As your enterprise gets faster—serving more users and devices across more locations, data centers, and clouds—you need network security solutions that do three things:
Continuously verify every query and endpoint
Proactively detect and prevent attacks
Resolve security incidents faster
BlueCat’s network security solutions help organizations use DNS data to resolve issues, stop attacks, and keep security risks from standing in the way of growth.
DNS security solutions for core-to-edge protection
Your network is getting bigger and more complicated every day. And without a specific DNS security solution at the core, you get more vulnerable every time you grow.
DNS is a popular attack vector: It’s simple, ubiquitous, and designed to serve queries without understanding their intent.
BlueCat’s DNS security solutions continuously and automatically verify the legitimacy of every query and endpoint so you can:
Eliminate risk
by applying policies that validate every interaction between users, devices, and endpoints
Prevent harm
by stopping attacks, breaches, and data exfiltration at the origin
Reduce time to remediation
by having a clear audit trail of actions
Automate compliance
by aligning your DNS policies with any compliance or regulatory requirements
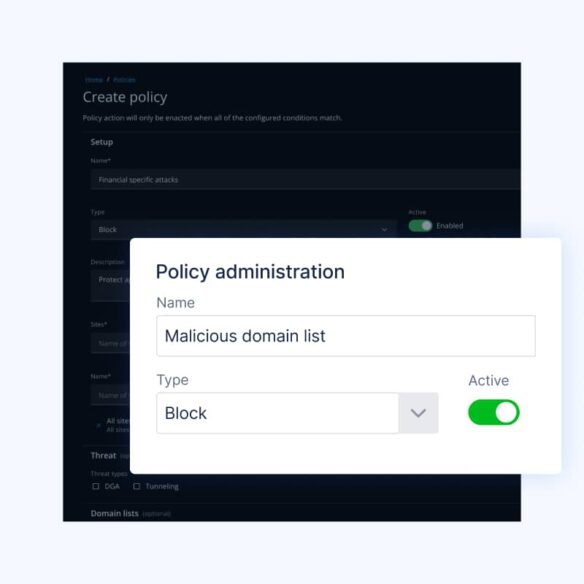
Cyber threat protection
BlueCat Threat Protection is like a DNS firewall that prevents devices on your network from querying malicious content.
It integrates DNS data with the latest security intelligence so your security teams can enforce policies that block threat sources from accessing your critical apps and data.
It’s fed by the most up-to-date threat intelligence from sources like Crowdstrike, BlueCat’s DoH block lists, and other third-party feeds—so you’re protected against new threats as soon as they emerge.
Zero Trust DNS
The traditional edge of your network is dissolving. It’s now more common for remote and hybrid workforces to access the services and apps they need from outside your network than from inside it.
Zero Trust is an evolving set of security principles that moves defense from fixed, network-based perimeters to focus on users, devices, and resources.
Zero Trust DNS is BlueCat’s framework to align and integrate your DNS, DHCP, and IP address management (together known as DDI) with your organization’s identity services and pre-existing Zero Trust policies and strategies.
Our Zero Trust DNS features are guided by three development principles:
Continuous verification
- Session and destination verification
- Real-time threat intelligence
- Integrated with user identity
Least-privilege access
- Block, track, and report on unauthorized DNS access
- Track user and device access to DNS data by role (using role-based access control and Zero Trust network access)
- Privileged access management integration
Context and response
- Contextual DNS (understanding actions by who, what, where, when principles)
- Identify actions based on anomalous behavior
- SIEM or SOAR integration
Want to speak to someone?
Let’s talk about how DNS can make your network faster and more secure.
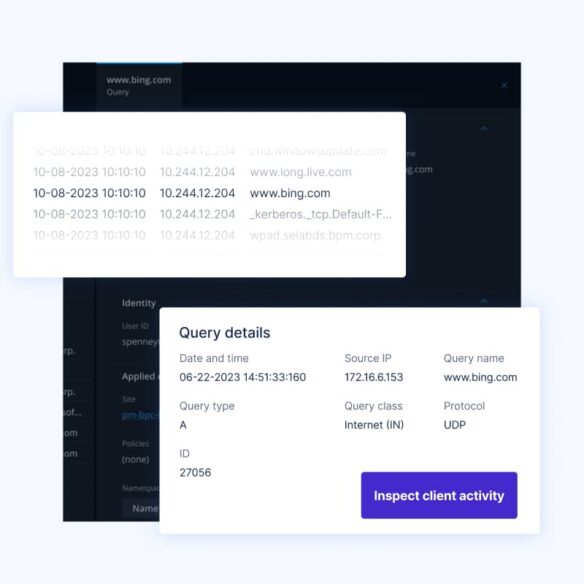
BlueCat Edge is our intelligent DNS resolver. It’s a caching and recursion layer that works in partnership with DDI products like Integrity and Micetro to handle outbound requests to the internet.
Edge deploys as a virtual machine at the first hop of every DNS query in your environment, tying every external request to a specific device (without needing an agent).

Tame complexity
Monitor and analyze every query and IP address to get full context—from one place and across any data center or cloud.
Drive performance
Reduce congestion and improve reliability with multiple optimized resolution paths and fewer overlapping zones.
Stop threats
Detect and stop external threats like tunneling, beaconing, domain generation algorithms, lateral attacks, and data exfiltration.
Prevent downtime
Create DNS redundancy for any environment. Centralize all DNS resolution under Edge, or failover to it from cloud-native DNS resolution.
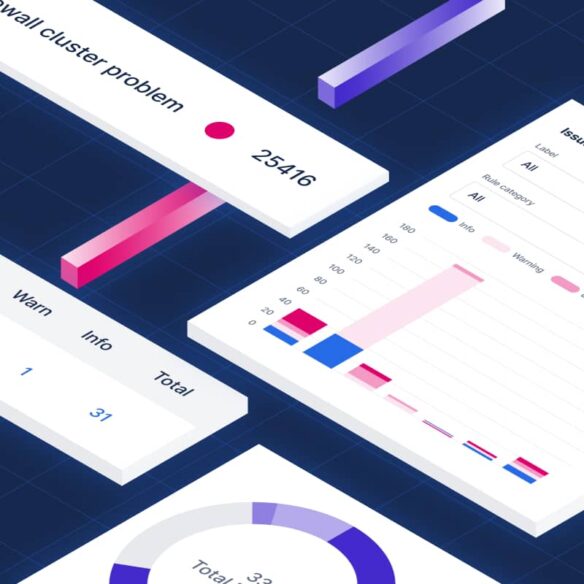
BlueCat Infrastructure Assurance is a proactive observability, troubleshooting, and remediation solution for network and security devices like DDI, firewalls, and load balancers.
It continuously scans your network and security infrastructure for signals of risk, performance, and availability issues.
Then it generates alerts and provides a list of recommended remediation steps from an expert-curated knowledge base that IT operations teams can use to resolve problems before they cause significant damage.
Integration with APIs and applications
IT team efficiency with the integration of email, syslog, APIs, and SNMP traps
Auto-detection
Continuous analysis of device metrics to track health posture and proactive notifications of issues before impact
Auto-triage
Autonomous or manual CLI commands and API queries and visual root cause analysis
Automated configuration backup
Scheduling of daily, weekly, or monthly device backups for common firewalls
Operations and troubleshooting tools
Visual tracking of health metrics over time, custom reporting, and scheduling for risky or noncompliant devices
Cisco Umbrella integration
BlueCat Edge integrates with Cisco Umbrella to help security teams enforce policies, filter malicious traffic, and get full visibility and protection for all local DNS traffic leaving your environment (to SaaS apps or the open internet).

Splunk integration
BlueCat Edge lets you bring the most critical DNS data into Splunk so you don’t have to pay excessive storage costs for all your data. And we make it easy to explore and filter to find patterns that can help you with analysis and reporting.

Additional features

Control malicious domains
Create, control, and block a list of suspicious or malicious domains—enriched with real-time threat updates.

Enforce policies
Prevent harmful or suspicious user activity with forwarding and steering policies that enforce role-based permissions.

Prevent DNS tunneling
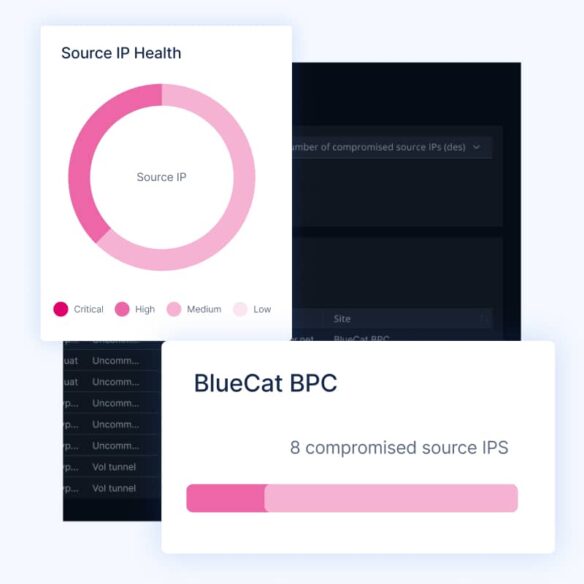
Detect and prevent DNS tunneling and data exfiltration with advanced pattern recognition and volumetric analysis.

Discover most compromised endpoints
Use risk scoring and traffic analysis to see the most common and riskiest query destinations—like from bad actors typosquatting.

Advanced DGA detection
Use machine learning models to identify and block malicious endpoints made using domain generation algorithms (DGAs).

Create trust policies
Log matches to determine which devices have attempted to access known malicious content.

Identity-based protection
Match IP addresses to user IDs to understand and track user behavior across different devices.
Related solutions

Network observability and health
Network health is about proactively identifying and preemptively remediating issues — across security, performance, uptime and maintenance.

Unified DDI
Bring DNS, DHCP & IPAM into one centralized, highly visible, secure, and automated function—via orchestration or authoritative appliance.

Network automation and integrations
Automate and simplify DNS ops with premade and custom workflows, plugins & apps for network automation plus turnkey integration with 3rd-party apps.

Multicloud management
Discover and resolve across any cloud and help Ops teams build faster and more safely.
Technical resources
Ready to dive deeper? Explore our technical resources.
Want to speak to someone?
Let’s talk about how DNS can make your network faster and more secure.
