NSA and CISA: Protective DNS key to network defense
U.S. cyber agencies now point to protective DNS as a defense strategy, confirming what BlueCat already knew: DNS is critical to detecting network threats.

U.S. federal cybersecurity agencies now point to protective DNS (PDNS) as a defense strategy, confirming what BlueCat has long understood: DNS is critical to detecting network threats.
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) recently released guidance for using protective domain name system (PDNS) services to curb cyber threats. It also points to several providers—BlueCat among them—for organizations to consider.
“DNS has historically been seen as a service that needs to be protected, as opposed to being part of the protection plan,” says BlueCat Chief Strategy Officer Andrew Wertkin. “This newly published guidance means they’re recognizing the need to use DNS as an essential part of an agency’s overall security architecture.”
BlueCat’s platform has long provided this capability. In fact, BlueCat’s biggest customer, with the most extensive deployment of BlueCat’s version of protective DNS, is a large federal agency. As a result, there is now regular detection and remediation occurring in their most sensitive environments where they had previously thought that DNS-based security risks didn’t exist.
This post will first examine how protective DNS works. Then it will delve into why it has become a requirement in any sound layered network defense strategy. And finally, it will look at how BlueCat Edge provides protective DNS and beyond.
The basics of how protective DNS works
Protective DNS is a service that analyzes DNS queries and mitigates or blocks connections to malicious domains. It uses existing DNS protocol and architecture to do so.
PDNS uses a DNS resolver (also called a recursive resolver) that returns answers based on policy criteria. This is often dubbed response policy zone (RPZ) functionality.
It not only checks the outbound queries but also examines the responses and returned IP addresses against all available threat intelligence. This intelligence is culled from open source, governmental, and security service commercial feeds.
It then prevents connections to known or suspected malicious sites or redirects requests to non-malicious sites. Or it can return an NXDOMAIN response.
PDNS providers also collect and store the logs of all these DNS queries, responses, and IP addresses. For security teams, these logs can be a goldmine to search for intrusion clues following breach detection.
Why you need protective DNS
The DNS protocol was built with scalability—not security—in mind.
“We’ve seen threat after threat wherein DNS is a core element of the mechanism of the actual attack,” Wertkin says.
DNSSEC and DoH are not enough
PDNS is just one part—albeit a very crucial part—of overall DNS security best practices. Indeed, there are other DNS security enhancements in place already. DNSSEC uses cryptography to provide authentication and integrity for DNS queries. And DNS over Transport Layer Security (DoT) and DNS over HTTPS (DoH) mask human-readable client DNS queries and responses to promote privacy.
However, none of these address the compromise of DNS infrastructure or malicious DNS activity. (And in the case of DNS over HTTPS, it can actually significantly lower your detection capabilities by hiding DNS-based threats.)
Bad actors exploit DNS in a number of ways. This includes phishing attacks through typosquatting, data exfiltration like DNS tunneling, and malware distribution and command-and-control. It also includes evasive techniques like domain generation algorithms. Even the SUNBURST/Solorigate compromise relied on DNS for execution within unprotected organizations.
It’s finally a big deal for the U.S. government
The $1.9 trillion coronavirus relief package signed this month includes $650 million for bolstering federal cybersecurity. This investment, combined with the newly published guidance on protective DNS, is confirmation that DNS should be at the core of any organization’s defense-in-depth strategy.
BlueCat Edge provides protective DNS and so much more
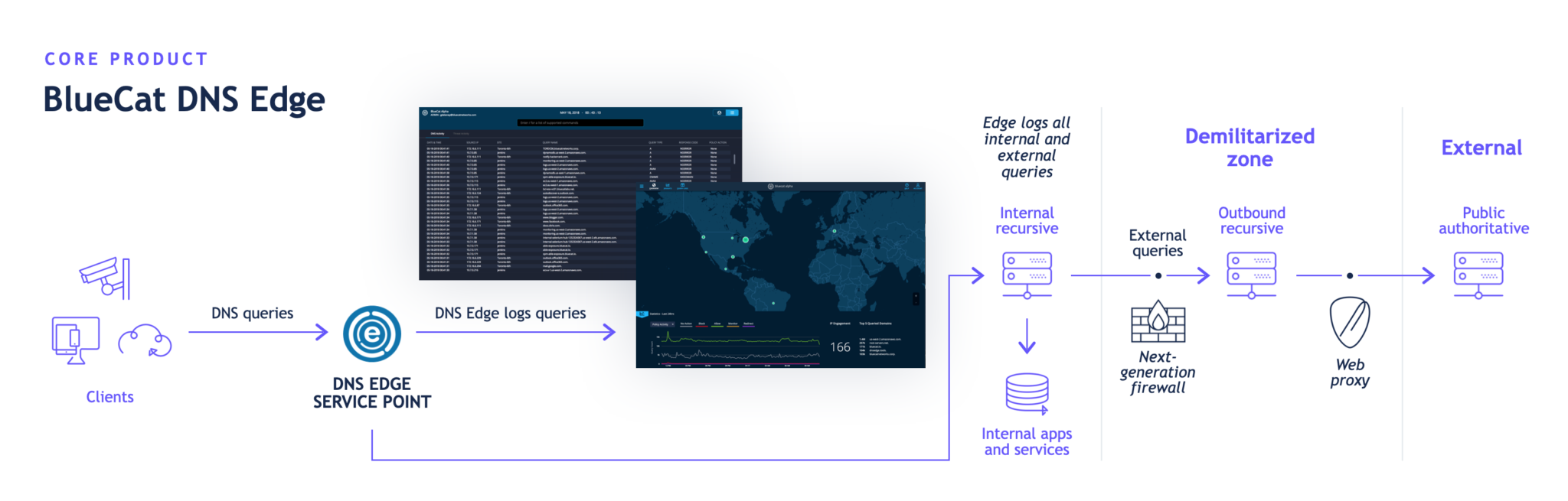
Named in the NSA and CISA guidance, BlueCat Edge is BlueCat’s DNS resolver. It gives cybersecurity and network teams shared visibility and control over internal and external DNS traffic through a single platform.
Edge seamlessly integrates security intelligence, including BlueCat’s blocklists, CrowdStrike, and other third-party threat feeds. It executes policy enforcement and granular content filtering based on queries, responses, valuable metadata, and custom domain lists.
Furthermore, Edge’s custom logging feature allows users to log DNS events for valuable insights wherever it suits them. That could be a private data lake or a security information and event management (SIEM) tool like Splunk.
Leveraging Edge and a SIEM tool together allows for automated sifting and detailed analysis of massive amounts of DNS data. It can not only alert security teams about known threats in real time but can also identify patterns that would have otherwise gone unnoticed.
A step further with internal queries
The NSA and CISA view PDNS as protecting against DNS queries egressing to the internet. But BlueCat regularly sees all sorts of indicators of compromise via internal queries as well.
As the DNS resolver, BlueCat Edge sees every query from every client device on the network. It works in a way that PDNS solutions sitting on the perimeter cannot.
Seeing this additional layer of traffic, called east-west traffic, allows security teams to establish organization-specific baselines. It can identify anomalous activity long before something approaches the network boundary or threat intelligence flags it. It also allows for identifying and shutting down complex, two-pronged attacks with both an inside and outside attack system.
Real results for customers
BlueCat’s largest customer leverages its Edge implementation to monitor and apply policies to 400 million internal DNS queries daily. Edge’s monitoring and policy application has allowed the organization to reduce remediation time by over 90%.
“It’s critical that companies and government agencies recognize the requirement for protective layers of DNS,” Wertkin says. “Protective DNS should be part of every security architecture. This way, you’re proactively looking for any DNS that is potentially indicative of a threat, as well as blocking it.”




