Simplify NIS2 compliance with DNS management
Learn whether the EU’s NIS2 requirements apply to your organization and about how DNS management and BlueCat can boost your path to compliance.
Last updated: July 31, 2025

If your organization provides critical infrastructure or essential services in the EU, deadlines are looming to comply with NIS2.
NIS2 is an updated EU regulatory framework to address evolving cybersecurity threats and vulnerabilities. Set to become law next month, NIS2 regulations will impact many medium- to large-sized public and private entities.
There are strict requirements for cybersecurity risk management and incident reporting. It covers a wide scope of entities and imposes stiff penalties for non-compliance. There are numerous baseline measures that organizations must ensure they have in place.
Among them is DNS management, which plays a vital role in keeping your network reliable and resilient. It’s crucial for ensuring you meet NIS2 mandates.
Don’t let requirements for NIS2 compliance catch your network team off guard.
In this post, we will explore what the NIS2 directive is and whether it applies to your organization. Then we will examine the directive’s requirements. Next, we will look at the crucial role DNS management plays in your network’s cybersecurity posture. Finally, we’ll touch on how BlueCat products offer a path to accelerate your organization’s NIS2 compliance.
What is the NIS2 directive?
The Network and Information Security Directive (NIS) was a landmark cybersecurity regulatory framework established in the European Union (EU) in 2016. The second iteration, NIS2 (or, alternatively, NIS 2), tackles the escalating cybersecurity challenges and vulnerabilities facing critical infrastructure and essential services in EU member states.
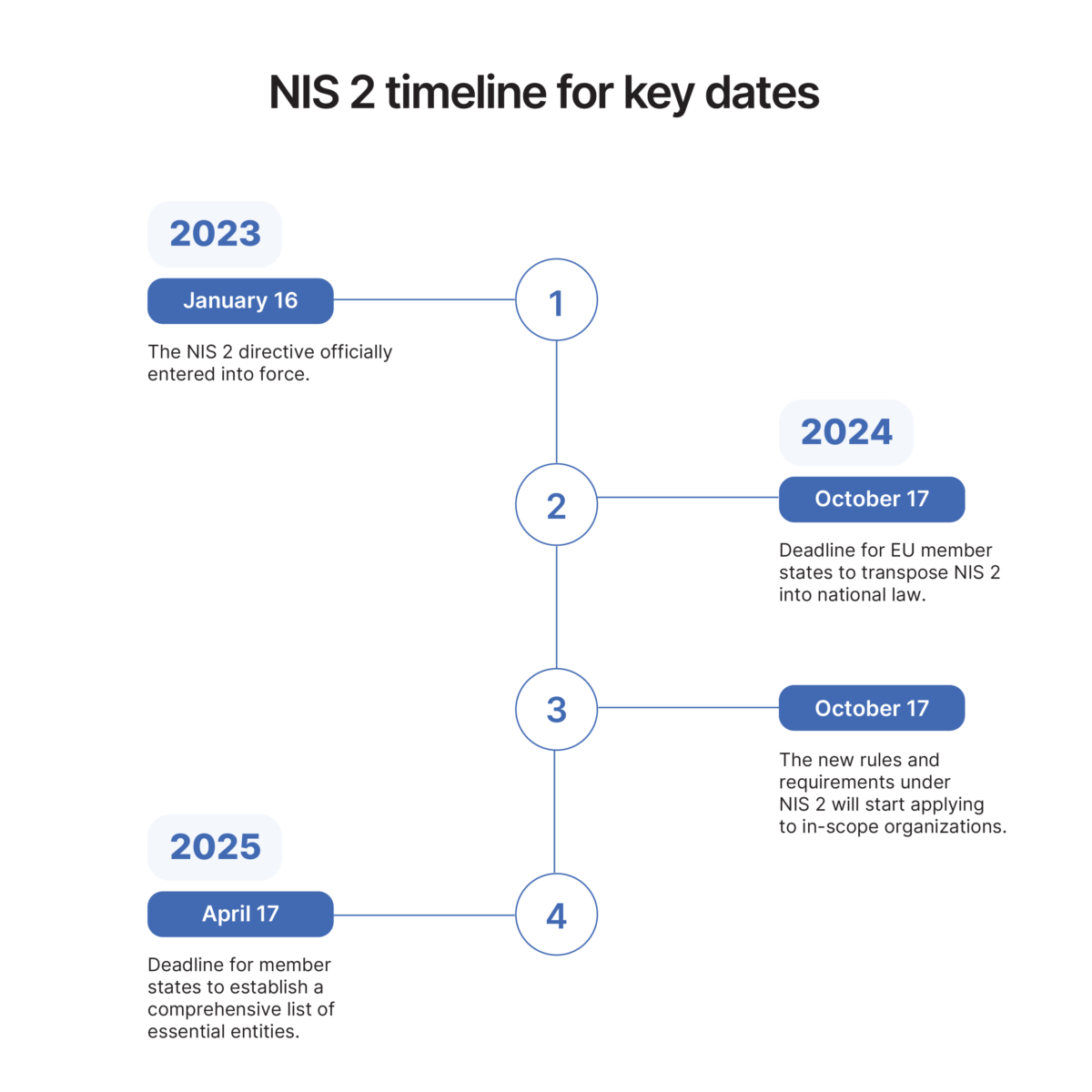
Each EU member state must transpose this updated directive into national law by October 17, 2024.
NIS2 recognizes an evolving threat landscape and inadequacies of the original directive. This version aims for member states to enhance their national cybersecurity frameworks. They must ensure they have competent authorities, crisis management frameworks, and vulnerability databases. Member states must improve cooperation, risk assessments, reporting, and certification schemes.
Compared to its predecessor, the NIS2 directive features stricter requirements for cybersecurity risk management and incident reporting. It expands the scope of entities that it covers and imposes stiffer penalties for non-compliance.
Does the NIS2 apply to my organization?
The NIS2 directive applies to medium- to large-sized public and private entities that provide critical infrastructure or services vital to the EU economy and society. The directive categorizes covered entities into two categories, essential and important, defined by size and type.
Essential and important entities
An essential entity is a large organization that operates in a sector of high criticality. According to the directive, a large organization has at least 250 employees. And it has an annual turnover of at least €50 million or an annual balance sheet of at least €43 million.
High criticality sectors for essential entities include:
- Energy
- Transport
- Banking and financial market infrastructure
- Health
- Drinking water and wastewater
- Digital infrastructure (such as DNS service providers, cloud computing services, and content delivery networks)
- Information and communication technology service management (business-to-business managed service providers and managed security service providers)
- Public administration
- Space
Essential entities face stricter supervision and higher penalties for non-compliance.
Meanwhile, important entities are medium-sized with at least 50 employees. They operate in other critical sectors that don’t fall under the essential category. And they have an annual turnover of at least €10 million or a €10 million balance sheet.
Other critical sectors for important entities include:
- Postal and courier services
- Waste management
- Manufacture, production, and distribution of chemicals
- Production, processing, and distribution of food
- Manufacturing
- Digital service providers (search engines, online marketplaces, and social networks)
- Research
For critical sector organizations that do not meet the ‘essential’ category size minimum, NIS2 still deems them ‘important’ entities.
NIS2 also mandates applicability for certain organizations, regardless of size. This includes providers of public electronic communications networks, trust services, and DNS services. Additionally, applicability can be mandatory for smaller entities in some cases. This includes if they are sole providers of essential services or if their disruption poses significant risks to society.
The role of supply chains
Supply chains and suppliers play an important role in cybersecurity. Numerous times, entities have been the victim of cyberattacks wherein malicious perpetrators exploited vulnerabilities affecting third-party products and services. Entities must assess and consider the overall quality and resilience of products and services they procure. Furthermore, they must pay attention to the cybersecurity practices of their suppliers and service providers.
Determining jurisdiction and if you fall within scope
Under NIS2, each EU member state regulates the essential and important entities established within its borders. Entities operating in multiple member states are subject to each member state’s jurisdiction concurrently.
However, the directive recognizes the borderless nature of entities providing digital infrastructure. These entities fall under the jurisdiction of the EU member state in which they have their main establishment. This is where an organization predominantly makes cybersecurity risk management decisions or carries out cybersecurity operations.
EU member states must identify the entities in their state that fall within NIS2’s scope by April 17, 2025.
It’s important for your organization to determine if it falls within scope. If so, your organization must identify which member states it falls within and register before the deadline.
What are the NIS2 requirements?
Four areas of focus and 10 baseline security measures
The NIS2 directive aims to reduce cyber risks with requirements across four key areas. These are risk management, corporate governance, incident reporting, and business continuity.
Risk management: Organizations must implement comprehensive risk management strategies to minimize cyber threats. They must conduct regular risk assessments, establish security policies, and implement measures to protect the integrity, confidentiality, and availability of their systems.
Corporate governance: An organization’s management body is responsible for overseeing and approving their respective entities’ protocols for cybersecurity risk management. Additionally, they must ensure effective implementation, including adequate cybersecurity training.
Incident reporting: Covered entities must report significant cyber incidents to relevant authorities promptly. They must provide detailed information about the nature of the incident and the mitigation measures taken. Furthermore, entities must provide initial notification no later than 24 hours after learning of an incident.
Business continuity: Entities must create a strategy that details how they will respond to and recover from incidents. The goal is to minimize disruptions and ensure business continuity following an attack.
To support these areas, NIS2 outlines ten baseline security measures. These measures cover:
- Risk analysis and information system security policies
- Incident handling
- Business continuity and crisis management
- Supply chain security
- Security in network and information systems acquisition, development, and maintenance
- Assessment of the effectiveness of cybersecurity risk-management measures
- Basic cyber hygiene and cybersecurity training
- Policies and procedures for cryptography
- Human resources security, access control policies, and asset management
- Multi-factor authentication
Penalties for non-compliance
The NIS2 directive imposes strict penalties for non-compliance, including non-monetary remedies, fines, and criminal sanctions.
Member states’ supervisory authorities can levy non-monetary remedies against non-compliant entities. This can include compliance orders, binding instructions, security audit implementation orders, and threat notification orders to entities’ customers.
Fines for non-compliance reach up to €10 million or 2% of global annual revenue for essential entities. Meanwhile, fines for important entities can be as high as €7 million or 1.4% of global annual revenue.
Supervisory authorities can hold top management personally liable for gross negligence after a cybersecurity incident. Additionally, they can order organizations to publicly disclose violations or make public statements identifying those responsible. Furthermore, authorities can temporarily ban executives of essential entities from holding management positions.
DNS management: A core element of a secure network
According to the NIS2 directive, “Upholding and preserving a reliable, resilient and secure domain name system (DNS) are key factors in maintaining the integrity of the internet and are essential for its continuous and stable operation, on which the digital economy and society depend.”
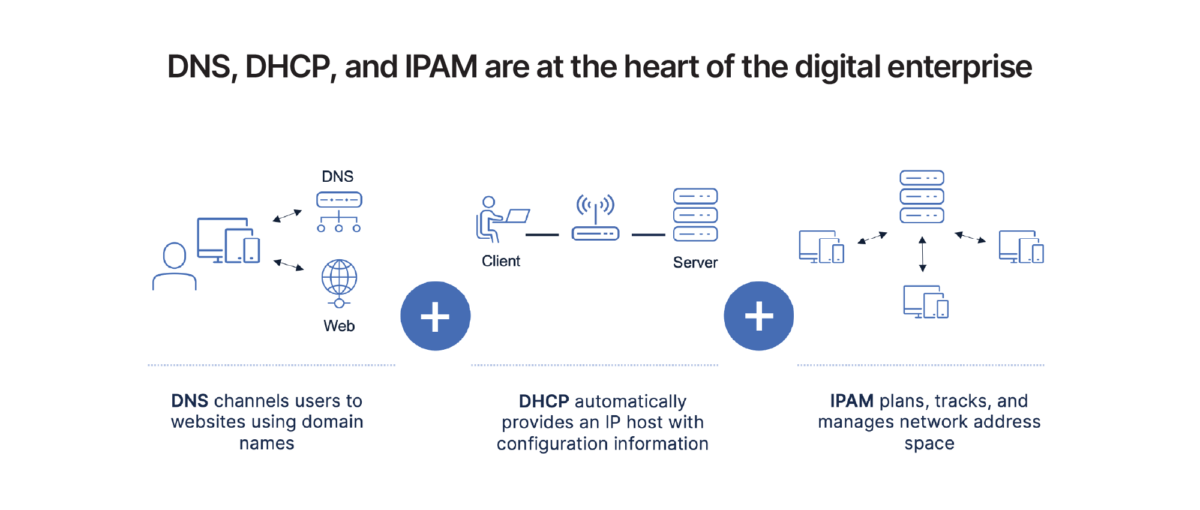
DNS is a hierarchical naming system that allows communication across devices on a network. Most commonly, it translates human-readable domain names (like bluecatnetworks.com) to computer-friendly Internet Protocol (IP) addresses (like 104.239.197.100). Essentially, it allows us to connect to websites without having to memorize a string of numbers.
But DNS is first and foremost designed to correctly and efficiently respond to queries, not question their intent. As a result, DNS has inherent limitations, inviting cyber attackers to use it as a potential vector. A well-orchestrated DNS attack against an unprotected network can bring an organization to its knees.
“Upholding and preserving a reliable, resilient and secure domain name system (DNS) are key factors in maintaining the integrity of the internet and are essential for its continuous and stable operation, on which the digital economy and society depend.”
Networks are growing increasingly complex and expanding to hybrid and multicloud environments. As a result, it has become an even greater challenge to maintain centralized visibility of DNS across your network.
Organizations need a consolidated, automated, and streamlined approach to managing DNS, dynamic host configuration protocol (DHCP), and IP address management (IPAM). Together, we call these DDI. A DDI management solution can then work in tandem with protective DNS solutions and network observability tools. Combined, they offer a robust answer to meeting the NIS2’s mandate.
How BlueCat accelerates NIS2 compliance
Solutions offering unified DDI, protective DNS, and network observability and intelligence can help enterprises comply with NIS2 requirements.
- Unified DDI solutions integrate DNS, DHCP, and IP address management functionalities into a single platform. They provide centralized visibility and control of IP resources and core network services.
- Protective DNS solutions enhance network security by monitoring and filtering DNS traffic to block malicious queries. They prevent access to harmful sites or attackers’ command-and-control channels. Furthermore, they help with compliance and reporting requirements.
- Network observability and intelligence solutions focus on ensuring that your network infrastructure is secure, reliable, and resilient. They offer features such as continuous monitoring and assessment.
Together, these types of solutions address many elements of the NIS2 directive.
They offer improved network visibility and automate network management. Further, they can help you meet compliance, reporting, and audit requirements. Additionally, they boost resilience and redundancy. Finally, they help detect and mitigate cyber threats and quicken incident response and recovery.
Three of BlueCat’s products—Integrity, Edge, and LiveAssurance—are solutions with these core capabilities and features. Each can help enterprises comply with NIS2 requirements.
Our comprehensive white paper, Complying with the NIS 2 cybersecurity directive, details how BlueCat can help. Specifically, it includes mappings of how our products help address specific mandates in NIS2 articles.
Download our white paper today to learn about how you can accelerate your journey to NIS2 compliance.
Published in:
Published on: September 24, 2024

Rebekah Taylor is a former journalist turned freelance writer and editor who has been translating technical speak into prose for more than two decades. Her first job in the early 2000s was at a small start-up called VMware. She holds degrees from Cornell University and Columbia University’s Graduate School of Journalism.
Related content

Security Insights for smarter, simplified network security without complexity
For LiveNX and LiveWire, get faster, cost-efficient threat detection and forensics without added complexity.

Network observability maturity stuck? Learn how to pull ahead
In EMA and BlueCat’s new report, learn about the five-stage Network Observability Maturity Model and how your enterprise can move along it.

How to choose a protective DNS solution for your network
Learn how to choose the protective DNS solution that’s right for your network, including capabilities and integrations—without vendor hype.

Route traffic intelligently with DNS-based GSLB for BlueCat Edge
Discover how DNS-based GSLB with BlueCat Edge empowers networking teams to control traffic steering, reduce costs, and improve resilience.