Indeni 8.2 Analytics Dashboard & Network Security Automation
New Platform Capabilities
1 – Analytics Dashboard
Continuing our Analytics Dashboard journey, we’re excited to share a few more enhancements to the dashboard.
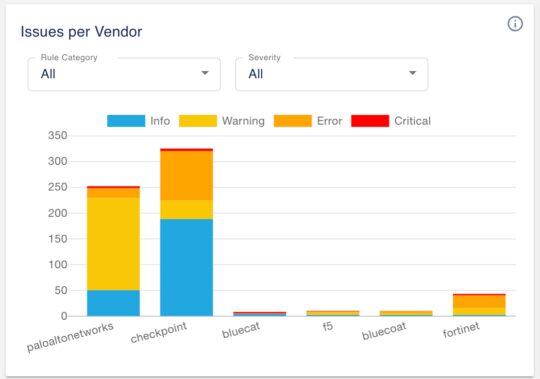
1.1 Issues per vendor
Our new and improved widget shows the number and the severity of the issues by vendor, instead of just showing the number of issues by vendor.
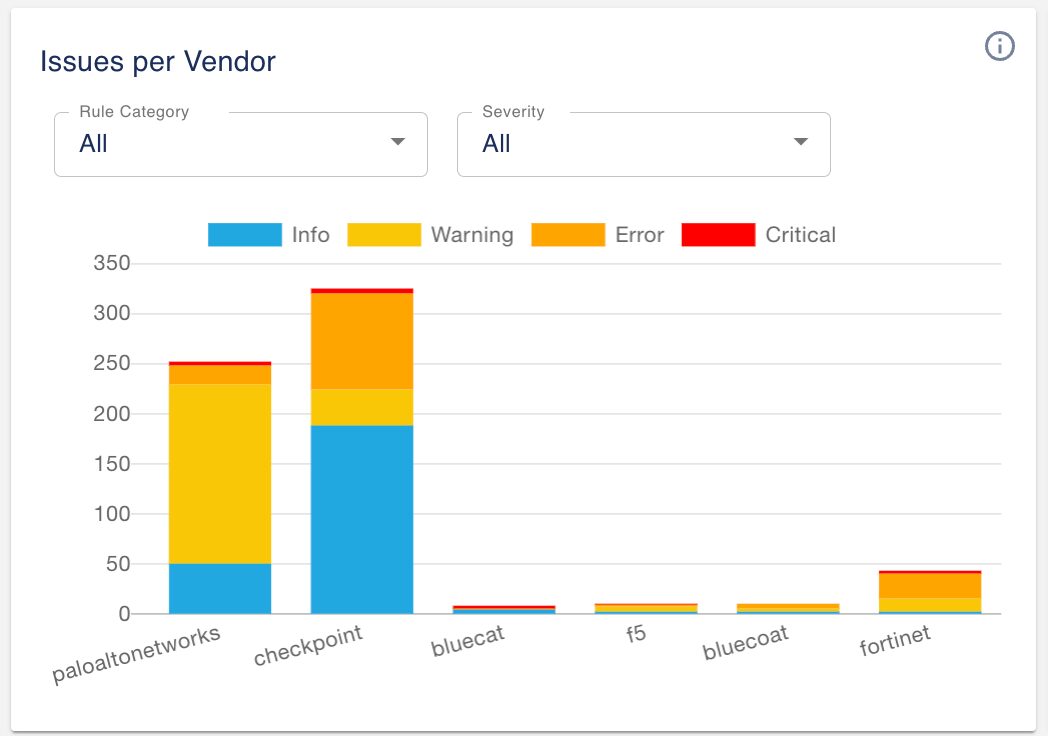
You can drill down by clicking on the bars to show critical, error, warning or information issues for the vendor. We also added the ability to filter by labels and severity. For example, clicking on the thin red strip for the Palo Alto Networks NGFW, the system will display the four critical alerts as shown below.
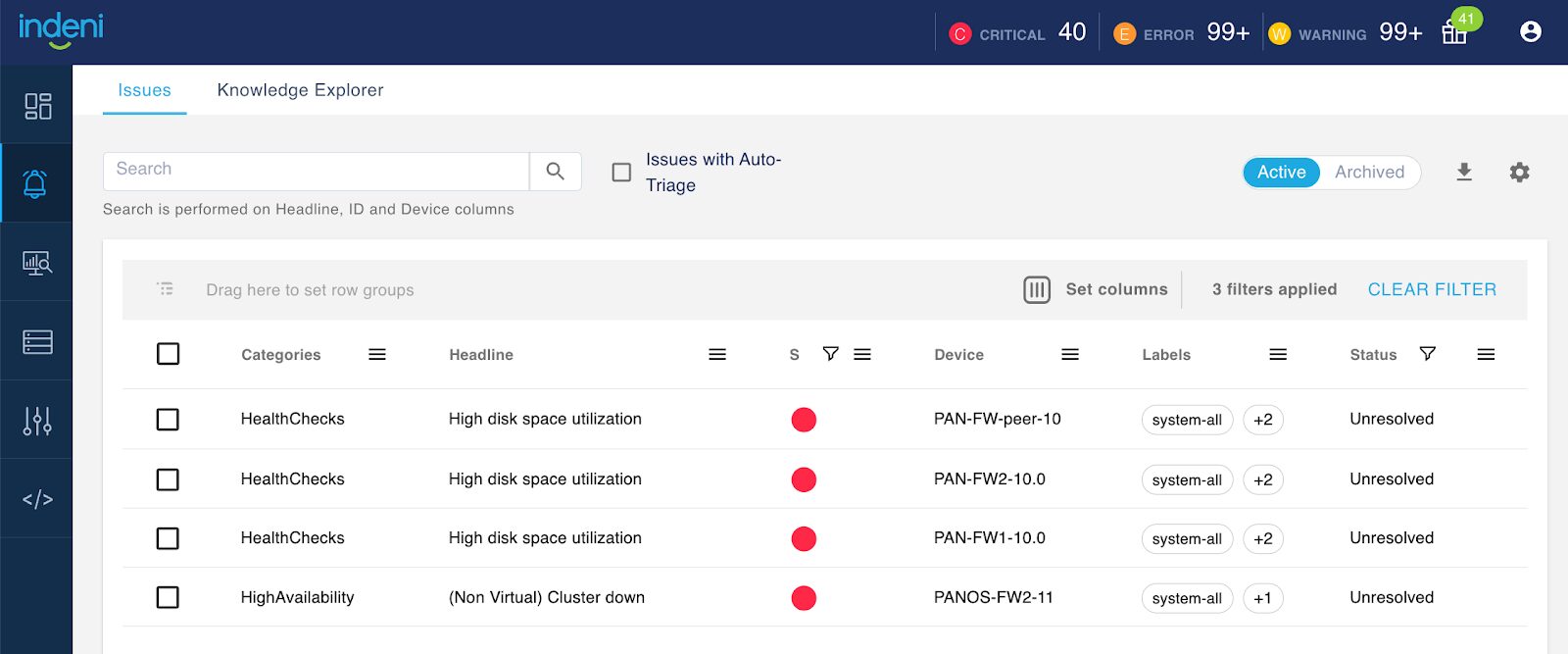
Notice the three filters from the issue page are set to:
- Vendor = panw
- Severity = critical
- Labels = system-all
With this enhancement we’re retiring the ‘Devices per Vendor’ widget.
1.2 Device connection status
Below is a new widget showing the number of devices you’ve added into the Indeni system.
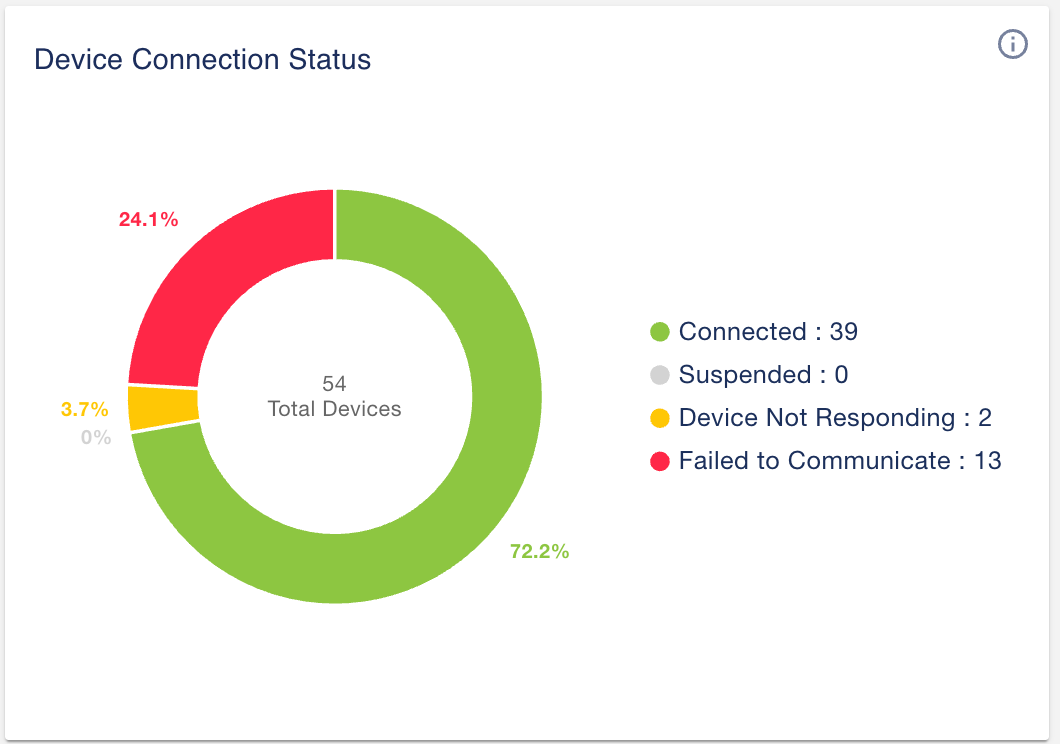
In this example, you have 39 devices connected to the system. Two out of the fifty-four devices are temporarily not responding to Indeni, and Indeni is unable to connect to thirteen of the fifty-four total devices.
This widget is particularly useful to draw your attention to the list of devices that you may have suspended for maintenance purposes. Some customers have, in the past, forgotten to resume automation for some devices after the maintenance window.
1.3 Device health by vendor
We enhanced the ‘Device Health by Vendor’ widget to help you quickly identify the number of devices in your environment with critical issues that need your attention.
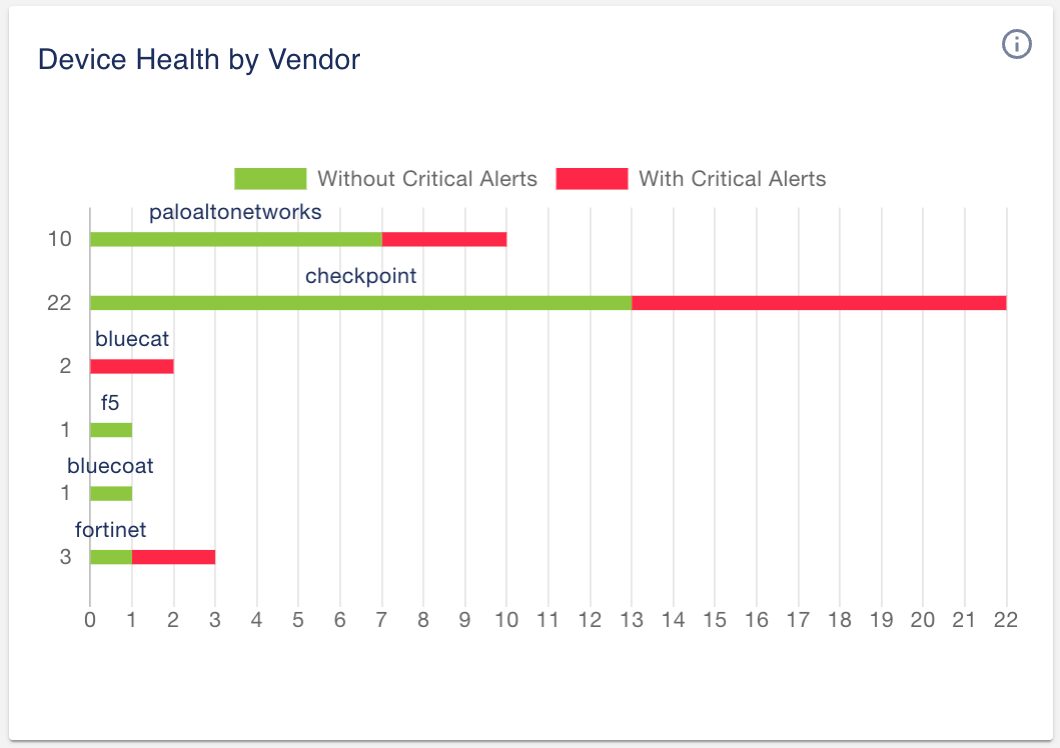
In this example, two out of the ten Palo Alto Networks NGFW have more than one critical issue. Similarly, nine out of the twenty-two Check Point devices have more than one critical issue.
1.4 Active issues by day of week
We added the ability to set severity as a filter. Going forward, we’ll add additional filters such as labels and a toggle to filter by unresolved or resolved issues, or both.
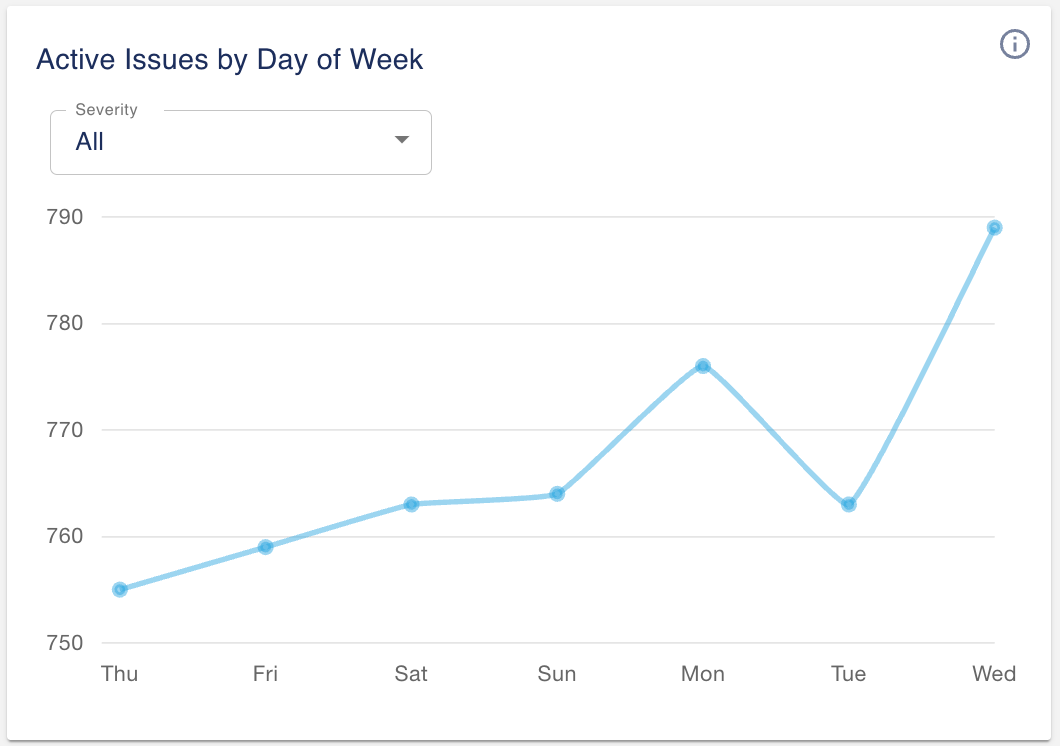
1.5 Issues resolved by day of week
This is a new widget intended to be used along with the above widget. The idea is to help you gauge if your issues resolved rate is faster than the incoming rate. This will become more intuitive once you can filter by resolved or unresolved issues (in the next release). For now, this simple widget gives you an idea what issues were resolved in the last week.

2 – Command-click usability enhancement
On a Mac machine, you can now use Command-click to start a new tab on your browser. This is for when you want to drill down from the dashboard to look at the list of issues in more detail.
3 – Credential sets enhancement
Customers would like to have Indeni alert when they are unable to connect to a device using the normal credential set and have to use a different credential set. For example, the customer policy is to use RADIUS credentials as the primary credential. If that fails, Indeni would fail over to the local credentials and notify the users that the primary credentials failed.
To accomplish this, two new features are developed:
- User credential sets by a sort order where Indeni sorts by the bitmask of the subnets. For example, /32 will come before /28. You can create multiple credential sets as follows:
- Default (0.0.0.0/0) using indeni-user
- Narrower (/24) using indeni-user
- Even narrower (/32) using indeni-admin
In this example, the system will use c. indeni-admin as a preference when connecting to a device. Then b. then a.
- A new alert is created to notify users if a user other than indeni-admin is logged into the device.
Effectively, if the primary credential set is used to connect to the device, no alert will be generated. If the primary credential set fails, Indeni fails over to the secondary credential with the username indeni, thereby causing an alert to be generated.
4 – Clone a report
Sometimes, you need to create reports that are only slightly different from a pre-existing report. Instead of creating a new report and re-applying all of the configurations, you can just clone it instead. This new feature allows you to quickly create a new report with the same data and visualization. For steps to clone a report, visit Custom Reports – Clone a report (toward the end of the chapter).
Platform Improvements
Online upgrade Process Improvements
- Online upgrade process
Enhance the online upgrade process to route the pip upgrade through service.indeni-ops.com. Previously, pip uses the OS-level proxy setting causing pip upgrade failure
- Dashboard
Enhance the dashboard to only count issues relating to the list of active devices. In other words, filter out issues relating to suspended devices. Previously, this caused discrepancies between the ‘Active Issues by Severity’ widget and the ‘Issues per Vendor’ widget
New Devices Support
For many years, Indeni customers have enjoyed the benefits of using Indeni to gain unprecedented visibility and the proactive nature of the solution has prevented many costly disruptions. With 8.2, BlueCat customers will gain an enhanced ability to maintain network resiliency and proactively manage their DDI infrastructure. We’re excited to announce our first release of support for BlueCat Address Manager and BlueCat DNS/DHCP Server. The use cases include:
- Stateful health checking
- xHA – High availability readiness
- NTP service availability
- DNS/DHCP monitoring
- Organization and BlueCat best practices conformance
More information can be found in the BlueCat LiveAssurance for Integrity Solution Brief.
Network Security Automation
1 – Check Point Secure Gateways
New Auto-Detect Elements:
- Alert when HTTP login deny logged
New improvement:
- Add description field to the “License expiration nearing” alert
Prior to this, the license expiration information looks like this:
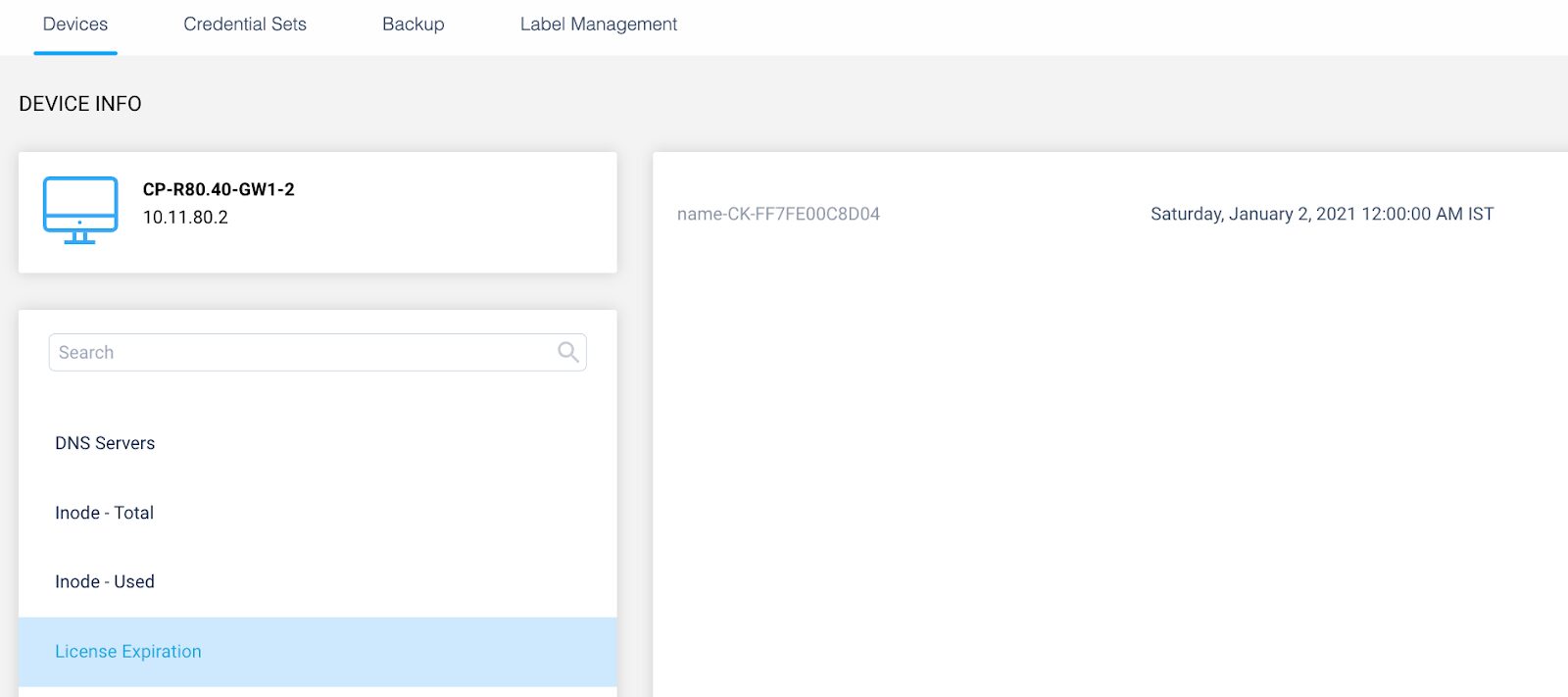
With this improvement, a more readable description is shown:
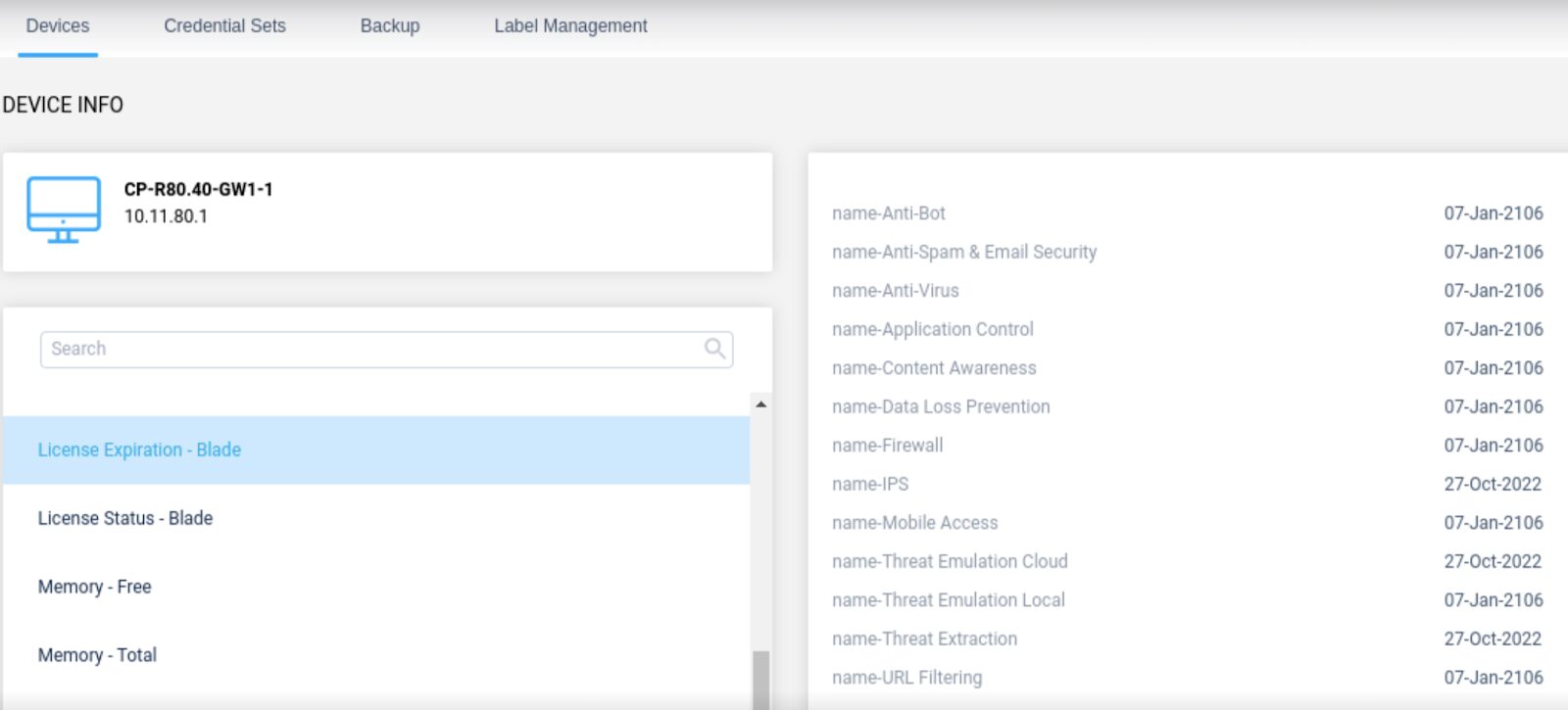
2 – New Auto-Detect Elements for Palo Alto Networks NGFW
- Alert when routes are changed
- Separate the ‘High CPU usage per core(s)’ alert for the management and data plane
- PANW Chassis – track line card status
- Monitoring zombie process(es)
- Six CVE’s:
- CVE-2023-0004 PAN-OS: Local File Deletion Vulnerability
- CVE-2023-0005 PAN-OS: Exposure of Sensitive Information Vulnerability
- CVE-2023-0007 PAN-OS: Stored Cross-Site Scripting (XSS) Vulnerability in the Panorama Web Interface
- CVE-2023-0008 PAN-OS: Local File Disclosure Vulnerability in the PAN-OS Web Interface
- CVE-2023-0010 PAN-OS: Reflected Cross-Site Scripting (XSS) Vulnerability in Captive Portal Authentication
- CVE-2023-38046 PAN-OS: Read System Files and Resources During Configuration Commit