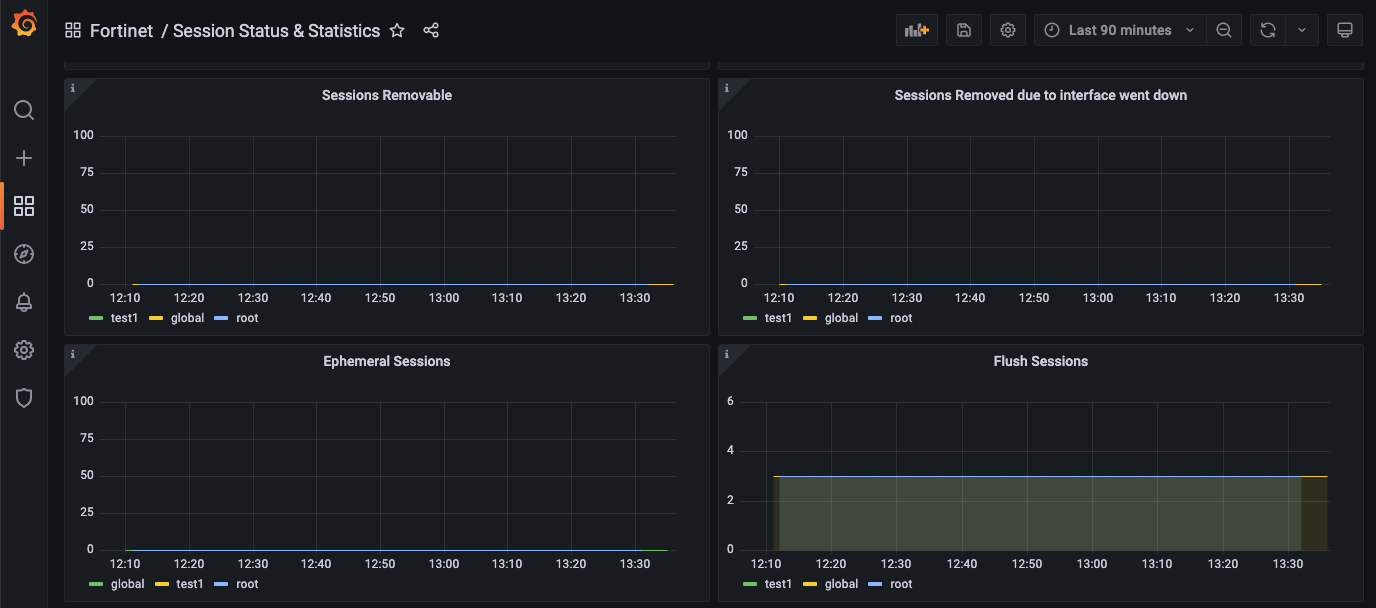
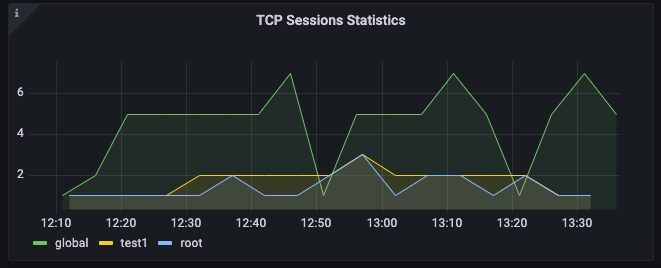
We capture statistics about the current number of TCP sessions in various states such as NONE, ESTABLISHED, CLOSE, CLOSE_WAIT. A high number of sessions in CLOSE or CLOSE_WAIT state could be an indication of attacks.
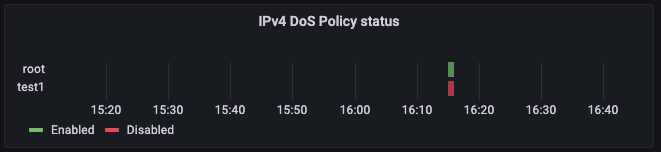
#5 DoS Policy Status
Separate recent reports by Cloudflare and Kaspersky Lab found that DDoS attacks have increased dramatically since the beginning of Russia’s invasion of Ukraine. Not only did the number of attacks grow significantly, the duration of these attacks grew notably. With DDoS attacks a growing threat, you want to enable IPv4 DoS policy as the first layer of protection against DDoS attacks.
A Denial of Service (DoS) policy examines network traffic arriving at a FortiGate interface for anomalous patterns, which usually indicates an attack. A DoS policy prevents attackers from flooding your network. Indeni generates an alert if the DoS policy is not enabled.
Try Indeni
There, you have our top picks for FortiGate firewalls. You have made a big investment in security with your firewall and all the features it has enabled. Let us help you make the most out of your security infrastructure. With Indeni, you can quickly get conclusions, not conjecture from your monitoring tool. For a complete list of Auto-Detect Elements, click download.
If you are new to Indeni, we encourage you to take Indeni for a spin and try out our automation capabilities.