JEDI will ease DOD’s FITARA woes, but when?

The latest FITARA scorecard released by the House Oversight Committee criticizes the Department of Defense yet again.
Of the eight categories covered in the report, DOD’s letter grade was an “F” in five of them. Citing data reported to Congress and multiple GAO reports, the Committee took DOD to task for failing to break up IT projects into manageable chunks, identify duplicative IT spending, optimize software licensing agreements, and move away from costly legacy IT investments.
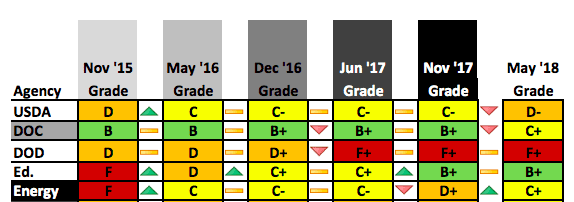
DOD’s FITARA scorecard
In a response to the committee, DOD CIO Dana Deasy noted the challenge of addressing the complicated thicket of IT spending in an agency as large as DOD. He was able to foreshadow progress in one particular area, however – data center consolidation.
The Data Center Consolidation Initiative (DCOI) was created in 2014 as a way of trimming down the out-of-control costs of data centers throughout the Federal government. Since the program’s creation, DOD has closed 834 data centers, with an additional 1,112 closures planned for the current fiscal year.
This massive shift in resources begs the question – how will DOD meet its computing needs as all of these data centers are eliminated? Enter the JEDI program, which is designed to move a significant amount of computing power away from both data centers and private clouds and into a COTS cloud offering. The financial advantages of this approach are clear – JEDI will finally allow DOD to pay for compute based on what it actually uses instead of its perceived capacity requirements.




