What BlueCat brings to CDM Phase 3
BlueCat is part of the CDM Phase 3 BOUND offering. Our DNS security system offers unique value which goes beyond standard filters and firewalls.
BlueCat is pleased to be a part of the Continuing Diagnostics and Mitigation (CDM) program run by the Department of Homeland Security (DHS), which offers Federal government agencies a set of pre-approved technologies to increase the security of agency networks.
BlueCat in the CDM context
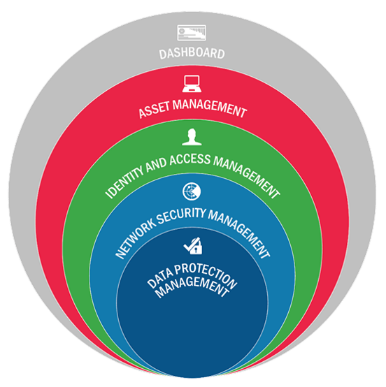
CDM is organized into four phases which roughly correspond to categories of network security tools. BlueCat’s DNS security products are in Phase 3 – the Network Security Management section. In this phase, agencies have already implemented (or are nearly finished implementing) asset management tools to discover what is on the network (Phase 1) as well as identity and access management tools to discover who is on the network (Phase 2). Phase three provides agencies the ability to monitor and manage what is happening on the network.
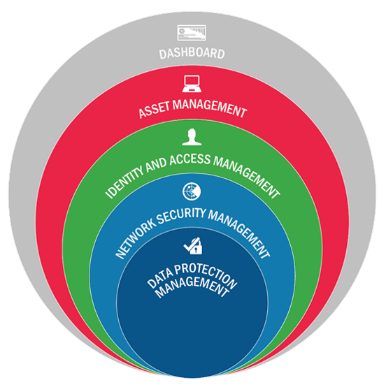
DHS created additional sub-categories for CDM Phase 3 to distinguish between different types of solutions for continuous monitoring of network and perimeter components, host and device components, data at rest and in transit, and user behavior and activities. BlueCat’s DNS security products fall under the “boundary protection” (BOUND) category.
Distinguishing between CDM BOUND products
There are plenty of filters and firewalls in the CDM Phase 3 boundary protection category. So many, in fact, that security officers and procurement personnel are likely to find it difficult to distinguish between them.
What sets BlueCat apart? Our definition of “boundary”. Every other filter and firewall on the market sits on the external boundary of your network. That’s all well and good for filtering inbound traffic. In fact, it’s a necessary component of any security stack.
But what about traffic that originates from within your network? Standard boundary filters and firewalls can manage queries as they leave the network, but tell you nothing about all the steps between the client device and the internet. The best they can do is tell you which recursive server processed the query. They have no data on which device sent the query or how it was processed through the network. It’s the cyber equivalent of smelling smoke, but not knowing where the fire is.
That can be a problem when you’re doing a forensic investigation or hunting for cyberthreats in real time. It’s simply not enough to know that a potential threat exists somewhere on the network. Blocking malicious traffic is all well and good, but it doesn’t deal with the core problem of mitigating threats from actual devices.
Then there’s the problem of internal network traffic. Traditional boundary filters and firewalls are designed to manage external queries. They can’t do anything about queries from one agency server to another. They are blind to malicious insiders, advanced persistent threats, and any other piece of software which hunts for data within the network before attempting to exfiltrate it.
What the “boundary” in BOUND means to BlueCat
For BlueCat, the network boundary is right where the client device sits. BlueCat is the “first hop” in any DNS query, allowing our software to monitor, block, and/or redirect any query before it goes anywhere else on the network. This provides visibility into far more, at a much more granular level, than what boundary-level filters and firewalls can see.
With BlueCat, you get the full context and intent behind every DNS query. The query type, response data, destination IP – all of these things are incredibly valuable for identifying and mitigating cyber threats. BlueCat also identifies DNS tunneling and domain generation algorithms, which are often signs of malicious activity.
Using this data, BlueCat also allows users to create security policies which stop malicious queries from resolving before they do any harm. Querying a domain in Russia? We can stop that. Connected security camera suddenly querying a finance server? No thank you. Infected computer using a domain that was registered just seconds ago? Get out of here.
Incorporating DNS into a CDM security stack
There is no silver bullet in cybersecurity, and DNS is no exception. DNS is a vital part of the “cyber kill chain”, but it cannot carry the burden of cybersecurity on its own. Like every tool in the BOUND category and CDM writ large, DNS is most effective when placed in context. DNS security provides comprehensive visibility into what’s happening on the network. At the same time, multiple types of data are often required to create a complete topology of cybersecurity.
The advantage of DNS is that it is everywhere on the network, cutting across different layers of the Open Systems Interconnection (OSI) network model and typical security architectures. Pairing DNS security from BlueCat with data integrity and application security software would provide a comprehensive security picture which protects against a wide variety of threats.
Contact BlueCat for more information on our DNS security products or see what we have to offer under the EC America GSA contract (SIN 132-44).




