Customer situation brief on SUNBURST/Solorigate
Learn more about the attack via the SolarWinds Orion platform and how BlueCat products use DNS to help protect customers against compromises like it.

The following statement is in response to questions BlueCat is receiving regarding news of the SUNBURST/Solorigate cyberattack on SolarWinds and many of their customers, including FireEye, Microsoft, and the U.S. government. It is comprised of the following sections:
Overview of SUNBURST/Solorigate malware
How BlueCat helps protect customers
SUNBURST/Solorigate cyberattack details
How BlueCat ensures protection against threats
Overview of SUNBURST/Solorigate malware
On December 13, 2020, FireEye uncovered and reported on a widespread campaign in which malicious actors gained access to numerous public and private organizations around the world. They gained access to victims via trojanized updates to SolarWind’s Orion IT monitoring and management software. Post compromise activity following this supply chain attack has included at least lateral movement and data theft. The campaign is the work of an entity with vast resources and they were careful not to reveal their activities.
According to media reports and filings with the U.S Securities and Exchange Commission, SUNBURST/Solorigate impacted approximately 18,000 customers using the SolarWinds Orion platform. This core platform allows customers to plug in SolarWinds products (including IP address management [IPAM]) to provide a unified data layer and cross-platform support. It is used to monitor, analyze, and manage customer environments across the hybrid cloud and data centers, creating a treasure trove of valuable data should it be maliciously accessed.
On the Orion platform, a DLL file (an executable library) was weaponized with a Trojan. It was distributed in versions 2019.4-2020.2.1 of the Orion application. These versions were released to customers between March and June 2020. Because this file was a properly signed component of the upgrade for Orion, it would not have been flagged by customers as a security issue.
Once in a SolarWinds customer environment, the malware used DNS to lookup command-and-control (C2) channel endpoints. A more detailed discussion of the malware, how it works, and how it uses DNS, as well as a list of malicious endpoints, follows below.
In addition, in this 50-minute webinar on the SUNBURST/Solorigate breach, BlueCat’s Chief Strategy Officer Andrew Wertkin and Software Security Director David Maxwell explore how the malware exploited DNS in the attack and demonstrate how BlueCat Edge could have helped detect the manipulation of DNS queries and flagged the threat in advance.
How BlueCat helps protect customers
BlueCat’s DNS security offerings include two products that can help protect customers from SUNBURST/Solorigate malware: BlueCat Edge™ (Edge) and BlueCat Threat Protection.
BlueCat Edge™ (Edge)
BlueCat Edge gives cybersecurity and network teams shared visibility and control over internal and external DNS traffic through a single platform to help detect and block cyberattacks, simplify DNS operations, and improve network performance. Edge is cloud-managed. It offers a number of deployment options for service points, including all major cloud providers and on existing BlueCat DNS/DHCP servers (BDDSes).
BlueCat Edge documentation provides details for configuration and administration.
How does BlueCat Edge help customers identify and remediate attacks like SUNBURST/Solorigate?
Edge detects malicious behavior hidden in millions of DNS queries and response activity. Cybersecurity teams seeking to detect and stop data exfiltration like DNS tunneling, beaconing to C2 servers, or evasive techniques like domain generation algorithms (DGAs) use Edge’s smart analytics developed by BlueCat’s decades of DNS expertise.
Specifically:
- Edge allows network security teams to monitor specific IP addresses to help provide an additional layer of visibility and control over critical infrastructure. Because most firewalls today cannot identify the source IP address for DNS queries that egress to the internet, trying to monitor all DNS activity becomes overwhelming for network security teams. Edge makes this manageable by capturing the origin of queries. Threat hunters can quickly analyze the most important data and set specific policies based on the device or network.
- Edge protects against tunneling and data exfiltration. Edge uses a number of behavioral and reputational techniques to detect tunneling and flag it to prevent data exfiltration. Logs in Edge can be used to investigate the IP of where the tunneling has occurred. Incident response (IR) can look for similar DNS activity elsewhere on the network to find other infected clients—signs of possible lateral movement. This video provides an overview of how Edge detects tunneling:
- Edge reduces the time to remediate breaches. Edge makes it easy to pinpoint the origin and review the internal and external DNS activity surrounding an incident. For example, if an IR team needs to swiftly investigate the scope of the breach, they can request DNS logs from the networking team. But these are typically incomplete and can represent an unmanageable volume of queries. Sending it to a security incident and event management (SIEM) tool without the source IP will hinder an investigation and drive up costs. Edge solves these problems. It integrates with SIEM tools like Splunk, ArcSight, Qradar, passing only the most relevant or suspicious query data for further analysis and correlation with other security data. IR teams can pinpoint relevant insights in DNS data and correlate it with other intel. This lowers costs and shortens time to remediation. This video illustrates how Edge reduces time to remediate breaches:
Using Edge with SolarWinds Orion
Edge doesn’t just give threat teams a firehose for every DNS query, from every source. Instead, it marks specific queries and helps to identify suspicious patterns in the queries themselves. This helps identify and mitigate compromise earlier than when indicators of compromise are available in threat intelligence.
To be clear, unless Edge is explicitly configured to block all tunneling, it would not have blocked SUNBURST/Solorigate on its own or prevented the breach. But it would have identified potential tunneling on specific devices, providing clues for security teams to identify the breach and quickly contain it. For critical infrastructure, Edge can be configured to actively block these sorts of queries without creating false positives in user-driven devices.
BlueCat Threat Protection
BlueCat Threat Protection integrated security intelligence helps identify and stop threats before they can reach business-critical applications or data. Security teams get an additional layer of defense against malicious internet content and infected devices. BlueCat Threat Protection enables seamless integration of security intelligence, including BlueCat DNS over HTTPS blocklists, CrowdStrike, and other third-party threat feeds. It is an additional product offering that integrates with both BlueCat Integrity and Edge products.
How to leverage BlueCat Threat Protection for mitigation
BlueCat Threat Protection is a DNS firewall backed by an industry-leading threat feed. It blocks known DNS queries that malware uses for establishing C2 channels. If you are not using BlueCat’s Threat Protection feed, you can manually create blocklists for the indicators listed below.
If you have a license for BlueCat Threat Protection
If you have a license for BlueCat Threat Protection, below are configuration instructions:
- For Integrity policy configuration, see Configuring local Response Policies – BlueCat Address Manager – 9.5.0.
- For Edge policy configuration, see Domain lists – BlueCat DNS Edge – 2020.11 and Policies – BlueCat DNS Edge – 2020.11.
SUNBURST/Solorigate cyberattack details
As previously mentioned, a DLL file using a Trojan in versions 2019.4-2020.2.1 of the Orion application released between March and June 2020 was used to execute this attack.
A security patch has been released to stop the exposure if installed. Vendors have worked to sinkhole the C2 domains that were used so the Trojan can no longer establish a tunnel to let attackers into the network.
At the time of upgrade, the file was activated within the application. The Trojan software used DNS to reach out to a machine-specific domain ([dga derived label].avsvmcloud[.]com) to register and send initial information (internal domain names, etc.). It used a CNAME record to direct to the in-country C2 service.
- The Trojan and attack were sophisticated and intelligent enough to check against blocklists before querying to avoid analysis and ensure successful completion. It also waited two weeks before activating. It did tests to determine if it was in a sandbox test environment and avoided showing any indicators that would reveal its presence if it was in one. Based on the initial DGA query, an algorithm was then used to decrypt which company they had accessed. Then, it identified interesting networks to trigger further activity. For those not deemed of value, it appears the Trojan would stop querying.
- For customers deemed interesting, additional information (specific DNS names, IP address, instructions) were sent to the trojanized software to do harm. Examples of activities included utilizing the privileged accounts in Orion to compromise the organization’s Security Assertion Markup Language (SAML) signing certificate. By doing so, they created valid keys to all sorts of systems and data.
Domains queried in the Phase 2 portion of the attack include:
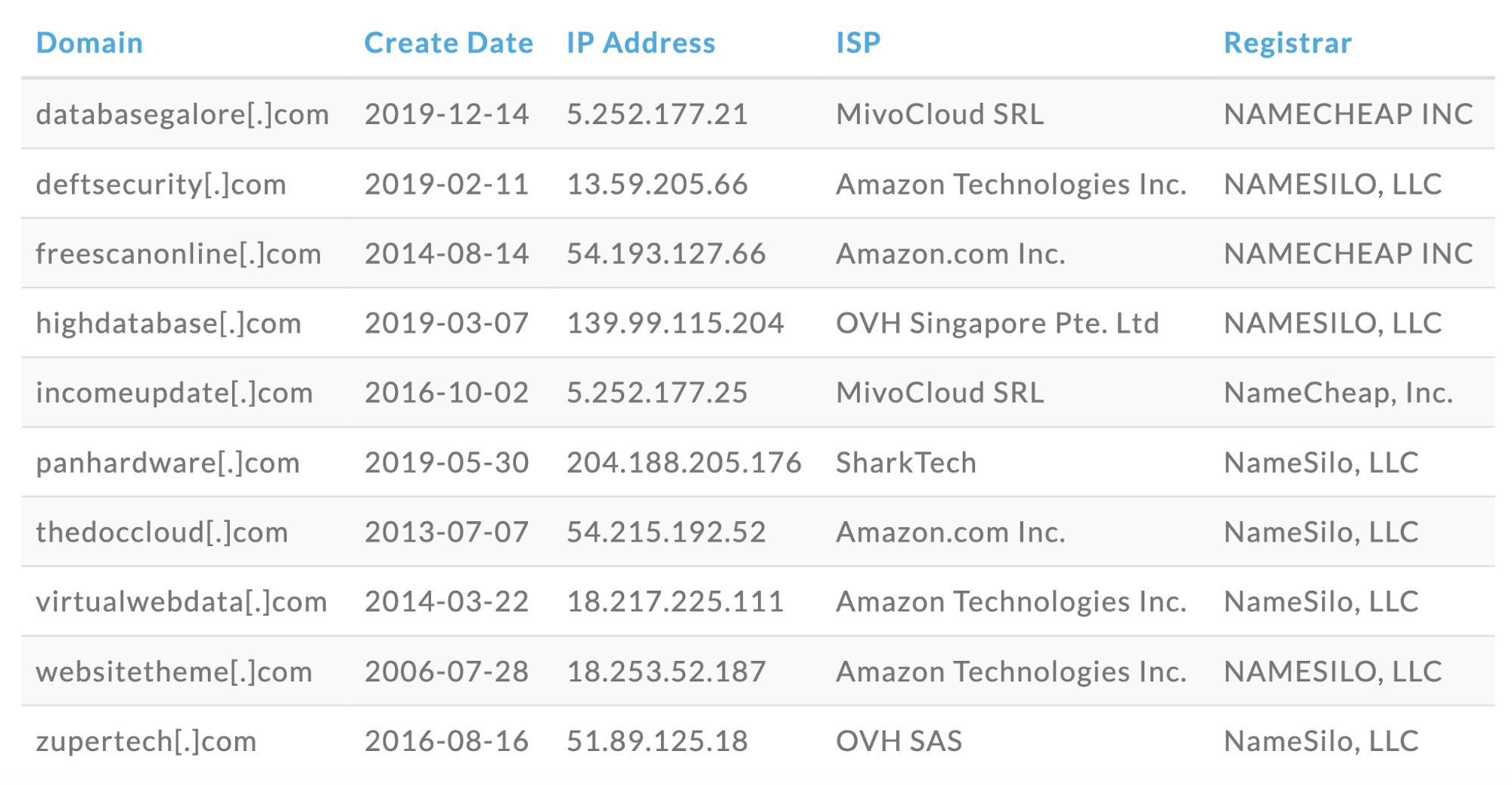
How BlueCat ensures protection against threats
BlueCat systems are not vulnerable. Our products do not contribute to the vulnerability of customer environments, nor are our corporate systems affected by this attack.
Steps BlueCat takes to protect its internal systems and codebase against malware
- We analyze our product builds using Software Composition Analysis (SCA). SCA lets BlueCat monitor the list of third-party components (especially open source) that are incorporated into our products. Having an accurate and specific component list allows BlueCat to make sure we comply with the license terms that apply to each component. The component list also gives BlueCat the ability to monitor known vulnerabilities in our software supply chain (Common Vulnerabilities and Exposures).
- Our engineers use two-factor authentication to access the corporate infrastructure. Our code is managed in version control systems that guarantee an unbroken chain of the modifications added to the codebase. Commits to the code must be approved by a reviewer other than the original code author.
- Our software builds that incorporate third-party software make use of strong cryptographic signatures. This ensures that the versions of the packages we retrieve for inclusion in the build are intact as intended by the upstream providers.
- BlueCat also analyzes our software using static code analysis to identify software defects. It allows many coding errors to be corrected during the development process before the software is shipped to customers. It can also highlight some unusual behaviors that would indicate unwanted functionality being inserted into the code.
- We have annual penetration testing performed against our products, configured as they would be deployed in a customer environment. Findings are remediated by engineering teams in past or current BlueCat releases via patches for high-severity items. For lower severity findings, fixes are incorporated in future releases only.
- Additionally, BlueCat runs vulnerability scanning tools against our products, looking for any issues in software or configuration that should be patched. These tools are run on an ongoing basis against current and prior releases. This ensures that any tool and knowledge base updates are applicable to all supported releases that customers may be using.
- From a corporate standpoint, BlueCat has annual penetration tests performed on BlueCat’s corporate IT environment. Our IT staff and operations staff also use two-factor authentication for access to BlueCat internal systems and our cloud infrastructure. BlueCat has annual SOC2 Type 2 audits performed to confirm that our set of operational controls are operational and effective. Finally, BlueCat has an internal security committee whose activities are visible and communicated at the board level.
Further developments and additional information
BlueCat will continue to monitor and provide updates as needed. This is a developing situation and all technical details may not yet be publicly available. You can also learn more about the attack and how BlueCat helps customers in our SUNBURST/Solorigate webinar with BlueCat’s Chief Strategy Officer Andrew Wertkin and Software Security Director David Maxwell.







