Cloud, automation, security drive DDI pursuit
EMA research found that cloud, automation, and security are the three primary drivers behind investing time or money in DDI technology. What drives you?

If your organization is ready to move on from a do-it-yourself (DIY) approach to DDI, what drives your pursuit to invest time or money in a DDI management platform?
DNS, DHCP, and IP address management (IPAM) provide the core services that enable network communications. DDI is often used as an acronym to describe the integration of these three core components of networking into one management platform. A mature DDI strategy is essential to taming complex enterprise networks.
A recent survey conducted by Enterprise Management Associates (EMA) of 227 IT professionals from medium and large enterprises (more than 2,500 employees) across North America and the United Kingdom explored what pushes organizations to invest time or money in mature DDI solutions. EMA found three primary drivers:
- Public cloud migration or transformation
- A network or IT automation initiative
- A security incident
This post will explore each of these factors in depth, as well as some additional factors that respondents cited, including the impact of the Internet of Things (IoT) in particular.
Network complexities underly DDI technology investment
Enterprise networks are complex by nature. A large network will have multiple IP address schemas and multiple internal and external DNS services driven by network architecture, geography, and business structure. In fact, 52% of respondents cited network complexity as one of their biggest challenges to DDI management.
Aiming for a mature approach to DDI — beyond a DIY approach of spreadsheets or open-source tools — is essential for any organization to overcome this complexity and enable true digital transformation. What differs for each organization is the primary investment driver.
First driver: Public cloud migration or transformation
Nearly 62% of respondents said cloud transformation is the primary reason behind investing time or money in DDI technology.
The migration to hybrid cloud or multi-cloud environments adds complexity because the network team loses centralized control over DDI services. A mature DDI solution with cloud support, especially for multiple cloud providers, can help the network team regain control.

Most enterprises have some form of a hybrid cloud approach. In a hybrid-cloud architecture, some applications and infrastructure are in third-party public clouds and some are in private clouds. And some remain in on-premises or hosted data centers. Admins use orchestration tools to manage the workloads and balance between them all.
At first glance, a public cloud DNS service appears like a great option for simplifying your operations. You can let a cloud provider help you manage the complexity of DNS in the environment you already subscribe to. But public cloud DNS has limitations that can present availability, compliance, and security challenges. Hybrid environments require centralized management of DDI, which cloud DNS does not provide.
BlueCat’s solutions for hybrid cloud management help you keep up with changes in the cloud while bridging to core DDI infrastructure.
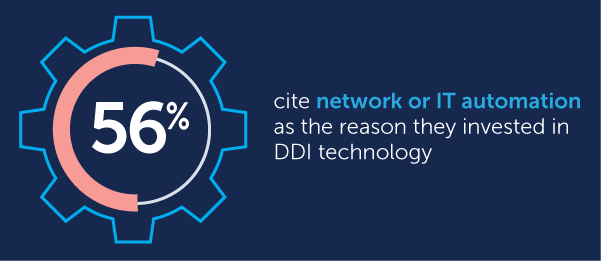
Second driver: Network or IT automation initiative
Just about 56% of respondents cited a network or IT automation initiative as their biggest driver behind an investment of time or money in DDI technology.
Network and IT automation initiatives usually aim to improve operational efficiency and compliance, neither of which are achievable without DDI services. For instance, when an automation tool instantiates a new virtual machine in a data center or a cloud environment, it will need to assign that server an IP address and domain name. Integration with a mature DDI solution facilitates more effective automation.
A senior network engineer with a Fortune 500 retail company told EMA about their path to network automation. “We had too many things we were doing manually with our small staff. We were spending an hour a day just doing DNS entries. Now, we have ServiceNow integration. You can open a DNS ticket and it automatically generates a DNS request and a DNS update [in our DDI management platform]. We are trying to automate more mundane tasks in DDI so our engineering team can focus on more important things.”
We had too many things we were doing manually with our small staff. We were spending an hour a day just doing DNS entries.
BlueCat’s automation platform and library of adaptive applications and plugins transforms business logic into custom DDI workflows using highly configurable and tailored APIs.
Third driver: A security incident
For nearly 48% of respondents, a security incident drove their investment of time or money in DDI technology.
DNS was built to correctly and efficiently respond to queries, not question their intent. As a result, DNS has real vulnerabilities and potential as a vector for cyberattacks.

A DNS attack is one in which a bad actor either tries to compromise a network’s DNS or takes advantage of its inherent attributes to conduct a broader attack. A well-orchestrated DNS attack can bring an organization to its knees.
Denial-of-service (DoS) attacks and distributed-denial-of-service (DDoS) attacks are what most people think of when they think of a DNS attack. Indeed, there were more than six million global DDoS attacks in the first half of 2022.
Other major types of DNS attacks include DNS hijacking, DNS tunneling, and DNS poisoning and cache poisoning.
While DNS has historically been seen as a naive pawn, it can also be a proactive part of a good defense-in-depth strategy. The concept of protective DNS recognizes that DNS is critical to protecting against network threats.
Commercial DDI products offer robust administrative security capabilities, such as role-based access control. DDI solution vendors are increasingly adding security features and additional security products to address this trend. EMA’s research found that 77.5% of survey respondents use a DNS security solution, such as a DNS firewall or DDoS protection.
BlueCat’s network security features can transform your DNS from an attack vector to a line of defense.
Other drivers (and IoT in particular)
Beyond these top three, EMA found a number of secondary drivers for organizations to invest time or money in DDI solutions. They include:
- Risk assessment or compliance (46%)
- Application modernization or cloud-native applications (46%)
- Internet of Things (IoT) (43%)
- Service outages or performance problems caused by DDI errors (41%)
- Mergers and acquisitions (25%)
Survey respondents who told EMA that they are successful in their DDI technology implementation singled out IoT as an important driver. As the IoT ecosystem grows, many enterprises have connected sensors, cameras, and other wireless devices to conduct business. These endpoints often have no individual user associated, so identity can’t be relied upon for access control. IP address management can serve as an important foundation of IoT network segmentation.
What is driving your investment in DDI technology? Learn how your organization compares by downloading EMA’s report today.
Want to read more about the report? Learn how two-thirds of enterprises realize the benefits of full-stack DDI solutions.
Want to know more about DDI maturity at small and medium enterprises in Europe, the Middle East, the Asia-Pacific region, and Latin America? Read the international version of the report and learn how automation is the No. 1 driver of DDI investment.





