DNSSEC vs DNS security: What’s the difference?
DNSSEC validates DNS queries and responses, while DNS security leverages DNS data to better secure your network. Learn how they’re different with BlueCat.

When you say DNSSEC, that’s just shorthand for DNS security, right?
In a word, no. But you need them both.
DNSSEC is a technical best practice to authenticate DNS queries and responses by using cryptographic digital signatures. DNS security, on the other hand, is the concept that you can leverage Domain Name System (DNS) data to better secure your entire network.
Here’s a good way to think about it: DNSSEC validates DNS queries and responses. DNS security asks, “What are you doing with those queries and responses?”
This post will first briefly define what DNSSEC is. Then, it will explore the idea of DNS security. Finally, it will touch on why you need both to keep your network secure and how BlueCat can help.
A brief primer on DNSSEC
To start, DNSSEC stands for Domain Name System Security Extensions. It is a set of specifications that uses digital signatures based on cryptography to authenticate DNS queries and responses.
(And for understanding DNS vs DNSSEC, remember, DNS is the protocol, and DNSSEC is a security extension for that protocol.)
DNSSEC helps a DNS server answer the following questions:
- Is the root or authoritative name server authorized to provide a query response?
- Can I trust the content of the query response?
- Can I trust that there were no modifications to the response in transit?
Unfortunately, attributes inherent to the DNS protocol can put any entity at risk for cyberattacks.
Normal DNS resolution cannot screen the responses it gets and answer the three questions above. This makes standard DNS queries susceptible to man-in-the-middle attacks like DNS poisoning. An attacker injects a forged response to replace the legitimate response to a DNS query.
DNSSEC validates responses to DNS queries before returning them to the client device. DNSSEC uses digital signatures stored in name servers alongside common DNS record types.
At the center of DNSSEC is a public-private key pair. Each DNS zone has a public key and a private key. Public key cryptography is the starting point for DNSSEC validation. Available to everyone, a public key provides the means to decrypt messages signed by a corresponding private key.
With DNSSEC enabled during an attempted man-in-the-middle attack, the validating resolver rejects the response from a rogue server because it does not have the cryptographic data that validates its origins. The resolver does not return the fake response to the client.
The more domains that support DNSSEC, the more secure the internet is for everyone. There is lots more to uncover to help you answer the “What is DNSSEC and how does it work?” question.
On the other hand, what is DNS security?
DNS security is a concept, not a single practice, protocol, or extension like DNSSEC. At its most basic level, it means leveraging your DNS data to better secure your enterprise network.
Recently, Gartner recognized DNS security as crucial for improving the overall defense of your network. Historically, DNS has been foremost thought of as something that needs to be protected. Indeed, a DNS attack can happen in a multitude of ways.
Meanwhile, it is not widely recognized for its importance to overall network security. It’s far less commonly seen as a line of defense in an overall protection plan. But two major U.S. security agencies released guidance pointing to protective DNS as a defense strategy, confirming DNS is critical to detecting network threats.
At the strategic level, DNS security means you are incorporating DNS into your overall network security plan. Operationally, it means using DNS security best practices to secure vital assets on your network (in conjunction with other tools, of course). There are several methodologies—like DNSSEC—and platforms—like BlueCat’s—that you can deploy.
While filters, firewalls, on-device agents, and other security software platforms scour or shield different parts of the network, DNS can provide critical contextual information to clue you into what might be happening on your network. You can discern who’s there, what they are trying to access, and aberrations in normal activity patterns.
DNS response data—not just queries—allows for an even more thorough forensic analysis. And with complete information about every query on the network, administrators can root out malicious patterns of behavior or identify infected devices.
Furthermore, creating block and allow lists for DNS are both highly popular and crucial for reducing attack surfaces. Enterprises can allow only a predetermined list of domains to resolve. Or block certain malicious domains from resolving.
You need both DNSSEC and DNS security
DNSSEC and DNS security are both critical to keeping networks safe.
You need to ensure the integrity of your DNS by authenticating queries and responses (DNSSEC) while at the same time analyzing the overall data that flows through that same protocol (DNS security).
BlueCat’s platform can help you manage both.
When it comes to implementing DNSSEC, it’s easy to underestimate its complexity and just how much knowledge it requires. When you centralize your DNS infrastructure with BlueCat, numerous DNSSEC-related tasks happen in the background, automatically, such as generating cryptographic key pairs.
Furthermore, you can find threats faster and get full visibility into internal and external network traffic with BlueCat’s platform. With BlueCat, you have the ability to systematically gather and analyze DNS data in one place.
For example, both DNS queries and responses are logged together. As a result, you get a complete picture of the DNS activity on your network. Using both query and response data, admins can then create policy-based rules that are more informed and precise. Furthermore, BlueCat DNS Edge attaches policy alerts to your logged query data.
And with BlueCat DNS Edge, you can apply threat intelligence and set policy-based rules to block, allow, or manually watch certain domains.
Whether at the network boundary or client level, DNS-based security policies can be very targeted, allowing as much or as little leeway for queries to resolve as appropriate. For example, a policy for an IoT device might limit DNS queries to a single server where they need to deliver information.
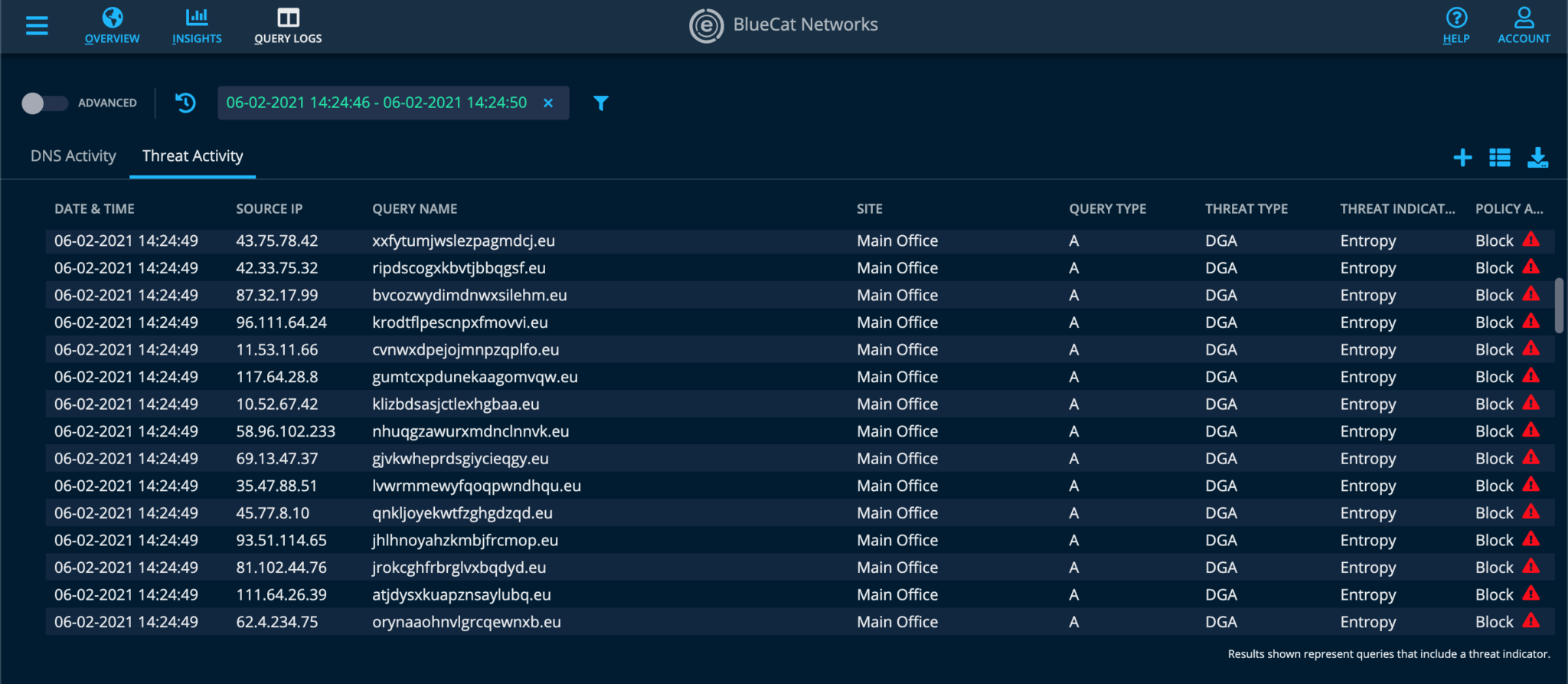
This screenshot illustrates how BlueCat’s policy-based rules block DNS queries from known domain generation algorithm (DGA) malware:
Learn more about how you can implement DNS security on your network.




