DNS helped stop the WannaCry ransomware attack
In 2017, the world was confronted by a ransomware attack that demonstrated how DNS visibility and control are key to any layered security strategy.

The 2017 WannaCry ransomware attack was one of the most devastating of the decade, impacting individuals and organizations in over 150 countries. It crippled hospitals in the UK, shut down manufacturing lines, and upended people’s lives.
A few hours after the ransomware appeared, a 22-year-old security researcher found an unregistered domain in the code. After registering that domain (the memorable “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com”) to create a DNS sinkhole so he could collect additional data, he unintentionally activated a kill switch that helped many affected.
The essential role of DNS sinkholing
The role that DNS played in thwarting this attack is fascinating. The malware was designed to try to resolve an unregistered domain to test whether it was executing in a sandboxed environment. If the malicious domain existed, WannaCry died to protect it from exposing any other behavior.
When the researcher spent $10 to register the domain, he only intended to set up a sinkhole server to collect additional information. Yet in doing so, he triggered that sandbox check. Ultimately, that subverted the attack by blocking malicious traffic from a single DNS server. Simple DNS concepts and actions were critical in identifying the core issue. These actions blocked the malicious command-and-control servers from receiving any DNS queries from infected devices.
This incident is a good demonstration of how visibility and control are critical to any layered security strategy. For example, a security solution that leverages DNS could have enforced policies on critical devices. This would have blocked the initial download of malware used in this attack. DNS also could have easily identified patient zero, enabling the incident response team to surgical address affected devices first.
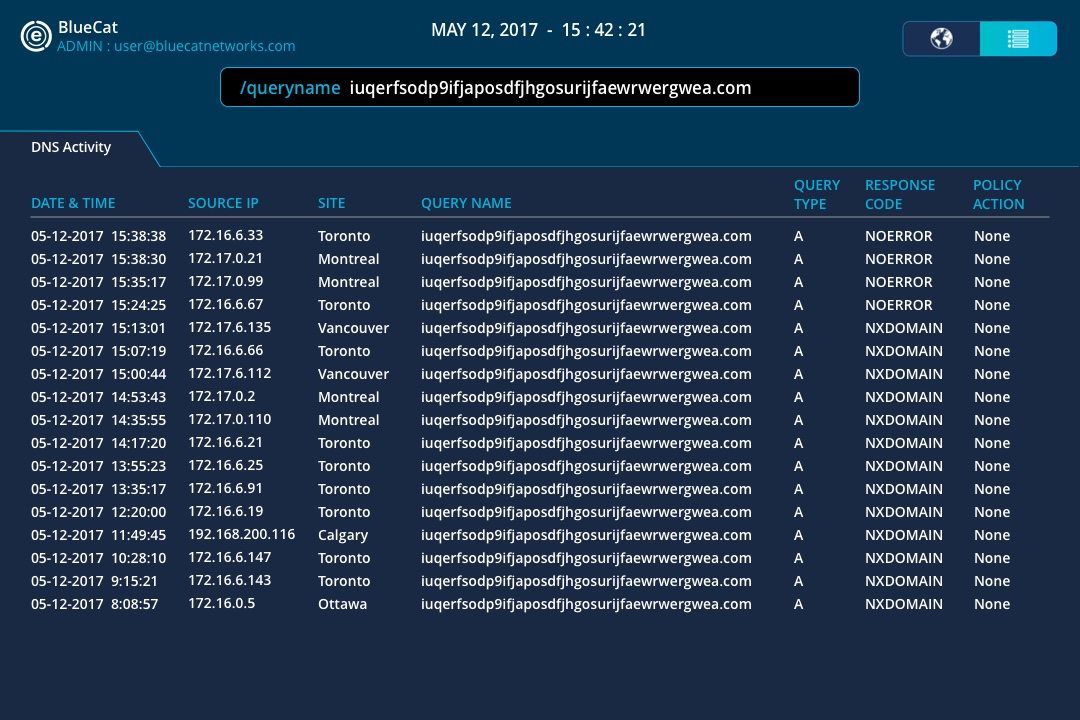
The BlueCat platform provides immediate visibility into lateral movement and patient zero within a compromised organization’s network.
The importance of a layered defense strategy
BlueCat stresses the importance of a layered defense approach when it talks to customers about DNS security. Security must cover perimeters, the cloud, endpoints, the network, data, and applications.
The WannaCry attack was specifically built to get past sandboxing tools. To stop it, an enterprise needed parallel ways of blocking the malware’s attempts to connect with remote servers. The concept and benefit of a layered security approach is simple: A comprehensive implementation of different security solutions covers gaps in the others’ capabilities.
There are many lessons to learn from the WannaCry attack. Clearly, a comprehensive and vigilant update policy is a must. A multi-layered security policy is a smart strategy for information security officers. Yet the next logical step is to find new methods and new sources of data (like DNS) to assess risk, identify issues, and take immediate action.
Adaptive DNS infrastructures enable businesses to seamlessly centralize and automate DNS services. With that infrastructure in place, they can leverage DNS data for superior control, compliance, and security.




