Gain More Insight with Indeni’s Network Security Automation – Rule Category
Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
In this blog, we’ll do a deep dive into Rule Category. Although the use of Rule Category is somewhat limited today, we’ve planned to expand its use to help you get more insight into your environment.
Why use Rule Category?
Rule Category helps you quickly process information about potential problems in your network. Today you use Labels to organize your devices, so you can view information about a group of devices and perform operations on the group with ease. Similarly, you can use Rule Category to organize your alerts, so you can quickly identify the type of problems you may be experiencing.
Unlike SNMP-based monitoring tools that’s main focus is device health, we cover many more use cases including High Availability readiness, external services monitoring, security risks identification and ongoing maintenance, just to name a few. We humans tend to take in large amounts of data, before we simplify and structure it. That is how we make sense of what is going on. Categorizing the alerts is a useful tool to help you navigate to the problem faster and more effectively.
Rule Category Types
We cover a diverse set of use cases, reflected by Rule Category. They are:
#1 Health Checks
Continuously assess device health and proactively identify issues before they become bigger problems.
#2 High Availability
Detect configuration mismatches among the active, passive and backup devices. Ensure High Availability best practices are followed. For example, we ensure redundant links are used for heartbeats between the active and passive devices.
#3 External Services (new)
Security devices rely on many critical services, such as DNS, NTP, LDAP, management servers, external rating services, whitelists/blacklists, threat intelligence feeds, etc. These rules ensure your devices can reach these services and successfully retrieve the information.
#4 Best Practices
Ensure vendor and industry best practices are adhered to. The rules in this category cover a lot of areas to produce good outcomes. For example, Palo Alto Networks Best Practices Assessments, SecureXL best practice configuration, etc.
#5 Organization Standards
Ensure organizations ‘gold standard configuration’ is followed. The rules in this category require you to provide the configuration that needs to be in compliance.
#6 Ongoing Maintenance
Detect expiration dates and provide advance notifications if expiration dates or usage limits are approaching. This includes licenses, SSL certificates, hardware and software end of support.
#7 Security Risks
Check for insecure protocols, strong passwords, timeout values not too high, restricted access to firewalls, failed logins, etc.
#8 CVEs (new)
This is a new category created for common vulnerabilities and exposures.
Plans for Rule Category
Today, you use Rule Category as a filter on the Issues and Knowledge Explorer pages to refine the list of alerts you want to investigate. In future releases, we are planning to leverage Rule Category in dashboards, reports and configurations.
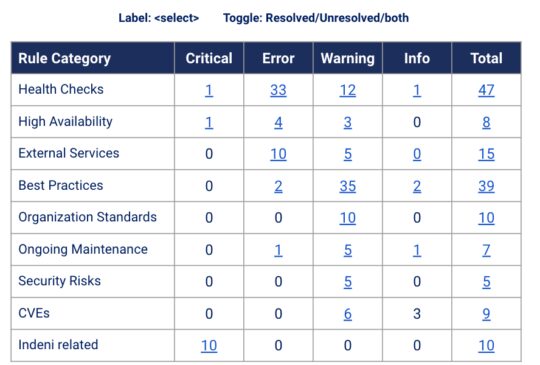
Dashboard – Issues At-A-Glance

This new widget will provide you a high level overview of the type of problems. You can set filters to refine the list to a group of devices. You can use the toggle to select unresolved issues, resolved issues, or both. You can click on a cell to drill down further to the actual issues. For example, clicking 35 on the Best Practices row under the Warning column will take you to the issues page showing the 35 warnings pertaining to Best Practices.
We are also planning to include this table in the device page view so you can perform a similar analysis at a per device level.
Reports
We are planning to provide templates for every Rule Category. These templates are intended to simplify reports creation. For example, you can easily create a security report from the security risk template in preparation for audits. If you have an initiative to harness site reliability, you may want to leverage the best practices report to ensure a device is operating in its optimal way.
We are also planning to provide a CVE report. We recommend that you run the CVE report after every upgrade to determine if any of your devices are exposed to vulnerabilities.
Configurations
What if we allow users to subscribe to alerts of a particular category? Your operations team may not be interested in alerts related to Best Practices. They are useful to engineers. Your auditors may only be interested in security related alerts and CVEs. Providing an ability to subscribe to a category of alerts will enable other personas to receive useful information about your environment.
Summary – call to action
Rule Category is a new tool you can use to gain insights of your environment. We would love to hear from you if you have any ideas about new usage of Rule Category. For example, do you think you would want to create your own Rule Category? Are there any other categories you would like to see? Please send your thoughts to [email protected].




