Top Network Automation for Palo Alto Networks NGFW
The support for Palo Alto Networks Next Generation Firewalls (NGFW) is one of our flagship products. The coverage spans a wide variety of use cases, all with problem avoidance as a primary goal. Today, we have over 240 Auto-Detect elements to help you proactively manage your firewalls.
Key use cases:
- In-depth visibility with proactive alerting
- High availability readiness
- Security risks identification including alerts on critical CVE
- Best practices validation including support for Palo Alto Networks Best Practice Assessment (BPA)
- Organization standards enforcement
- Ongoing maintenance automation
In this blog post, we’ll look at some of the most popular automation elements among our customers.
#1 Monitoring Critical Services
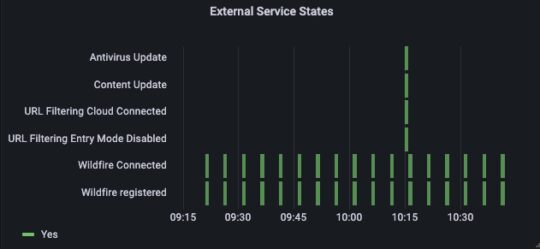
Firewalls depend on many external security services to get dynamic content updates for the latest threat intelligence. Services include advanced threat prevention, malware prevention, URL filtering, External Dynamic List (EDL), etc. A key capability of Indeni is ensuring connectivity to these external services is maintained at all times.
It goes beyond just constantly checking on the connectivity, but ensuring service registration is successful and vendor recommended best practices are followed. For example, if WildFire content update is not set to “every minute” and update action is not set to “download and install”, Indeni will generate a warning.
Another example is our support for EDL. It is important to ensure that the EDL list is not empty and it has not reached capacity.
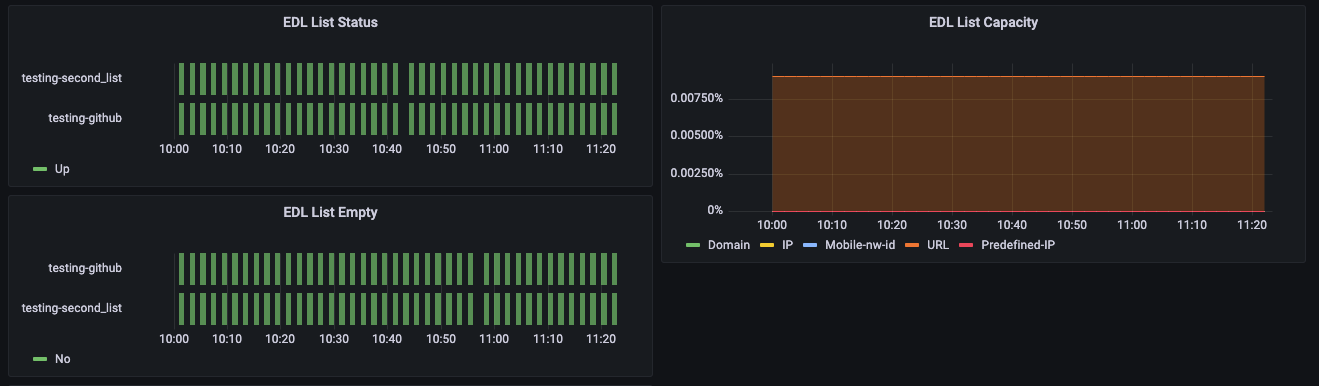
If the connectivity is lost, Indeni will even perform automated troubleshooting to determine the root cause of the connectivity problem.
#2 Automated Troubleshooting
When an issue is detected, Indeni will automatically apply device-specific domain knowledge to the problem. It will analyze the problem to accelerate root cause analysis. Let’s look at the previous WildFire connectivity problem as an example. Indeni first checks to see if the best server assigned for WildFire updates is reachable. If pinging fails, we will determine if it is due to DNS unknown host or unresponsiveness. If ping fails and DNS is working, we run a traceroute command to see if there is a route to the host. We then query the traffic log to see if traffic from the local service route IP address is blocked from reaching the destination IP of the WildFire Cloud IP address.
Complete workflow
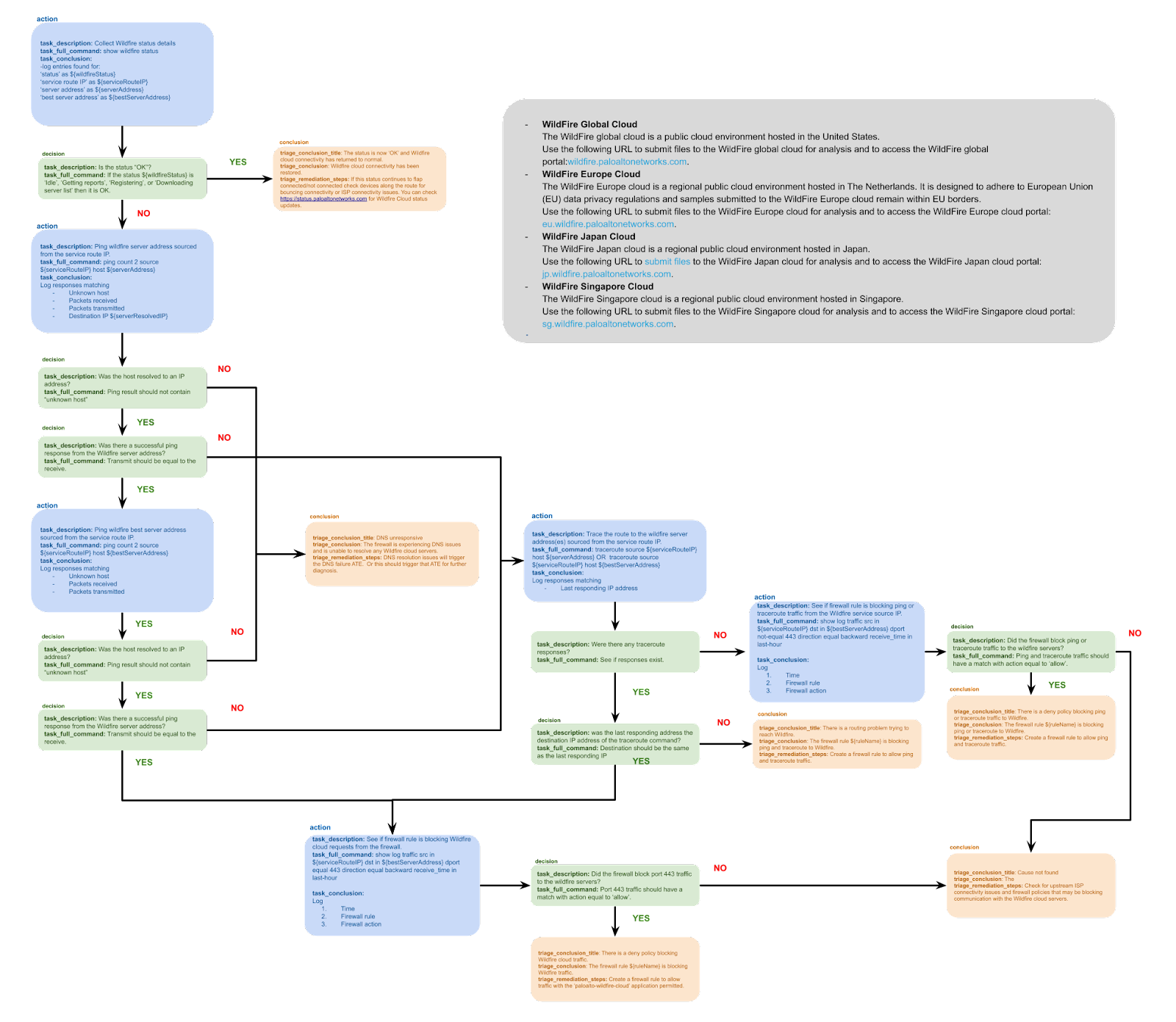
Automatically investigating a problem enables us to provide you with very detailed and prescriptive remediation steps to accelerate resolution. With the help from our community of experts and customers, we developed 20 Auto-Triage elements that are considered either business critical or common problems.
Auto-Triage Elements for Palo Alto Networks NGFW:
- BGP peer(s) down
- Cluster member no longer active
- Communication between management server and specific devices not working
- DNS lookup failure(s)
- Debug mode enabled
- Device restarted (uptime low)
- Disk RAID in error state
- Dynamic VPN in error state
- EDL(s) configured not reachable
- High ARP Cache
- High CPU usage per core(s)
- Logs are being discarded
- MAC cache usage high
- Maximum number of routes nearing (IPv4)
- NTP sync failure(s)
- Next hop inaccessible
- Permanent/Monitored VPN tunnel(s) down
- Temperature nearing maximum
- URL cloud not connected
- WildFire cloud status is not OK
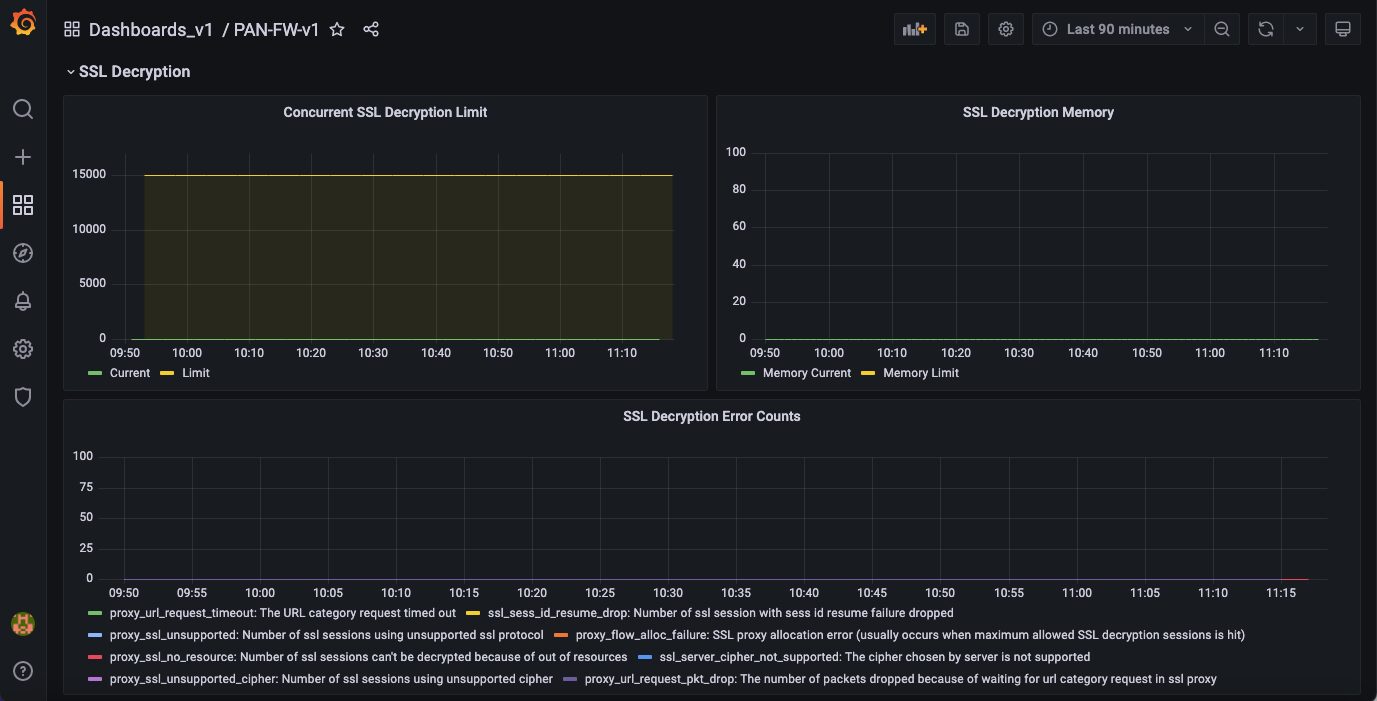
#3 SSL Decryption Visibility
Decrypting encrypted traffic can consume significant firewall processing resources. If firewall resources are an issue, it can affect performance. Measuring firewall performance is a great first step to understand the available resources. Measuring specific metrics relating to decryption traffic is essential. Receiving notifications about decryption sessions approaching limit and high memory usage enable you to take corrective measures before service is impacted.
#4 High Availability
Our support for high availability readiness has always been popular among our customers. An all time favorite is the check for synchronized static routes among the firewalls in a cluster. This is something people often forget to add to the standby firewall when a new static route is needed. Sadly, no one notices the missing static route until a switchover occurs when you actually need it!
Learn more about our high availability support here.
#5 Center for Internet Security Benchmark Automation
With cyber attacks on the rise, enterprises need to be hyper-vigilant about how they secure their firewalls. Device hardening is necessary to reduce the attack surface. Aligning to the Center for Internet Security (CIS) benchmark for Palo Alto Firewalls helps you strengthen your security with a best practice implementation. It can also improve your security compliance programs and posture.
Learn more about our support for CIS here.
Try Indeni
There, you have our top picks for Palo Alto Networks firewalls. You have made a big investment in security with your firewall and all the features it has enabled. Let us help you make the most out of your security infrastructure. For a complete list of Auto-Detect Elements, download here.
If you are new to Indeni, we encourage you to take Indeni for a spin and try out our automation capabilities.