Why you should pay attention to DNS tunneling
DNS tunneling transmits information through the protocol that usually resolves network addresses. Your DNS data can provide clues to help keep it at bay.

DNS is a prime vector for cyberattacks, including DNS tunneling.
In short, tunneling is a way of transmitting information through the DNS protocol that usually resolves network addresses.
A normal domain name system (DNS) query only contains the information necessary to communicate between a client and a server. DNS tunneling inserts an unrelated stream of data into that pathway. It establishes a form of communication that bypasses most filters, firewalls, and packet capture software.
That makes it especially hard to detect and to trace its origin. It’s an elusive menace for network security.
But it is stoppable.
This post will explore how DNS tunneling works and why it is a security risk. Next, it will discuss how to detect an attack. Finally, it will examine how to use your DNS data and the BlueCat platform to monitor your DNS traffic and block tunneling altogether.
How does DNS tunneling work?
To start, a bad actor registers a domain, like evilwebsite.com. The bad actor installs a tunneling malware program on their DNS server and points evilwebsite.com’s name server to it.
The attacker then infects a computer behind the victim’s firewall with malware. Because DNS requests can normally move in and out of the firewall, the infected computer can send a query to the DNS resolver.
The DNS resolver then routes the query to the attacker’s command-and-control server where the tunneling malware is installed. The attacker establishes a connection to their victim through the DNS resolver.
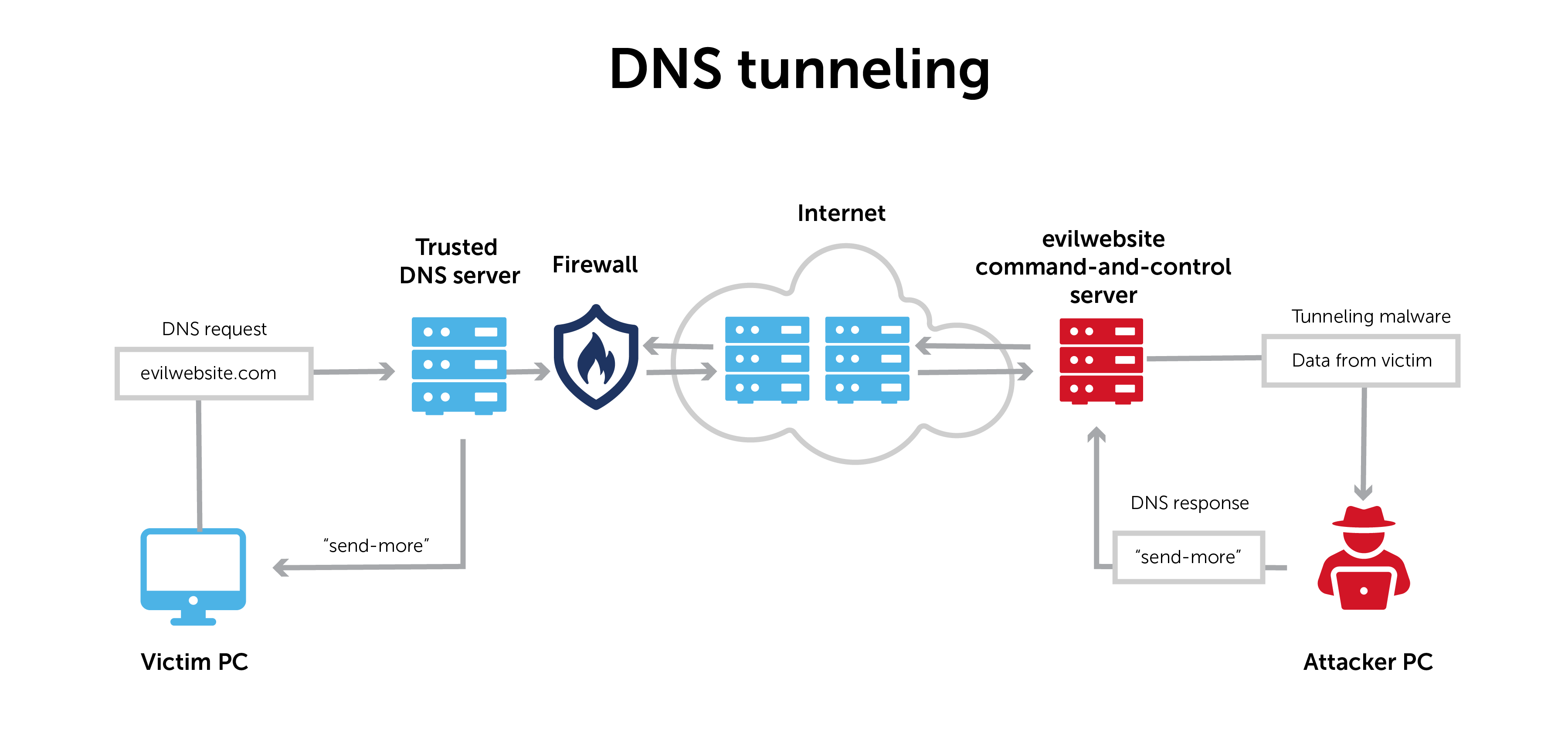
DNS tunneling moves data across a network in a way that makes it appear as public information. In fact, however, it is private. This form of secure movement allows the data to pass through the network unnoticed via a process called encapsulation.
In short, it’s like a VPN connection through the DNS protocol. And now the bidirectional tunnel is available for data exfiltration or other malicious activities.
Why DNS tunneling is a security risk
DNS is often left open and unmonitored. Some network administrators believe that they’ve got Port 53 covered with their firewall and take no further action.
Knowing this, malicious actors increasingly use tunneling to their advantage. They skirt standard cybersecurity protections by communicating through what looks like a background operational channel. There are plenty of DNS tunneling tools, like Iodine, to use right off the shelf.
Most techniques, whether using these tunneling toolkits or otherwise, are not particularly stealthy. When no one’s looking, they don’t have to be.
Malicious actors use this tactic in many ways. They can establish command and control (C&C) with DNS tunneling. This hides the beaconing to outside assets that most filters and firewalls would notice.
Data exfiltration can also take place through DNS tunneling attacks, resulting in compromised systems and data. In these cases, information is often broken up into smaller pieces and moved out through DNS. Then it is reassembled on the other end.
How to detect a DNS tunneling attack
How do you detect tunneling attacks? DNS queries themselves often provide clues.
Standard DNS queries are usually quite simple—they consist primarily of a domain and subdomain. On the other hand, with tunneling, malicious actors try to put as much data into the communication channel as possible. Querying for text (TXT) records, which are not commonly used by a typical client, may be helpful in identifying tunneling activity.
It’s important to note that tunneling often includes a series of queries from the DNS server. Each one is different from the next. The unique nature of these queries increases the chances of getting through to the server side.
Records with long strings of unique characters, long labels, and long hostnames are almost always DNS tunneling.
DNS tunneling: friend or foe?
DNS tunneling has legitimate uses. For example, many anti-virus software providers use it as a way to update malware profiles in the background.
Apart from these known use cases, however, it is usually a tip-off that something may not be right.
Other patterns in DNS data can indicate whether the tunneling is a possible threat to your network’s security. When administrators notice a lot of DNS requests at once, this often indicates a malicious purpose. Examples might be an abnormal pattern of DNS activity for a single IP address, or multiple requests and response pairs over time.
The answers are in your DNS data
The key is to pay close attention to DNS data. Questions you need to consider are:
- What does the volume of DNS traffic and number of hostnames per domain say about what’s happening on your network?
- What can the domain history tell you about network activity?
- Have DNS queries jumped to a part of the world where your organization has no business or other connections?
- Does the device making those connections have any business doing so? Or is it a single-use IoT device?
Taking action against malicious activity
DNS is not intended for data transfer. As a result, many enterprises don’t monitor their DNS traffic for signs of suspicious activity. And bad actors take advantage of it.
Following solid clues can help you determine if someone is holding your DNS hostage and using it for malicious communication. You just have to pay attention to it.
On a basic level, it means having an organized system to collect, monitor, and take action on DNS data. If you don’t have a centralized DNS management system, you will have a hard time detecting any activity. Microsoft DNS, BIND, or a homegrown solution like IP address spreadsheets make detection a real challenge.
The BlueCat platform monitors your DNS traffic and can block DNS attacks like tunneling before they wreak havoc on your network. Learn more about how BlueCat can transform your network security.




