7 Ways to Manage F5 LTM Traffic With Profiles

Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog

In a virtualized environment, configurations and connections can change on a dime. Leverage these 7 best practices from the Indeni Community to ensure the services that rely on your network and sending and receiving packets at full speed.
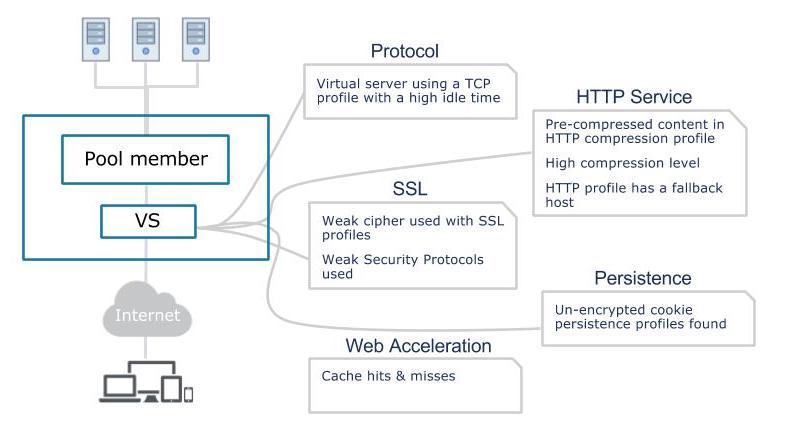
1.Virtual server using a TCP profile with a high idle time
Having very long TCP idle timeouts for virtual servers could make the load balancer keep too many connections open, which in turn could potentially cause memory exhaustion. Indeni will alert when the idle timeout appears too high.
View remediation steps
2.Pre-compressed content in HTTP compression profile
Using the F5 device to compress content is a way of accelerating application content delivery. However, compressing content that is already pre-compressed results in longer response times and is using up system resources in vain. Indeni will alert when already-compressed content types are set for compression.
View remediation steps
3.High compression level
Setting a higher compression level makes compressed content smaller, but the cost of higher CPU usage and longer time to compress the content. The difference in terms of percentage gets lower the higher the level and setting this too high is not recommended. Indeni will alert if the gzip compression level is too high.
View remediation steps
4. HTTP profile has a fallback host
A fallback host redirect a user to a different page/URI. It is in most cases better to use an iRule to rewrite the request. Indeni will alert if fallback is used instead of an iRule.
View remediation steps
5. Weak cipher used with SSL profiles
Weak ciphers could allow for man in the middle attacks. Administrators would ideally want to keep track of their cipher string configurations in order to protect their clients against known attack vectors. This alert verifies that the management interface does not use any weak ciphers.
View remediation steps
6. Weak Security Protocols used
Certain security protocols are now considered weak. Indeni will alert if any SSL profiles are set to use them. Weak protocols could also enable for man in the middle attacks. This alert verifies that the management interface does not use any weak protocols.
View remediation steps
7. Un-encrypted cookie persistence profiles found
According to best practices, cookies should be encrypted when persisting to client browser to avoid security issues. Not encrypting persistence cookies discloses internal information such as internal IP, port and pool name. This information could be used by an attacker to gather information about your environment. Indeni will alert when this is not the case.
View remediation steps
Interested in seeing another use case? Join the F5 Networks discussion on Indeni Crowd or Download Indeni today.



