Vulnerabilities from SWEET32 in F5 Load Balancers Reveal
Worried about SWEET32 and OpenSSL vulnerabilities? Check out this step by step guide to fix issues before they become critical events. Read more.

Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
How to Mitigate Vulnerabilities from SWEET32 in F5 Load Balancers
The SWEET32 vulnerability is targeting long lived SSL sessions using Triple DES in CBC mode. The attack targets the cipher itself and thus there is and will be no hotfix for this. The only way to mitigate is to either disable the 3DES-CBC ciphers or set a limit on the renegotiation size.
This guide will cover how to configure both in the load balancer, and also how to protect your management interface (only possible by changing the cipher string). To simplify your F5 network try out Indeni which will automate some of the processes in your environment and save you time for the important tasks.
For the official F5 article, please refer to this link: https://support.f5.com/csp/#/article/K13167034
Configuring an SSL Renegotiation size limit
SSL renegotiation options determines if the BigIP will allow the client to make mid-stream reconnections or not. The option called size limit will set a limit, in megabytes, of how much data that is allowed to pass through the connection before an SSL renegotiation will be disabled (on that specific connection). Since the attack targets long lived sessions (or rather high amount of SSL data) this will mitigate the attack. F5 recommends to set the limit to 1000MB.
Possible impact of setting a renegotiation size limit
Clients with renegotiation support will need to be able to handle a failed SSL Renegotiation and instead establish a new one completing the full SSL handshake. This should not pose a problem in the vast majority of applications.
SSL session settings are regulated by SSL profiles. While you can change the parent profiles we do not recommend doing so without doing proper testing.
Procedure to set an SSL Renegotiation size limit via the GUI
- Log in to the F5 administration interface
- Navigate to Local Traffic -> Profiles -> SSL -> Client
- Click on the profile you wish to set the limit to
- In the settings, locate Renegotiation size
- If it’s disabled (see the picture below), click on the custom option checkbox to allow changes

- Change the value from Indefinite to Specify, then enter 1000
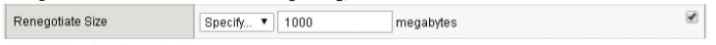
- Click on “Update”
Procedure to set an SSL Renegotiation size limit via TMSH
- Connect to your load balancer via an SSH client
- If not already in the tmsh, enter it
- To modify the size limit of a profile, issue this command and replace the profile name with the full path of the ssl profile you wish to modify:
modify /ltm profile client-ssl <profile_name> renegotiate-size 1000
Example:
modify /ltm profile client-ssl /Common/example.com renegotiate-size 1000
- Commit the configuration to disk by running the command “save sys config”
Disabling 3DES-CBC ciphers in SSL Client profiles and the management interface
This method will remove the affected ciphers from the list of applicable ciphers during SSL connection negotiations. SSL cipher settings are regulated by SSL profiles. While you can change the parent profiles we do not recommend doing so without doing proper testing.
Possible impact of disabling 3DES-CBC ciphers
While most modern browsers supports wide array of ciphers this will still reduce the cipher support of the virtual servers using the modified SSL profile. Depending on your current cipher string this could or could not pose a risk to clients and the virtual servers not being able to agree on a cipher.
Please note that the following guide is just meant to show how to disable these specific ciphers and uses the system default cipher list to do so. Using the default list is not recommended. To determine which cipher list you should use, please read up on ciphers.
To see F5 scripts refer to here.
This guide is a really good start:
Procedure to set an SSL cipher string via the GUI
- Log in to the F5 administration interface
- Navigate to Local Traffic -> Profiles -> SSL -> Client
- Click on the profile you wish to alter the cipher string on
- In the settings, locate Ciphers
- If it’s disabled (see the picture below), click on the custom option checkbox to allow changes.

- Change the value from the current value to <CURRENTLIST>: !DHE-RSA-DES-CBC3-

SHA:!DES-CBC3-SHA:!ECDHE-RSA-DES-CBC3-SHA
- Click on “Update”
Procedure to set an SSL cipher string via TMSH
- Connect to your load balancer via an SSH client
- If not already in the tmsh, enter it
- Show the current cipher string with the following command:
list /ltm profile client-ssl [profile name] ciphers
Example:
list ltm profile client-ssl /Common/example.com ciphers
ltm profile client-ssl Testpartition/testthemciphers { ciphers DEFAULT
}
- Note your current cipher string. In the example above it was “DEFAULT”
- Modify the cipher string with the following command:
modify ltm profile client-ssl [profile name] ciphers <CURRENTLIST>:!DHE-RSA-DES-CBC3-SHA:!DES-CBC3-SHA:!ECDHE-RSA-DES-CBC3-SHA
Example:
modify ltm profile client-ssl /Common/example.com ciphers DEFAULT:!DHE-RSA-DES-CBC3-SHA:!DES-CBC3-SHA:!ECDHE-RSA-DES-CBC3-SHA
- Commit the configuration to disk by running the command “save sys config”
[divider width=”full”]
Start automating your F5 Network with Indeni, see scripts here. Thank you to Patrik Jonsson for contributing this article.



