Four major DNS attack types and how to mitigate them
In a DNS attack, DNS is compromised or used as a vector. Learn about the different attack types and how to prevent, detect, and mitigate them with BlueCat.

Do you know what a DNS attack is and is your network fortified against it?
DNS was built first and foremost to correctly and efficiently respond to queries, not question their intent. As a result, DNS has real vulnerabilities and potential as a vector for cyberattacks.
A Domain Name System (DNS) attack is one in which a bad actor either tries to compromise a network’s DNS or takes advantage of its inherent attributes to conduct a broader attack. A well-orchestrated DNS attack can bring an organization to its knees.
This post will delve into the four major types of DNS attacks. Next, it will discuss basic steps you can take to prevent DNS attacks. And finally, it will briefly explore how BlueCat can help.
Major DNS attack types
A DNS attack targets the DNS infrastructure. Attacks can be tailored to either recursive or authoritative servers. There are four main types of attacks that use DNS.
DoS, DDoS, and DNS amplification attacks
Denial-of-service (DoS) attacks and distributed denial-of-service (DDoS) attacks are two forms of the same thing. They’re what most people think of when they think of a DNS attack. In both cases, attackers flood internet servers with so many requests that they simply can’t answer them all, and the system crashes as a result.
DoS attacks
A simple DoS attack uses one computer and one internet connection to flood a remote server. They aren’t terribly effective at overwhelming today’s high-capacity systems.
DDoS attacks
In a DDoS attack, multiple computers and internet connections target a site.
Often, DDoS attacks add compromised computers to a botnet that runs malicious queries in the background. Attackers can harness the power of devices from around the world to query the target network all at once.
There are also three sub-types of DDoS attacks:
- Protocol attacks: This attack cripples actual server resources or other network equipment like firewalls and load balancers.
- Application layer attacks: To crash the web server, the attacker sends requests that seem harmless but actually exploit the target’s vulnerabilities.
- Flood attacks: Floods aim to make a server unavailable to real traffic by ‘flooding’ the targeted server’s resources.
Indeed, DDoS attacks often target specific layers of the OSI model. The model divides communication across computer networks into seven abstract layers that each perform a distinct function in network communication.
In February 2020, Amazon’s AWS Shield service thwarted the largest DDoS attack ever (2.3 Tbps), which was carried out using hijacked Connection-less Lightweight Directory Access Protocol web servers.

DNS amplification attacks
Furthermore, a DNS amplification attack is a type of DDoS attack in which attackers use publicly accessible open DNS servers to flood a target with DNS response traffic. An attacker sends a DNS lookup request to an open DNS server with the source address spoofed to be the target’s address. When the DNS server sends the DNS record response, it is sent to the target instead.
Here’s a quick video of BlueCat’s Chief Strategy Officer Andrew Wertkin describing how DDoS attacks turn your network into a weapon:
DNS hijacking
There are three types of DNS hijacking:
- Attackers can compromise a domain registrar account and modify your DNS nameserver to one that they control (see illustration).
- Bad actors can change the A record for your domain’s IP address to point to their address instead.
- Attackers can compromise an organization’s router and change the DNS server that automatically gets pushed down to each device when users sign on to your network.
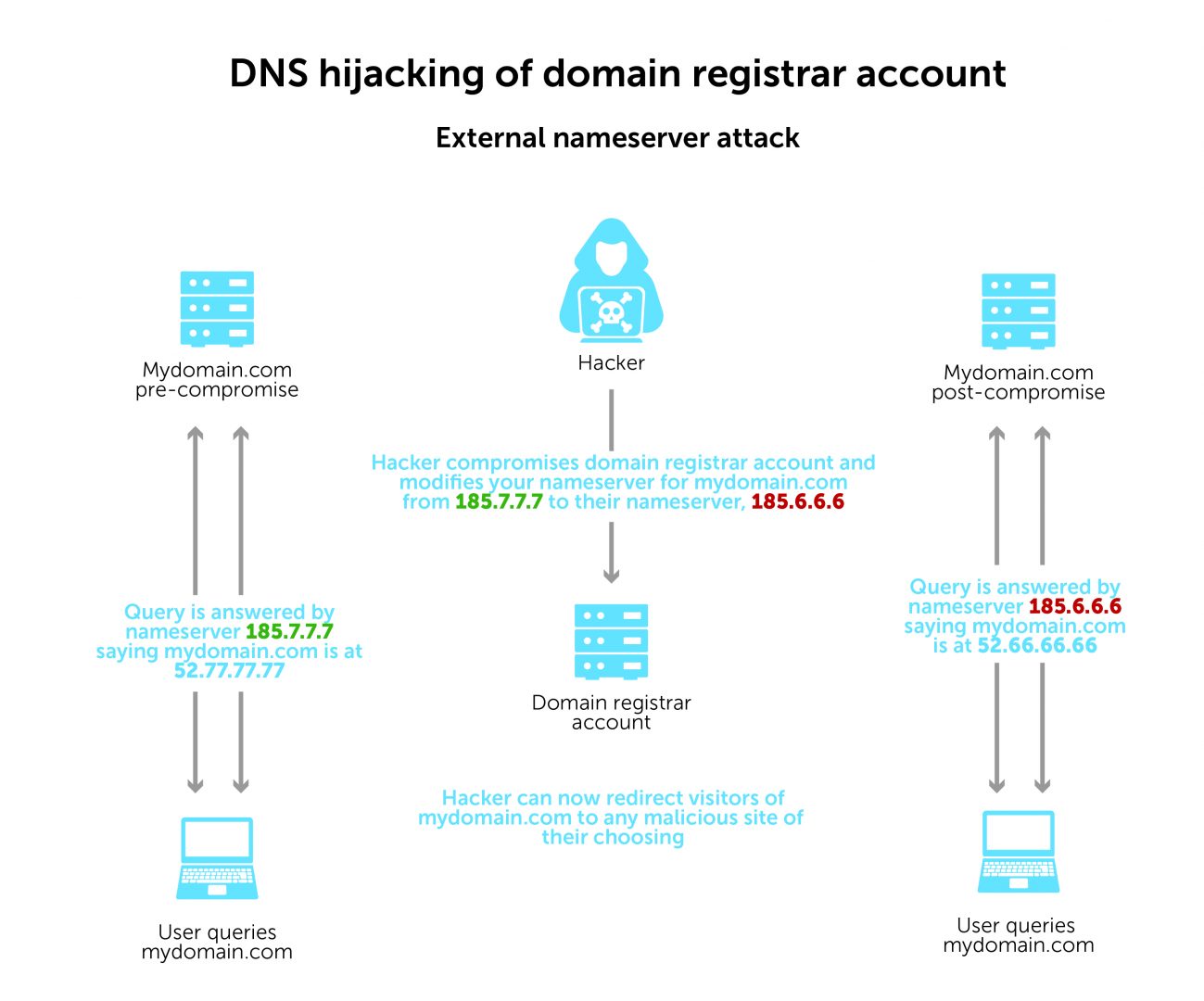
In 2019, security experts discovered Sea Turtle, a state-sponsored DNS hijacking campaign that manipulated and falsified DNS records of at least 40 organizations in 13 countries.
DNS tunneling
DNS tunneling transmits information through the DNS protocol that usually resolves network addresses.
Normal DNS requests only contain the information necessary to communicate between a client and a server. DNS tunneling inserts an additional string of data into that pathway. It establishes a form of communication that bypasses most filters, firewalls, and packet capture software.
That makes it especially hard to detect and to trace its origin.
DNS tunneling can establish command and control. Or, it can exfiltrate data. Information is often broken up into smaller pieces, moved throughout DNS, and reassembled on the other end.
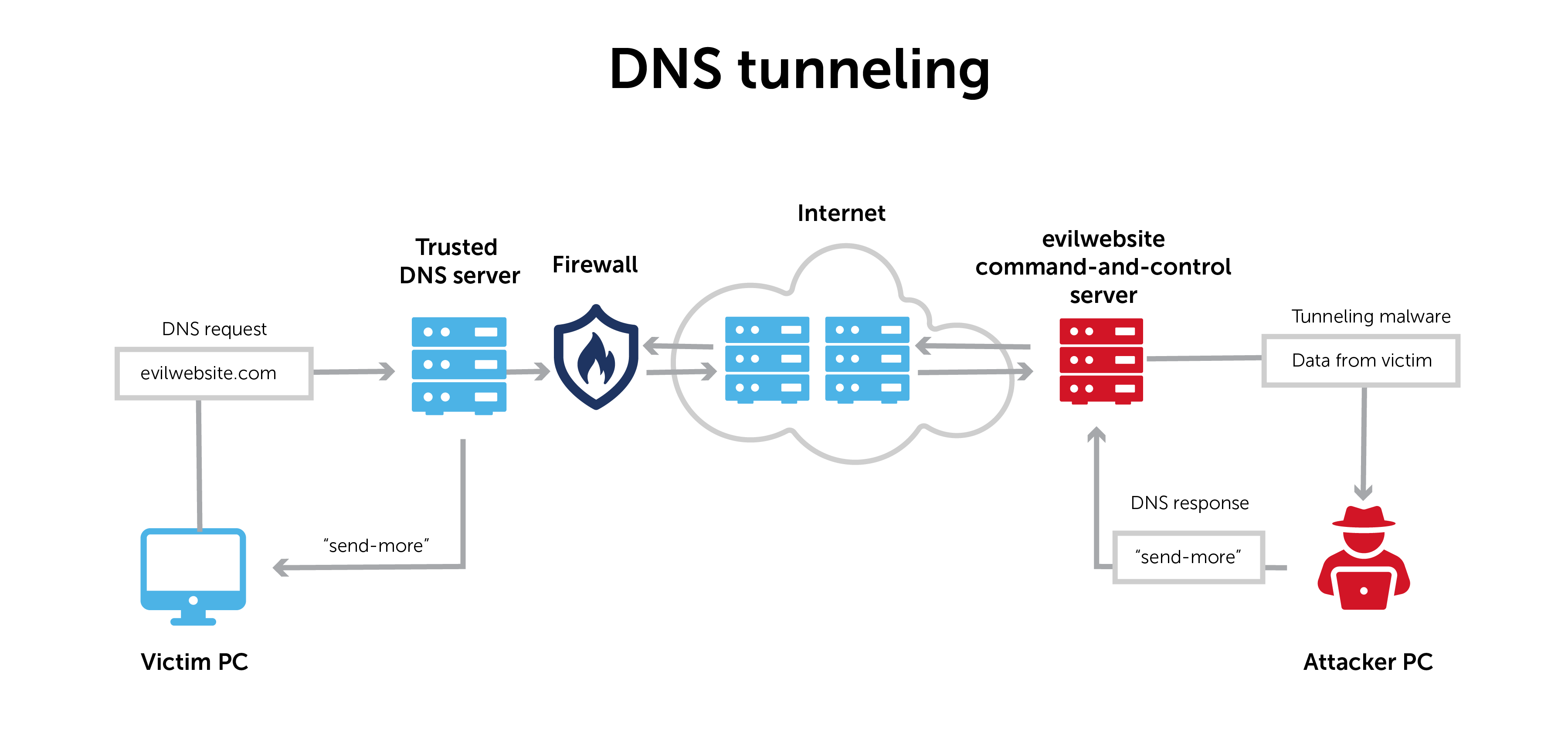
Since 2016, the Iran-linked group OilRig has used DNS tunneling to communicate between infected hosts and command-and-control servers.
DNS poisoning and cache poisoning
DNS poisoning (also known as DNS spoofing) and its cousin, DNS cache poisoning, use security gaps in the DNS protocol to redirect internet traffic to malicious websites. These are sometimes called man-in-the-middle attacks.
When your browser goes out to the internet, it starts by asking a local DNS server to find the IP address for a website name. The local DNS server will ask the root servers that own that domain, and then ask that domain’s authoritative name server for the address.
DNS poisoning happens when a malicious actor intervenes in that process and supplies the wrong answer. Once it has tricked the browser into thinking that it received the right answer to its query, the malicious actor can divert traffic to whatever fake website it wants.
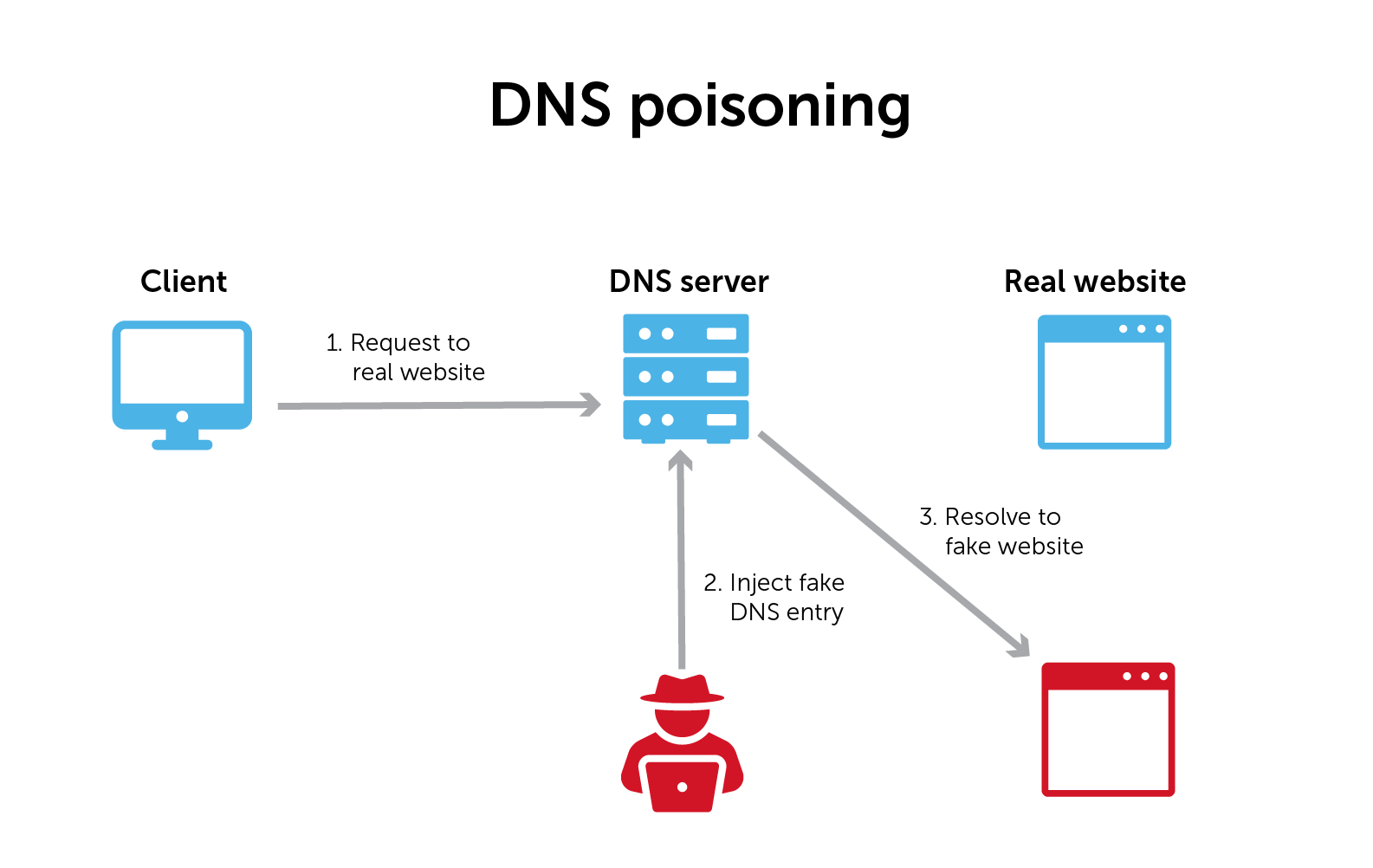
In DNS cache poisoning, once a malicious actor intercepts and ‘answers’ a DNS query, the DNS resolver stores that answer in a cache for future use. (Most DNS resolvers are caching resolvers.) In this case, it makes the attack worse by continuing to supply that wrong answer.
How long those DNS entries remain in your cache depends on the time to live (TTL). This is a DNS server setting that tells the cache how long to store DNS records before refreshing the search for a legitimate server.
In November 2020, researchers uncovered a new way to carry out cache poisoning, called SAD DNS (short for Side-channel AttackeD DNS). The method allows an attacker to use a side channel to inject a malicious DNS record into a DNS cache.
How to prevent, detect, and mitigate a DNS attack
While DNS has historically been seen as a naive pawn, it can also be a proactive part of a good defense-in-depth strategy. Along with notable U.S. government agencies like the NSA, Gartner recently recognized DNS security as crucial for improving the overall defense of your network.
The concept of protective DNS now exists to describe DNS as critical to protecting against network threats. However, for some number of years already, many vendors (like BlueCat) have been helping organizations secure their networks by leveraging DNS security.
Here are some basic protective steps:
- Know your entire DNS architecture. For starters, securing a network requires awareness of your enterprise’s entire DNS estate. Often, network teams lack complete visibility thanks to a mess of DNS silos, orphaned zones, or shadow IT.
- Log and monitor DNS queries and response data. Logging and monitoring outbound and inbound queries is the first step to detecting anomalies. Furthermore, your response data provides contextual information that allows for a more thorough forensic analysis.
- Harden your recursive DNS servers. Protect recursive servers from unwanted access and tampering through DNSSEC, access controls, and other architecture enhancements.
- Tighten admin access to your DNS. Enable multi-factor authentication on your domain registrar account and use a registrar lock service to request your permission before changing DNS records.
Ward off a DNS attack with BlueCat
The best way to prevent DNS attacks is to deploy a centralized, automated, and secure DDI platform. This allows administrators get a complete picture of the DNS activity on their network whether it’s a large enterprise or mid-market.
Important features include:
- Comprehensive DNS logging: BlueCat logs both DNS queries and responses, providing a complete overview of DNS activity on your network
- Integration with SIEM tools: DNS logs can be sent to network Security Information and Event Management (SIEM) tools or Splunk, enabling the setting of alerts for anomalies
- Policy-based rules creation: Utilizes both query and response data to allow admins to create precise policy-based rules such as monitoring or blocking domains with bad reputations.
- Threat intelligence integration: Integrate security intelligence from BlueCat’s threat feed to block the latest threats
Learn more about how BlueCat’s network security features can transform your DNS from an attack vector to a line of defense.





