IPv6 DDoS attack is a warning to protect your network
The first IPv6 DDoS attack surfaced in 2018. While IPv6 is more secure than IPv4, if bad actors want to attack your network, they will find a way.
First IPv6 DDoS attack foreshadowing: Protect your IPv6 networks now
In early 2018, reports surfaced of the very first IPv6 DDoS attack. It was spotted by network engineers who warned it could be a harbinger of cyber infiltrations to come.
Wait a second—wasn’t IPv6 designed with security in mind? So, how did this happen?
While not exceptionally vast or severe, the attack provides an important reminder: nothing is invincible. It’s critical to incorporate IPv6 into your network security model and to do so now.
In this post, we’ll first remind you of some of the IPv6 fundamentals. Then, we’ll explore the details of the attack. Finally, we’ll discuss some of the security implications and precautions to keep in mind as the internet transitions to IPv6.
Before IPv6 DDoS, a quick IPv6 primer
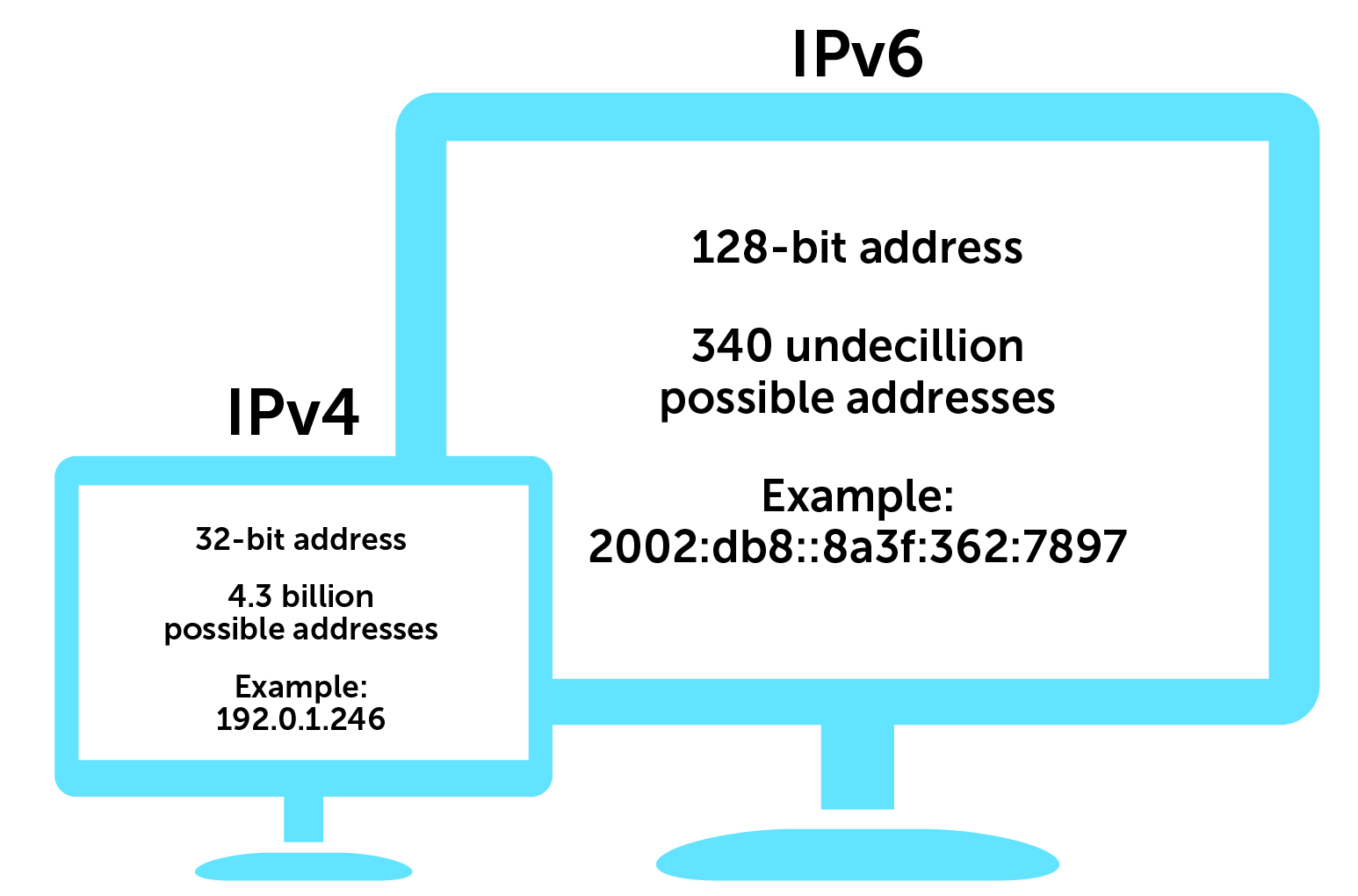
IPv4, or internet protocol version 4, uses 32-bit addresses (for example, 192.0.1.246), to route most of today’s internet traffic.
A 32-bit address space limits the number of unique hosts to 232, which is nearly 4.3 billion IPv4 addresses. But in today’s ultra-connected world, where every device from your smartphone to your doorbell camera now has an IP address, it turns out that 4.3 billion isn’t nearly enough.
In 2011, the Internet Assigned Numbers Authority (IANA), the global coordinator of IP addressing, ran out of free IPv4 addresses to allocate to regional registries. Since then, regional registries have nearly exhausted those allocations.
IPv6, the most recent version of the internet protocol, uses 128-bit address space. Unlike IPv4, both letters and numbers are used as identifiers (for example, 2002:db8::8a3f:362:7897). By implementing these changes, IANA created 2128 new IP addresses, which makes the number of possible IPv6 addresses about 340 undecillion or 340 billion billion billion billion.
IPv6 has some obvious advantages, the primary one being that it’s a lot more space.
Details of the IPv6 DDoS attack
Wesley George, a network guru at Neustar, noticed some strange activity during his work for the company’s DDoS protection services. As part of a larger attack on a Neustar DNS server, he told tech publication The Register that he noticed that there were “‘packets coming from IPv6 addresses to an IPv6 host.’”
Computers behind 1,900 different IPv6 hosts on more than 650 networks were attacking the DNS server as part of a larger group of overtaken systems, according to The Register. Of those 1,900, Neustar observed that 400 were used by poorly configured DNS systems. And about a third of the overall attack traffic came from those servers.
What the IPv6 DDoS attack says about DNS security
A DNS amplification attack relies on publicly accessible DNS servers to overwhelm a victim with DNS response traffic.
For many years, the internet community has identified and patched open IPv4 DNS resolvers because they can be used in amplification attacks. But that effort has been do-able in large part because the IPv4 space, at approximately 4.3 billion addresses, is scannable.
However, at 340 undecillion possible addresses, the scale of IPv6 makes it nearly impossible to scan for misconfigurations and potential vulnerabilities. And if those DNS resolvers can be exploited in the same manner on an IPv6 network, then we’re in trouble.
Other potential security flags for IPv6 include the incompatibility of some network security tools. IPv6 packet headers are also much longer and more complex than their IPv4 predecessors, providing more potential attack vectors.
Like the attack that he witnessed on Neustar, George suggested to The Register that combination IPv4 and IPv6 attacks could be especially detrimental. A network admin might use all the usual attack mitigation tools but only kill off the IPv4 traffic. This would leave the network still under attack from IPv6, without a response tool at the ready.
Routers and switches on dual-stack networks, which allow the network to handle IPv4 and IPv6 connections simultaneously and have been implemented at some large enterprises, are also vulnerable.
Protecting your network from an IPv6 DDoS attack
The security strengths of IPv6
Overall, IPv6 protocol is much stronger security-wise. It was built from the ground up with security in mind. On the other hand, IPv4, which has been in place for more than 35 years, has had modern-day security measures tacked on after the fact.
Furthermore, IPv6 traffic still isn’t ubiquitous enough for bad actors’ exclusive attention. And most IoT devices, which have gaping security holes that attackers regularly exploit, are incompatible with IPv6.
But that doesn’t mean you should let your guard down.
Act now to secure IPv6 networks
Take this attack as a precautionary tale. If you’re implementing an IPv6 network, ensure it has the same level of security and mitigation tools as your IPv4 networks. Different teams might be running each network in parallel, and not necessarily on the same page security-wise.
With the huge increase in the total number of IP addresses under IPv6, hackers now have many, many more addresses to leverage.
While not a huge attack volume this time around, it’s a sign of what’s possible down the road. Bad actors will most likely continue focusing on IPv4 vs IPv6 for now. But it is only a matter of time before they shift their sights to the latest internet protocol version.
Unfortunately, too many enterprises are getting IPv6 networks up and running and worrying about securing them later. But no one wants to respond reactively to a cyberattack. Now is the time to get your network security protocol and tools in place for IPv6.
BlueCat’s platform can help you manage and secure your new slice of IPv6 addresses, especially as you transition to IPv6 DNS. We also offer virtual instructor-led training on IPv6 for DNS, DHCP, and IP address management.




