Our analysis: Gartner’s DNS security best practices
BlueCat has long known what Gartner now says: Your network needs DNS security. Learn how DNS data logs, threat feeds, and setting policies can help.

Earlier this summer, Gartner recognized DNS security as crucial for improving the overall defense of your network.
They made four recommendations in their quick-answer report:
- Know what security capabilities your existing DNS solution or service provider offers.
- If you don’t have a DNS solution or service provider that provides security capabilities, look into getting one.
- Collect and analyze your DNS logs for threat detection and remediation using your security information and event management (SIEM) or similar tool.
- Implement threat prevention and block lists and monitor DNS traffic for anomalies.
BlueCat agrees. In fact, we’ve been saying for years most of what’s in Gartner’s report. Now, you don’t just have to take our word for it—you can take Gartner’s, too.
This post will first explore the value of integrating DNS security into your protection plan. Then, it will provide deeper analysis of some of Gartner’s specific recommendations. Furthermore, it will highlight ways that BlueCat can help you bring some of these DNS security best practices to fruition.
Integrating DNS security into your protection plan
The nature of the Domain Name System (DNS) protocol presents opportunities for enhancing network security. Gartner’s report states—and BlueCat has certainly observed this as well—that too few organizations take full advantage. You should know exactly what your DNS solution or service provider can and can’t do for you.
Because of the intrinsic nature of the function that Domain Name System (DNS) performs, it presents security and risk management leaders with opportunities to anticipate, prevent, detect and respond to prevailing threats, regardless of where the user, device or workload is located. — Gartner’s Quick Answer: How Can Organizations Use DNS to Improve Their Security Posture?
The report notes that it’s important to remember these things about DNS:
- DNS infrastructure is not widely recognized for its network security use cases.
- DNS is very commonly used by attackers in a multitude of ways.
- Few organizations have realized the security enhancements available to them by simply storing, monitoring, and analyzing DNS log data for threat detection, investigation, and remediation.
Historically, DNS has been foremost thought of as something that needs to be protected. It’s far less commonly seen as a line of defense in a protection plan. In fact, earlier this year, two major U.S. security agencies released guidance pointing to protective DNS as a defense strategy.
DNS should be proactively used to protect your network against threats. Otherwise, enterprises leave themselves open to unnecessary risk. Worse still, they’re underutilizing a technology they’ve had all along.
Most cybercriminals use DNS
Furthermore, while attackers can use different methods to compromise a network, the common thread is often DNS. While DNS can bolster your security posture, don’t ignore the prospect of DNS as a threat vector. When someone controls your DNS, they can redirect users anywhere or commit data exfiltration.
Specific types of attacks include DNS tunneling, DNS poisoning (also known as DNS spoofing), and DNS cache poisoning. There’s also DNS hijacking and distributed denial of service, or DDoS, attacks.
Consider your DoH and DoT strategies
Importantly, the report notes that it’s crucial for you to have some control over DNS resolution for your users. Solely relying on what an ISP returns is rarely going to provide added security. The current norm of working from home and co-working spaces only exacerbates this.
In order to capitalize on the security capabilities of DNS, you need to be able to manage your own DNS and control DNS resolution—that is, ideally you need to ‘own your resolver.’ — Gartner’s Quick Answer: How Can Organizations Use DNS to Improve Their Security Posture?
For example, DNS over HTTPS (DoH) is often the default for browsers. Not all operating systems across an organization’s endpoints support DoH configuration for private DNS. This means that the browser will use predetermined DNS service providers and bypass network-level DNS.
As a result, many organizations are blocking DoH, forcing browsers to use their DNS resolvers. If enterprises can’t block public DoH, they lose visibility. This limits their ability to pigeonhole malware domains, resolve internal domains, or detect phishing or data exfiltration.
Furthermore, some organizations using external DNS resolvers utilize their provider’s DNS over TLS (DoT) to encrypt their DNS traffic. DoT can apply to internal DNS servers as well.
DNS security best practice: Create DNS allow and deny lists
Gartner’s report correctly asserts that allow and deny lists are both highly popular and crucial to effective cybersecurity. It notes that we exist in an era where hundreds of millions of new malware strains crop up each year.
Much of that malware is dependent on network connectivity to keep spreading and for command-and-control. The latter allows bad actors to communicate with the malware and tell it exactly what it’s supposed to do.
And what does network connectivity require? DNS.
Furthermore, malware often relies on multiple domain resolution to evade detection and takedowns. As a result, it’s rare to find malware that uses a direct IP address connection that bypasses DNS controls. A domain generation algorithm is a common malware technique. It generates seemingly random new domain names and IP addresses for command-and-control servers.
Enterprises can use DNS to prevent threats with DNS filtering. They can allow only a predetermined list of domains to resolve. Or block certain malicious domains from resolving.
BlueCat has long known the value of policy-based rules for DNS. Consider this simple example. If a point-of-sale device is pinging Google at 2 a.m., context-based policy should flag that. It’s a purpose-built device that shouldn’t need to look up Google, and it’s outside of business hours.
Consequently, with BlueCat DNS Edge, you can set policy-based rules to block, allow, or manually watch certain domains. This screenshot illustrates how BlueCat’s policy-based rules block DNS queries from known DGA malware:
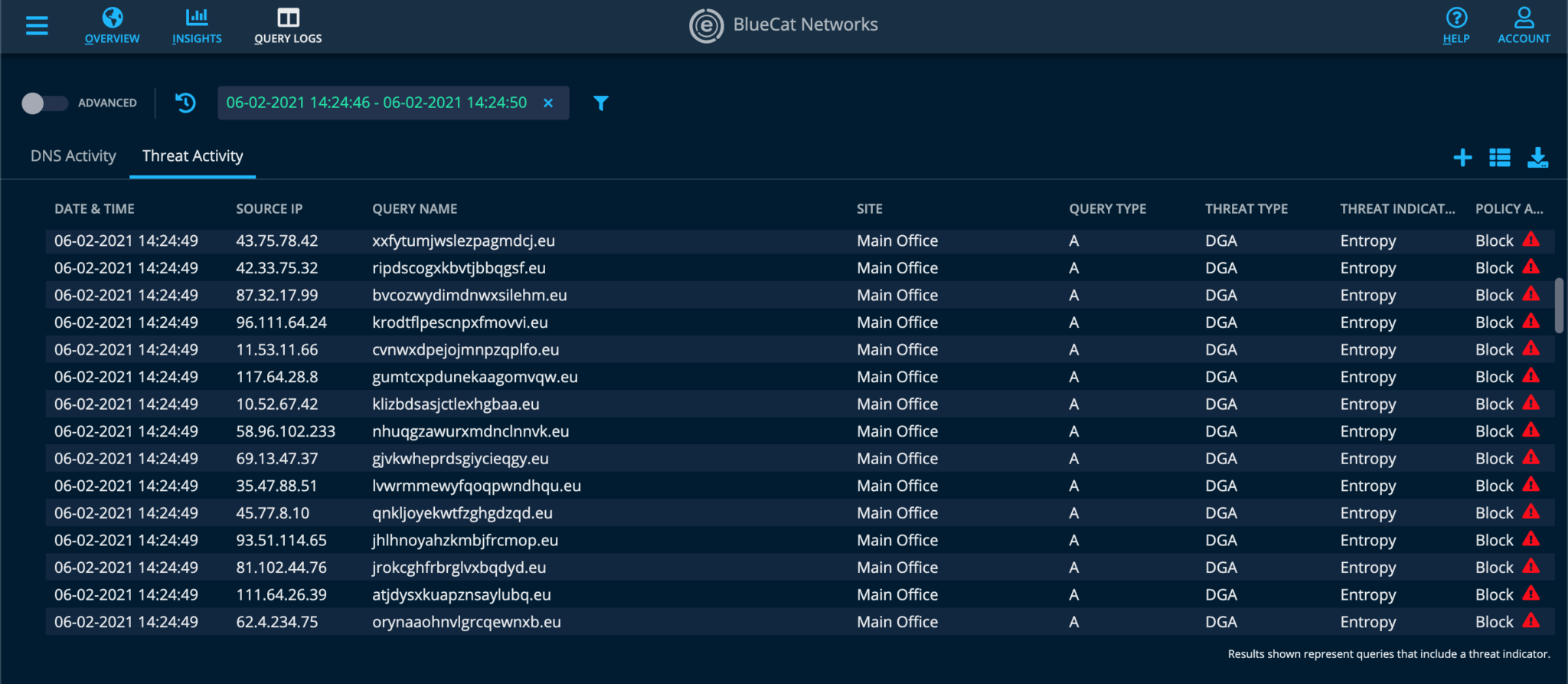
DNS security best practice: Integrate threat intelligence
Gartner’s report notes that many enterprises use machine-readable threat intelligence to aid with threat prevention, detection, and remediation.
Threat intelligence can come from many sources. These can include Information Sharing and Analysis Centers or reports from DNS solution vendors. Common sources are also commercial providers that make enterprise firewalls or intrusion prevention and detection products.
Threat intelligence can be used to generate curated domain lists in your SIEM tool. This can help your security team to spot activity on those domains. Intelligence providers can monitor for registration of potential phishing domains or other new domains that are likely to be malicious.
BlueCat knows the value of integrating threat intelligence with DNS. What you don’t know can hurt you.
With Edge, you can seamlessly integrate security intelligence from BlueCat’s own blocklists. By subscribing to our continuously updated security feed, you can spot and block threats. BlueCat’s Threat Protection is integrated with insights from CrowdStrike’s elite team of threat analysts and researchers.
Furthermore, you can ensure your data correlates with other security data and analysis. You can integrate it with your choice of popular security technologies and SIEMs, Cisco Umbrella, or Splunk. As a result, you can shorten the time it takes to identify and respond to threats.
DNS security best practice: Use your DNS data
BlueCat has long advocated that your DNS data is a goldmine of information. Gartner’s report agrees.
Analyzing your DNS logs can help inform you about what’s happening on your network. You can discern who’s there, what they are trying to access, and aberrations in normal activity patterns.
But admins can do more than simply see query logs—they can gauge query intent. With complete information about every query on the network, administrators can root out malicious patterns of behavior or identify infected devices.
However, it’s not just DNS queries that can provide insight. For example, suppose a hacker infiltrates your network and redirects everybody who goes to bluecatnetworks.com to their phishing site. If you’re only logging users’ queries, everything would appear to be perfectly fine. There would be no way to identify that the answer is pointing users to a malicious site.
Only the response packets and contextual information show us what’s actually going on. Hence, DNS response data allows for a more thorough forensic analysis.
With BlueCat’s platform, both DNS queries and responses are logged together. As a result, you get a complete picture of the DNS activity on your network. Using both query and response data, admins can then create policy-based rules that are more informed and precise. Furthermore, BlueCat Edge attaches policy alerts to your logged query data.
Here’s a quick demo of how Edge gives you forensic insight:
Ready to learn more? Explore the role of DNS in cyberattacks and how your overlooked DNS data can unlock more robust detection and response with our eBook, Exposing the Enemy Within. Or, watch a webinar exploring the recent SUNBURST/Solorigate malware attack, a prime case study. Learn how that attack exploited DNS and how BlueCat Edge could have helped detect DNS query manipulation and flagged the threat sooner.





