The iPhone X Face ID Hack and the Weapon of Curiosity
In the era of large-scale breaches and cybersecurity protocols, even on the most basic level, everything needs a password.

In the era of large-scale breaches and cybersecurity protocols, even on the most basic level, everything needs a password. Precious and private information must be guarded and protected. Whether you’re the owner of an iPhone or the CISO of a multinational corporation, you need to keep your data under wraps and out of the wrong hands.
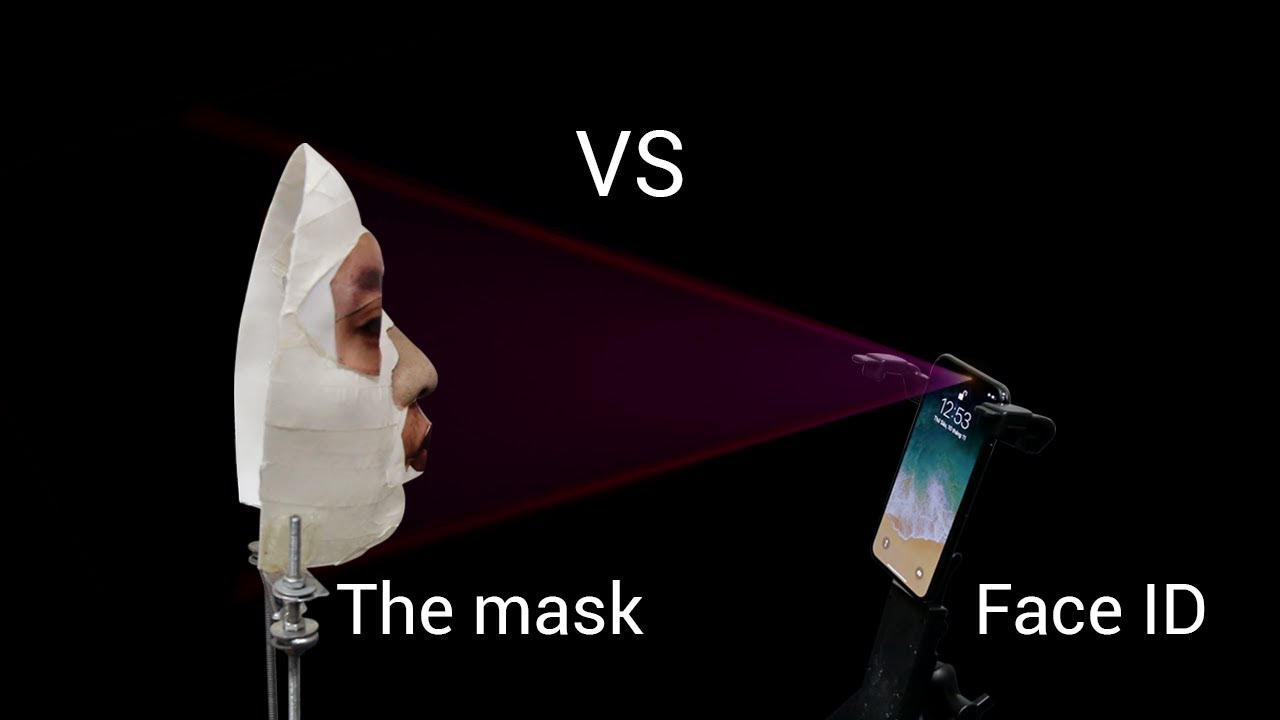
In recent weeks, it was reported that researchers from Vietnam-based information security firm Bkav found a way to hack the new iPhone X’s facial recognition feature, Face ID, with a makeshift mask composed of 3D printing and 2D images in just 5 days. Basically, the story goes something like this:
Apple: “There is only a one in a million chance that the wrong face could be used to unlock Face ID. This feature could not be fooled by masks.”
Bkav: “Challenge accepted.”
The first iPhone started out with a simple numeric passcode. They then introduced Touch ID, which was also eventually hacked, and was “no challenge at all.” With the arrival of the new iPhone X’s Face ID, it wouldn’t be long before bad-intentioned hackers or in this case curious-minded individuals figured out how to trick the new software. The higher we build our walls, the higher people will build their ladders.
However, Bkav did not try to override Face ID because they wanted to. They did it simply to see if they could. They did it for fun – not with malicious intent, but only to prove that Apple’s new software was not as secure as they touted it to be.
This then raises the question: Should we be focusing our efforts on creating unhackable security measures, or should we instead be focusing on how to best and more effectively nip these things in the bud? In our recent webinar with cybersecurity expert Dick Clarke, he mentions the importance of a breach plan and knowing exactly how to act in case of a breach. And as a former Homeland Security Advisor to 3 presidents, it’s safe to say he knows a thing or two about cybersecurity…
Clarke emphasizes the importance of creating proper cybersecurity protocol and being prepared. Clarke goes on to say that a penetration test is futile, as hackers have all the time in the world, and if there’s a will there’s a way. Because what you call unhackable, hackers call a challenge.
Again, the point is not how Bkav managed it; it’s that if people are determined enough and want to access your data, they can get it and they will. We are no longer living in a time of breach or hack prevention. We are living in a time of inevitability. As Dick Clarke warned, “It’s no longer a matter of if, but when, an IT breach will occur.”