APIs and data: The way to your IT organization’s heart
Show your security and network teams some love with DNS data to spot threats before they cause damage and BlueCat’s API to automate DNS services.

February 14 is upon us, and we all know what that means. It’s that time of the year when you show the people you care about just how much they mean to you. Some people give chocolates, others give flowers. Others will take their nearest and dearest out for a fancy meal. But your organization’s network and security teams might have some other gifts on their mind.
If you’re not sure what to get them to show your appreciation, we’ve put together a couple of gift ideas that are sure to make both your network and security teams happy.
The gift of data
When tasked with hunting cyber threats and getting one step ahead of malicious adversaries, data is your best friend. Data will tell you everything about everything; however, combing through mountains of data looking for those hints and patterns can prove to be cumbersome and extremely time-consuming, at times with little to show for it. After all, how do you know what to collect? How do you decide what you should store and what you should prioritize? How do you even know what you’re after? Simply put, you don’t know what you don’t know.
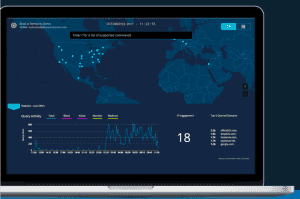
Subsequently, not all data is created equal. So don’t settle for just any type of data. Go with the gold standard: DNS data.
DNS data is full of possibilities. For one, it gives you the insights you need to spot threats before the damage is done, and allows you to make educated decisions to set policies. That’s where the value within the data reveals itself. DNS data also gives you more control and a more secure network without the steep costs associated with other types of data storage like full packet capture.
With DNS data, it’s possible to correlate an IP address to a destination, which can ultimately be the starting point for what is happening across an entire network. From this, tactics can be used to analyze the data and draw meaningful conclusions. That said, however, more data is not necessarily better. What security teams need is data that is valuable; they need data that lets them glean meaningful, actionable insights.
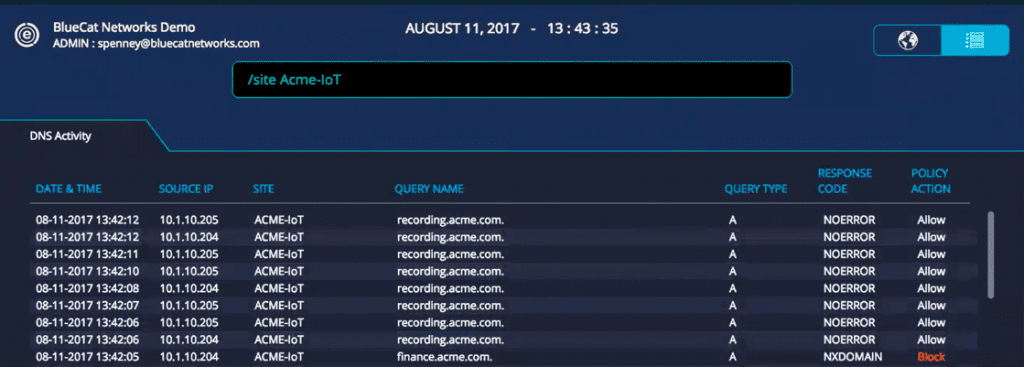
The way to a network team’s heart is through an API
Not sure what to give your network team? Give them the gift of time, and let them automate key IT services with a robust API. As we learned in our recent New York user group, automation is one of the most common and most important corporate mandates. BlueCat’s API provides access to DNS services to help automate key IT initiatives – and that keeps both network teams and the C-suite happy. IT organizations are constantly looking for ways to automate processes to not only deliver services faster but to enable new solutions that solve complex business problems.
To make all this happen, DNS has to work in orchestration with these workflows to ensure things like network availability, change control, and compliance. For example, our API can automate workflows to facilitate IP provisioning when onboarding a new client, particularly IoT devices like security cameras, servers, and more.
BlueCat’s API ultimately allows you to control how your enterprise deploys and consumes services, and helps you get the most out of DNS and DHCP services.




