DNS security is crucial for network defense
DNS security is a concept—not a single practice, protocol, or extension. At its most basic level, DNS security is about leveraging your DNS to better secure your enterprise network.
The Domain Name System (DNS) was built foremost to correctly and efficiently respond to queries, not question their intent. As a result, DNS has real vulnerabilities and potential as a vector for cyberattacks.
DNS is usually thought of as something that needs to be protected. Indeed, a DNS attack can take various forms. But industry watchers like Gartner now recognize DNS security as crucial for improving the overall defense of your network.
At the strategic level, DNS security means you are incorporating DNS into your overall network security plan. Operationally, it means using DNS security best practices to secure vital assets on your network (in conjunction with other tools, of course). There are several methodologies and DNS security solutions that you can deploy.
Common DNS attack types
A DNS attack is one in which a bad actor either tries to compromise a network’s DNS or takes advantage of its inherent attributes to conduct a broader attack. A well-orchestrated DNS attack can bring an organization to its knees.
There are four main types of DNS attacks.
DoS, DDoS, and DNS amplification attacks
When most people hear of a DNS attack, they think of denial-of-service (DoS) attacks or distributed-denial-of-service (DDoS) attacks. In both cases, attackers flood internet servers with so many requests that they simply can’t answer them all, and the system crashes as a result.
A DoS attack uses one computer and one internet connection to flood a remote server. In a DDoS attack, multiple computers and internet connections target a site. Often, DDoS attacks add compromised computers to a botnet that runs malicious queries in the background. Attackers can then harness the power of infected devices around the world to query the targeted network all at once.
A DNS amplification attack is a type of DDoS attack in which attackers use publicly accessible open DNS servers to flood a target with DNS response traffic. An attacker sends a DNS lookup request to an open DNS server with the source address spoofed to be the target’s address. When the DNS server sends the DNS record response, it is sent to the target instead.
DNS hijacking
There are three types of DNS hijacking:
- Attackers can compromise a domain registrar account and modify your DNS nameserver to one that they control.
- Bad actors can change the A record for your domain’s IP address to point to their address instead.
- Attackers can compromise an organization’s router and change the DNS server that automatically gets pushed down to each device when users sign on to your network.
The result is that attackers can phish for login credentials or trick a user into clicking on a link that downloads malware. They can even sometimes display advertisements that generate revenue for the hacker.
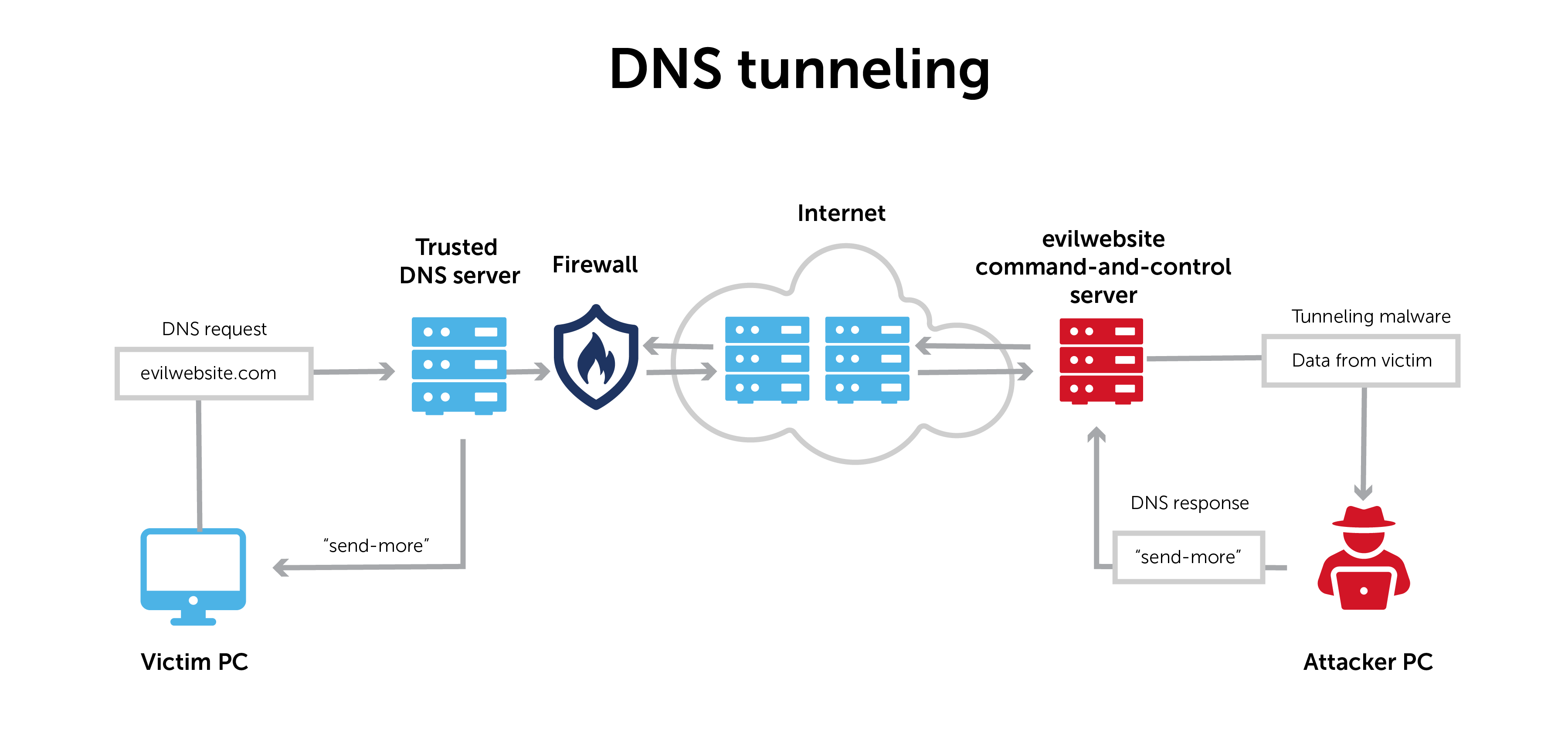
DNS tunneling
DNS tunneling transmits information through the DNS protocol that usually resolves network addresses.
Normal DNS requests only contain the information necessary to communicate between a client and a server. DNS tunneling inserts an additional string of data into that pathway. It establishes a form of communication that bypasses most filters, firewalls, and packet capture software.
That makes it especially hard to detect and to trace its origin.
DNS tunneling can establish command and control. Or, it can exfiltrate data. Information is often broken up into smaller pieces, moved throughout DNS, and reassembled on the other end.
DNS poisoning and cache poisoning
DNS poisoning (also known as DNS spoofing) and its cousin, DNS cache poisoning, use security gaps in the DNS protocol to redirect internet traffic to malicious websites. These are sometimes called man-in-the-middle attacks.
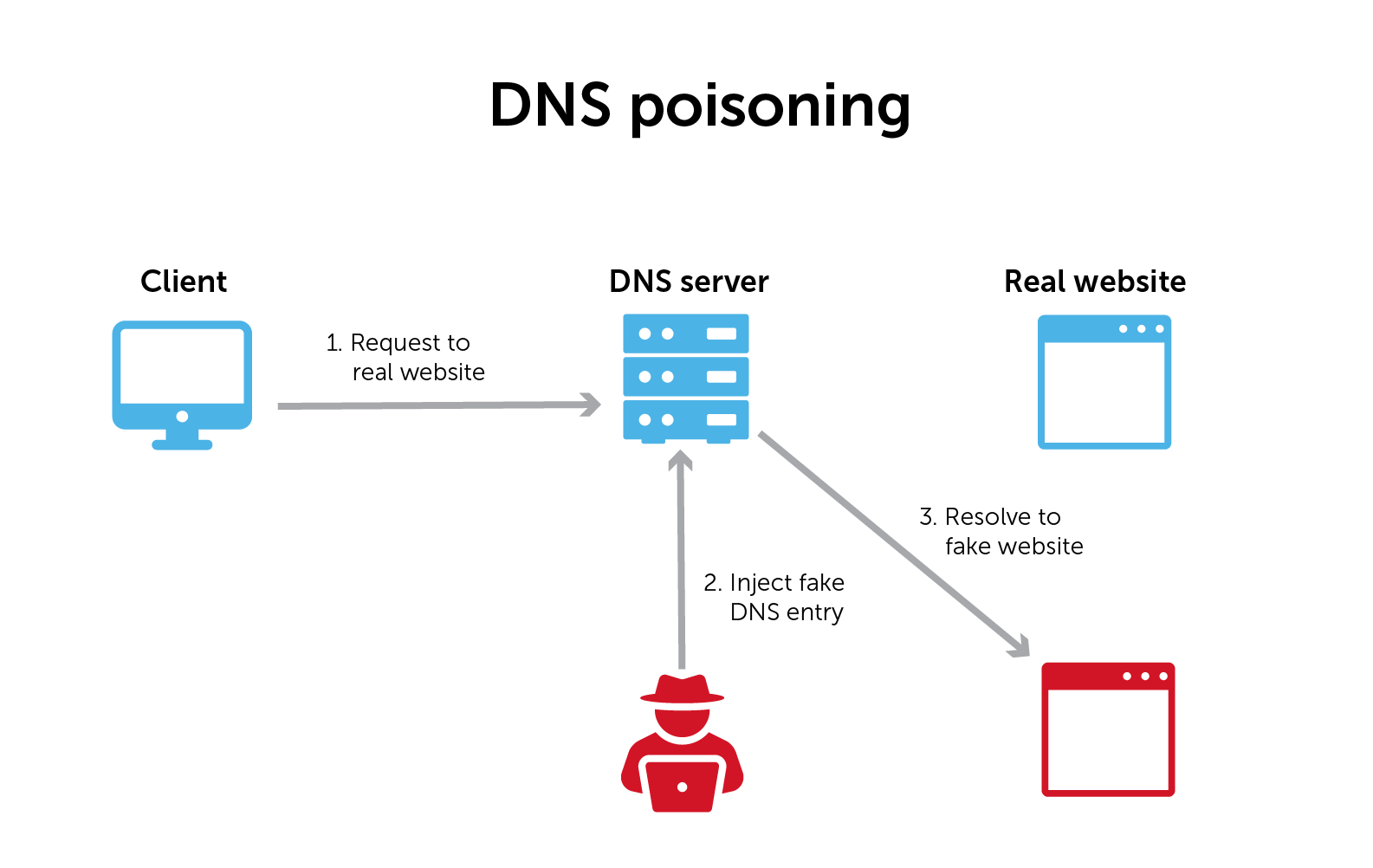
When your browser goes out to the internet, it starts by asking a local DNS server to find the IP address for a website name. The local DNS server will ask the root servers that own that domain, and then ask that domain’s authoritative name server for the address.
DNS poisoning happens when a malicious actor intervenes in that process and supplies the wrong answer. Once it has tricked the browser into thinking that it received the right answer to its query, the malicious actor can divert traffic to whatever fake website it wants.
In DNS cache poisoning, once a malicious actor intercepts and ‘answers’ a DNS query, the DNS resolver stores that answer in a cache for future use. (Most DNS resolvers are caching resolvers.) In this case, it makes the attack worse by continuing to supply that wrong answer.
The road to secure DNS
There are measures that you can take to help ward off DNS attacks. Two very common tactics are DNS firewalls and DNSSEC.
DNS firewalls
A DNS firewall uses your network’s core infrastructure in real-time to block, monitor, or redirect users attempting to access known malicious domains.
Standard firewalls tend to use complex, proprietary, and expensive signature detectors that don’t always catch DNS-based malware and threats. These firewalls detect and block all kinds of other general threats and prevent malware from entering networks.
Meanwhile, by operating at the protocol layer, a DNS firewall can go even deeper to protect a larger part of the threat landscape. For example, some firewalls can protect against data exfiltration through the DNS protocol itself by identifying DNS tunneling.
DNSSEC (which is not shorthand for DNS security)
While some may think that DNSSEC is shorthand for DNS security, it’s not.
DNSSEC stands for Domain Name System Security Extensions. It is a set of specifications that uses digital signatures based on cryptography to authenticate DNS queries and responses.
DNSSEC helps a DNS server answer the following questions:
- Is the root or authoritative name server (also sometimes called an authoritative DNS server) authorized to provide a query response?
- Can I trust the content of the query response?
- Can I trust that there were no modifications to the response in transit
Normal DNS resolution cannot screen the responses it gets and answer the three questions above. DNSSEC validates responses to DNS queries before returning them to the client device.
DNSSEC uses digital signatures stored in name servers alongside common DNS record types.
At the center of DNSSEC is a public-private key pair. Each DNS zone has a public key and a private key. Public key cryptography is the starting point for DNSSEC validation. Available to everyone, a public key provides the means to decrypt messages signed by a corresponding private key.
DNS security as part of your defense strategy
While DNS has historically been seen as a naive pawn in attacks, it can also be a proactive part of a good defense-in-depth strategy. Along with Gartner, U.S. government agencies like the NSA have recognized DNS as crucial for improving the overall defense of your network.
The concept of protective DNS now exists to describe DNS as critical to protecting against network threats.
Filters, firewalls, on-device agents, and other security platforms are effective at using real-time threat intelligence to scour or shield different parts of the network. And certainly, DNS services offer some security measures.
But DNS data can also provide critical contextual information to clue you into what might be happening on your network. You can discern who’s there, what they are trying to access, and aberrations in normal activity patterns.
Ensure a more protective DNS security posture
Here are some basic steps to ensure you have a more protective DNS security posture:
- Know your entire DNS infrastructure. For starters, securing a network requires awareness of your enterprise’s entire DNS estate. Often, network teams lack complete visibility thanks to a mess of DNS silos, orphaned zones, or shadow IT.
- Log and monitor DNS queries and response data. Logging and monitoring outbound and inbound DNS traffic is the first step to detecting anomalies. Furthermore, your response data provides contextual information that allows for a more thorough forensic analysis.
- Harden your recursive DNS servers. Protect recursive servers from unwanted access and tampering through DNSSEC, access controls, and other architecture enhancements.
- Tighten admin access to your DNS. Enable multi-factor authentication on your domain registrar account and use a registrar lock service to request your permission before changing DNS records.
How BlueCat can help
With BlueCat, you can find threats faster and get full visibility into internal and external network traffic. You can systematically gather and analyze query and response data in one place, giving you a complete picture of the DNS activity on your network.
Furthermore, with BlueCat DNS Edge, you can apply threat intelligence and set policy-based rules to block, allow, or manually watch certain domains.






