Everything you need to know about shadow IT
When users implement their own solutions behind the IT team’s back, that’s shadow IT. Learn about the risks and how to manage and reduce it with BlueCat.

When an IT department can’t or won’t give users what they want, users sometimes take matters into their own hands and engage in shadow IT. In other words, to get their work done, users sometimes develop their own IT solutions behind their IT department’s back.
A typical anecdote might go like this: Users in a branch office could not reliably access the mainframe at headquarters running mission-critical software needed to do their jobs. Yet IT would not invest in routers to correct the issue. A user quietly installed unauthorized soft routing on a server. Problem solved.
But in reality, the results vary. While shadow IT sometimes seems a convenient solution, it can end up causing more problems than it fixes.
This post will examine what shadow IT is and why it occurs. Then, it will delve into the primary drawbacks, as well as some upsides. Finally, it will discuss best practices for managing it.
What is shadow IT?
Shadow IT refers to acquiring and running information technology systems, services, solutions, or technologies without the knowledge or consent of the IT department.
It generally falls into five categories:
- Cloud computing services. Without IT’s knowledge, a developer with a need and a credit card signs up to test an application in AWS. Or a marketing VP believes Google Workspace is a better SaaS application for team productivity than IT-mandated Office 365.
- Unauthorized software. Users find an app that performs a task faster and more easily than the sanctioned application.
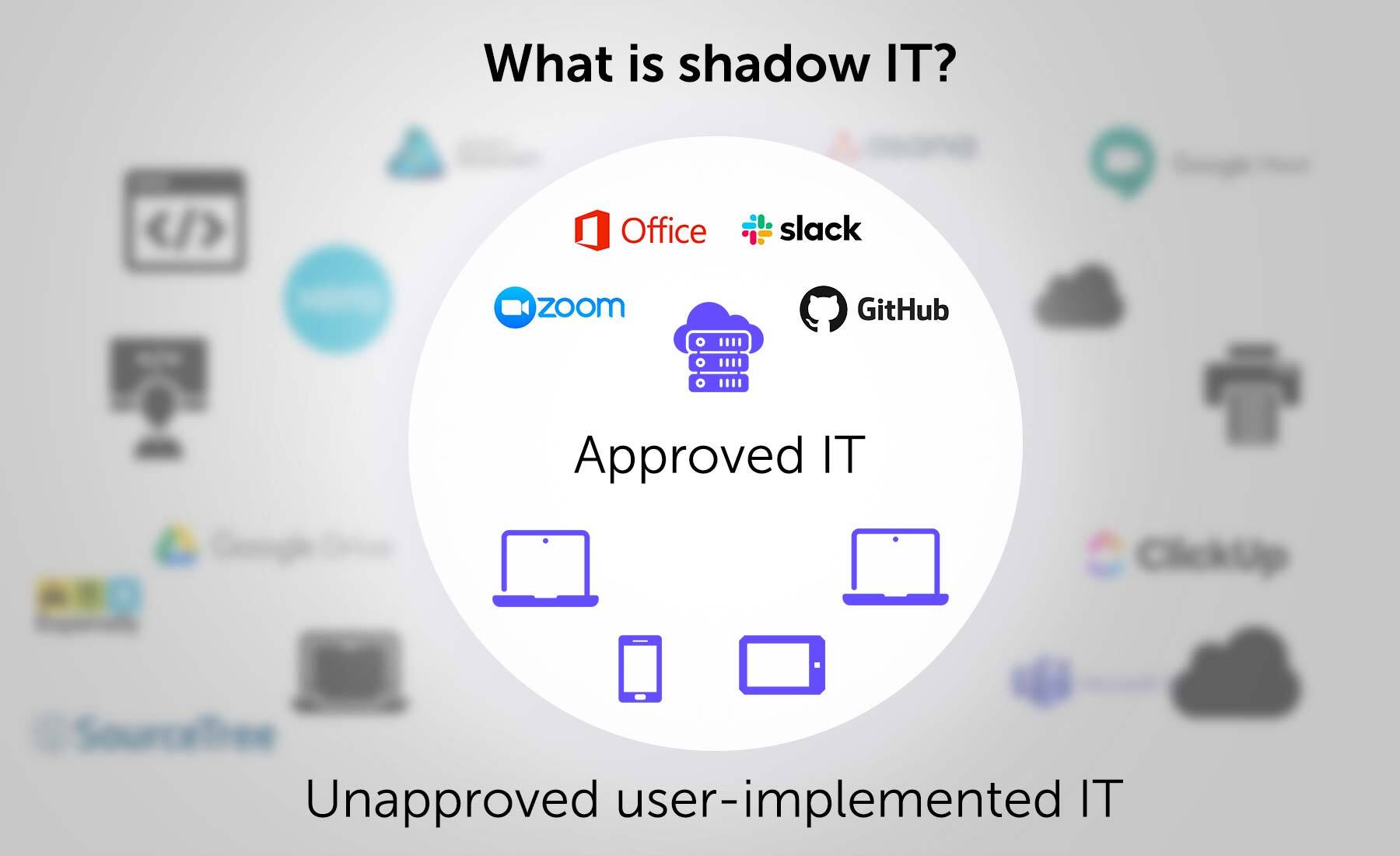
- Unauthorized hardware. When users flout the company standards with a device that does not meet spec. Perhaps it’s a smartphone, tablet, or even something as simple as a document scanner. Regardless, it’s unsupportable by IT.
- Unauthorized development. Lacking a needed database, a user may cobble something together in Microsoft Access. Or a user may code a quick program to perform a critical function more efficiently.
- Unauthorized use of resources. In the introductory example, the user who installed soft routing was not on the server team and should not have been able to access that server.
Why does shadow IT occur?
Microsoft estimates that 60% of cloud-based applications in large enterprises are unknown to IT and that the number is probably growing. There are three probable reasons for the prevalence of any form of shadow IT:
- IT out of touch or overwhelmed. Shadow IT is often a symptom of an IT department that is either out of touch with the business needs or too overburdened to address them. Rapid growth can often be an underlying factor.
- Users’ expectations have changed. If users happen to find an app that helps them do their job faster and more easily than the sanctioned product, they’ll use it.
- IT’s reputation. In many organizations, internal IT departments have a reputation as the “Department of No”. If IT greets every request with a negative response, people will stop asking. They’ll figure it will be easier to ask forgiveness.
Benefits and drawbacks of shadow IT
Four key challenges
Shadow IT introduces challenges in four key areas: security, compliance, cost, and interoperability.
- Security. Shadow IT activities may inadvertently introduce security risks. Shadow IT applications may contain malware or vulnerabilities that hackers can exploit. Unmanaged devices and software may not be patched in a timely manner or might be configured improperly. Sensitive data may not be backed up or stored securely. And uncontrolled access to confidential information is likely.
- Compliance. Auditors, especially in regulated industries, are apt to be extremely displeased to find unauthorized products in use. For many organizations, hefty fines can result from a lack of proper controls on data.
- Cost. Using unsanctioned products to perform tasks that an organization already has solutions for means that the organization is effectively paying twice to do the same job. Even free apps can be costly if they cause data loss or a security incident.
- Interoperability. When different departments use different programs, extra steps will probably be needed to convert the data into a common format. Worse, when the data resides in different cloud services, providers may assess extra fees for file sharing.
Two key upsides
However, despite the doom and gloom, it’s not all bad. The key, some experts argue, is to learn how to effectively embrace shadow IT.
A report from Gartner suggests that companies should leverage employee-led IT initiatives as an essential part of their IT strategies. Furthermore, data security firm Entrust has published a guide on the upside of shadow IT. There are two key benefits of shadow IT:
Shadow IT shows you what users really want. When a line of business employs shadow IT, it reflects an understanding of that unit’s needs that IT can learn from.
Shadow IT is collective problem-solving in action. Not only does Shadow IT allow users to signal exactly what it is they want, but it is also a means for them to contribute to the solution. Many IT programs began in the shadows and were later formally adopted.
Best practices for managing and reducing shadow IT
Getting a handle on the extent of the situation
Dealing with shadow IT activities can be challenging. However, getting a handle on the extent of your situation is the first step to manage shadow IT effectively.
Technology solutions exist. A cloud access security broker offers visibility into cloud apps and services used in the organization. Some will assess the apps for risk and generate analytics about their usage. BlueCat’s solution uses network data (DNS logs for the win) to uncover undocumented dependencies.
The analog way. Have persistent complaints about needed functionality suddenly silenced? Maybe the users found their own shadow IT solutions.
If they have a cordial relationship with someone in IT, this could be an opportunity to turn it into a sanctioned and effectively managed asset. But don’t wait for that. Build and leverage relationships beyond your department to learn about how your users lean on IT services (or don’t).
Streamline processes and become a business partner
Certainly, it’s always difficult to balance what users want (basically everything, and they want it now) with what’s possible and affordable. And, most importantly, with what is secure and compliant. But it can be done.
Proactively streamline IT processes. Whether it is deciding to sanction a product or provisioning an IP block, IT processes can be slow and cumbersome. Some are undeniably necessary; others are unnecessarily inefficient. However, if users see IT speeding up, they may be less likely to rampage ahead on their own.
Become a business partner. Users may not be aware that there is an approved solution to their problem. Become a trusted advisor to the business. Further, invest time in educating users about the options so they don’t default to thinking the answer isn’t available through IT.
When IT acts as a business partner, it can be more in tune with its users’ needs. That, in turn, can reduce the prevalence of dangerous shadow IT practices.
For more discourse on shadow IT, give this podcast episode about the right way to roll out new technology a listen.




