IPAM should work like a vending machine
There are alternatives to free-for-all service desk tickets for provisioning IP addresses: automation with an IPAM system.

There are alternatives to free-for-all service desk tickets for provisioning IP addresses: automation with an IPAM system. Here are three of the most effective and efficient automated IP address management models to maximize the potential of your network.
1) The open access model
First is what you might call “open access”. In this model, the network team opens up the IPAM system for everyone to allocate IP addresses as they like.
Speed and scale are clear advantages of this model. When people need to get an IP address, they don’t want to wait for someone on the network team to deal with a service ticket. When they can just go and grab what they need directly, nothing needs to slow down.
System integrity is one of the weak points of this model, especially if you’re using IP address spreadsheets as a management tool. If anyone can grab and use an IP address, the network team is trusting end users to adequately document what they’re doing. If someone takes an IP address and doesn’t note it on the spreadsheet, the same IP address could easily be allocated elsewhere, causing a conflict that brings down the network.
Security is also an issue with this model. When the entire system is open, everyone on the network can see the IP addresses assigned to specific devices. That can lead to all sorts of security problems and malicious insider activity.
In sort, the open access model depends on trust and accountability. When network teams open up their systems for general use, they want to be sure that everyone who’s making changes understands the impact of their actions (and is accountable for those actions). This tends to be workable only in smaller environments, where all the network admins know one another.
2) The service desk model
The second way to allocate IP addresses is your standard service desk model. This is what most enterprises are used to: if you want an IP address, you submit a service desk ticket. Network admins check their spreadsheet or IPAM solution for an unused address, assign it to a device or server, mark it as “in use”, and resolve the ticket in ServiceNow or whatever platform they use.
System integrity is the main advantage of this model, and that’s why most IT teams use it. When the network team controls IP address allocation, they can make sure that address conflicts don’t bring down the network. They can also optimize architectures, allocating IP addresses to the zones and organizational units where they belong.
Security is also an advantage of the help desk model. When only network admins know the architecture and procedures behind IP address allocation, the risk of misuse by a malicious insider is dramatically reduced.
The main challenge with this model is speed. The process of actually allocating an IP address is simple and quick enough, but it doesn’t scale well. In a large organization, the standard churn of IP space for employee devices, IoT sensors, and internal servers can quickly fill up the pipeline of several network admins if they’re managing IP space through a manual process.
If you’re in the cloud, the trickle of IPAM service tickets quickly turns into a flood. All of the VMs and containers that get spun up and spun down in the cloud create a dizzying management challenge for network administrators. At a certain point, there just aren’t enough hours in the day to answer the mail on these tickets. DevOps and cloud teams are often kept waiting for basic IP address requests, slowing down their rhythm and ability to deliver innovative capabilities.
That inability to allocate IP addresses quickly points to a related challenge: shadow IT. When DevOps and cloud teams can’t get IP addresses when they need them, they’re going to look for alternatives. They’ll stand up a BIND server in the cloud and bypass the network team altogether. When that happens, all the advantages of system integrity and security go out the window. Suddenly, the process of IP address allocation is decentralized and the network team is left without visibility into a significant part of the network.
So while the service desk model gives network teams the control they crave, that control comes at a significant cost. It can also prove illusory, especially where cloud environments offer a viable alternative.
3) The vending machine model
Most network teams feel caught between open access and the service desk model. There seems to be an intrinsic tradeoff between service quality, control, and security. But there is a third way. Our nickname for this is the “vending machine” model.
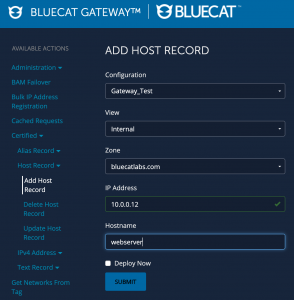
When the underlying IPAM system supports automation, network teams can deliver IP addresses quickly and securely while maintaining control over the back-end through a self-service model. Users see a basic UI like this:
This is basically the same kind of information they would input as part of a service desk ticket. The difference is what happens next. In an automated system, the request goes directly into the IPAM engine, which allocates an IP address based on the parameters set by the network team. The end user receives the IP address instantly, and the “ticket” is closed. The IP address is marked as “in use” by the system, ensuring that it isn’t used elsewhere.
Using this “vending machine” approach for IP addresses is clearly the fastest option. Even the open access model requires a manual look at which IP addresses are available. Automated IPAM systems make that calculation instantaneously and spit out the right answer every time. In a DevOps/cloud environment, this means that IP address allocation doesn’t slow anything down – the need for shadow IT is eliminated.
System integrity and control are also distinct advantages of the self-service approach. When network admins dictate which IP addresses are available to the automation engine, they can ensure that IP conflicts don’t bring down the network. The parameters of the self-service engine can also keep users from making manual, “fat finger” errors by double-checking their work against system parameters.
On the security front, an automated back end allows for a form of role-based access control. Network admins can create user profiles which allow them access to IP address space or other functionality based on their role within the organization. The user only sees what they’re allowed to see, effectively preventing them from accessing IP space or other critical data from unrelated areas of the network.
Everyone wins with the vending machine option. Network admins keep control over the IP space they manage, ensuring system reliability and security. End users get the IP addresses they need quickly and easily, without having to resort to shadow IT.
How do you get started with this vending machine approach? We’re so glad you asked. Our network automation page can get you started.