Manipulating traffic with flow mode on Juniper SRX Series


Every experienced Network Engineer and System Administrator will agree with the fact that firewalls are an essential part of every network. The Juniper SRX Firewall is no exception because it provides essential security from the outside world and hacking predators. These dangers are patiently waiting to exploit every possible mistake you can make when you are implementing your network.
The standardized definition of firewalls, which use various rules to protect your network and control the traffic both coming in or going out of the firewall, has changed over recent years. Lately, firewalls have been produced to offer a lot more than just policing. They have been given new and more complex capabilities. One of the most important to note is their ability to look deeper into the packets traversing through them and being able to gather all that information and implement it in a way that would be the most beneficial for the network they are protecting. This deep packet inspection is the main feature with Juniper’s SRX Series Gateways and even though Juniper haven’t invented it, they worked on finding the most suitable way to solve problems their customers face. They used various methods to achieve this and worked from the ground up on the complicated new SRX platform which made them influential among the biggest enterprises in the world.
The Juniper SRX Series
The Juniper SRX Series Gateways are known as the beginning of Juniper’s “attack” on global Service Providers. They are the first devices that have been migrated from the previous Screen OS operating system to the new Junos OS which provides a more in-depth view in configuration, maintenance, and operation. Junos is a state of the art operating system based on FreeBSD which is a UNIX implementation. Therefore, engineers can execute standardized UNIX commands. Besides the many features that Junos OS provides, one of the highly attractive ones is the option to change how the device is inspecting and processing the traffic. Or, in other words, manipulate traffic based on yours or your customer’s needs. It’s important to note that different networking vendors have different solutions that handle passing traffic. With SRX devices, this is done by changing the default mode of operation of the device. There are two options you can choose from: flow mode and packet mode.
The most common definition that can be found regarding these modes, and the difference between them, is: flow mode traffic processing analyses all traffic passing through by the state or session of traffic while packet mode processes all traffic as a traditional router, widely known as per-packet basis. It is worth mentioning that all SRX devices work in flow mode by default. Let’s dig in a bit more in how these modes operate.
Understanding Juniper SRX’s flow mode operation
We will start from the default mode of these devices, the flow mode. This mode is also known as the stateful mode. This is the more complex one because it needs to monitor the state of all traffic passing through the firewall. Unlike past firewalls, where you could choose from packet-based, proxy, or stateful, the future of firewalls is the stateful firewall because of the attractive price/performance ratio they offer, therefore they are most commonly deployed. Although packet-based and proxy firewalls are slowly becoming part of the past, the stateful firewall has “stolen” some features from its predecessors. Two important features are:
- SSL traffic decryption
- IPS (Intrusion Prevention System) inspection which provides the ability to accurately determine the protocol beyond the traditional port number
The flow mode gives the SRX a chance to run smoother and improve overall performance because the traffic is inspected at the transport layer of the TCP-IP stack. The traffic is inspected in five separate steps: match of source and destination IP addresses, match of source and destination ports and protocol with the source and destination zones, to determine if the packet belongs to a new or existing session. If the traffic belongs to a new session, additional policy and route lookups will have to be done. After all these steps are finished, the traffic is processed and if future traffic matches the session, the traffic flow will proceed uninterrupted. This processing approach allows the firewall to handle more complex operations and solutions like NAT, JFlow, IPS, and a crucial one: UTM (Unified threat management). UTM handles content and web filtering, antispam, as well as other similar threats. The below image shows how the traffic is handled:
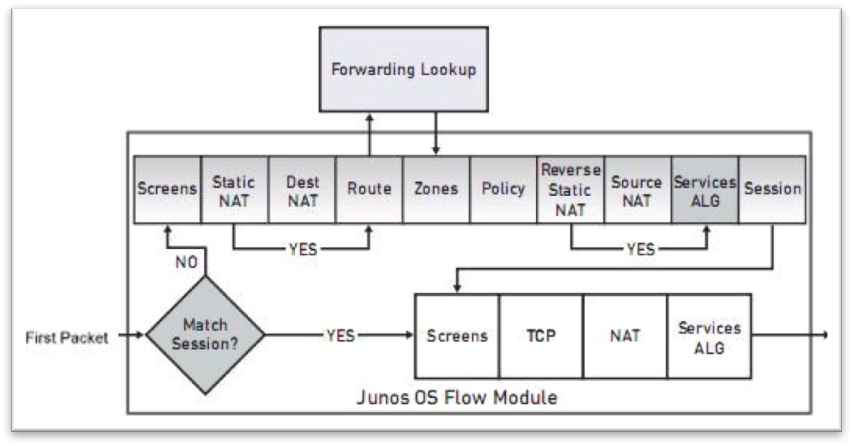
Original Source: https://kb.juniper.net/InfoCenter/index?page=content&id=kb16110
Understanding Juniper SRX’s packet mode operation
On the other hand, the packet mode operation is a simple, routing-like, operation of a firewall. This mode provides the firewall to inspect packets individually and not as part of a session flow. With this mode, as soon as the packets enter the Juniper firewall, various filters and policies are being added. After these are applied, the firewall will look for the route so that the egress interface for that packet can be determined. When the egress interface is determined, and confirmed, the packet is sent there, where it’s scheduled for transmission. Because the packets are individually inspected, any decision to allow or deny the traffic is packet specific. In packet mode the firewall doesn’t have to determine how the sessions are established and keep track of every session. This provides an optimal routing of the packets which sometimes can be handled by the ASICs. The image below shows how the packet is processed once it enters the firewall:
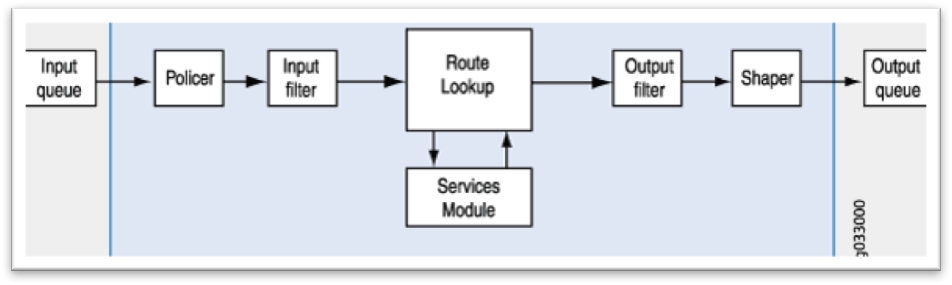
Original Source: https://www.juniper.net/documentation/en_US/junos/topics/concept/security-packet-based-processing-understanding.html
With Junos 9.6 and beyond, Juniper decided to provide the option for both modes to operate simultaneously. This eventually avoids the limitation of having to choose between both modes and what they offer, providing simplicity in configuration and deployment. In this case, the traffic that requires packet mode processing is marked by packet filters, while the traffic that requires flow mode processing is left unmarked. This way, the firewall can determine which processing mode to use. This is simple to understand through the image below:
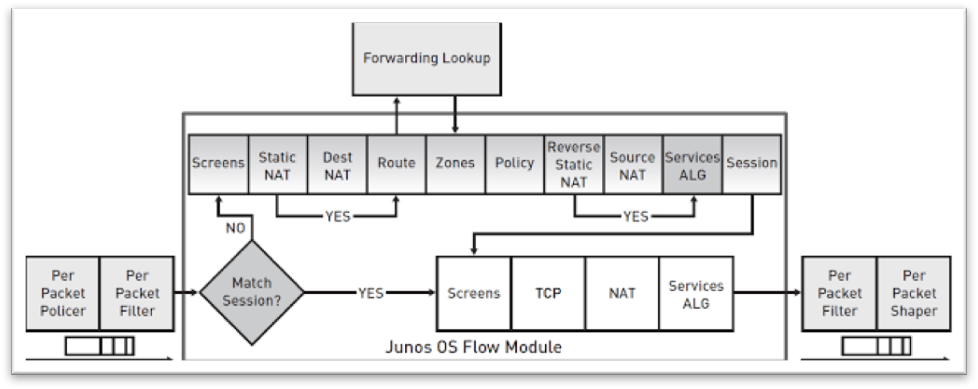
Original Source: http://jncie-sec.exactnetworks.net/2012/10/junos-flow-based-processing.html
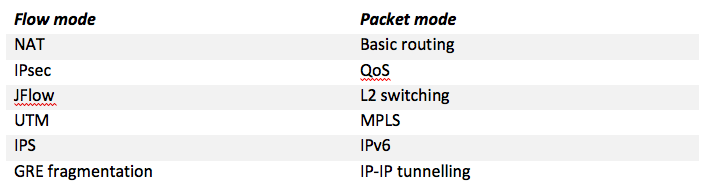
A short list of protocols supported by the two modes is provided in the table below:
Sample deployment of a flow mode configuration with NAT and DHCP
For this sample deployment, we are going to use a real-world example of how flow mode is deployed on an SRX platform. We are going to focus on the SRX device deployed on customer’s site and specifically on customer’s requirements. This sample deployment will show the sample configuration, including the needed steps to take when configuring it.
The client has requested:
- A DHCP server to be configured on the Juniper provided by their Service Provider. They require a separate private IP block assigned by the DHCP, to use for Internet browsing.
The first step in this configuration is to confirm the current operational mode of the SRX. This is simple to do with executing the command shown below, from the Junos operational mode:

Next, we must confirm what is needed to meet their requirements. For this requirement to work as expected we need to focus on a couple of things:
- The customer used to browse the Internet with a public IP block. This public block would have been routed in the core network of the Service Provider.
- The customer would like to use a private block instead. This means that a protocol called NAT will have to be implemented. This protocol will translate the private IP block in a single public IP address.
- A DHCP configuration will have to be deployed to assign IPs from the private IP block.
- The SRX will have to be configured to operate in flow mode.
The next step is to configure the router to operate in flow mode so the above can be deployed. Switching between both modes on an SRX platform is extremely simple, however please note that with every mode switch, a reboot of the device is mandatory. To set the router to operate in flow mode and be able to pass traffic we need to undertake some steps:
- Define security zones
- Create a security policy to allow traffic between zones
- Add any firewall rules
- Add any NAT rules
- Add any DHCP configuration
To switch from packet mode to flow mode simply execute the following command from the device’s configuration mode:
- set security forwarding-options family mpls mode flow-based
After the router reboots, the next step is to configure the security zones which will tell the router which zone to trust. For this example, we will configure interface fe-0/0/1 as “trusted” and interface fe-0/0/5 as “untrusted”:

- The next step would be to add the policy that will allow traffic flow between the zones:
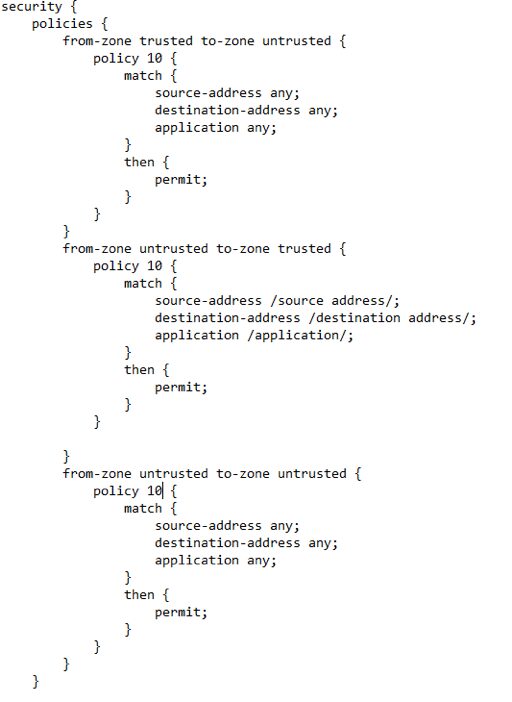
- Next, we must configure NAT using an address pool and a static NAT to make the end customer able to browse the Internet with a private IP address:
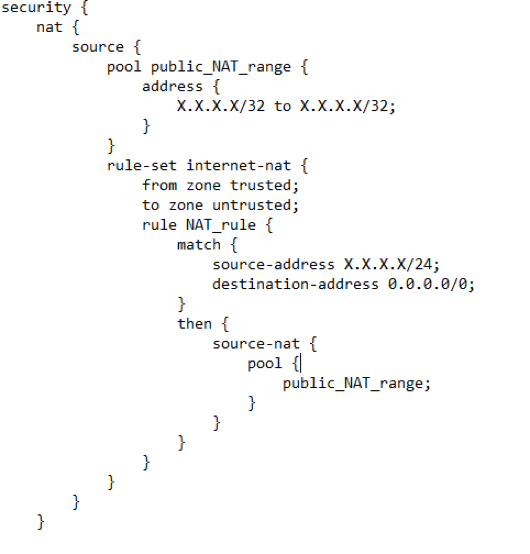
- After the NAT configuration we need to focus on the DHCP configuration. When we are configuring DHCP we must specify the DHCP pool, the interfaces that will work as the DHCP servers, the low and high IP address to be assigned, the default gateway and the DNS server IP (primary and secondary):
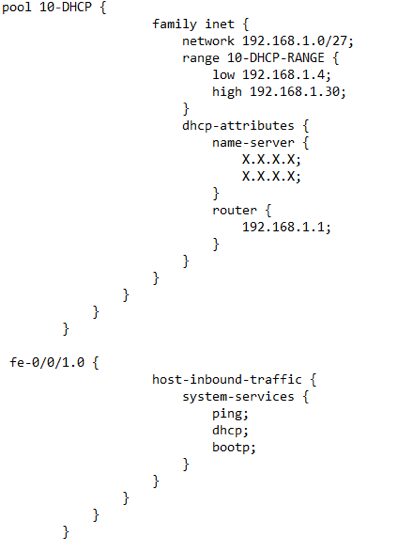
To verify if the above configuration is working please execute the following command:
- show security nat source rule X– where the X Is the rule you specified in the NAT configuration
The output of this command will show everything you need to observe when NAT is configured. You need to point your attention to the number of “Translation hits” and confirm they are incrementing:
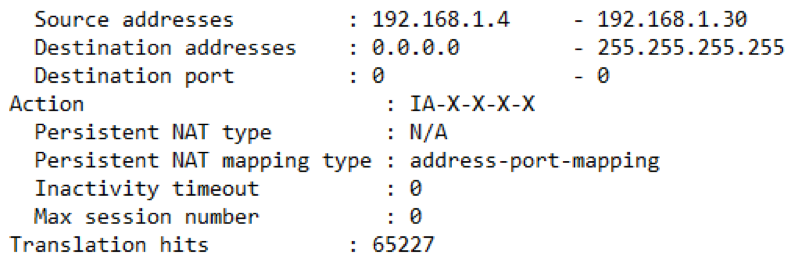
If these hits are incrementing the NAT works as expected and the private IP block is being translated into a public IP address. Customer successfully browses the Internet with a private IP address.
Juniper’s SRX Series Summary
In this brief article we covered the basics of Juniper’s SRX series devices and we only scratched the surface of their networking capabilities. If we go deeper and research all their capabilities, we will end up with hundreds of pages of definitions and configuration examples. In the end, we will end up concluding that the SRX devices, which operate on Junos OS, have a lot more capabilities than most firewalls currently on the market. In addition, we covered a configuration sample and the basics needed to manipulate the traffic with the flow mode forwarding option, which allows us to implement a more complex solution to meet the client’s requirements.
When it comes to processing traffic, you can choose from a wide variety of options that will best suit your network. By knowing and understanding how these modes and the separate policies work, you have the possibility to create a powerful tool to protect your network.
Thank you to Bojan Janevski for his work on this article.