Fortinet Zero Touch Provisioning – Design, Configuration & Verification
Notice: This blog post was originally published on Indeni before its acquisition by BlueCat.
The content reflects the expertise and perspectives of the Indeni team at the time of writing. While some references may be outdated, the insights remain valuable. For the latest updates and solutions, explore the rest of our blog
Zero Touch Provisioning (ZTP) is a very popular technology on the feature list of networking products. ZTP is common in network devices like switches, Access Points (APs), routers, and firewalls.
The main goal of ZTP is to install a networking device without someone needing to configure it locally. A device that runs factory default configuration finds the management system and automatically receives the configuration. However, it should be highlighted that not all the ZTP implementations are truly ‘zero touch’. So, sometimes vendors use terms like ‘minimal touch provisioning’ or ‘one-touch provisioning’.
This article is part of the series of Fortinet Indeni technical articles. The different methods and advantages of ZTP supported methods by Fortinet are reviewed. The FortiGate design and configuration of the 100% Zero Touch Provisioning method are implemented and tested. Finally, it is presented how Indeni can significantly contribute to the operation and eliminate service outages after the successful deployment of a new FortiGate firewall via ZTP.
Are you a network administrator, system engineer, software engineer, or tech geek? If yes, then read on! This article is for you!
Why use Zero Touch Provisioning?
Zero Touch Provision dramatically reduces the lead time, the number of hours spent on an installation and the number of configuration errors especially if we consider the following:
- The latest annual outage analysis report (2021 hot off the press) by Uptime suggests an aggregated year-on-year average of 63% of failures due to human error.
- Manual configuration is laborious, prone to errors, costly and time-consuming.
- People and travel are expensive.
The installation process is simplified from hundreds of manual steps to the next three simple steps:
- Rack
- Connect
- Power-on
A firewall can be shipped directly from any warehouse to the final location and installed as soon as it arrives. Finally, it is up and running within minutes of installation!
These are potentially huge benefits when there are many sites with no IT staff or new sites are opening frequently, such as stores or temporary offices.
FortiGate Zero Touch Provisioning Methods
FortiGate has many zero-touch configuration methods to achieve connectivity to an assigned FortiManager and receives the configuration. Low-Touch Provisioning requires a customer to manually configure the FMG details on the new FGT firewall.
Those methods are the following:
- Connect to FortiManager via the GUI (Low-Touch Provisioning)
- Connect to FortiManager via the CLI (Low-Touch Provisioning)
- Connect to FortiManager via DHCP option (Low-Touch Provisioning)
- Connect to FortiManager via auto-install script via USB (Low-Touch Provisioning)
- Connect to FortiManager via FortiGate Cloud (Zero Touch Provisioning)
The last method is the only option which doesn’t require any configuration to FortiGate Cloud and FortiManager. This ZTP method will be configured and described in the following sections.
FortiGate Zero Touch Setup
Zero-Touch Provisioning using FortiGate Cloud allows a deployment of FortiGate with minimal interaction.
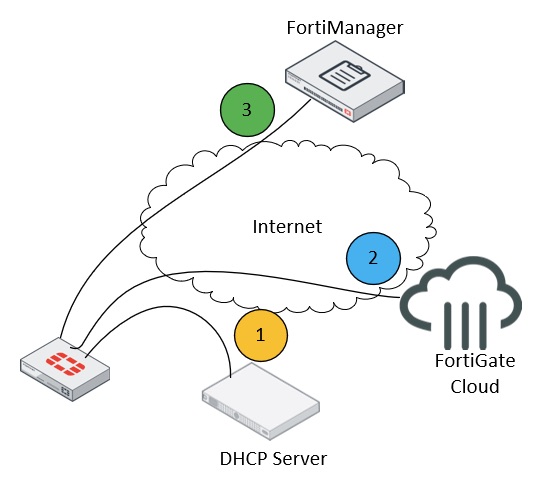
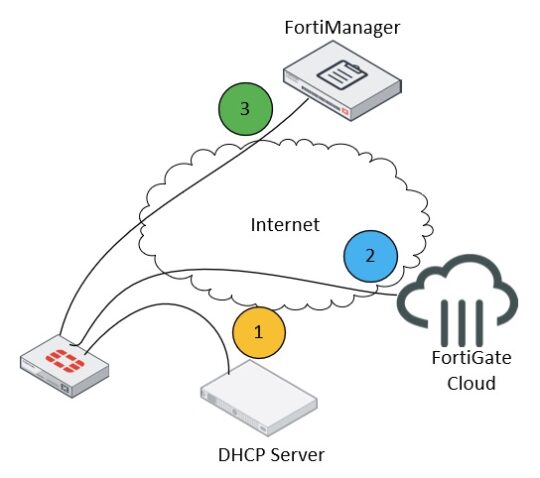
The next actions are performed in a sequential order:
- FortiGate with the default configuration is plugged into the network. It gets IP/DNS settings from the DHCP server to “call home” – communicate with FortiGate Cloud via the internet.
- FortiGate Cloud, based on the imported bulk key license, will push the FortiManager IP address to FortiGate. The IP address of FortiManager should be reachable from the internet and the required TCP/UDP ports should be open.
- FortiManager authorizes FortiGate and pushes the configuration based on the FortiGate S/N or manually. Once this operation is complete, FortiGate is fully deployed and managed.
Let’s move on to test it!
Provisioning FortiGate Cloud
First login to the FortiGate cloud portal by using a Fortinet account. Then select the “inventory” tab from the Menu on the left.
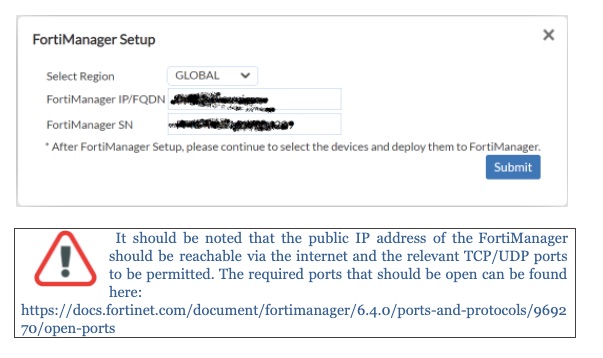
Select the “FortiManager setup” tab from the Menu on the right to set the FortiManager configuration. This configuration is going to be pushed to FortiGate during the initial boot with the default config.
The FortiManager IP or FQDN as well as FortiManager S/N should be completed on this Menu.
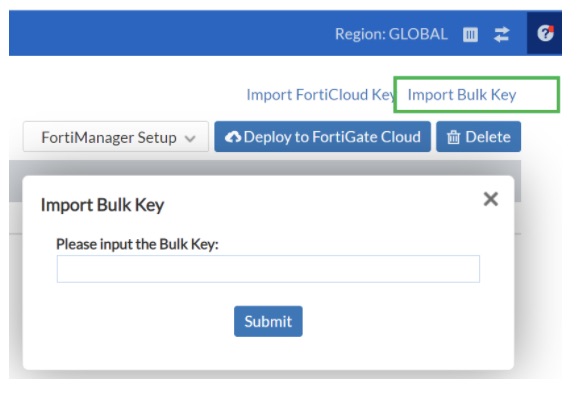
Select Import Bulk Key on the right.

Provisioning FortiGate
A FortiGate 101F is used to test the ZTP. It has a default configuration, and it is powered on. The actions will be performed in the following order:
- FortiGate will receive IP address and DNS info from the DHCP server connected to the network upon the reboot.
- FortiGate will reach FortiGate Cloud as illustrated below.
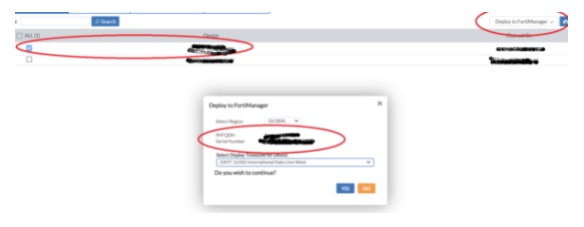
Select the firewall, then the “Deploy to FortiManager” option. The configuration with the FortiManager settings used on Fortigate Cloud is successfully pushed to the firewall as shown below.
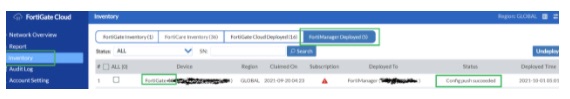
This can be verified from the FortiGate CLI where the IP or FQDN of FortiManager has been pushed to the configuration via the ZTP described in the above process.
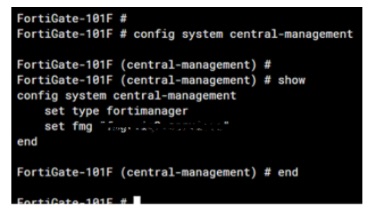
Provisioning FortiManager
A new ADOM has been created for use with this firewall as illustrated below.
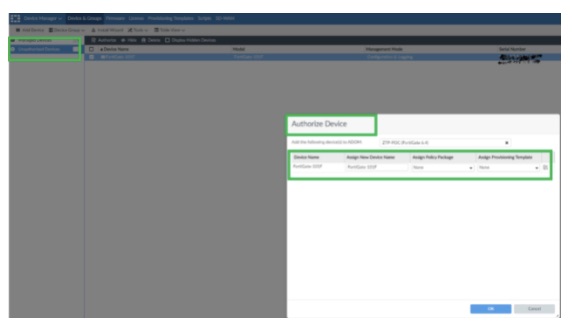
With ZTP, the new firewall appears as an unauthorized device without performing any action on FortiManager. An alarm will be triggered on the FortiManager top right Menu.
The next step is to authorize the firewall and assign the relevant preconfigured templates.
Alternatively, the firewall is pre-provisioned based on the S/N. The configuration templates are automatically pushed to the firewall without any manual intervention.
Then select the “Add device” option from the “Device Manager” menu.
Then select the “Add model device” option.
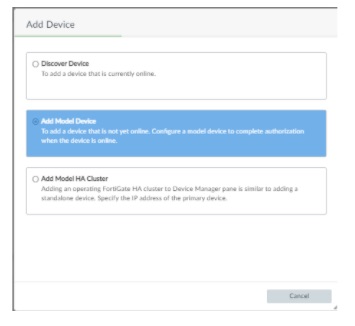
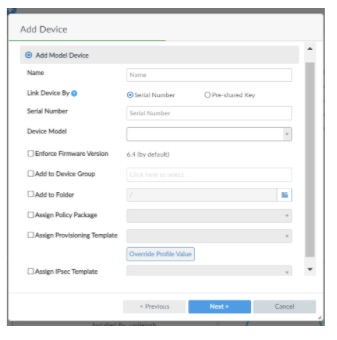
Finally, complete the Serial Number and the additional configuration settings to be pushed to the firewall. Parameters like the relevant Device Group, Provision Template, Firmware version, etc. can be set.
Verifying FortiManager
FortiGate has successfully received the configuration and it is presented in the “Device & Groups” tab. Now the firewall is fully managed by FortiManager.
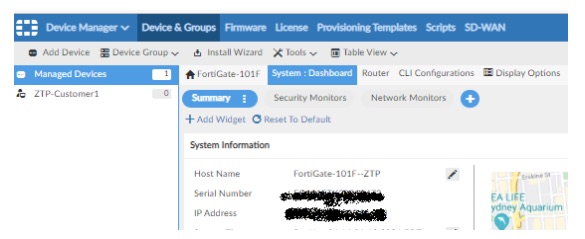
The template has successfully been pushed to the firewall via the ZTP process, as presented on the “System : Dashboard” menu.
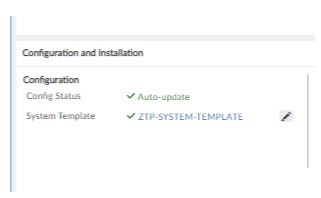
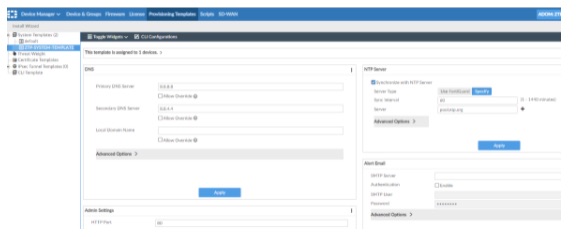
Indicative settings on the used ZTP system template are presented in the figure below.
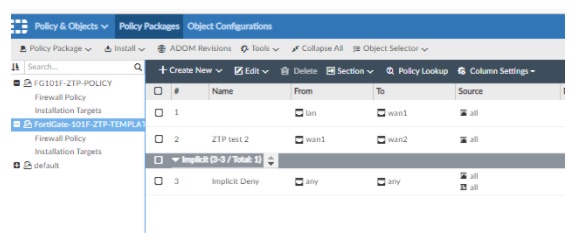
Finally, the policy template which includes the firewall rules has been deployed with success.
FortiGate and Indeni
The Zero Touch Provisioning process has been completed and the firewall has been successfully configured and deployed. Next, ensure the firewall operates as intended and avoids service outages.
To address these challenges, Indeni and Fortinet have established a technology partnership. Indeni ensures FortiOS configurations are done correctly and consistently. In addition, FortiGate performance is continuously assessed and optimized. By using Indeni, engineering and operations teams can be notified of misconfigurations and degradations in performance before they result in service downtime!
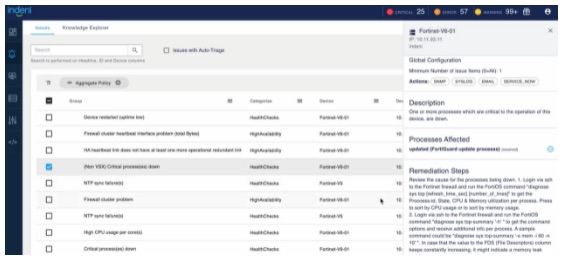
Indeni automatically detects issues relating to FortiGate and offers a way to remediate them. IT operations teams can gain Fortinet specific knowledge from the descriptions and recommended remediations built from real-world experience of certified Network Security Experts. Check out our top automation elements that can help you prevent costly disruptions.
Summary
Zero Touch Provisioning significantly reduces the delivery time, the number of hours spent on an installation and the number of configuration errors during the initial deployment. The installation process and initial configuration/staging is now simplified with three simple steps: Racking, Connect on the Network and Power on!
A Network Security Administrator typically spends 70% of his or her time identifying and remediating known errors. In addition, the 75% of outages (according to the Uptime’s 2020 annual survey) can be avoided if IT operations teams receive an advanced notice with respect to common issues stemming from hidden configuration skew, forgotten ongoing maintenance, or a combination of lack of adherence to vendor, industry, and high-availability (HA) best practices. All these challenges are addressed by Indeni!
To sum up, ZTP can significantly reduce the initial deployment time and Indeni can reduce the operation time and the unexpected service outages with continuous analysis and remediation.
If you like this article, please share it by clicking on one of the social media sharing icons at the top of this page.
More articles for Fortinet and Indeni are coming soon. Stay tuned ☺



