Pulling Data via SNMP, SSH or API – PAN Firewall Best Practices
If you’re want to integrate Palo Alto firewalls as part of some automated system – scripts, central NOC, SDN. What protocol is best? SNMP, SSH, API? Read…
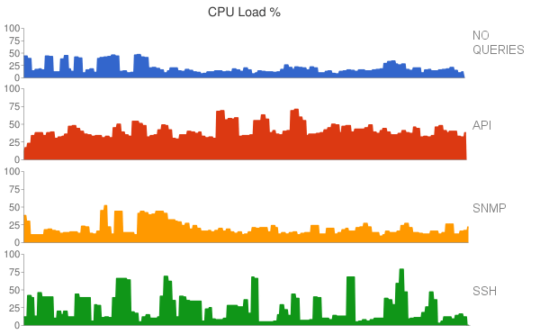
When querying a firewall, what’s the best protocol to use? SNMP, SSH or API?
If you are looking to integrate Palo Alto firewalls as part of some automated system – scripts, central NOC, software-defined-whatever, etc. – you’d want to hear what we have to share. You should also read this post if you like learning about interesting technical aspects of the products you use.
As you may know, we have started supporting Palo Alto Networks (PANW) firewalls in our product late last year. We are currently developing new support and are working with large and small organizations throughout the globe. One interesting thing we’ve noticed that’s worth sharing is that PANW’s customers are very open to embracing new technologies. That is great for us 🙂