Infrastructure Automation with Indeni 7.6
Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
Check Point Device Hardening
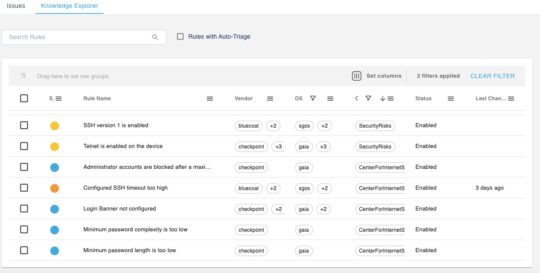
Device hardening is a necessary step to ensure your security devices do not have any potential loopholes which can be exploited by hackers. In 7.6.1, we added new Auto-Detect Elements (ADE) to harden Check Point firewalls. These checks apply to Check Point GAiA devices as well as Maestro devices.
- Check for Strong passwords
- Ensure minimum password length is set to a user defined length.
- Ensure the password contains a combination of uppercase and lowercase letters, numbers and special characters.
- Ensure password complexity is set to 3.
- Close inactive SSH sessions automatically. Ensure a timeout for automatic disconnection for inactive sessions is set. The wait time is >0 and <10 minutes by default. The timeout value is user configurable.
- Ensure “Login Banner” is set to prohibit unauthorized access.
- Ensure remote management is using SSH v2 and not SSH v1.
- Ensure that the local admin user accounts will not be blocked by checking that the CLI accounts are not being blocked under any circumstances.
SecureXL Disabled Enhancements
Prior to 7.6, Indeni only collected the global status of SecureXL and alerted based on enable/disable status. In 7.6, Indeni will alert if SecureXL is disabled by the firewall as a result of certain conditions.
Three new ADE’s were added to collect the state of the three SecureXL templates used to accelerate the connections: Accept, Drop and NAT. Indeni will alert if any one of these templates is disabled.
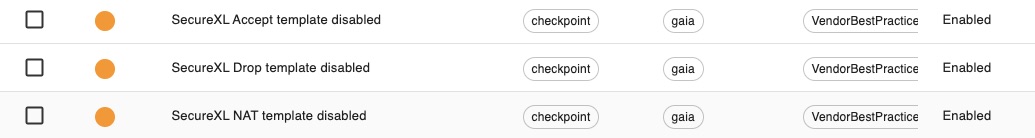
These templates are available in version R80.10 later. The new rules are only applicable to Check Point GAiA devices.
Other New Auto-Detect Elements
- Check Point Light Out Management (LOM)
- New ADE to collect the TLS version, IP address and Firmware information. Indeni will alert if the LOM interface was configured with default values.
- Extended the support of the “configuration mismatch” rule to Palo Alto Networks devices.
Next Steps
To see a complete list of features and bug fixes, refer to the release notes page on our website. You can download the latest list of Auto-Detect Elements for Maestro here. As always, if you have questions or comments, we’re here to help.




