How to choose a protective DNS solution for your network
Learn how to choose the protective DNS solution that’s right for your network, including capabilities and integrations—without vendor hype.

Knowing how to choose a protective DNS solution is crucial for enterprises seeking to enhance their defenses against evolving cybersecurity threats.
DNS (Domain Name System) is inherently vulnerable to compromise by bad actors. DNS management tools offer some protection, but their limits make DNS a common target for exploitation. Protective DNS (PDNS) solutions analyze and filter DNS queries in real time using policy-based security controls. With strong endorsements from U.S. federal cybersecurity agencies CISA and NSA, selecting the right PDNS solution tailored to your organization’s specific needs is essential.
But with lots of vendor hype out there, it can be daunting to know how to select the protective DNS solution with the right capabilities and integrations for your network.
In this post, we first offer six essential features to prioritize when assessing a PDNS solution. Next, we delve into the eight evaluation criteria to keep in mind when choosing your solution. Then we touch on important points to keep in mind for privacy and compliance and common mistakes to avoid. Finally, we highlight how BlueCat’s security solutions offer a protective DNS solution that proactively defends against threats and offers comprehensive visibility and control over DNS activity.
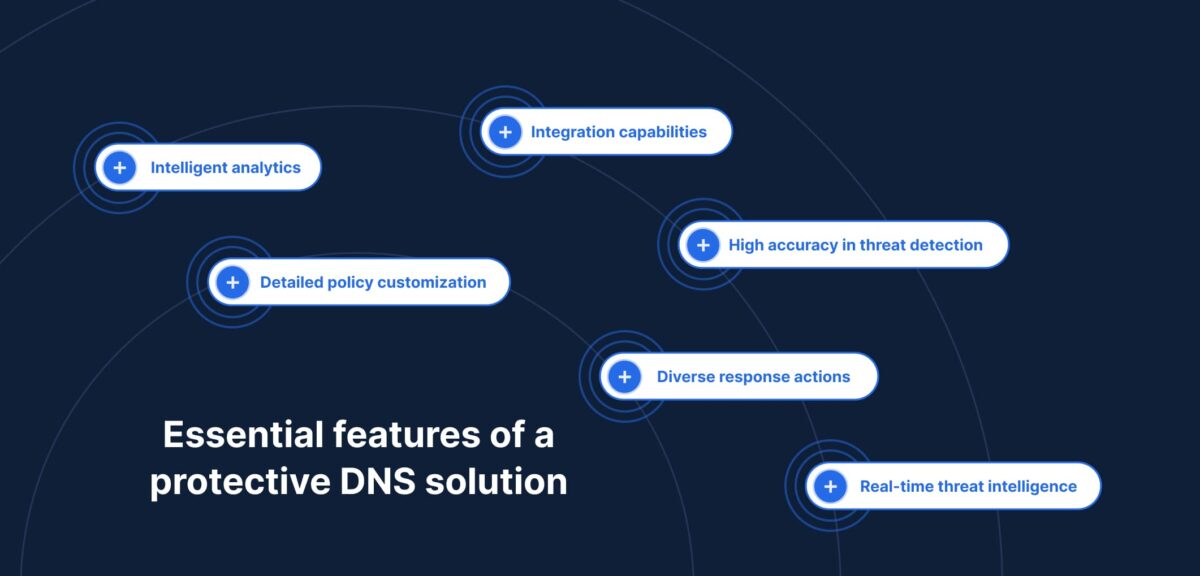
Essential features of a protective DNS solution
When assessing a PDNS solution, prioritize the following core features:
- High accuracy in threat detection: Solutions should accurately identify and classify malicious domains.
- Diverse response actions: Look for solutions that offer options such as NXDOMAIN blocking, traffic redirection, and sinkholing, providing flexibility in threat management.
- Real-time threat intelligence: Continuous updates from multiple threat feeds ensure rapid responses to new threats.
- Intelligent analytics: Advanced analytical methods, including detection of domain generation algorithms (DGAs), improve the identification of sophisticated threats.
- Detailed policy customization: Fine-grained policy controls allow organizations to implement security tailored to specific user groups, geographical regions, or business units.
- Integration capabilities: A PDNS solution should integrate smoothly with existing security tools such as SIEM and SOAR platforms, endpoint detection and response systems, and firewall solutions.
Furthermore, robust API support and webhook capabilities ensure future-proof integration. Additionally, intuitive administrative dashboards and comprehensive alerting systems facilitate efficient management and oversight.
Evaluation criteria for choosing a PDNS solution
Keep these criteria in mind when selecting your PDNS solution:
- Effectiveness: Consider validated accuracy, low false-positive rates, and third-party evaluations.
- Threat intelligence sources: Verify the diversity and robustness of intelligence data used.
- Deployment options: Ensure the solution supports diverse deployment scenarios, including cloud, hybrid, and on-premises.
- Configurability: Look for customizable settings that adapt to your organization’s risk profile, operational geography, and internal policies.
- Scalability: The solution must be easily scaled to accommodate organizational growth while maintaining performance.
- Performance metrics: Assess factors like DNS query resolution speed and minimal latency.
- Visibility and logging: Comprehensive logging, historical data accessibility, and integration with SIEM systems are crucial for effective threat monitoring and incident response.
- Support and reliability: Select providers that offer reliable, around-the-clock support to minimize downtime and maintain high service availability.

Privacy, compliance, and data management
When selecting a protective DNS provider, it’s essential to ensure their practices align with your organization’s privacy expectations and compliance mandates. This includes strict adherence to data sovereignty laws and clearly defined retention policies that govern the duration and location of DNS data storage.
Transparency is equally critical. Your provider should offer clear insights into how your data is handled and analyzed, and whether it’s shared with third parties.
Finally, comprehensive service-level agreements should clearly outline these policies, providing contractual assurance of accountability and compliance.
Common mistakes to avoid
Avoid the following mistakes when choosing a PDNS solution:
- Making decisions based solely on cost or brand: Evaluate solutions based on their specific capabilities and alignment with your organization’s needs.
- Ignoring potential bypass risks: Ensure the selected PDNS solution addresses bypass threats, such as direct IP addressing or alternate resolver usage.
- Underestimating deployment constraints: Consider practical aspects of deployment and integration within hybrid or multicloud network environments.
Enhancing protective DNS with BlueCat solutions
If you’re evaluating protective DNS solutions as part of a broader security strategy, consider how DNS visibility, control, and integration factor into your overall architecture.
Whether you’re just starting with protective DNS or optimizing an existing stack, aligning your DNS infrastructure with your security goals can make all the difference. BlueCat’s security solutions combine DNS-layer control with packet-level visibility and real-time flow monitoring to detect threats earlier, respond faster, and enforce policies across your entire network. You can take the next step towards a more secure, agile, and resilient network with BlueCat Edge to proactively defend against threats, streamline security operations, and gain comprehensive visibility and control over DNS activity.
Furthermore, products like BlueCat Integrity provide centralized DNS orchestration that complements the protective DNS solution that Edge offers. Integrity ensures policy enforcement, reduces misconfigurations, and supports complex hybrid and multicloud environments.
Request a demo today to see how BlueCat Edge can transform your DNS security and empower your enterprise.




