Check Point appliances refresh: how do you compare?
Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
We often get asked if we have data pertaining to the upgrade processes and cycles of Check Point users around the world. The short answer is, YES. The longer one, is that thanks to our indeni Insight service we get a deep view into the Check Point firewall user base. Once in a while, we publicly share the findings we’ve come to based on that data, like we did last September.
Today we’ll take a look at the appliance refresh process across our user base. Apparently the 2012 (and later) appliances are gaining a stronger foothold with almost three quarters of the Check Point firewalls indeni is connected to being these newer appliances. This is in contrast to less than half, just 10 months ago (see the September report referenced above).
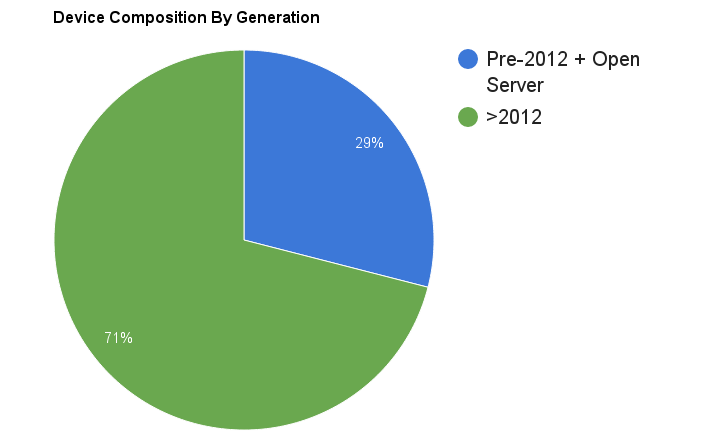
This is a pretty good ratio, considering most older appliances still have until April 2017 before they reach end of support.
In our daily conversations with Check Point customers (some, who are not indeni customers, yet) we see that summer-time is being utilized to complete hardware and software upgrades. It is usually a more relaxed time and easier for the higher ups to approve maintenance windows. It is also before the holiday season, a time of change freeze for most companies.
During this process, we suggest you keep in mind that the recommended way of upgrading a Check Point firewall is through a complete rebuild, even in the case of just a software upgrade. This is better than simply backing up the firewall configuration and restoring it. It is possible because most of the interesting configurations – the security policy – are actually stored on the management server.
However, this approach can also result in issues – routes that are missing, kernel parameters that are no longer set the way they should, SecureXL settings that have been lost, etc. So be extra careful and test things thoroughly before putting the new firewalls in production, as well as after. The list of top 10 issues people run into when working with Check Point firewalls can be found here.
Happy upgrading!



