Introducing Security Insights for smarter network security without complexity
For LiveNX and LiveWire, get faster, cost-efficient threat detection and forensics without added complexity.

Key takeaway:
Security Insights is a cost-efficient alternative to traditional Network Security Detection (NDR) by analyzing flow and packet telemetry directly at the network edge. This edge-first approach enables faster detection, stronger forensics, and shared NetOps and SecOps visibility—helping teams respond to threats quickly without adding complexity or infrastructure.
Harnessing network telemetry at the edge for faster, cost-efficient detection
Organizations face an increasingly hostile threat landscape as attackers exploit the gaps created by siloed tools and teams. Modern adversaries don’t confine themselves to one domain. Instead, they move laterally across endpoints, servers, networks, cloud environments, and data centers. But most enterprises still operate with fragmented visibility: The network team sees one slice, the security team another, and blind spots remain. These blind spots are exactly where attackers thrive.
To compensate for this fragmented visibility, Security Operations Centers (SOCs) have standardized on Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) as their systems of record. At the same time, many organizations have added standalone NDR tools that ingest massive volumes of packet data into centralized cloud platforms for analysis. In practice, this approach is increasingly viewed as data-transfer intensive, expensive, and slow. For industries with strict cost, performance, and compliance requirements—such as finance, healthcare, and government—this model simply doesn’t scale.
Yet abandoning packet and flow data isn’t the answer. These signals remain among the richest and most trustworthy sources of security insight. Too often, however, organizations confine them to basic performance monitoring, leaving their forensic and detection value largely untapped. The opportunity lies in analyzing packet and flow telemetry directly at the network edge—where the data is generated. This closes visibility gaps, accelerates detection, and avoids the overhead of traditional, centralized NDR architectures.
The result is a shift in how network observability supports security. Organizations that modernize their approach can improve resiliency, strengthen security outcomes, and enable faster, more cost-efficient threat detection—without adding complexity or infrastructure burden.
Security Insights—a modern, reimagined approach to network threats
Security Insights reimagines how enterprises detect, investigate, and respond to network-borne threats. Instead of introducing yet another complex, data-heavy security stack, it leverages the telemetry and packet data you already own, through LiveNX for flow visibility and LiveWire for deep forensic analysis.
The solution surfaces threats, anomalies, and policy violations directly within the LiveNX Security Insights Dashboard, giving both network and security teams a unified view of risk across hybrid and distributed environments. When deeper investigation is needed, LiveWire provides full packet-level visibility—reconstructing sessions, uncovering hidden behaviors, and validating Indicators of Compromise (IOCs) with forensic precision.
By analyzing flow and packet data at the edge of the network, Security Insights eliminates the need to backhaul massive data sets to the cloud or a centralized analysis platform. This edge-first approach delivers faster detection, lower costs, and stronger resilience. And it results in real-time anomaly detection, proactive threat hunting, and forensic-grade investigation within the trusted LiveNX and LiveWire environments.
What’s more, Security Insights also integrates seamlessly with existing Security Orchestration, Automation, and Response (SOAR) platforms, as well as SIEM and XDR platforms—making it simple to operationalize within current workflows. By leveraging infrastructure already in place, enterprises maximize ROI, streamline operations, and scale defense across distributed, hybrid, and regulated environments.
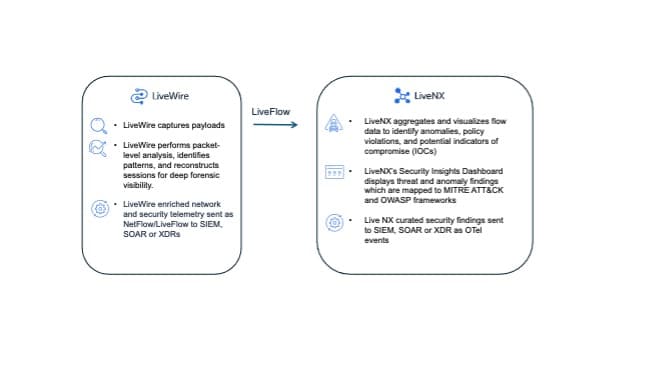
Security Insights bridges NetOps and SecOps
For years, network and security teams have worked mostly in parallel rather than in partnership—though that’s improving with each passing year. Each operates with its own tools, datasets, and objectives. Network teams are focused on uptime and performance, and security teams are dedicated to detection and defense. Yet, the reality is that threats don’t distinguish between operational domains. Attackers exploit the seams between these functions, moving through hybrid and multicloud environments faster than traditional processes can respond.
This disconnect leaves organizations with a critical visibility gap. Network teams see performance anomalies but often lack the context to understand their security implications. Meanwhile, security teams may spot suspicious behavior without knowing where it originated or how it’s moving across the infrastructure. Without a shared view, investigations stall, response times increase, and risk compounds.
Security Insights, however, bridges the gap, turning network data into a shared source of truth for both NetOps and SecOps. It empowers the network team to provide meaningful, real-time intelligence that complements security telemetry, enabling both groups to operate with the same visibility and context. Rather than layering yet another NDR platform or forcing teams into new workflows, Security Insights maximizes the value of tools they already trust—LiveNX for flow visualization and anomaly detection, and LiveWire for packet-level forensics.
With this integration, analysts gain a unified view of network behavior across LAN, WAN, SD-WAN, data center, and cloud environments. Flow telemetry and packet evidence are correlated automatically, providing an immediate connection between what’s happening at the transport layer and what’s being observed at the application or endpoint level. Teams can pivot seamlessly from a high-level detection in LiveNX to full packet inspection in LiveWire—reconstructing events, validating indicators of compromise (IOCs), and tracing lateral movement, all from a single interface.
This shared visibility transforms what were once isolated datasets into coordinated, actionable intelligence. The result is faster detection, stronger collaboration, and more confident decision-making across both disciplines. Network and security operations evolve from being reactive and working mostly separately into a unified, proactive defense unit—one that improves resiliency, reduces investigation time, and maximizes the return on existing technology investments.
When NetOps and SecOps share the same operational truth, every team gains the insight needed to move faster, respond smarter, and keep the business secure, without adding cost or complexity.
Top use cases for Security Insights
Security Insights enables organizations to see, understand, and act on network-borne threats faster than ever before. By unifying flow telemetry, packet analysis, and security findings in one environment, it provides a powerful foundation for detection, investigation, and prevention.
Here are the most common and high-impact ways enterprises use Security Insights today.
1. Real-time security findings
Modern attacks move at machine speed, so detection must too. Security Insights continuously monitors network behavior, automatically identifying suspicious activity, policy violations, and insecure protocol usage the moment they occur.
By leveraging flow telemetry from LiveNX and packet-level analysis from LiveWire, the platform correlates these findings across all environments, LAN, WAN, SD-WAN, data center, and cloud, giving teams complete visibility into where and how threats emerge.
Each detection is mapped to industry frameworks such as MITRE ATT&CK and Open Worldwide Application Security Project (OWASP), ensuring that findings are not just accurate, but actionable and aligned to known adversarial tactics and techniques. This mapping enables faster triage, standardized reporting, and more confident response workflows across both network and security operations.
Whether it’s identifying an unapproved application using encrypted channels or detecting an RDP brute-force attempt, Security Insights surfaces the context and impact immediately, empowering teams to respond in minutes instead of hours.
2. Forensic investigation
When incidents occur, speed and precision are everything. Security Insights combines flow analytics from LiveNX with LiveWire’s indexed packet capture to deliver full forensic visibility across the network. Analysts can reconstruct events in seconds, identify root causes, and validate IOCs with pinpoint accuracy.
Unlike traditional NDR systems that depend on costly cloud-based analysis, Security Insights performs this work locally, directly at the edge of the network. This edge-first architecture eliminates data movement delays and allows teams to replay historical network sessions instantly for post-incident review.
The forensic process is both intuitive and comprehensive. Analysts can pivot from a flow anomaly to the exact packet exchange that caused an incident, view payloads, confirm malicious behavior, and correlate that evidence to the affected systems or users. This level of visibility not only accelerates investigation but also strengthens audit readiness and compliance reporting.
In regulated sectors like finance, healthcare, and government, where audit trails and forensic records are non-negotiable, this capability ensures every decision is backed by verifiable data and a complete record of activity.
3. Proactive threat hunting
The most effective security programs don’t just wait for alerts, they actively seek out hidden risks. With Security Insights, analysts can perform proactive threat hunting across flow and packet data, uncovering subtle command-and-control traffic, policy bypass attempts, or abnormal behavioral patterns before they escalate.
By correlating insights from LiveNX’s flow telemetry and LiveWire’s packet-level intelligence, analysts can visualize suspicious behaviors at both the macro and micro level. They can drill down from high-level anomalies—such as repeated connections to unclassified domains or unusual encryption usage—into the full packet payloads to confirm or rule out malicious activity.
This continuous, iterative approach enables security teams to shift from reactive incident response to proactive defense. Over time, these hunts also feed back into operational improvements, refining detection rules, tuning policies, and closing visibility gaps.
For organizations striving to align with Zero Trust and Continuous Monitoring frameworks, Security Insights offers the telemetry and analytical depth needed to make proactive threat hunting a repeatable, scalable practice–and not a specialized art form.
The outcome: smarter security, shared insight
Together, these use cases highlight how Security Insights transforms existing infrastructure into an intelligent, integrated detection and response layer. It bridges the gap between performance monitoring and security operations, turning raw network data into a continuous source of truth for faster detection, deeper analysis, and stronger resilience without the overhead of traditional NDR solutions.
Why enterprises need Security Insights now
Attackers are moving faster, budgets are tighter, and security operations are consolidating around interoperable platforms like SIEM and XDR. The era of siloed, monolithic NDR tools is over.
Security Insights delivers a scalable, open, and cost-effective alternative, purpose-built for hybrid, distributed enterprises. It delivers high-fidelity visibility across every domain—LAN, WAN, SD-WAN, data center, and cloud, empowering teams to accelerate response, strengthen resilience, and reduce risk without rebuilding their stack.
As security operations converge, Security Insights stands out as the practical bridge between network observability and threat intelligence.
Security Insights enables:
- Faster detection and response: Move from hours to minutes with real-time, edge-based analytics.
- Reduced cost and time: Perform packet analysis locally with no time consuming and costly data backhaul to the cloud or centralized data center for analysis.
- Deeper forensics: Retain and analyze packet and flow data to meet compliance and investigation requirements.
- Unified visibility: Bridge network and security insights for faster decision-making.
- Seamless integration: Send data to Splunk, Cisco Secure Network Analytics, and other SIEM/SOAR/XDR platforms for correlation with endpoint logs, to set policies to block threats, and to quarantine offenders.
Security Insights transforms the network into a proactive defense layer. By leveraging the telemetry and packet data already in motion, it empowers teams to detect, investigate, and respond faster, without the cost and complexity of legacy tools.
In a world where attackers move in minutes and defenders often take days to respond, Security Insights delivers the visibility, intelligence, and agility that enterprises need to stay ahead.
Ready to experience the next level of security? Request a demo of Security Insights here.




