Palo Alto Networks Advanced Administration Tips
Introduction
The Palo Alto Networks next-generation firewalls are a part of a security platform that provides a plethora of configuration options within its devices. The results from adequately utilizing the available configuration options provide a strengthened security posture in respect to existing and future information security challenges or organization mandates.
Thus, the installation of the Palo Alto Networks next-generation firewalls in your information technology infrastructure is likely imminent or already underway. Accordingly, increasing your familiarity with the Palo Alto Networks firewalls is wise, so you can ensure you have the capabilities to support daily operations.
Scenario Set-Up
To help with your understanding for this blog, a sample environment has been created utilizing a Layer 3 configuration. Unlike the VWire Interface configuration, the firewall utilizes a Layer 3 configuration. Therefore, the firewall plays the role of the gateway for the connected networks.
In this scenario, the firewall is a VM-100 virtual next-generation firewall within a virtualized environment and connects to the two internal networks that have one virtual desktop computer each and the Internet.
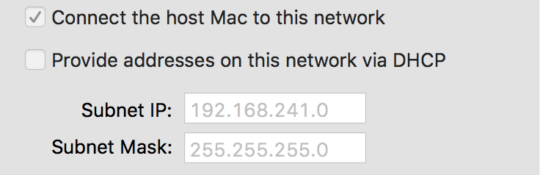
Note: The instance of VMware environment is configured with the two private networks/vmnets that each has the host physical computer as the gateway for the virtual desktops computers on the respective subnet and a connection to the Internet via a dedicated vmnet.
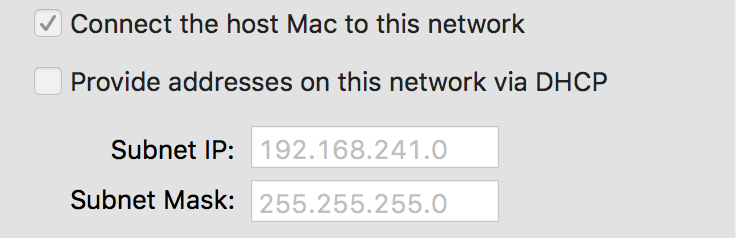
Additionally, the internet facing interface is configured with a static IP address on the same range as the example internet router to provide external connectivity to the firewall and the virtual desktops computers. Lastly, the firewall has already been registered via Palo Alto Networks Support Portal.
Note: You can complete this configuration with any physical Palo Alto Networks next-generation firewalls and host computers or via the Palo Alto Networks FUEL User Group Virtual Test Lab.
Network Architecture:
Internet Interface (Eth 1/1): 192.168.1.173/24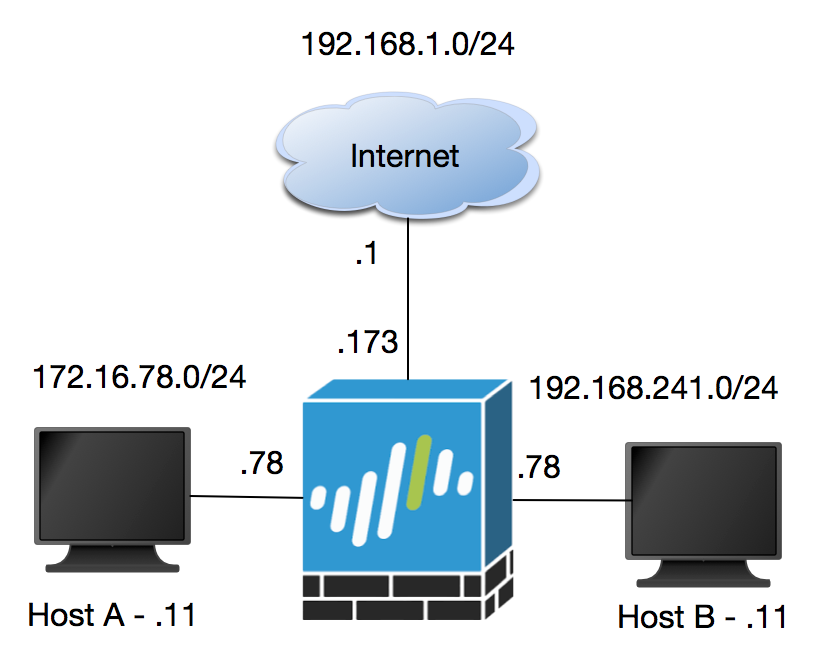
Internet Router: 192.168.1.1
Subnet: 192.168.1.0/24
Zone: Internet
Host A: 172.16.78.11
Gateway (Eth 1/2): 172.16.78.78/24
Subnet: 172.16.78.0/24
Zone: 78-Zone
Host B: 192.168.241.11
Gateway (Eth 1/3): 192.168.241.78/24
Subnet: 192.168.241.0/24
Zone: 241-Zone
General Settings
During the configuring your firewall, you can update many General Settings including your hostname (the default is model name for each firewall, ex. VM-100 or PA-3020), the login banner, timezone, locale, and time.
- Go to Device>Setup>Management and click on the gear symbol on the General Settings ribbon
- Update with Hostname field (ex. Indeni-Palo-Ex)
- Update with Login Banner field
- Update with Time Zone field
- Update with Locale field
- Update with Date field
- Update with Time field
- Click the OK button

Interface Management
The interface type that we will use to support traffic for the network devices is a Layer 3 Interface:
- Layer 3 – Operates at Layer 3 and will have an IP address and be attached to the virtual router on the NGFW.
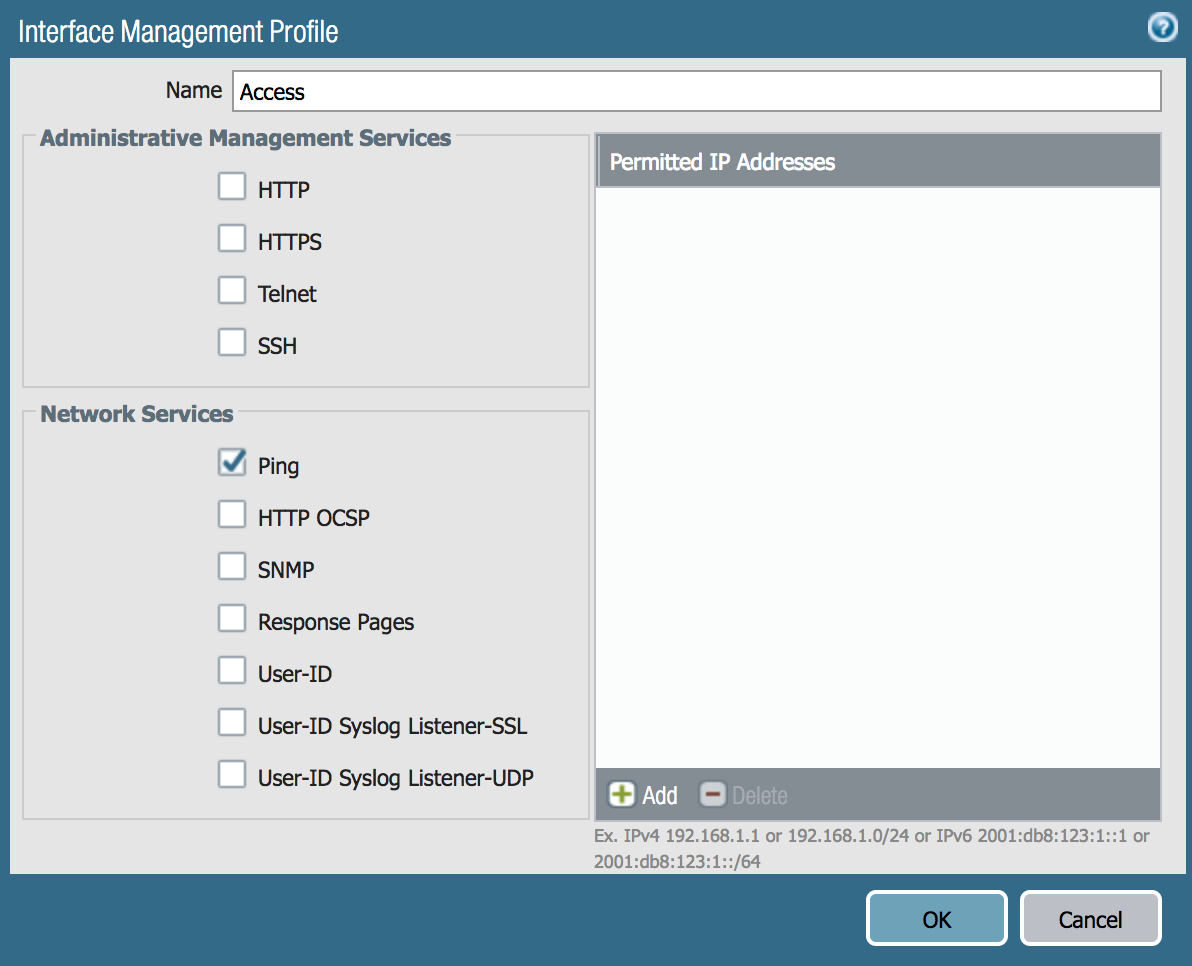
Furthermore, the interfaces can be configured via Interface Management Profiles to run specific services when being managed via IP address. A few of services that we will use are HTTPS, Ping, and SSH.
Now we’ll create one profile to support ping, which will be used for the ethernet1/1 (external connection) and the ethernet1/2 and another profile to support https, ping, and ssh for ethernet1/3.
- Go to Network>Network Profiles>Interface Mgmt and click Add
- Update the Name field with the designated name
Example (Access):
Example (Access-Admin):
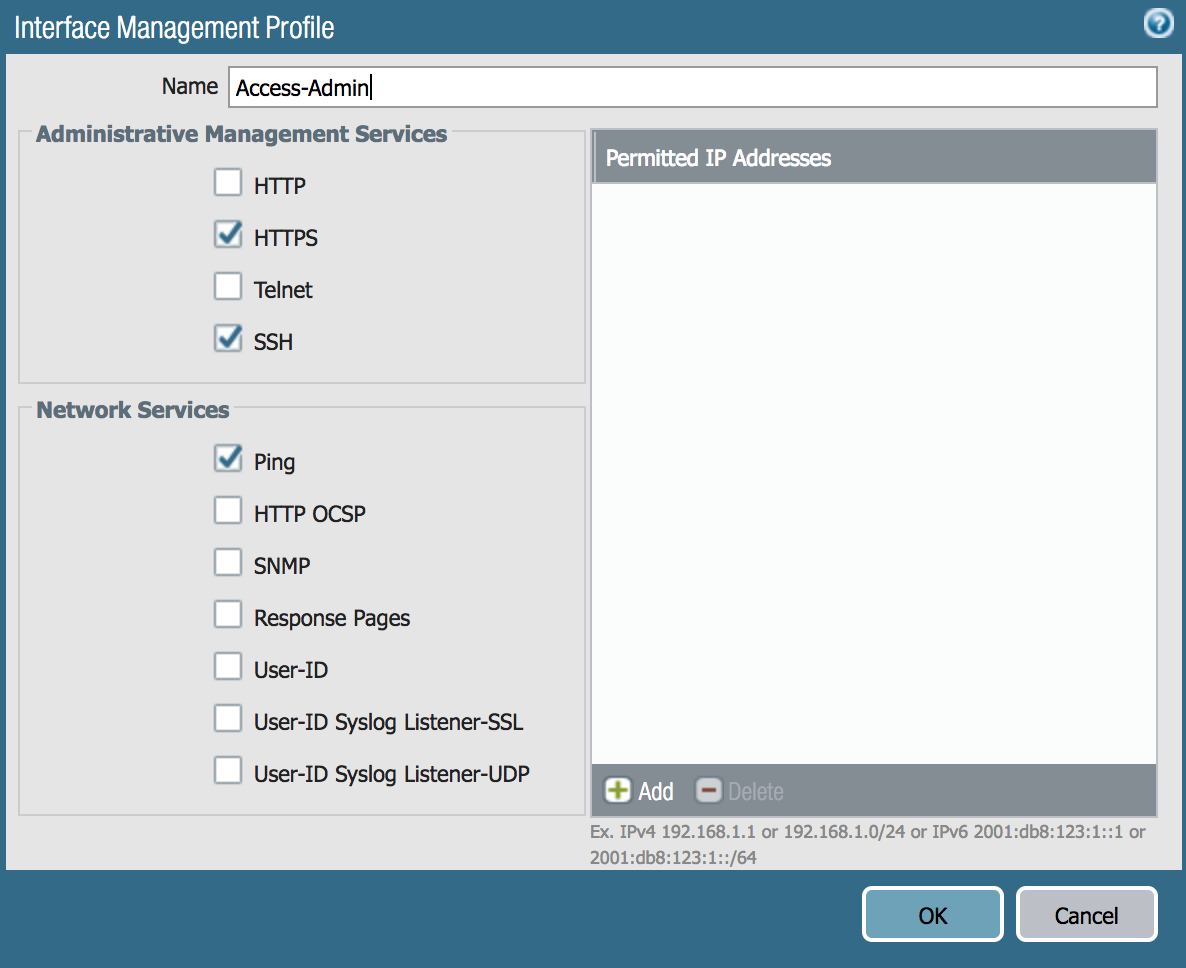 Note: The subnets accessing the services on these interfaces can be specified within the Permitted IP Addresses field.
Note: The subnets accessing the services on these interfaces can be specified within the Permitted IP Addresses field.
Let’s utilize ethernet1/1 (external connection), ethernet1/2 and ethernet1/3 as a part of a Layer3.
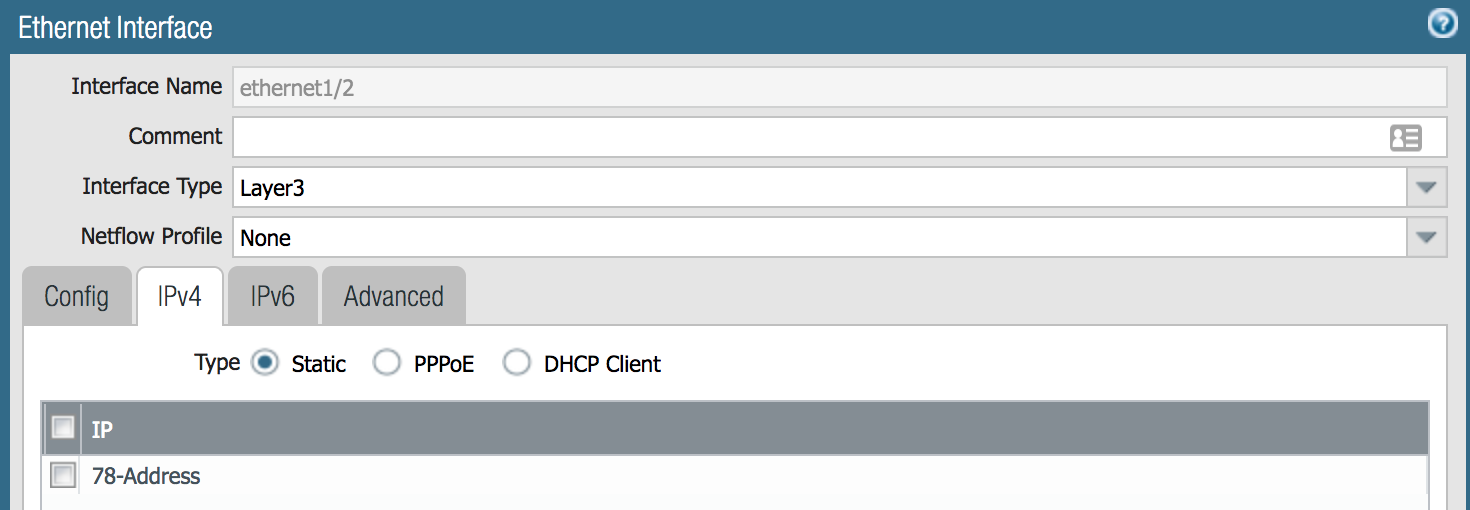
- Go to Network>Interfaces and click on ethernet1/1, ethernet1/2 and ethernet1/3 and change the Interface Type dropdown to Layer3
- Click the IPv4 tab, click the Add button, and add in the interface IP address (the IP type is Static by default and the address object has already been created with the IP
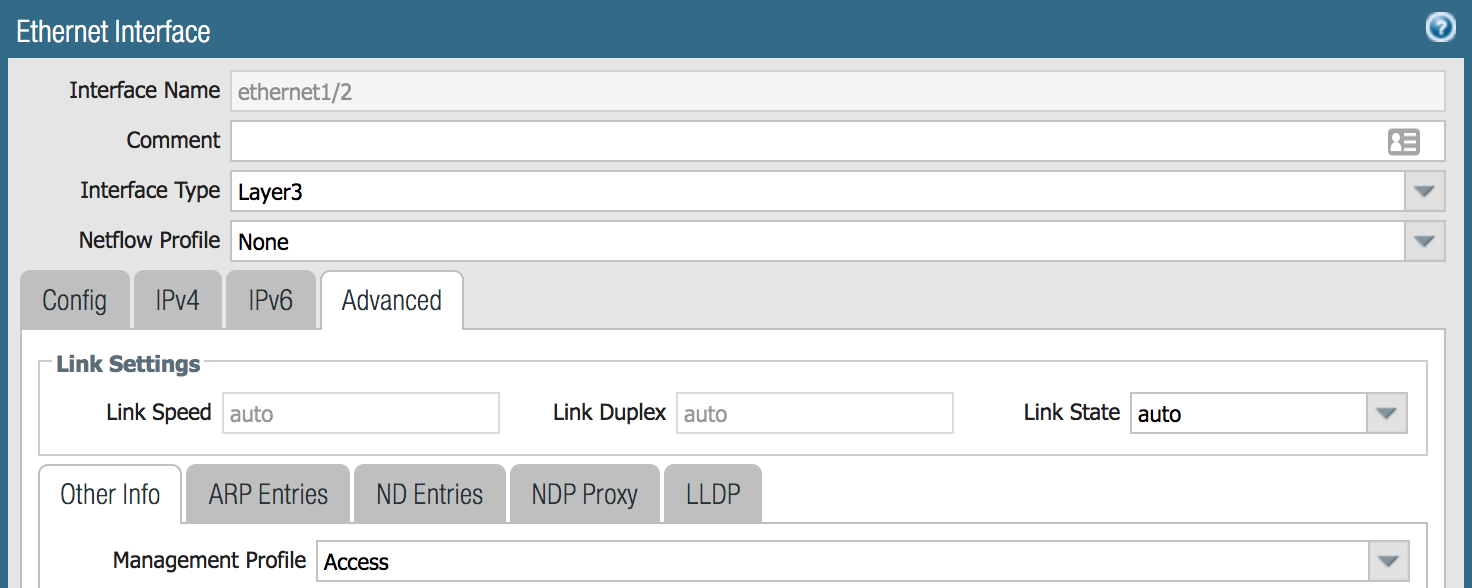
- Click the Advanced tab and update the Management Profile field with the designated Interface Management Profile
Zone Referencing
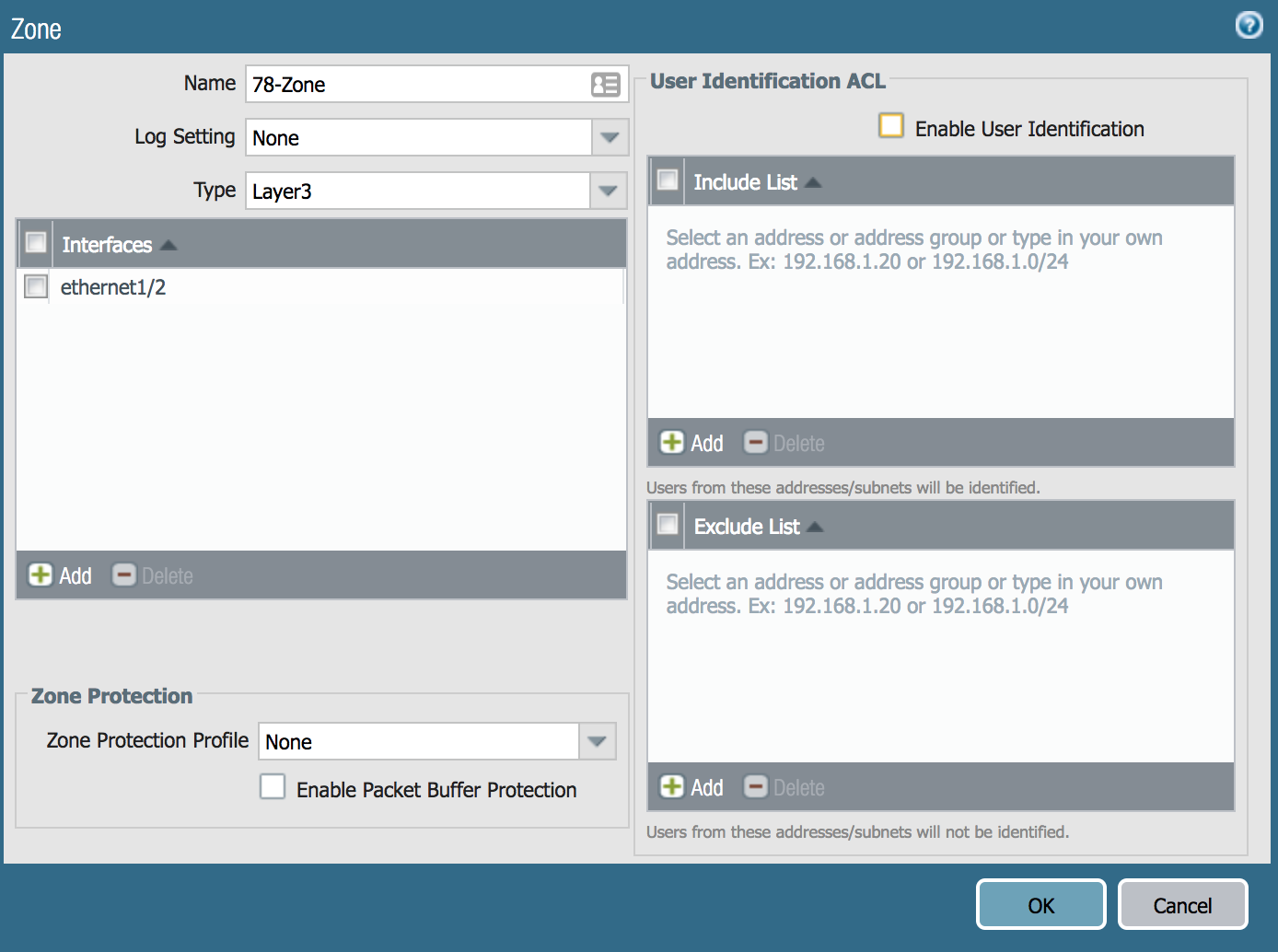
Zones reference certain traffic and is comprised of one or more interfaces on the NGFW. We will utilize Layer 3 Zones for the interfaces that were previously configured types.
Now, we still change ethernet1/1 to a Zone named Internet, ethernet1/2 to a Zone named 78-Zone, and ethernet1/3 to a Zone named 241-Zone.
- Go to Network>Zones and click Add
- Update the Name field
- Change the Type dropdown to Layer 3, click Add in the Interfaces section and click the OK button
How To Create A Virtual Router
- Go to Network>Virtual Routers and click Add
- Under the Router Settings, update the Name field
- Under the General tab, click Add and select ethernet1/1 (and repeat the process for ethernet1/2 and ethernet1/3)
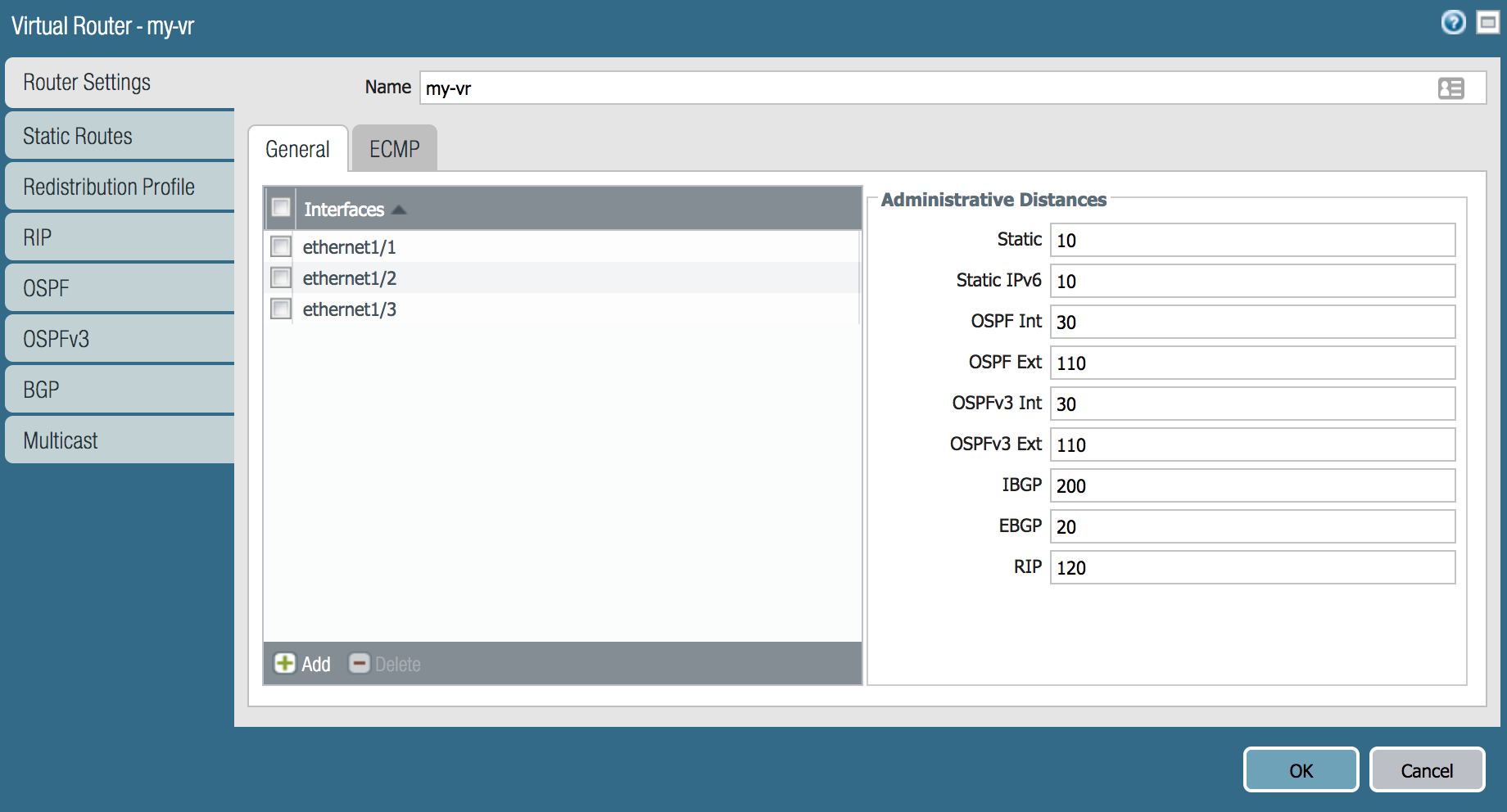
- Under the Static Routes tab, click Add under the IPv4 tab
- Update the Name field (ex. Default Internet)
- Update the Destination field (0.0.0.0/0)
- Update the Interface field (ethernet1/1)
- Update the Next Hop field with type (for this instance, it is IP Address)
- Enter IP Address of the Next Hop (192.168.1.1)
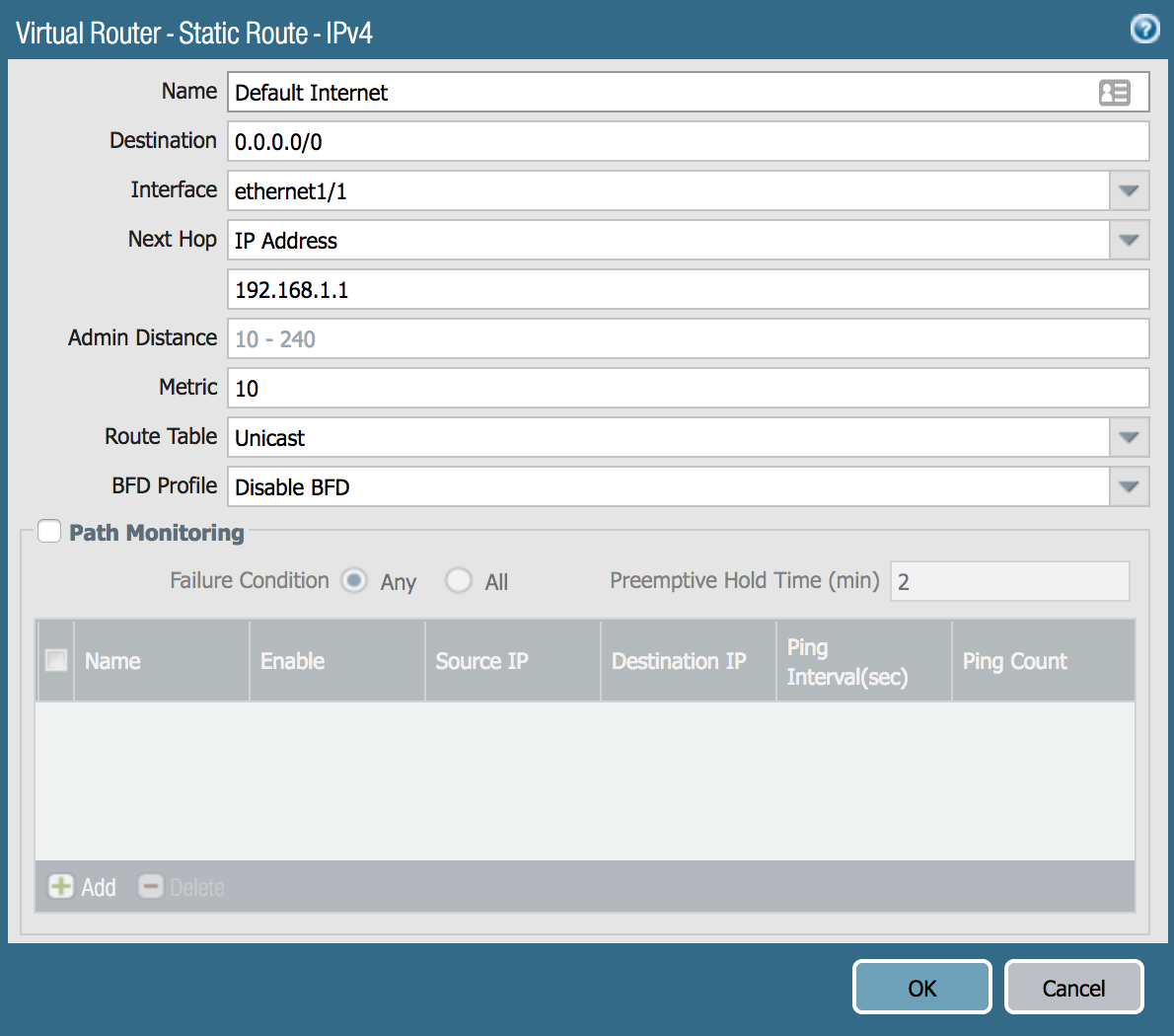
- Click the Add button for the Static Route window
- Click the Add button for the Virtual Router window
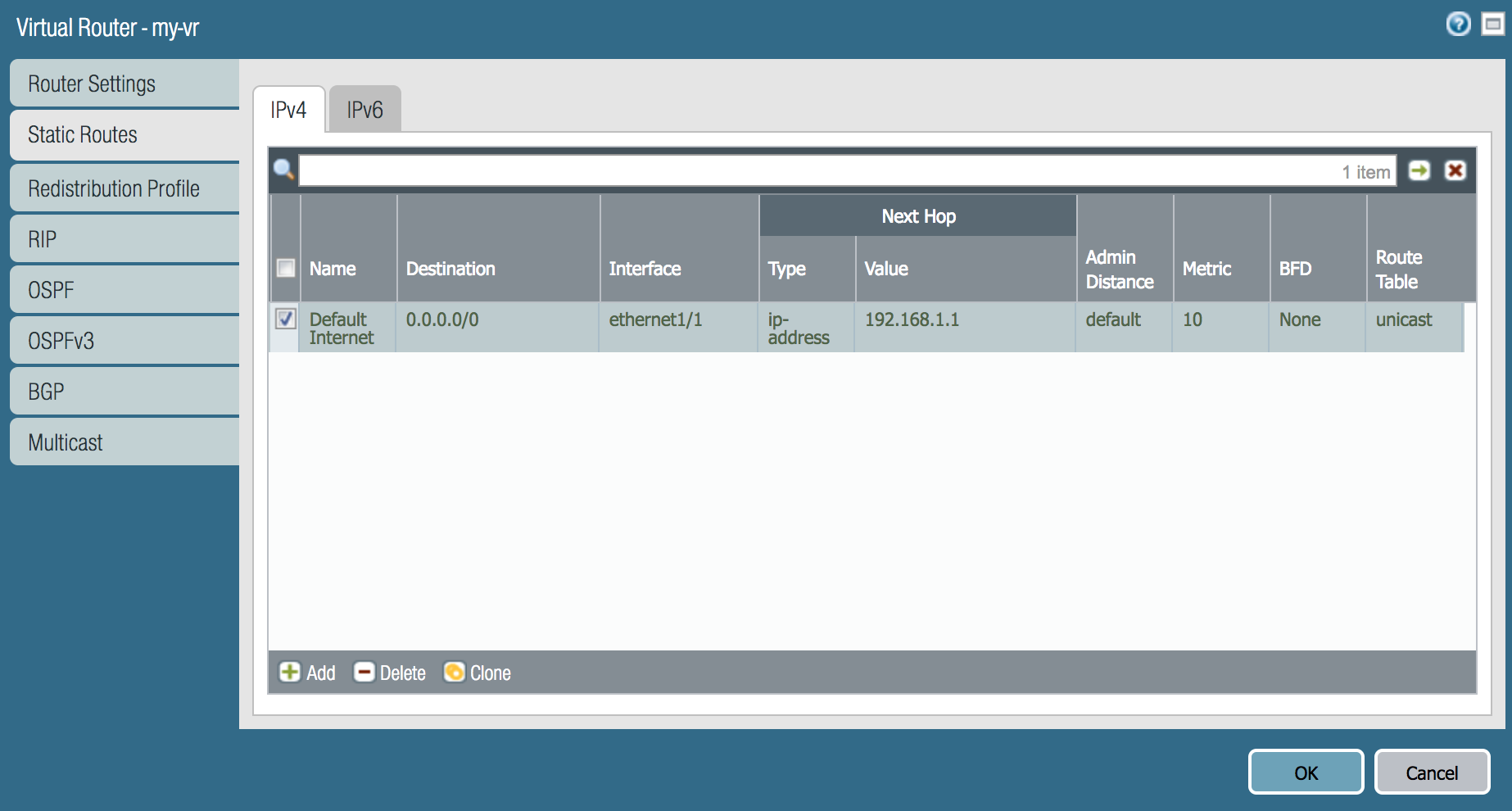

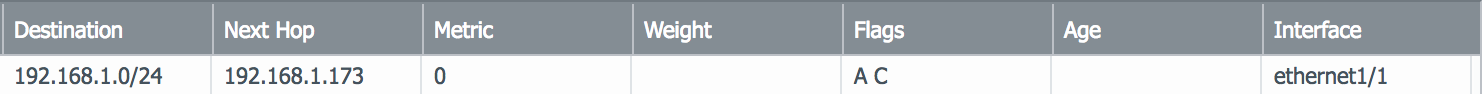
Note: By adding the interfaces, the subnets for the interfaces will be added as connected routes in the virtual router instance under More Runtime Stats.
Network Address Translation (NAT)
NAT allows you to conceal one or more IP addresses and display designated IP addresses.
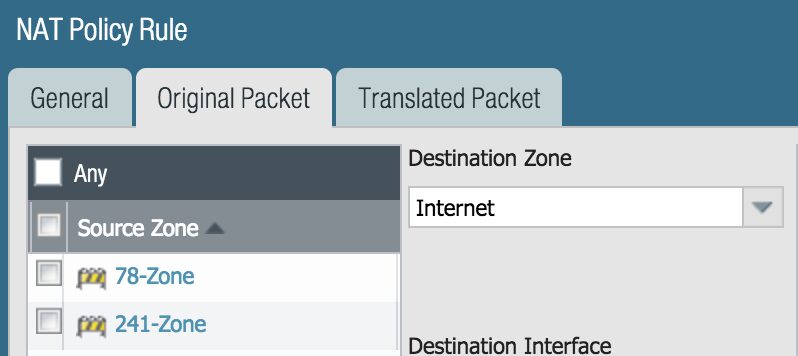
Let’s create a policy to the NAT the LAN traffic (78-Zone & 241-Zone) to the ethernet1/1 when the destination is the Internet zone
- Go to Policies>NAT and click Add
- Under the General tab, update the Name field
- Under the Original Packet tab:
- Add 78-Zone and 241-Zone in the Source Zone box by clicking Add for each zone
- Change the Destination Zone drop-down to Internet
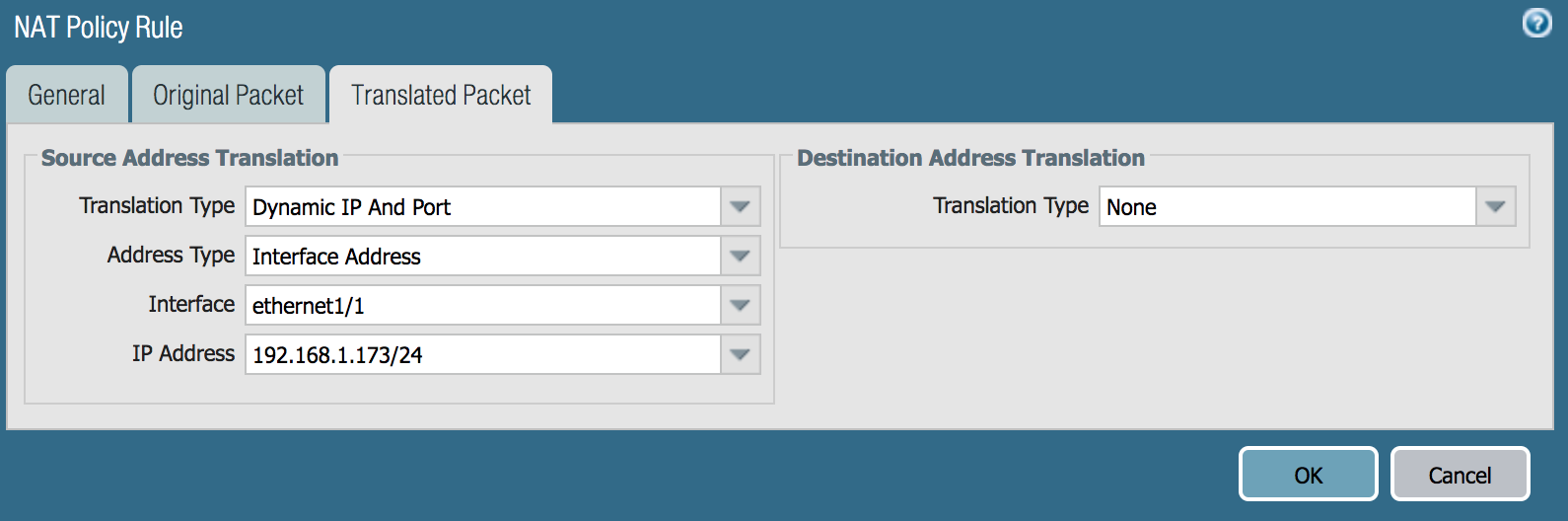
- Under the Translated Packet tab
- Change the Translation Type drop-down to Dynamic IP and Port
- Change the Address Type drop-down to Interface Address
- Change the Interface drop-down to ethernet1/1
- Change the IP Address drop-down to the interface IP (ex. 192.168.1.173/24)
- Click the Ok button
How To Create Security Policies
Security policies allow or deny traffic. They also allow the traffic that will correspond to the NAT policy the previous section
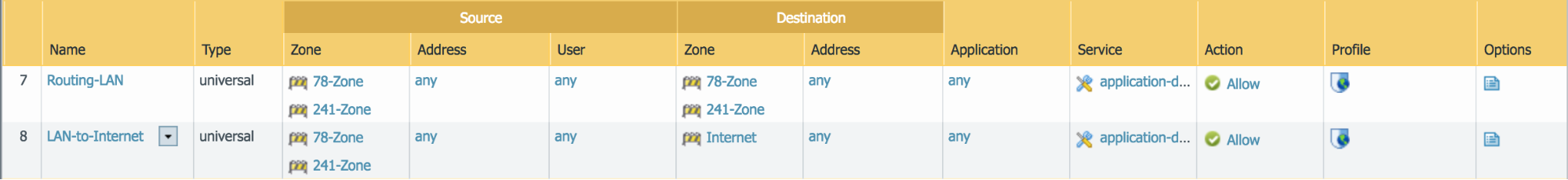
Let’s create a two security policies. One security policy will allow traffic between the LAN zones (78-Zone & 241-Zone) and another security policy that will allow the LAN traffic to the Internet Zone.
- Go to Policies>Security, click Add, and update the two security policies:
- General>Name field (Routing-LAN/LAN-to-Internet)
- Source>Source Zone, click Add (select 78-Zone & 241-Zone for both security policies)
- Destination>Destination Zone, click Add (select 78-Zone & 241-Zone/Internet)
- Click the OK button for the Security Policy
How To Commit Configuration Changes
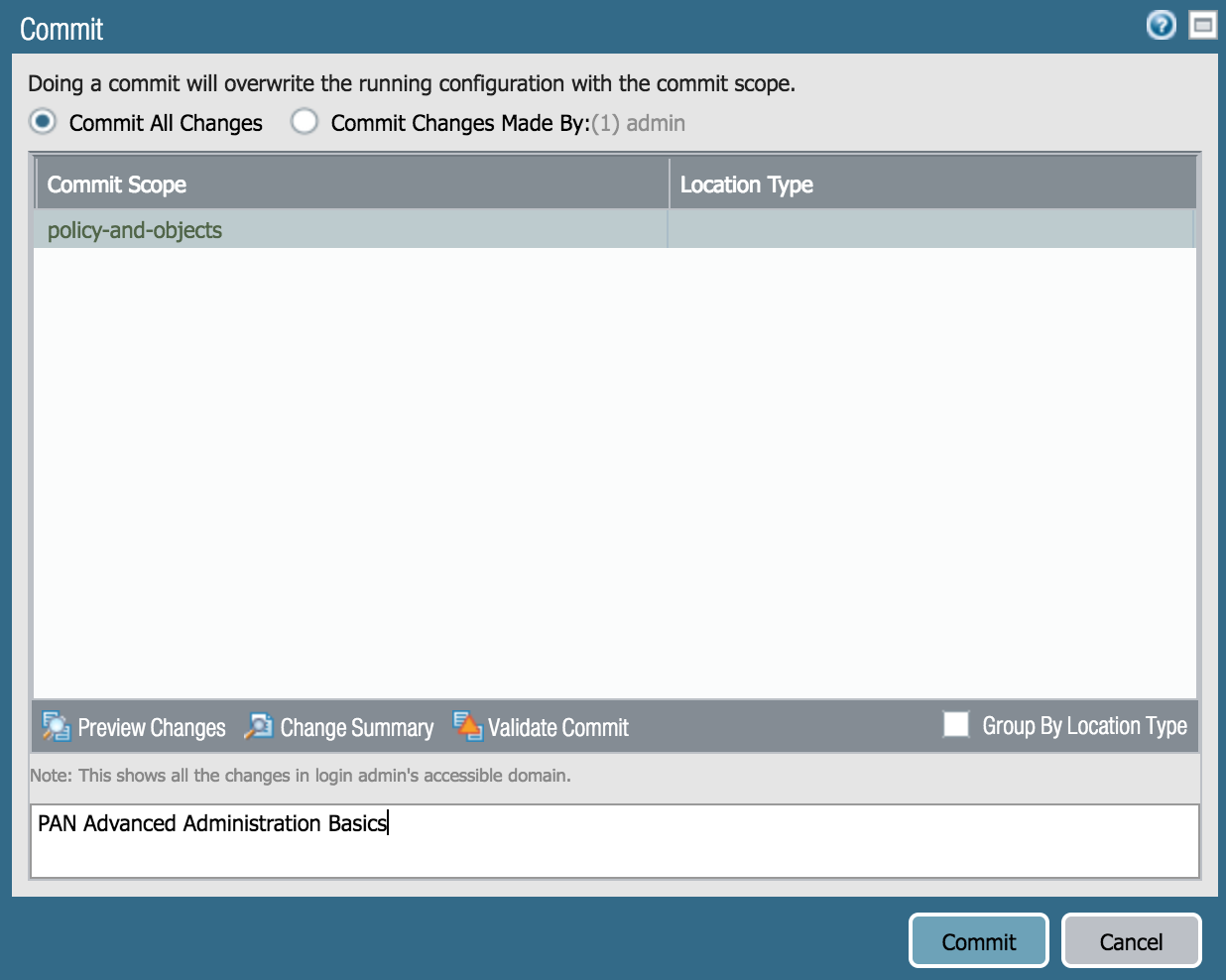
The changes made to the firewall have been added to the candidate config, but need to be committed to add them to the running config. To add changes to the running config:
- Click Commit
- Click the Commit button on the bottom right of the window
Advanced Administration Results
Here are the results of your advanced administration:
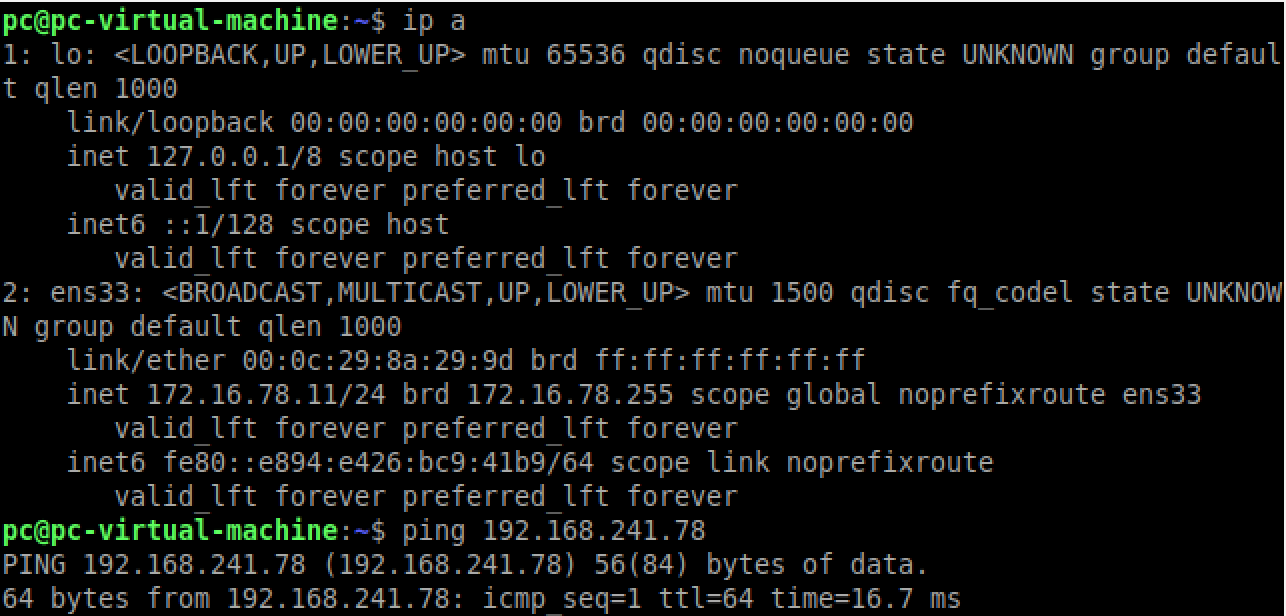
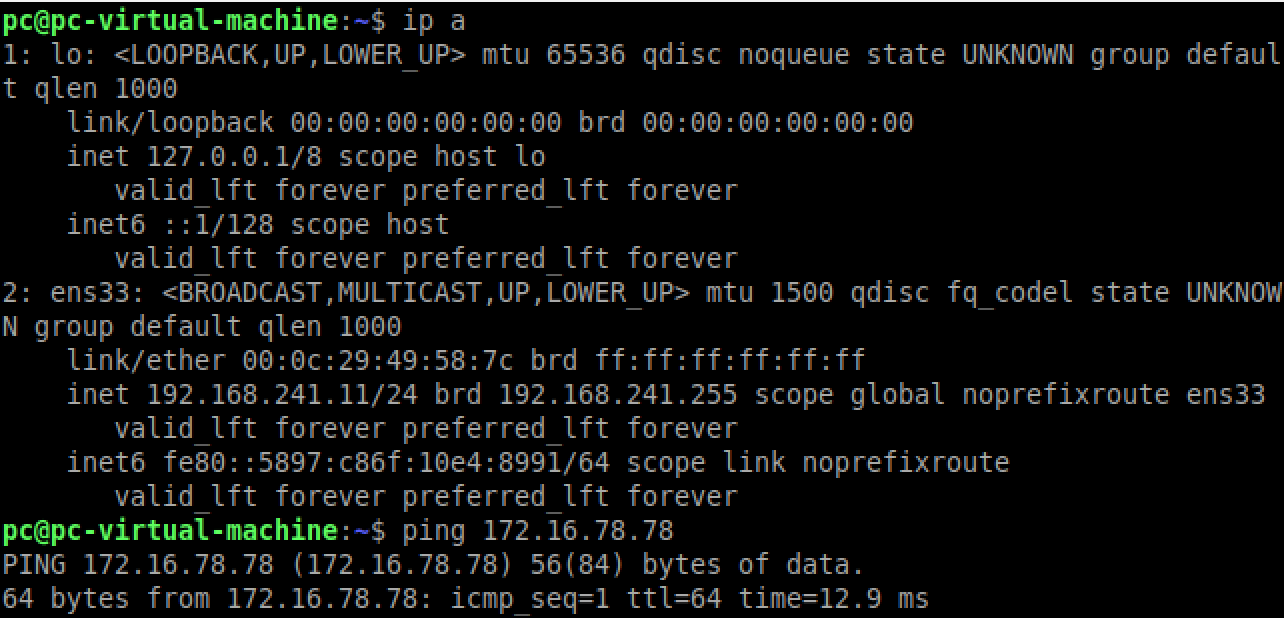
![]()
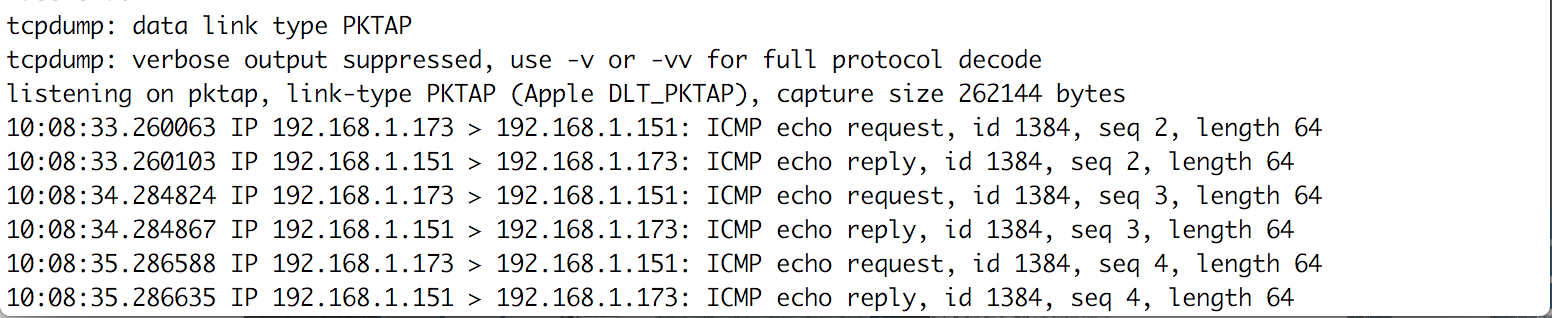
What We Learned
You just learned about Interface Management Profiles, Layer 3 Interfaces and Zones, Virtual Routers, NAT policies, and creating the Security policies that allows the traffic matching the NAT policy. For more guides, tips, and how-to guides, join Indeni Crowd. Indeni Crowd includes learning paths and challenges which grant points that you can redeem for epic rewards!