Fortinet FortiGate Automation
FortiOS 6.0 introduces Automation Stitches as part of the Security Fabric. Automation Stitches can be used to automate certain actions in response to certain triggers. In addition, Automation Stitches can automate activities between the different components in the Fortinet Security Fabric. This new feature can drastically decrease the response times to security events, operation tasks, and network problems.
This article is a part of the series of Fortinet technical articles. In brief, the main configuration components of an automation stitch (Trigger and Action) are reviewed. The configuration methodology is presented and tested via indicative configuration examples. Finally, we will discuss how Indeni can significantly simplify operations and eliminate service outages in parallel with the deployment of automation to the Fortinet Security Fabric.
Are you a network administrator, system engineer, software engineer, Indeni Knowledge Expert (IKEs), or tech geek? If yes, then read on! This article is for you!
FortiGate Automation Stitches Methodology
An automation stitch consists of two main tasks, the trigger and the actions. The trigger is the condition or event on the FortiGate that activates the action. For instance, a trigger could be a specific log message such as BGP neighbor status change. The action is what the FortiGate does in response to a trigger, e.g. send an email message or run a command script. Finally, it should be considered that automation stitches can only be created on the root FortiGate in a Security Fabric.
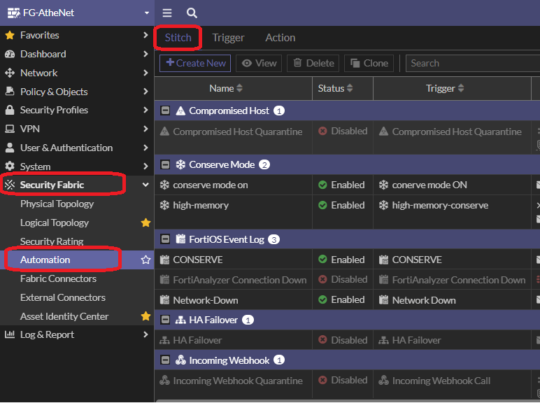
Creating Automation Stitches
The creation of an automation stitch requires a trigger event as well as a response action or actions to be selected. Most automation stitches support the option to be triggered with a false positive, e.g. create a fake log message to be able to simulate and test it. The following default automation stitches are included in FortiOS:
- Compromised Host Quarantine
- Incoming Webhook Quarantine
- HA Failover
- Network Down
- Reboot
- FortiAnalyzer Connection Down
- License Expired Notification
- Security Rating Notification
Create an automation stitch:
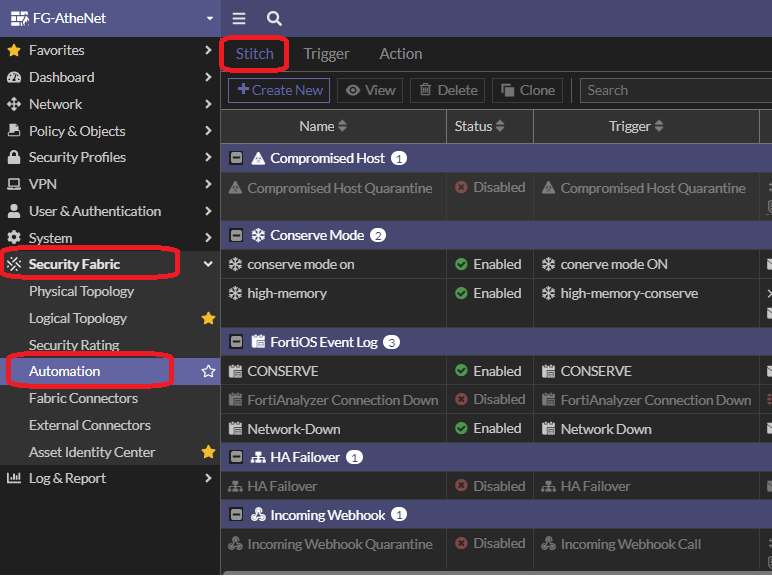
Automation stitches have the option to delay an action after the previous action is complete. Executing the next action can be delayed by up to 3600 seconds (one hour).
Triggers
A large number of available pre-configured triggers is supported. List of security fabric triggers:re included in FortiOS:
- Compromised Host
- Security Rating Summary
- FortiAnalyzer Event Handler
- Fabric Connector Event
- FortiGate Cloud-Based IOC
Create a trigger:
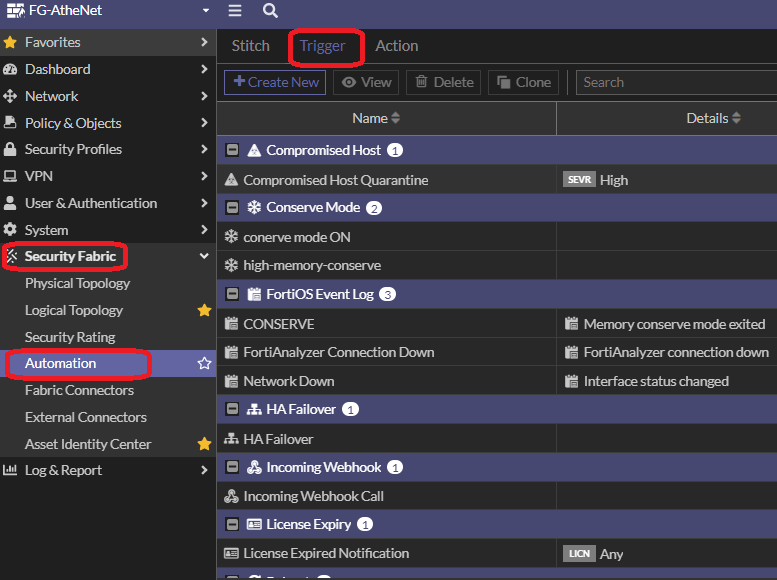
List of system triggers:
- Reboot
- HA Failover
- Conserve Mode
- Configuration Change
- License Expiry
- AV & IPS DB Update
- High CPU
Finally, triggers can be set also for the next cases. In particular, the FortiOS Log Event is common since multiple event log id can be used, e.g. OSPF status change or link status log messages.
- FortiOS Event Log
- Incoming Webhook
- Schedule (very helpful for common operation tasks like configuration backups)
Actions
Multiple actions can be configured for an automation stitch.
Available actions for the Security category:
- Access Layer Quarantine
- FortiClient Quarantine
- FortiNAC Quarantine
- VMware NSX Security Tag
- IP Ban
Menu to create an action:
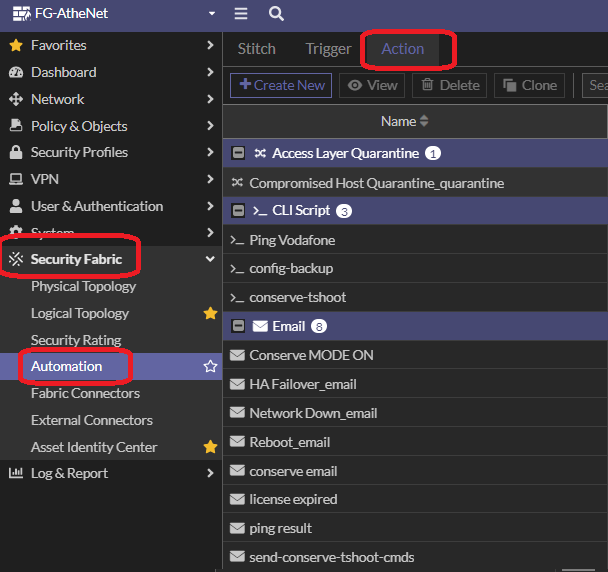
Available actions for the notification category:
- FortiExplorer Notification
- Slack Notification
- Microsoft Teams Notification
Available actions for the cloud compute category:
- AWS Lambda
- Azure Function
- Google Cloud Function
- AliCloud Function
You can also run a CLI script as the next action when an event is triggered:
- CLI Script
- Webhook
- Alert
- Disable SSID
Automation Script Examples
Let’s see how we can configure a few useful automation scripts on a FortiGate.
Note: the latest FortiOS release 7.0.3 is used for the configuration and testing in the lab. The menu to configure automation on the FortiGate is different in the previous releases which support the automation feature (after 6.0).
Schedule daily configuration backup
This example creates an automation script to upload a daily configuration backup to an FTP file server. FileZilla is used as the FTP server application and an automation stitch is created on a FortiGate 60E running the latest FortiOS 7.0.3 release.
First step is to create an automation stitch. Select on the FortiGate menu the Security Fabric -> Automation -> Stitch-> Create New, and configure it as below:
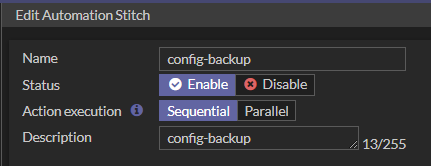
Select on the FortiGate menu the Security Fabric -> Automation -> Trigger-> Create New and set the schedule to run the backup.
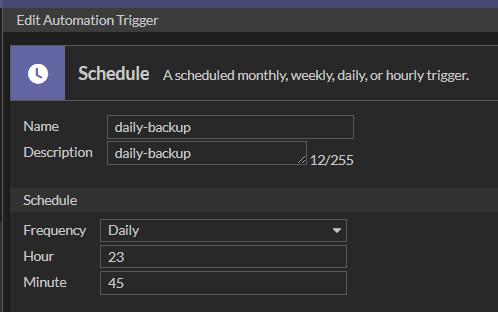
A scheduled monthly, weekly, daily, or hourly trigger can be selected. There is an option to set the time on a specific minute of a specific hour on a specific day. It has been configured in this example to run daily at 23:45.
Next step, select on the FortiGate menu the Security Fabric -> Automation -> Action-> Create New and configure the Action.
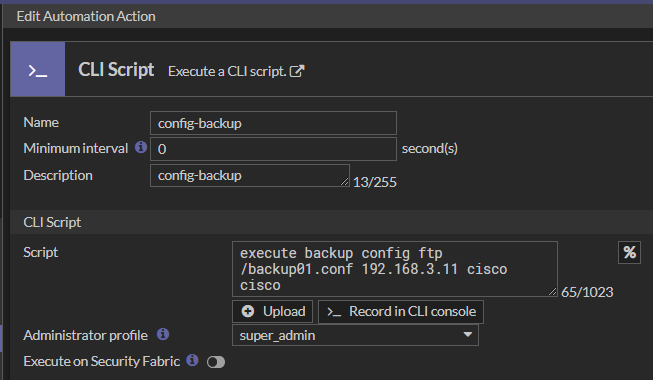
The scripts can be entered manually, uploaded as a file, or recorded in the CLI console. There is a very useful option to select the “Record in CLI console” to easily create the CLI script and test in parallel the commands.
As soon as the “Record in CLI console” is selected, a new window pops up and the CLI commands are recorded. Finally, the commands are presented on the CLI script menu by choosing “Save Script”.
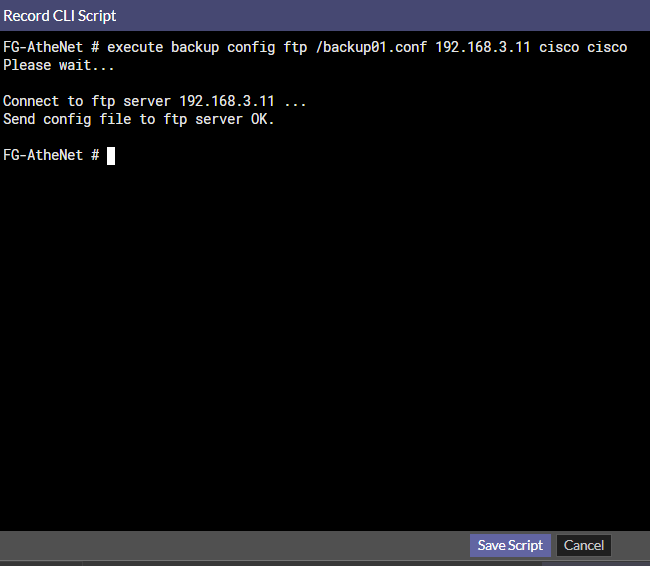
As soon as the saved script is selected, the executed commands are added to the Script. Next, configure the administrator profile to execute this script. Finally, there is the option to extend this script to all the FortiGate firewalls on the fabric by enabling the “Execute on all fabric” option. The automation stitch runs on a single FortiGate if this option is not selected.
The last step is to correlate the created trigger and actions with the automation stitch.
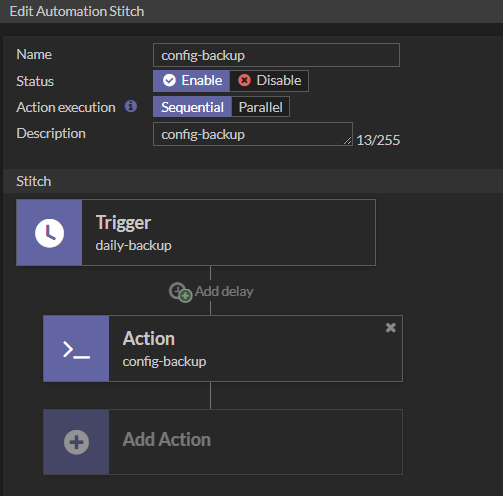
The Trigger named “daily-backup” and the Action named “config-backup” created in the previous steps are selected. Since it is a scheduled backup which runs on a specific time slot, there is no need to config any “Add delay” between the trigger and action.
The first automation stitch script is ready! Let’s test it manually.
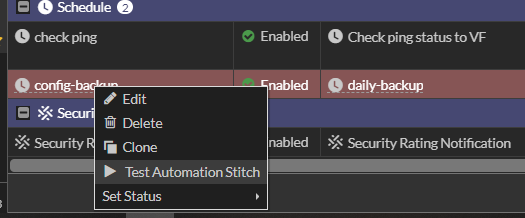
Select the configured automation stitch, then right click to select “Test Automation Stitch”.
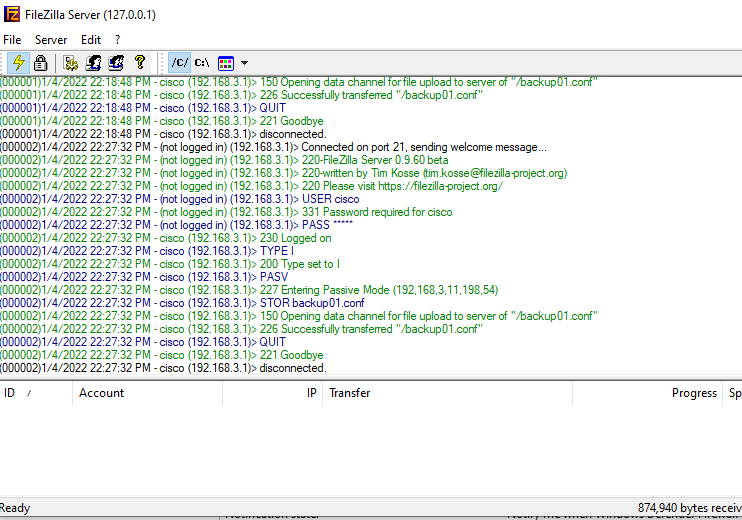
It is verified that the CLI-script is successfully executed. The FortiGate runs the command and uploads the config backup to the FileZilla FTP server.
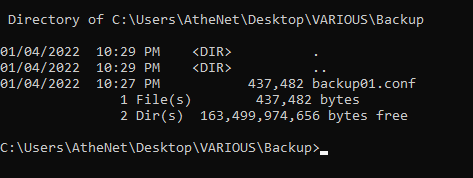
The config backup file has been successfully created on the ftp server.
Memory – Conserve Mode Automation
This example creates an automation stitch that runs a CLI script to collect debug information when the memory usage causes the FortiGate to enter conserve mode. The automation stitch sends an email with the results of the script to a specified email address for further troubleshooting and analysis.
Memory conserve mode is very often an issue which can cause service impact. It appears when a FortiGate is heavily utilized and several UTM features like AV and IPS are used extensively on the firewall policies. There are three different conserve mode thresholds:
- memory-use-threshold-extreme: Threshold at which memory usage is considered extreme, and new sessions are dropped, in percent of total RAM (default = 95).
- memory-use-threshold-green: Threshold at which memory usage forces the FortiGate to exit conserve mode, in percent of total RAM (default = 82).
- memory-use-threshold-red: Threshold at which memory usage forces the FortiGate to enter conserve mode, in percent of total RAM (default = 88).
The same simple 3-step methodology is going to be implemented again.
Create the automation script as below:
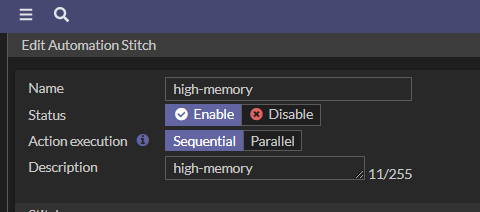 .
.
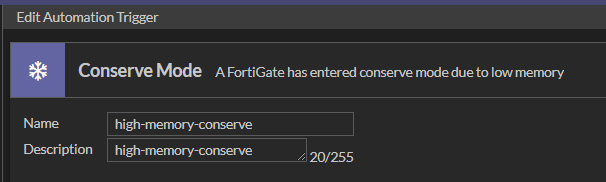
Configure the trigger by choosing the predefined trigger for “Conserve Mode”
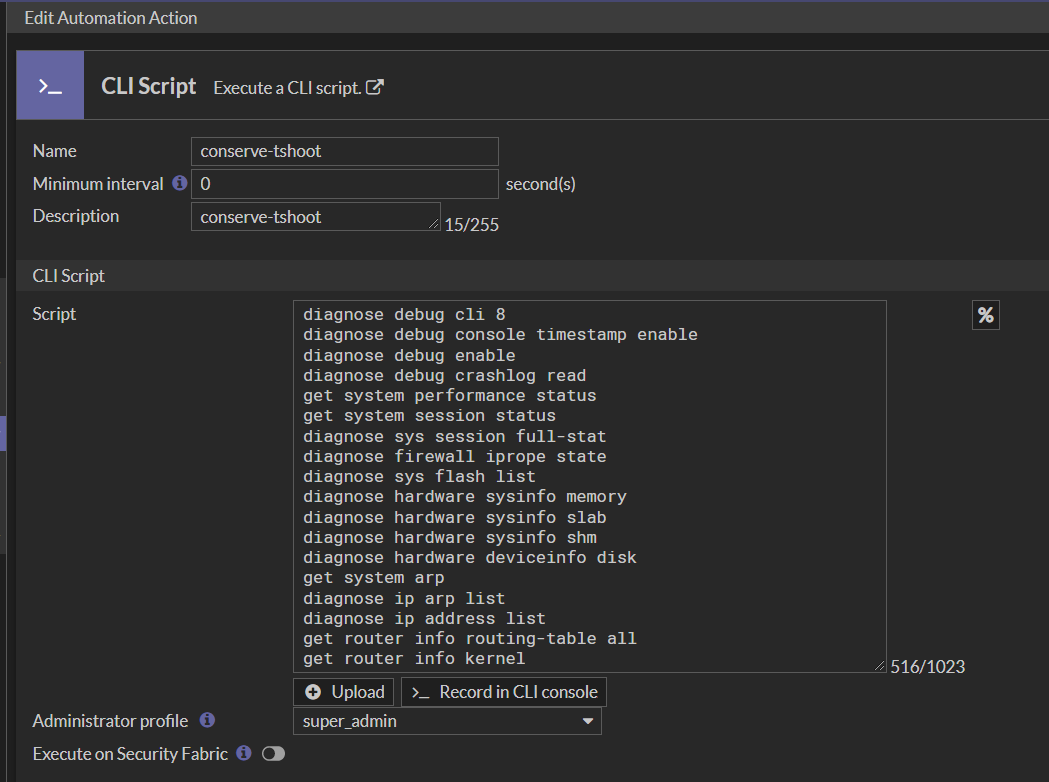
The third step is to configure the action. Create the script to run the diagnose and get commands in order to collect the requested outputs for analysis when the issue happens.
Configure the next additional action script to send all the outputs via email.
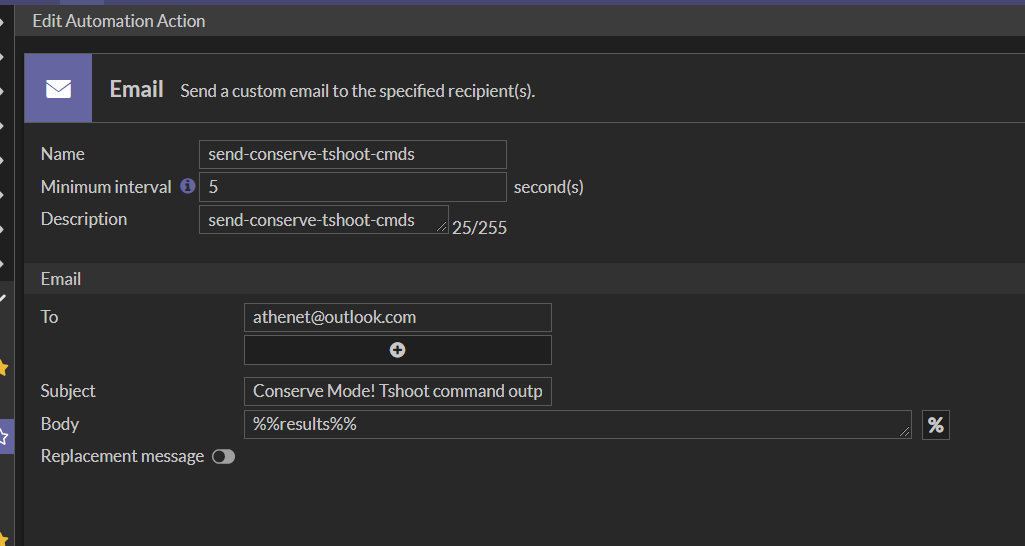
The results of the command’s outputs from the previous scripts can be presented by using the command %%results%% on the body.
Last step is to associate the trigger and action scripts with the automation stitch created in the first step.
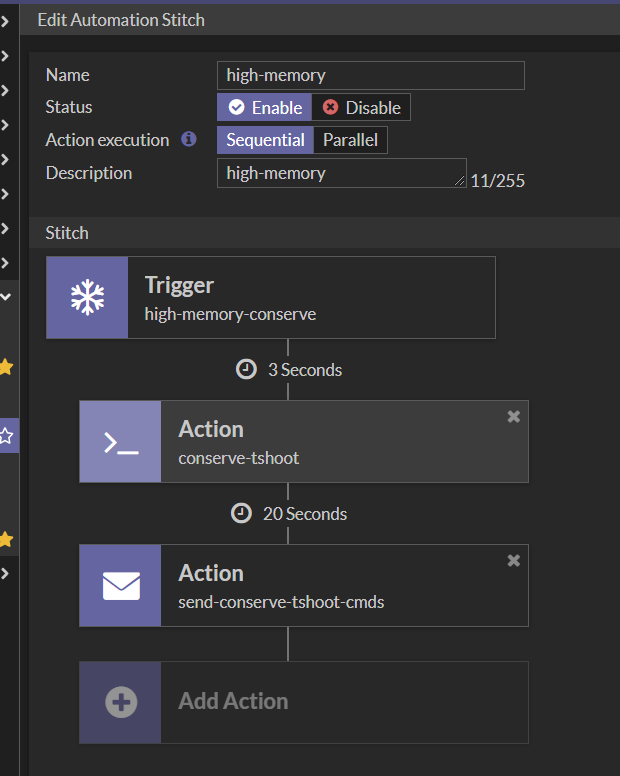
Based on this configuration, as soon as the FortiGate enters conserve mode, two actions are executed in sequential order. First script runs all the get/diagnose commands after 3 secs and then sends via email the cli outputs after 20 secs.
NOTE: Any delay time on the Action tasks can be used.
Finally, it is possible to verify if the script works manually by running the “Test Automation Stitch”
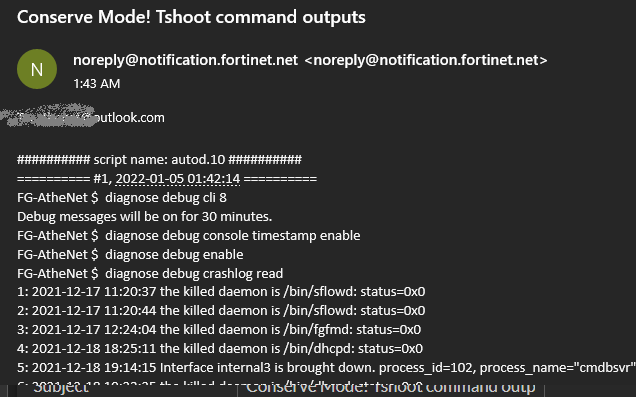
An email message with the relevant command outputs has been received!
FortiGate and Indeni
The automation on the FortiGate is a powerful feature introduced in the 6.0 FortiOS release that can simplify operations and improve fault management. The challenge is to ensure that the FortiGate operates without any issue and complies with a strict SLA with multiple nines availability.
To address these challenges, Indeni and Fortinet have established a technology partnership. Indeni ensures FortiOS configurations are done correctly and consistently. In addition, FortiGate performance is continuously assessed and optimized by advanced scripting based on programming languages like python. By using Indeni, engineering and operations teams can be notified proactively of misconfigurations and performance degradations before they result in service downtime!
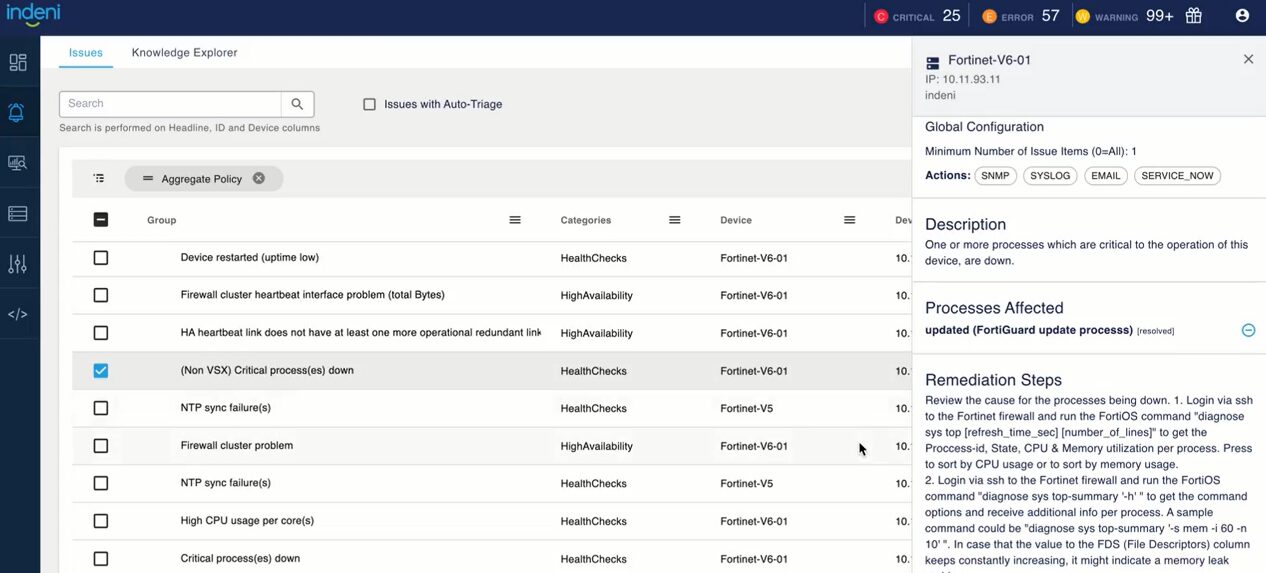
Indeni automatically detects issues relating to FortiGate and offers a way to remediate them. IT operations teams can gain Fortinet specific knowledge from the descriptions and recommended remediations built from real-world experience of certified Network Security Experts. Check out our top automation elements that can help you prevent costly disruptions.
Summary
FortiGate Automation Stitches can decrease the response times to security or system events. It supports integration with FortiAnalyzer, FortiNAC and other platforms like VMware NSX. Besides, it can be integrated with applications like Slack and Microsoft Teams for instant notification. Scripts can be easily created with the simple 3-step methodology discussed in this article so it is possible to simplify operation tasks like scheduled backups or troubleshooting.
Indeni further improves the performance and high availability by offering continuous analysis of the FortiGate with advanced automation scripts. Finally, Indeni provides remediation steps authored by Fortinet NSE certified Security experts in order to quickly isolate or resolve the issue.
If you liked this article, please share it by clicking on one of the social media sharing icons at the top of this page. More articles for Fortinet and Indeni are coming soon. Stay tuned ☺