The Future of Network Automation

Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
How to Move from Manual Operations to Self-driving IT
It’s no secret that automation is entering IT, and specifically the network and security space. At Indeni, the network automation platform, our customers have guided us in our evolution from Network Monitoring to Network Automation Platform. With over 1100 community members and leading customers in Financial Services, Healthcare, Retail and Government, it is very clear to us that this evolution is necessary for both individuals and corporations to remain competitive in today’s market. Let’s use the next 7 minutes to discuss how this evolution will take place, and how you should expect technology like Indeni to earn your trust and confidence along the way.
Why hasn’t network and security automation happened already?
Technologies for server automation such as Ansible, Puppet and Chef have been leading the way showing the productivity and agility possibilities programming can bring. However in network and security part of the infrastructure IT continues to use point solutions for monitoring and management. Why is this the case? Here are three reasons:
- Lack of APIs. As a symptom of of our industry’s hardware roots, many network and security devices do not have well defined APIs which makes it difficult to extract data or push commands to them. Unfortunately interacting with devices is done manually by writing commands through a CLI (Command Line Interface) which is highly error-prone and time consuming.
- Expert knowledge required. Majority of network and security devices have proprietary protocol stacks. This means you need an expert in that particular device to know how to extract and analyze the information. Many legacy devices are also still in use, which makes it hard to find expertise to manage the old and new technologies in your environment.
- Lack of time to learn new skills. Network and Security professionals are interested and capable of using automation tools, however they do not have the time. In our recent Network Automation Report firefighting was the #1 most time consuming task in their day to day. These professionals need a way to jump start their use of automation (read = turn-key), and once they have the bandwidth, begin writing code themselves.
Why Now? Adoption of private and public cloud technologies is gaining speed.
Our recent Network Security and Automation Trends report with GNS3, 73% rof respondents cited migrations to virtual and public cloud platforms are a top priority. In both cases, the cloud enables automation and a software-first approach. This is helping drive the desire for automation across the entire infrastructure (data center, campus, private+public cloud).
With this shift to the cloud, there are additional complications ahead as many cloud offerings replace components of existing network technologies, such as switching and routing, and introduce new networking concepts, such as AWS VPC. While cloud adoption is daunting to most network and security pros, it will be an opportunity for some. Operations teams that are able to efficiently and proactively manage a heterogeneous network will be able to leapfrog their competition.
So how do we capitalize on this?

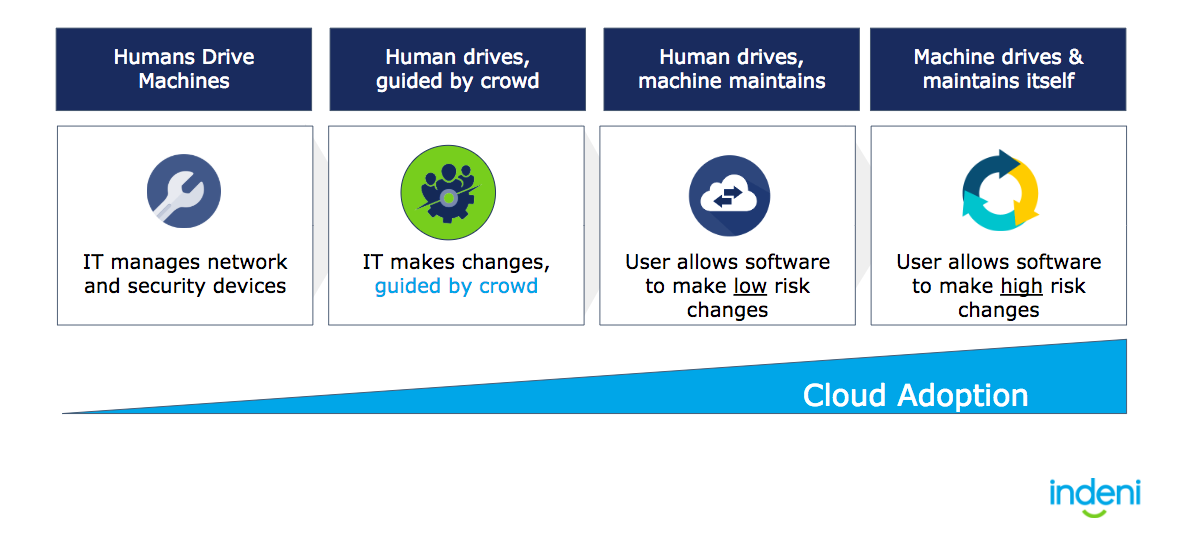
Let’s start with something familiar and fun, Cars. If you skip the phase where we used horses as transportation, and go straight to the moment we had powerful machines, there are four levels of automation that are taking place.
- Level 1 – Humans used to drive machines on their own with no external support.
- Level 2 – Waze was introduced and the crowd could help one another navigate events as they occurred.
- Level 3 – Automated maintenance was introduced from vendors like Tesla, so cars could help take care of themselves.
- Level 4 – Now we’re seeing the world of self-driving cars – removing the error-prone human from the equation, but allowing them to regain control in the event of an emergency.
Like Cars, Network and Security Devices are Becoming autonomous
Regardless of the use case, there is a multi-step process that encompasses data collection, identification of gaps, proposal of manual remediation, and then automating the proposed remediation. This is a crawl-walk-run method where users can move at their own pace by enabling software to first provide information in a read-only fashion, then to accepting suggestions, to at last allowing automatic behavior.
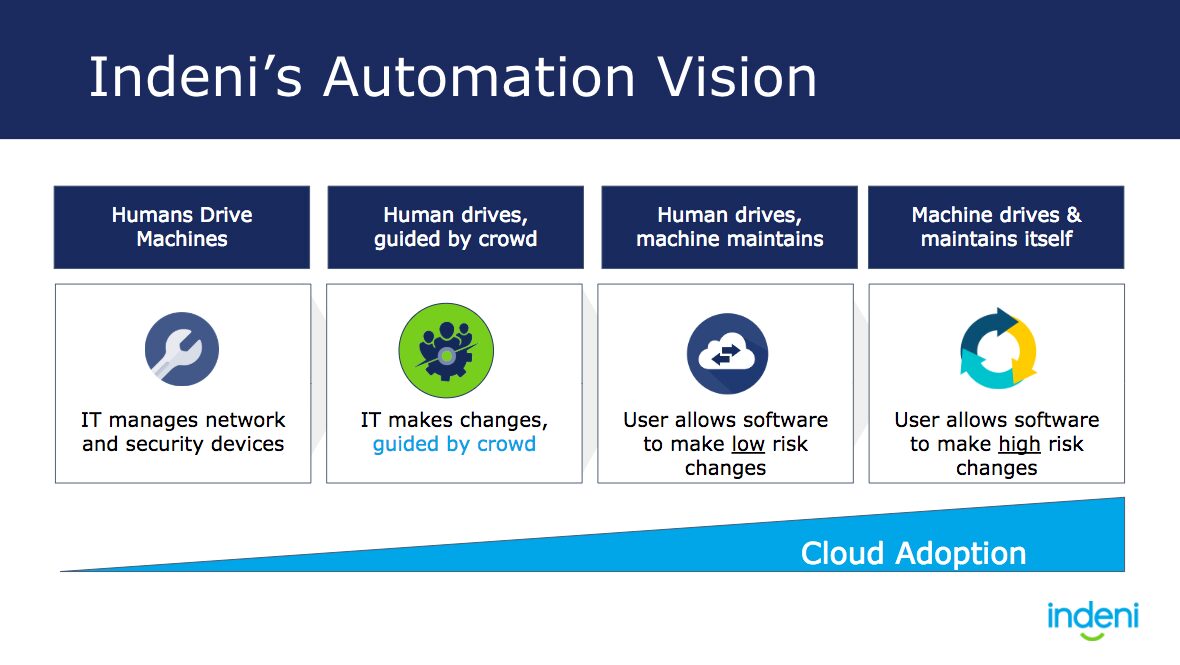
Level 1 – Manual. Humans manually run the network and do all of the maintenance
This is the all to common scenario today where one person gets pulled into crisis after crisis and is the primary person entrusted to make changes.
Level 2 – Advisory. Operations trusts the advice from the community.
Here is where Indeni is focused today. Similar to Waze for cars, Indeni leverages the wisdom of the crowd to guide other IT users to proactively avoid issues. Instead of being alone on the IT road, you can now get help from other peers. For example here are some of the issues that are reported and in turn automatically verified once complete:
- Compliance: Default security certificate used, HTTP server enabled or Weak security protocol used
- Fault management: High CPU usage, OS software version mismatch, Crowded information pathways causing dropped packets, VPN connection drop
- Provisioning: Vendor hardware / software becoming out of date
- Maintenance: SSL certificates about to expire
View all issues here
Level 3 – Automate Low Risk Changes.
The next step from here is not only consuming information and remediation recommendations from peers, but allowing software like Indeni to make low risk remediation changes. Some of these low risk tasks could be:
- Maintenance: Tuning of software, upgrade of hardware or virtual instance.
- Compliance: Update configurations where needed automatically
- Provisioning: Reconfigure or fix ones that need to be upgraded or decommissioned.
Level 4 – Automate High Risk Changes.
As more low risk tasks are completed successfully, administrators will trust the software. This evolution of trust, and understanding of how the code works (what metrics it measure, the rules it applies, what happens once it makes a change). Only once we’ve gained that trust will IT allow platforms like Indeni to move into higher risk changes. That’s when we will arrive at the Final step of self-driving IT
- Compliance: Auto-tuning to ensure performance goals are met
- Fault management: Automate upgrade OS software
- Provisioning: Automatically provision new devices
Our crowd-sourced automation platform is powered by thousands of IT engineers. Together they solve some of the toughest problems such as how to automate routine validation tasks for maintenance, cluster availability, network visibility, compliance and security best practices. Automation is enabling IT leaders in Financial Services, Retail and Healthcare to reduce re-work and deliver projects to the business at faster rates. Let’s build a self-driving solution together.



