Firewall Most Requested Change – Copy Rule on one Host to Another Host

Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog

Oftentimes, firewall administrators get requests either to change something or add up a couple of rules to help get things moving around the network. The frequency and dynamics of composition of these requests vary from one company to another.
As companies adhere to security standards, networks are going to follow the path of least privilege or simply put, giving out access only to those who need it blocking everything else otherwise. Due to this concept, firewall administrators have been brought to the forefront of security battlegrounds. Blocking the networks that don’t need to talk to each other or at least when no one tells them they should be.
However, when the need arises, say a new server gets stood up due to expansion, or an employee being pulled to a new role that requires additional access rights, firewall administrators get thrown into the mix. They go back to the drawing board and consider every possible way to put a hole in the bricks they’ve set up to secure the network.
Some requests would be as detailed as specifying the source and destination addresses and ports, even sharing details about the project they are working on and the expected traffic flows. Most, others are vague like where the most requested change goes – mimic the policies for this host to that.
Here are some copy hacks that firewall administrators can consider for such requests. Note that for this article, Palo Alto firewall is being used as the sample environment but most other firewall share the same functionality as this would not involve any patented technology or any wizarding tricks.
Copy hack #1: Objects
Objects are mainly used to identify resources such as an IP address, service port, application, and more depending on the firewall platform. In some cases, objects can come in groups and if fully utilized will be a great tool for copy requests.
Note: this hack will only be reliable if pertaining to the inheritance of certain access from a server that is member to a group of other servers with the same level of access. If the goal is to copy the level of access of one server alone, do not use this method.
- On a Palo Alto firewall, browse to the objects tab. Here you can define IP addresses, service ports, applications, and more.

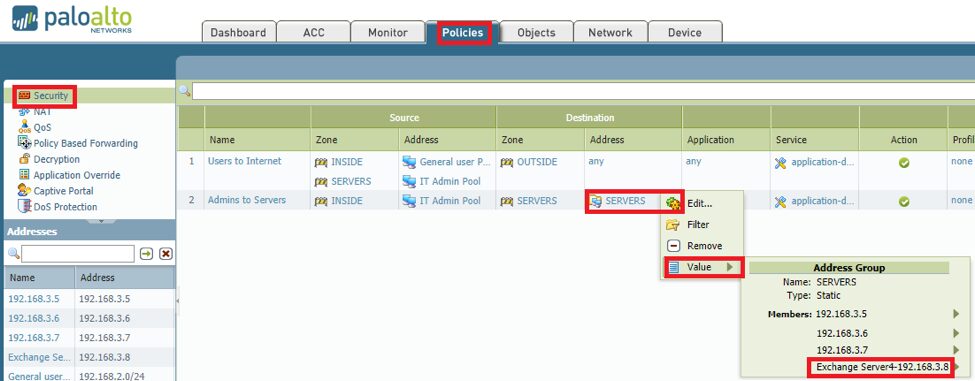
- Go to the Address Groups selection and select the existing group you need to change or where the certain server you need to copy into is a member of.

- Click on Add and define the IP address of the new server. It would help to add some descriptive notations on the naming part so as not to confuse and for easier management. Hit OK.

- Verify that the new IP was included on policies pertaining to the group – ‘SERVERS’. Navigate to the Policies tab, click on the drop down arrow beside the address group you want to verify, in this case ‘SERVERS’, then hover the pointer to the value option. This will show all members of that group so you can verify if the new server indeed has been added and inherited the corresponding policy.
Copy hack #2: Section search
The good old section search as many Palo Alto firewall administrators would know is still as reliable. The same as how you filter logs on the traffic log section, the section search serves the same purpose on any other tabs of the Palo Alto firewall GUI. However, you won’t have the same flexibility as in the monitor tab where you can do some Boolean expressions to filter the logs. Section search only do a string match to the configuration items on the specific tab you are in.
- On the Policies tab, locate the section search bar on the upper portion beside the magnifying glass. Type the IP address of the host you want to replicate access.
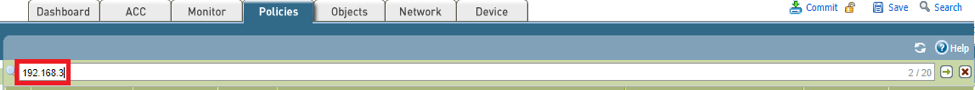
- Notice that there is a hit count on the far right portion of the search bar when you hit search. You can use this hit count to verify how many configuration discrepancies you need to look into for the copy request. Once you did the necessary changes, it pays to go back here and do a quick check if the hit count of the new IP is equal to the hit count of the IP you are copying.

Copy hack #3: Global Find
Global Find in Palo Alto firewalls is a way to find the presence of any string into the entirety of the configuration database. This is the smaller search box on the top right corner of the web interface. While there is the section search bar that will give the same output but only to the particular section that you are in, the Global Find option gives better visibility on what policies are currently applied to a particular host for replication purposes.
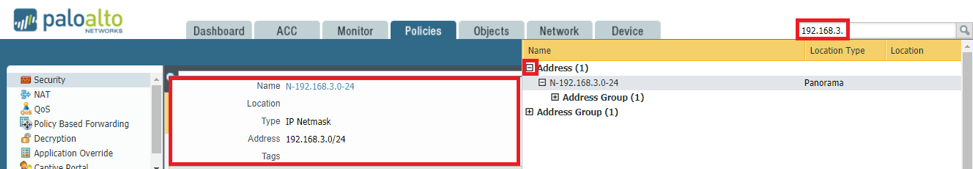
- Go to the Global Find box located on the upper right corner of the Palo Alto firewall GUI. Type the IP address of the host you need to replicate and hit the magnifying glass button to search. All configuration items that matches the input string will show in a neatly sectioned list.

- From the list, click the plus (+) button to show the specific configuration input. You can then determine which items you need to change to satisfy the rule replication request. The most important items are – Address Group, Policy Based Forwarding Rule, and Security Rule.
That wraps it up! There are many ways to accomplish our goals and if it gets the job done, then do it. Be sure to keep in mind that the quality of your work should never be compromised though; it should at least increase your efficiency.
Thanks to Ralph Masajo for his contribution to our blog.



