3 cloud networking challenges architects should know
Collaboration is the key to gaining control over the cloud networking challenges of connectivity, security, and observability. Learn more with BlueCat.

While cloud computing has brought incredible benefits, cloud networking presents particularly complex challenges.
Cloud architects can feel like they are dancing on quicksand without a firm foundation of knowledge in technical disciplines like networking. Meanwhile, network operators can feel at a loss with the plethora of options the cloud presents. Cloud is a dynamic and ever-evolving set of services and features, sowing the seeds for potential chaos across an organization.
There are three primary aspects of cloud networking that present particularly weighty challenges: connectivity, security, and observability.
This post will first explore the complexities of cloud networking and connectivity. Then it will examine the implications for security. Next, it will look at how to effectively measure and monitor cloud networking components. Finally, it will touch on how collaboration with networking teams is the key to getting all this complexity under control.
The complexities of cloud networking connectivity
Cloud computing networks are highly segmented, with multiple options for connectivity. It’s no longer as simple as advertising a route or creating a VPN tunnel.
There are numerous variables to account for as well. These include peering, traffic management gateways, nested networks, and a lack of Layer 2 control.
Furthermore, with all the complexity of managing connectivity, security can become an afterthought. The desire to ‘just get this working’ leaves wide-open ports and protocols that are never remediated.
Additionally, the lack of a well-defined border between public and private networks further exacerbates the problem. Traditional boundaries delineated by firewalls and security stacks don’t make sense in a distributed cloud workload.
To even begin implementing proper security and connectivity, one must track and observe the network infrastructure as it functions. But, once again, the sources for network information are disparate and fragmented. Traditional firewall logs and packet captures are not enough to diagnose a problem. One must collect, aggregate, and analyze traffic data from tens or hundreds of sources.
It is into this world that cloud practitioners are thrust, and it is their remit to improve it. But they need not go it alone!
The core principles behind connectivity, security, and observability still hold up; it is the implementation details that have changed. By collaborating with subject matter experts in networking, security, and application development, cloud practitioners will find the cloud networking challenge is not insurmountable.
Cloud networking connectivity for modern applications
Modern applications born in the cloud are no longer composed of virtual machines each running a component of the application. Cloud-native application development practices have broken monolithic applications into microservices running in containers on platforms like Kubernetes.
Beyond containers, developers have taken advantage of native platform services in the cloud, such as serverless or database-as-a-service. A common application architecture could include:
- a web frontend running in Kubernetes,
- application servers running on virtual machines,
- a database provided as a service, and
- batch processes being handled by functions.
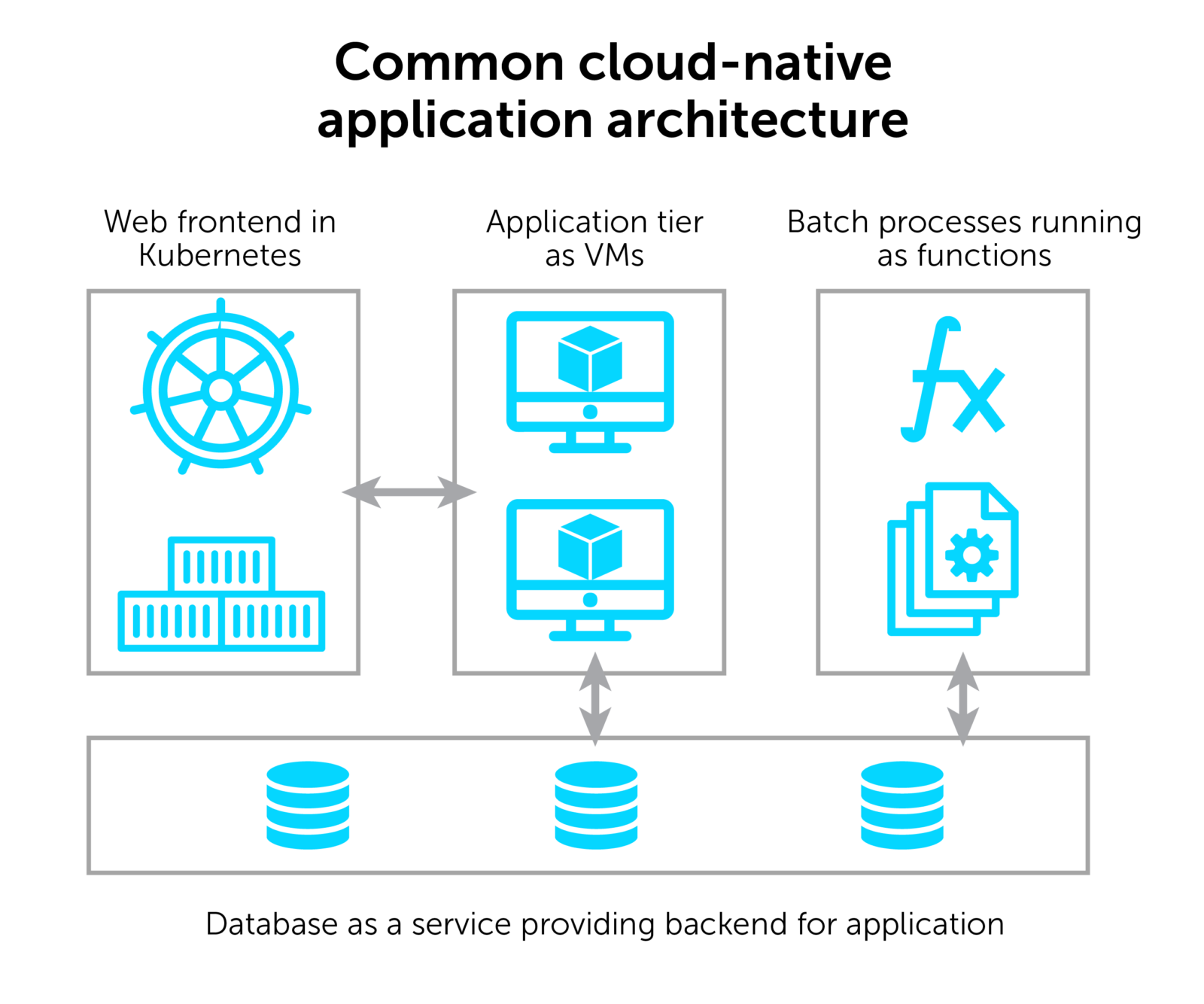
All of the components of the application must be connected using the native cloud constructs. This includes virtual private clouds, private endpoints, API gateways, and ingress controllers. All of this complexity in a single application!
Adding more applications to the mix further increases complexity. A common practice is to dedicate a virtual network to each application. After all, there is no cost for creating additional networks. Per-application dedicated virtual networks help maintain strong boundaries and limit the blast radius of changes made by a development team.
Implementing connections between applications
While this is a pragmatic approach, applications do not live in a vacuum. They often require connectivity to other applications. Cloud architects must connect several virtual networks within cloud infrastructures together to achieve the required connectivity. Meanwhile, they must deal with issues like overlapping IP addresses and DNS zones.
The knowledge to wire up all of these components properly may exceed the skill set of a typical cloud architect. A networking subject-matter expert familiar with designing complex segmented networks is invaluable for architecting a performant and sustainable solution.
Implementing connections across regions and cloud providers
To further compound the complexity, organizations often have an application portfolio spanning multiple regions and cloud service providers. And on-premises data centers have not disappeared from the picture, either.
It’s unreasonable to expect a cloud architect alone to design a proper WAN topology. They must consider routing, path selection, and resiliency. The networking team has the requisite experience. They can surely assist the cloud team with properly planning out their multi-cloud and hybrid cloud networking strategy.
At the same time, the cloud team can introduce the networking team to cloud networking solutions. These services could potentially improve or replace components of the traditional WAN architecture.
Multiple clouds and integration with on-premises data centers complicate DNS and IP address management as well.
Each public cloud has its own internal DNS service and namespaces, as does each Kubernetes deployment. Application teams also create private DNS zones. The dream of a grand unified DNS authority across the environment may be untenable. But one must still manage and troubleshoot DNS zones across the virtual networks and services in each cloud.
BlueCat’s Cloud Discovery & Visibility can help you create end-to-end visibility and discover resources across service boundaries.
Security considerations for cloud networking
Certainly, applications are no longer monoliths sitting on a handful of servers in a data center. In the cloud-native era, they have become a complex amalgam of microservices and platform-as-a-service offerings. Furthermore, they exist across a highly segmented network backdrop.
The micro-segmentation of applications is an opportunity to implement enhanced security. And not just between applications, but between the individual components that comprise an application. Each cloud provides network security through:
- security groups at the interface level,
- network access control lists at points of transfer, and
- web application firewalls for load balancing and ingress.
The challenge is not implementing all of these new cloud constructs. The challenge is doing it properly, following industry best practices and conventional security theory.
Application developers can easily add a public IP endpoint to their service. That makes the potential attack surface for your environment immeasurably larger. Every application poses a potential entry for a malicious attacker. And it cannot be up to the cloud team alone to implement the correct level of security.
Furthermore, the attack surface doesn’t just extend across a single cloud. Security is still required as applications in multiple clouds are connected together and plumbed into existing on-premises networks. It must occur at each segment in the network, from the endpoint to the application to central services.
Modern solutions like SASE and Zero Trust deal with these new challenges. However, a single group cannot deploy these solutions. Instead, they require collaboration across the development, security, networking, and cloud teams to properly implement and maintain.
Measuring and monitoring cloud networking components
The Peter Drucker maxim, “If you can’t measure it, you can’t manage it,” certainly rings true for cloud networking. Indeed, properly measuring and monitoring cloud-based networking components is critical for improving the security, connectivity, and performance of applications.
As always, it’s more complicated with the cloud. Proper monitoring now must incorporate all the disparate pieces in the cloud environment. This includes load balancers, virtual network logs, traffic flows, Kubernetes clusters, and the various platforms-as-a-service.
Knowing where and how to capture the information is just the first step. Different metrics may interest each team in the organization. The security team may want to investigate failed requests on the load balancer. Meanwhile, the application team is more interested in the average request time.
Collecting everything is not a viable option. It’s up to the cloud team to ensure that each team is receiving the data that is relevant to them.
After capturing information, it still needs analysis (measurement) to be of any use to each team. It requires tools and processes that merge and refine all the raw data no matter where it flows from.
For instance, DNS information proliferates across cloud environments. It requires a solution like BlueCat Cloud Discovery & Visibility that observes various DNS sources and builds a complete representation.
Cloud networking is easier with collaboration
I may have painted a pretty grim picture of endless complexity and overwhelming challenges for the cloud architect. But fear not—there is hope in sight!
Organizations across the globe have found ways to wrangle this complexity and bring it under a semblance of control. What is the aspect all these successful organizations have in common? Collaboration.
The first step to make things better is to realize the size and scope of the problem. Then, the second step is asking for help. Cloud teams need to build bridges of collaboration with other teams in the organization.
At an application level, that could be a team composed of members from each group practicing DevOps together. Each team member brings their own expertise to the table and gets involved earlier in the decision-making process.
At the enterprise architecture level, it is not uncommon to see a Cloud Center of Excellence (CCoE) form. In a CCoE, each group works together to develop standards and best practices for the organization as a whole. Application-level teams can implement the resulting documentation and example architectures.
CCoEs can do their work confident that an overriding set of principles guides them. Furthermore, the CCoE or similar body can recommend toolsets for developing operational consistency across smaller teams.
It is foolish and impractical to believe a single cloud team has all the necessary knowledge to navigate cloud networking. The key to successful cloud adoption is collaboration. Working together as a cohesive team, organizations can improve their connectivity, security, and observability in the cloud and beyond.





